
Applications Release 12 users can configure their environments to delegate user authentication to an external Single Sign-On 10g 10.1.4.0.1 instance. In this optional configuration, Single Sign-On validates E-Business Suite user credentials against an external Oracle Internet Directory 10g 10.1.4.0.1 instance.
This certification is documented in:
- Integrating Oracle E-Business Suite Release 12 with Oracle Internet Directory and Oracle Single Sign-On (Metalink Note 376811.1)
A Quick Conceptual Overview
Looking over previously published articles, I’m bemused to see that I haven’t profiled this configuration for Release 12 environments yet. So, I’ll file off the serial numbers and revisit the Release 11i version of this article in a quick recap of the key things you need to know about this configuration.
Centralized Single Sign-On Solution
Most E-Business Suite users have multiple environments for sandbox testing, QA, development, and production. You’ll likely have even more environments if you’re migrating from Release 11i to Release 12.
If
you have a mix of E-Business Suite Release 11i and/or 12 instances and are
tired of maintaining users separately for each environment, you can
create a central Oracle Application Server 10g environment running Single Sign-On and Oracle Internet Directory 10g. This allows you to manage all E-Business Suite users for all of your environments centrally. You can use the same central environment to manage PeopleSoft and JD Edwards users centrally, too.
Use Oracle Internet Directory Instead of FND_USER
The
E-Business Suite’s native user management capabilities (based on the FND_USER
directory) are perfectly adequate for administering E-Business Suite
users. However, security administrators looking for additional user
management and provisioning features would benefit from switching to Oracle Internet Directory.
Integrate with Third-Party LDAP and Single Sign-On Products
If
you have an existing corporate security system such as Microsoft Active
Directory, Windows Kerberos, Sun Java Identity Management Suite (SunONE/iPlanet), or Netegrity SiteMinder,
using Single Sign-On and Oracle Internet Directory 10g allows you to integrate your E-Business Suite with
that infrastructure. This is a topic for a future In-Depth posting;
watch this space.
How Single Sign-On 10g Works With the E-Business Suite
When the E-Business Suite is integrated with OracleAS 10g and Single Sign-On 10g, the user authentication process is handled by Single Sign-On 10g.
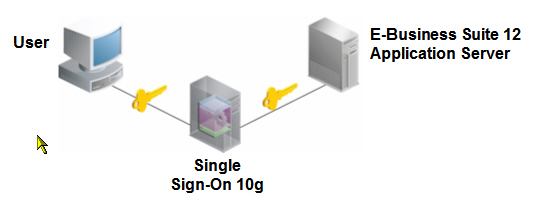
Users
attempting to access protected E-Business Suite content are redirected
to Single Sign-On 10g for authentication. Users log in via Single
Sign-On 10g, and then are redirected back to the E-Business Suite and
the protected content they wished to access.
Authentication versus Authorization
It’s important to distinguish user authentication from user authorization:
- User authentication is the process of establishing whether the user is whom they claim to be.
- User authorization is the process of determining what resources an authenticated user is permitted to access.
our current integration for the E-Business Suite Release 11i, these two
processes are handled by Single Sign-On and the E-Business Suite,
respectively:
- When the E-Business Suite is integrated with Single Sign-On 10g, it delegates user authentication to Single Sign-On.
- After Single Sign-On has successfully authenticated a user, the E-Business Suite handles the authorization process: e.g. ensuring that the user is entitled to file expenses.
The E-Business Suite is a Single Sign-On partner application.
Once a user logs on successfully to Single Sign-On 10g, the user has
access to all registered partner applications without having to log on
again.
Likewise, if a user logs out of any one of those partner applications, the user is logged out of all of them. This is called Single Sign-Off, and works with the E-Business Suite, too.
Under the Covers: The Chain of Trust
The key architectural concept to understand is that there is a chain of trust established between the E-Business Suite, Single Sign-On 10g, and Oracle Internet Directory 10g:
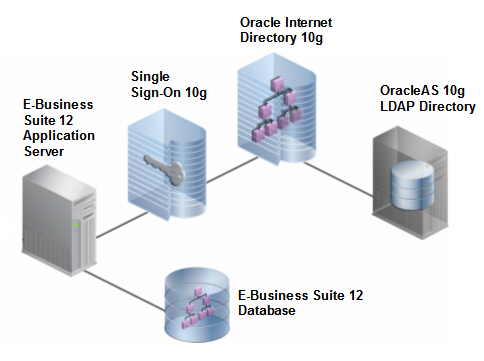
The
E-Business Suite delegates user authentication to Single Sign-On, and
Single Sign-On delegates user credential validation to Oracle Internet
Directory.
The Log In Process, Deconstructed
Let’s walk through this with an example:
Our
example user isn’t logged into the E-Business Suite. She attempts to
access a bookmarked link in her browser that points to the E-Business
Suite’s Self-Service Expenses page.
The E-Business Suite checks
the user’s browser for a valid Release 12 cookie, but doesn’t find one: not
surprising — she hasn’t logged in yet.
The E-Business Suite
redirects the user to Single Sign-On 10g. Single Sign-On 10g displays
a login screen and collects the user’s userid and password. It then
passes those credentials to Oracle Internet Directory for validation.
Oracle
Internet Directory looks up the user’s credentials in the Oracle
Internet Directory LDAP directory in the OracleAS 10g Infrastructure, providing an approval or rejection as
appropriate to Single Sign-On.
If
approved, Single Sign-On 10g issues a set of security tokens to the
user and redirects her back to the E-Business Suite. If rejected, the
user is given another chance to log in with valid credentials.
Once
redirected back to the E-Business Suite, the E-Business Suite
recognizes the Single Sign-On security tokens and looks up the user’s
assigned Applications Responsibilities in the E-Business Suite FND_USER
table.
Having established that our example user is authorized
to access Self-Service Expenses, the E-Business Suite issues its own
security tokens and creates a new ICX user session. The user now has
two sets of security tokens in her browser, one from Single Sign-On
10g, and another from the E-Business Suite.
At this point, the user is officially logged in, and is redirected to Self-Service Expenses.
Synchronizing User Credentials Between Oracle Internet Directory and the E-Business Suite
If
user authentication and user authorization are performed by two
different parts of this integrated system for the same user, the alert
reader will leap ahead and guess that user credentials need to
synchronized.
That guess would be correct: user credentials in
Oracle Internet Directory and the E-Business Suite’s FND_USER directory
need to be synchronized. A user must be recognized and have valid
entries in both locations to gain access to protected content.
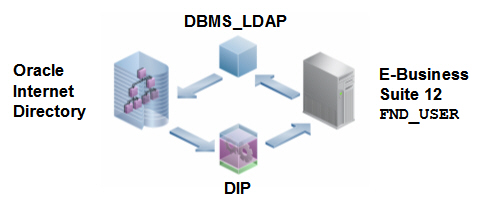
This synchronization is handled by an Oracle Internet Directory
tool called the Directory Integration & Provisioning Platform.
It’s
up to you to designate the master “source of truth” for user
credentials; this is fully configurable. For example, you can
designate the E-Business Suite as the master and Oracle Internet
Directory as the slave, or vice versa. You can even elect to manage
user credentials in both locations and have changes updated
automatically between the two of them.
In other words, changes to user credentials can flow:
- From the E-Business Suite to Oracle Internet Directory
- From Oracle Internet Directory to the E-Business Suite
- Bidirectionally between them.
Related
- Portal 10g (10.1.4.1) Certified with Apps 11i & 12
- In-Depth: Using Single Sign-On 10g with E-Business Suite Release 11i
- Security Best Practices for Release 12
- FAQ: Using Oracle Application Server 10g with E-Business Suite Release 12
