[Contributing Author: Madhu Majari]
We are currently working on the certification of SHA-2 with the Oracle HTTP Server (OHS) delivered with Oracle E-Business Suite 12.1.3. As described in this blog article, a reverse proxy or load balancer can be used until that certification is available. You can use a reverse proxy or load balancer as the end-point for the encrypted connection that is initiated by a client (for example, a browser). In other words, the reverse proxy or load balancer — not Oracle HTTP Server — acts as the TLS termination point. Since that article was published, many customers have requested that we certify a reverse proxy for use as the TLS termination point with Oracle E-Business Suite Release 12.1. I’m pleased to announce that we have completed the certification of HAProxy 1.5.2 with Oracle E-Business Suite 12.1.3. HAProxy is an open source offering that provides load balancing and proxy solutions. The certification of HAProxy 1.5.2 with Oracle E-Business Suite 12.1.3 provides the following configuration options:
- Certificates signed with SHA-2 for inbound HTTP connections
- TLS 1.2 with stronger cipher suites
Note: There are many reverse proxies and load balancers that can be used as an TLS termination point for Oracle E-Business Suite. If you already have a reverse proxy or load balancer deployed you may configure it as the TLS termination point for your Oracle E-Business Suite 12.1.3 environment.
Deploying and Configuring HAProxy
For detailed installation instructions, refer to the following My Oracle Support Knowledge Document:
You may deploy HAProxy as follows:
- On an existing Oracle E-Business Suite application tier
- On a separate server or virtual machine
HAProxy is available as an installable RPM package as part of the Oracle Linux distribution. You can also download HAProxy and compile it for other operating systems (refer to the installation note for more details). On Oracle Linux you may install it as the root user with the following command:
#yum install haproxy The main configuration file is located here:
/etc/haproxy/haproxy.cfg
A summary of the configuration steps for HAProxy includes the following:
- Define the IP address and and port for the Oracle E-Business Suite 12.1.3 environment.
- Setup TLS protocols and avoid SSL 3.0. (This will the mitigate POODLE vulnerability.)
- Enable strong cipher suites. (This will mitigate the FREAK vulnerability.)
- Define the certificate (chain) with PEM files.
If you have an existing Oracle E-Business Suite 12.1.3 environment configured with SSL/TLS per Enabling SSL in Oracle E-Business Suite Release 12 (Note 376700.1), then you may easily configure HAProxy to serve as the TLS termination point.
For example, given the following conditions for your Oracle E-Business Suite Oracle HTTP Server listener configuration:
- HTTP requests use port 8000
- HTTPS requests use port 4443
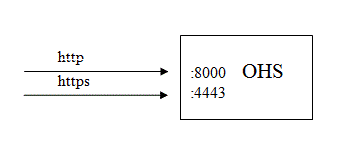
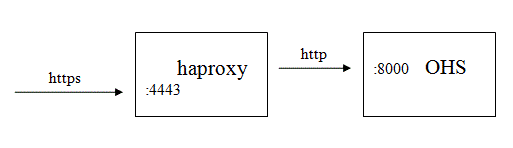
Then, you may perform the following:
- Shutdown the Oracle HTTP Server HTTPS listener (port 4443)
- Install, configure and start HAProxy to listen on port 4443
Related Articles
References
- Using HAProxy as the TLS Termination Point for Oracle E-Business Suite 12.1.3, Note 2012639.1
- Secure Configuration Guide for Oracle E-Business Suite Release 12 (Note 403537.1)
- Enabling SSL in Oracle E-Business Suite Release 12 (Note 376700.1)
