[Dec. 16, 2014 update: There is another newer-version of this article that references Oracle Access Manager instead of the now-obsolete Oracle Single Sign-On product]
This article is an updated R12 version of an earlier one written for Oracle E-Business Suite Release 11i.
Like most of our customers, you probably already have a corporate identity management system in place. And, you’ve probably not been enjoying the experience of redundantly administering the same user in your corporate identity management system as well as the E-Business Suite. If this describes your environment, this in-depth article about integrating Oracle E-Business Suite Release 12, Oracle Single Sign-On and Oracle Internet Directory with third-party identity management systems will show you a better way of managing your EBS users.
No More Redundant User Administration
It is possible to integrate the E-Business Suite with existing third-party LDAP and single sign-on solutions via Oracle Application Server 10g and Single Sign-On 10g, like this:
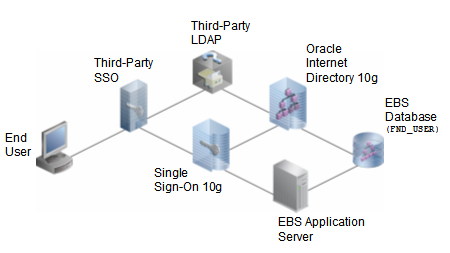
Third-party single sign-on solutions can be integrated with Oracle Single Sign-On 10g, and third-party LDAP directories can be integrated with Oracle Internet Directory 10g. From there, it’s a short hop to the E-Business Suite.
Example Scenario: The Deluxe “Zero Sign-On” Approach
A user logs on their PC using their Windows userid and password. Wanting to avoid real work, the user decides to file a long-overdue expense report for last year’s OpenWorld conference. He starts Internet Explorer, opens Favorites, and selects a bookmarked
link for the E-Business Suite’s Self-Service Expenses.
Self-Service Expenses starts up, and the user begins the process of assembling rationalizations to justify that $450 dinner at Jardiniere with their favorite Oracle blogger. (This is a fictional example, of course; nobody takes bloggers out to dinner)
We sometimes call this “zero sign-on” because the user never actually logged on to any Oracle systems at all; their Windows Kerberos ticket gave them an all-access pass to the E-Business Suite automatically.
Magic? What Really Happened?
Brace yourself: some of the following material might require a couple of passes to sink in.
The “deluxe” scenario above illustrates the following integrations:
- Microsoft Active Directory with Oracle Internet Directory 10g
- Microsoft Kerberos Authentication with Oracle Single Sign-On 10g
- Oracle Application Server 10g with the E-Business Suite
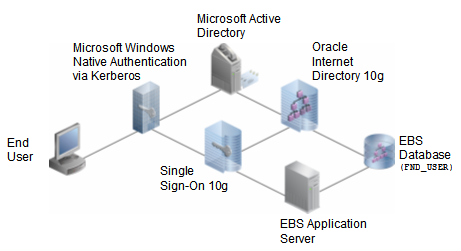
The user logged on to their PC, which authenticated them against Microsoft Active Directory. As part of that logon process, Microsoft Kerberos Authentication issued a valid Kerberos ticket to the user.
When the user attempted to access Self-Service Expenses via his bookmarked link, he was redirected to Oracle Single Sign-On 10g. Oracle Single Sign-On 10g recognized the Microsoft Kerberos ticket, issued its own Oracle security tokens to the user, and
redirected the user back to the E-Business Suite.
The E-Business Suite recognized the Oracle Single Sign-On 10g security tokens and looked up the user’s assigned Applications Responsibilities to ensure that he was authorized to access Self-Service Expenses. That done, it issued its own E-Business Suite
security tokens and then passed the user through to Self-Service Expenses without requiring any additional logons.
Integration with Microsoft Active Directory Only
Not everyone uses Microsoft Kerberos Authentication. A simpler integration option omits Kerberos and includes only Microsoft Active Directory and Oracle Internet Directory, like this:
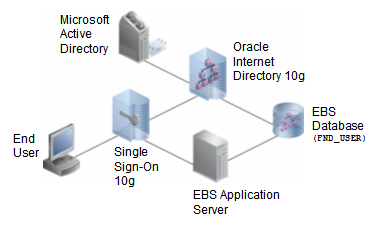
In this simpler architecture, when the user attempts to access Self-Service Expenses via his bookmarked link, he’s redirected to Oracle Single Sign-On OracleAS 10g. Single Sign-On displays a login screen and collects the user’s ID and password.
Single Sign-On passes the user’s supplied ID and password to Oracle Internet Directory for validation. Oracle Internet Directory uses the Windows NT
External Authentication plug-in (sometimes also called the Windows Native Authentication plug-in) to delegate user authentication to Microsoft Active Directory.
Microsoft Active Directory looks up the user’s ID and password in its database, and informs Oracle Internet Directory that this is an authenticated user. Oracle Internet Directory informs Single Sign-On that the user was successfully authenticated.
Single Sign-On issues the user a set of security tokens and redirects the user to the E-Business Suite. The E-Business Suite recognizes the Single Sign-On security tokens and looks up the user’s assigned Applications Responsibilities to ensure that he’s
authorized to access Self-Service Expenses. That done, it issues its own E-Business Suite security tokens and then passes the user through to Self-Service Expenses.
“Out-of-the-box” Third-Party LDAP Integration with Oracle Internet Directory
Due to the popularity of Microsoft Active Directory, Oracle Internet Directory provides a prebuilt connector out-of-the box, ready to use.
Oracle Internet Directory also provides a prebuilt connector for the SunONE (iPlanet) Directory Server, ready-to-use. You should note that Sun
(like Oracle, following its myriad recent acquisitions) has rebranded its identity management products, so there’s a new name for the Sun LDAP directory now. I’ll update this post with the latest name as soon as my Sun contacts provide me with that
information.
Synchronization of User Credentials with Third-Party LDAP Directories
If you’ve been paying close attention so far, you have likely gathered that user credentials need to be synchronized between the third-party LDAP, Oracle Internet Directory, and the E-Business Suite. The synchronization architecture looks like this:
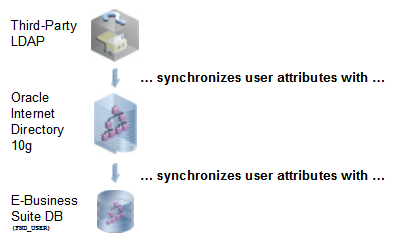
In this configuration, only the user name needs to be synchronized; the user’s password is stored in the third-party LDAP directory. None of the Oracle products need to store the user’s password, since they delegate user authentication to the third-party
LDAP solutions.
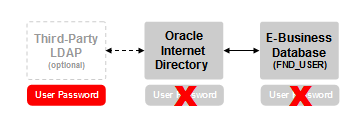
The key concept here is that user authentication is still separated from user authorization even when a third-party LDAP is in place.
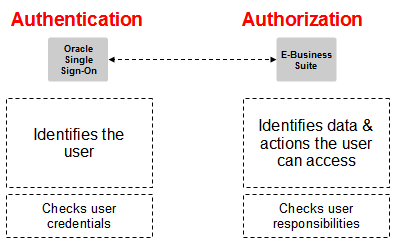
So, the E-Business Suite still grants authenticated users access to E-Business Suite protected content based on the users’ Applications Responsibilities, which are managed in the E-Business Suite exclusively.
Integration With Other Single Sign-On Solutions
It is also possible to integrate Oracle Single Sign-On 10g with other single sign-on solutions, including:
CA Netegrity SiteMinder
Biometric devices like fingerprint readers
Smartcards
PKI X.509 digital certificates
When integrated with other single sign-on solutions, a chain of trust is established between the third-party, Oracle Single Sign-On, and the E-Business Suite. Users logging on via the third-party single sign-on solution are passed through transparently to
Oracle Single Sign-On and the E-Business Suite.
Relax, It’s Easy and Fun
Well, maybe not… but at least it’s technically feasible. You might find it reassuring to note that a number of E-Business Suite customers are running this configuration in production already.
This is about as much detail as I think is appropriate for now. Feel free to post comments if you have questions about this topic.
References
For detailed instructions on how to integrate Single Sign-On and Oracle Internet Directory with Oracle E-Business Suite Release 12, see:
- Integrating Oracle E-Business Suite Release 12 with Oracle Internet Directory and Oracle Single Sign-On (Metalink Note 376811.1)
There are many more options for integration with the E-Business Suite, including options for linking OID userids to different E-Business Suite userids, and so on. If you’re really interested, I’d recommend a careful reading of the “Oracle Single
Sign-On Integration” section of this document:
Related Articles
