What is Transparent Data Encryption in the context of Cloud Services?
Transparent Data Encryption (TDE) in the cloud refers to the encryption of data at rest, meaning the data stored on the cloud infrastructure, without requiring any changes to the applications accessing it. In the case of databases it is a security feature that encrypts database files and log files, making the data unreadable to unauthorized users who might gain access to the physical storage.
Transparent Data Encryption (TDE) in Oracle HeatWave MySQL, a fully managed database service within Oracle Cloud Infrastructure (OCI), is a security feature that protects sensitive data at rest by encrypting database files at the storage level without requiring application changes. It provides industrial level data protection from unauthorized access while meeting compliance regulations like GDPR, PCI DSS and HIPAA.
Encryption at rest:
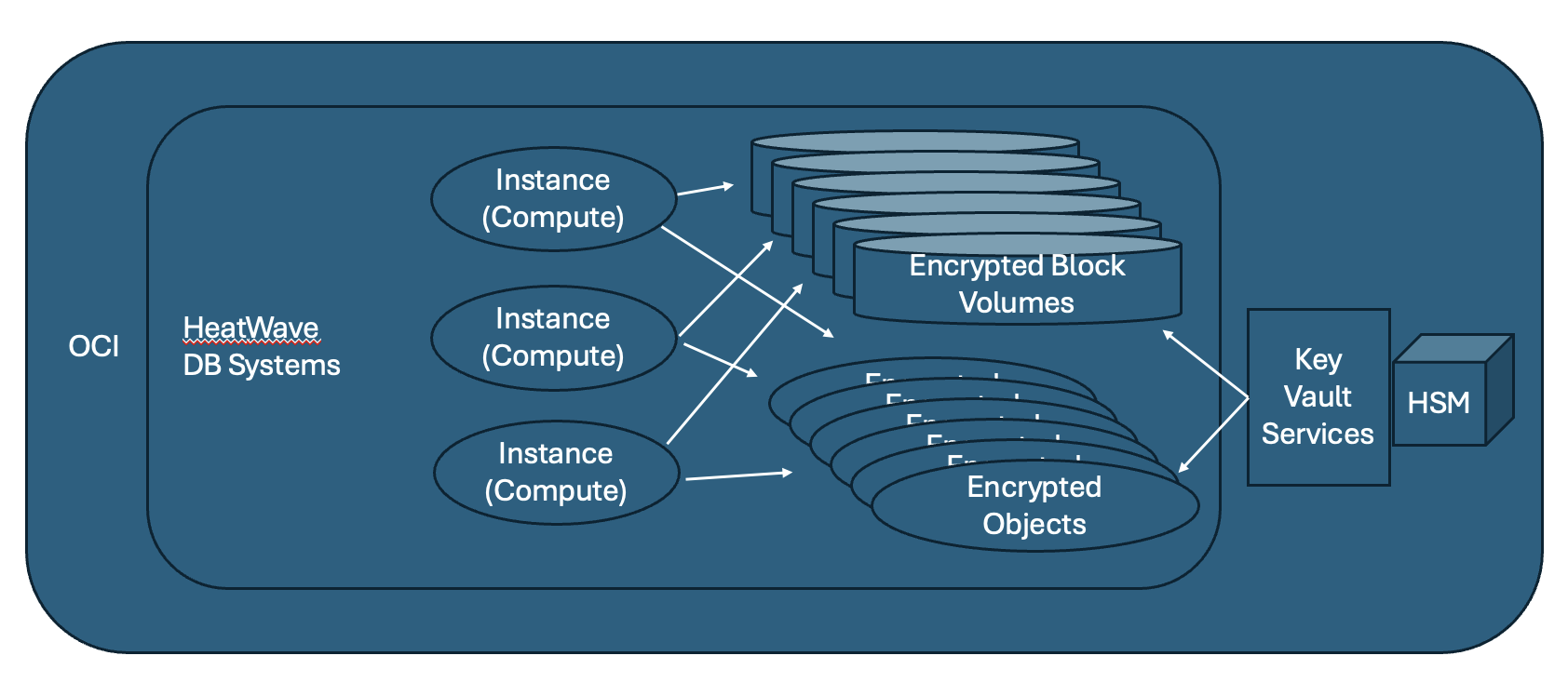
HeatWave MySQL DB systems uses OCI Block Volumes and Object Storage for all data persistence. Encryption at rest protects sensitive data stored in database files on disk by keeping it encrypted when not in use. When data is read, it’s automatically decrypted, so applications and users don’t need to make any changes to their workflows.
HeatWave MySQL DB systems also stores data in OCI managed Object Storage for database backups, source data for HeatWave Lakehouse and PITR log files. The data in Object Storage is also encrypted. By default, all data at rest including the backups are AES-256 bit encrypted (a strong, industry-standard encryption algorithm) with Oracle-managed keys, which are automatically rotated periodically for added security.
OCI HeatWave MySQL uses the Oracle-managed keys which are extremely secure. These keys are rotated every 90 days.
Here is a concise explanation of TDE in the context of HeatWave MySQL:
- Purpose: TDE safeguards data by encrypting physical database files, preventing unauthorized access if the storage media is compromised. It helps meet compliance requirements for regulations like PCI DSS and HIPAA .
- How It Works: TDE uses OCI Block Volume for Storage and OCI Object Storage
- Data is encrypted using industry-standard AES algorithms. Encryption and decryption occur in real-time during I/O operations and this is a default behavior.
- Transparency: Encryption is handled seamlessly with no changes to the application.
- Scope in HeatWave MySQL: Encrypts all data at rest .
- Block Volume Encryption: HeatWave MySQL DB systems uses OCI Block Volume Service for data storage, where all data and log files are stored in block volumes encrypted with Oracle-managed keys by default. Any data stored in OCI-managed Object Storage for HeatWave Lakehouse or customer enabled exports are also encrypted.
- Backup Encryption: Ensures that HeatWave MySQL database backups are also encrypted, protecting data even when backed up.
- Transparent Decryption: Authorized users or applications accessing data in HeatWave experience transparent decryption, requiring no additional steps once access controls are passed.
- Key Management:
-
Master Encryption Keys (MEKs) encrypt data encryption keys (DEKs).
-
MEKs Stored securely in Oracle Key Management Services. There are two options
- Oracle Managed Keys (default)
- Customer managed the keys for encryption using Oracle Cloud Infrastructure Vault services.
- Create your customer-managed keys in Oracle Cloud Infrastructure Vault.
- Once set up, you can assign a custom encryption key to your Heatwave DB System.
- For more details see OCI Key Management
-
Visually represented by this abstract and simplified view with Key Vault Services and Hardware Security Module (HSM).
Here are key points of TDE for MySQL EE and HeatWave MySQL
| Aspect | MySQL Enterprise Edition | HeatWave MySQL |
| Deployment | On-premises or self-managed cloud deployments, offering full control over configuration. | Fully managed cloud service on OCI, with TDE enabled by default. |
| Key Management | Supports multiple keyring plugins (e.g., keyring_okv, keyring_encrypted_file, keyring_aws) for integration with external key management systems like Oracle Key Vault, AWS KMS, or Gemalto SafeNet KeySecure. Requires manual setup of keyring plugins. | Uses OCI Vault for key management, which is tightly integrated and managed by Oracle. No manual keyring plugin configuration is needed |
| Configuration | Requires manual enabling of TDE via commands (e.g., adding ENCRYPTION=’Y’ to CREATE TABLE statements) and configuration of keyring plugins. | TDE is automatically enabled for all data-at-rest eliminating the need for manual configuration. |
| Maintenance | Users manage key rotation, plugin updates, and server maintenance, which may involve restarts during patching. | Key rotation and maintenance are handled by Oracle as part of the managed service, with restarts possible during maintenance windows. |
| Scalability and Integration | Offers flexibility for custom environments but lacks native integration with cloud-specific features like HeatWave’s in-memory analytics. | Optimized for OCI, with seamless integration with HeatWave’s analytics engine and automatic scaling |
| Compliance | Supports compliance with GDPR, PCI DSS, HIPAA, and SB 1386 via TDE and external key management. Users must ensure proper setup. | Also supports GDPR, PCI DSS, HIPAA, and SB 1386, with simplified compliance due to managed key storage in OCI Vault. |
| Cost | Requires a MySQL EE license, with additional costs for key management solutions like Oracle Key Vault. | Included in the HeatWave MySQL subscription, with no separate licensing for TDE or key management, but tied to OCI pricing |
Summary:
HeatWave MySQL on Oracle Cloud Infrastructure (OCI) provides a robust, secure, and compliance-focused solution for enterprise data protection. Utilizing Transparent Data Encryption (TDE) with AES-256 bit encryption, it secures data at rest by default with minimal performance overhead, while Oracle-managed keys rotate periodically to enhance security. Oracle’s stringent privacy policies ensure controlled and monitored access, keeping customer data private.

