IAM Domains / IDCS allow the definition of custom clients (called Applications) in IAM Domain / IDCS. The description and config is the same for IAM Domain / IDCS, only UI of the IAM Domain / IDCS would look different. There are several options for the definition of authorizations within applications like Scopes, Claims, User-attributes, Groups and Application Roles.
For using Scopes and Claims or User-attributes e.g. see this blog: https://blogs.oracle.com/coretec/post/protect-apis-with-api-gateway-using-idcsiam-jwt-with-scopes-and-claims
Using IAM/IDCS groups is trivial and not explained further, but just to remember they are global to the IAM/IDCS instance. For easier access during runtime the groups could be added as claim in Access Token (see also previous link).
This blog covers Application Roles. Application Roles are created for an App and are only valid in this context. There is one special Application Role type called Service Administrator, which is marked as admin=true through creation. This is for managing the App itself, e.g. if you want to assign the management of App config itself to a user or group. Custom Application roles are intended for Oracle Cloud Service app type see here. Although users can be added to custom app roles and queried.
Application Roles
You might have noticed that Application Roles are used ootb with several PaaS services like Analytics Cloud Service. If used through a Cloud-Service the admin UI is different: a further tab is visible to manage the Application Roles. Application Roles are pre-defined in case of Oracle Cloud-Services.
Sample with Cloud-Service:
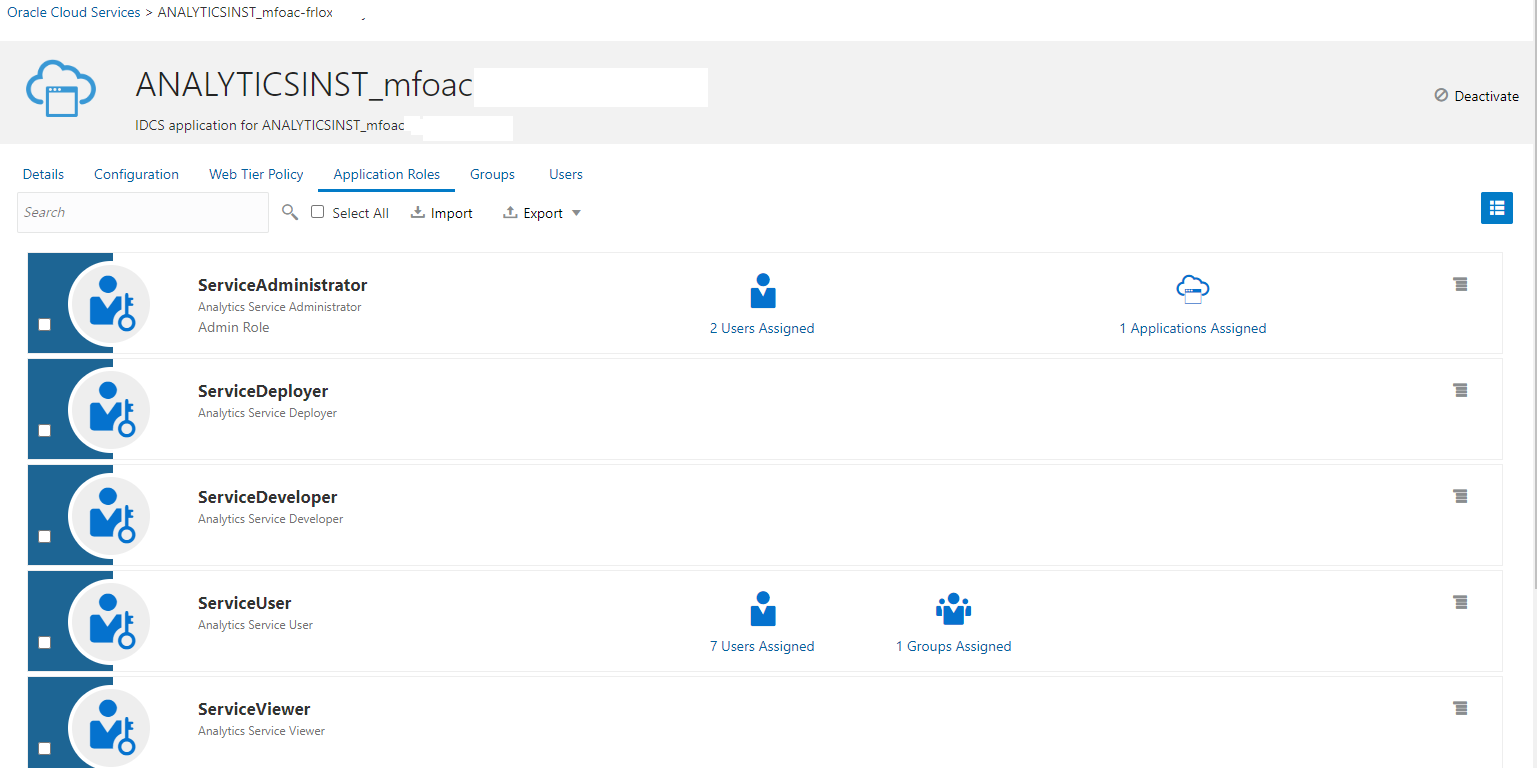
and even an Cloud-Service could be extended with custom Application Roles (here 2x, names start with Test):
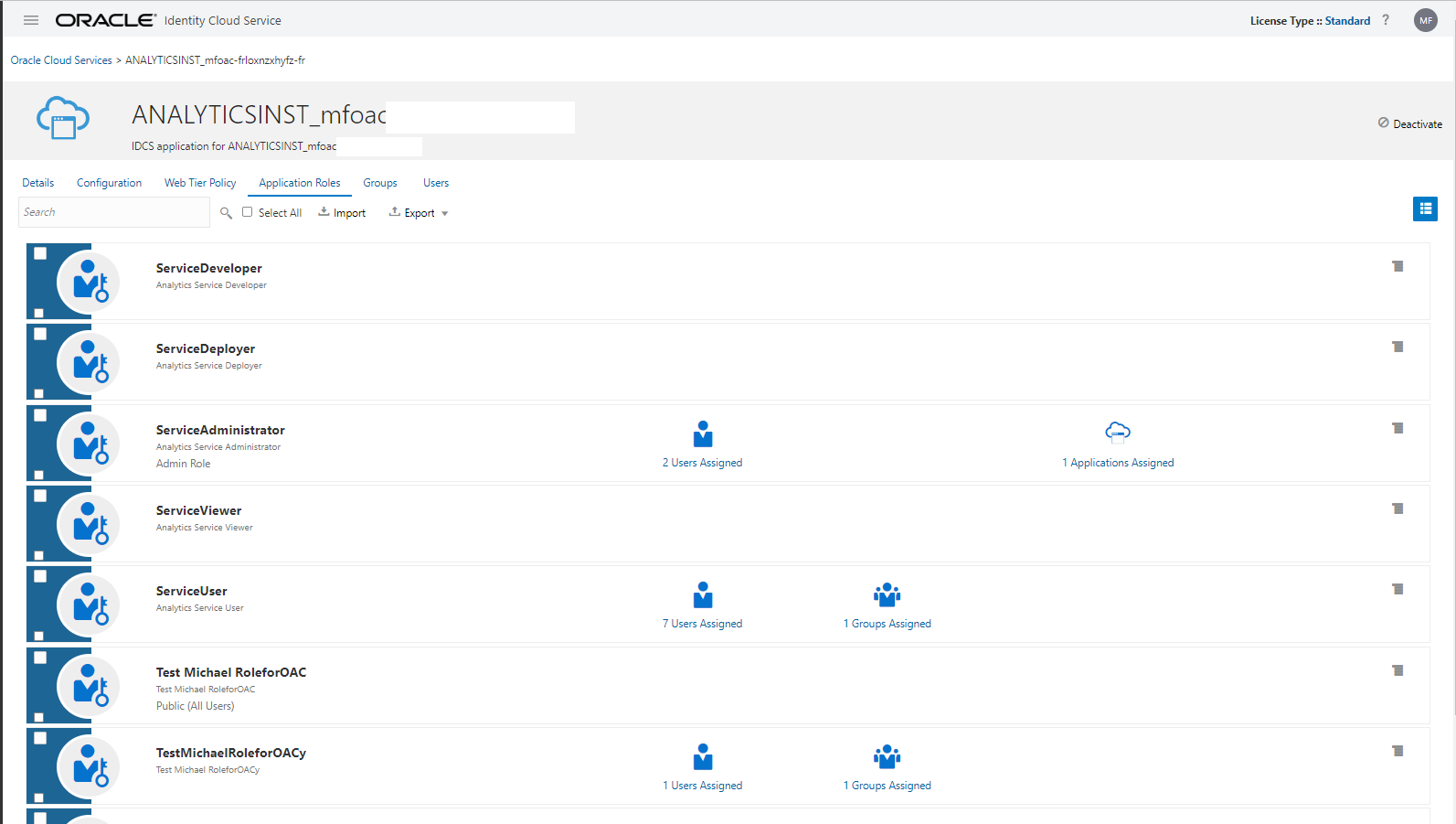
The predefined Application Roles are correlated with some functionality in the PaaS Service as explained in the corresponding docu, below for Oracle Analytics.
Added Application Roles are not wired but give the possibility for further use in calling applications as they could be queried during runtime.
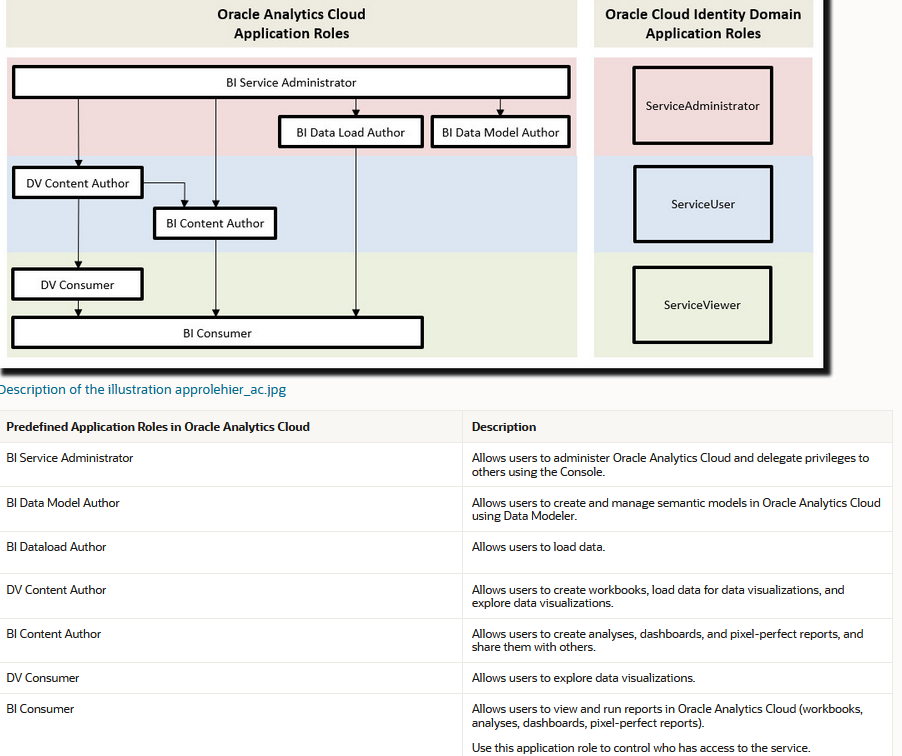
more on the predefined Oracle Analytics roles here.
Custom Application Roles
An Application Role is always in the context of an application. This is reflected when making changes because you have to know the
Application (AppID) and the Application Role (AppRoleID). Using Application Roles has to be decided before the creation of an App.
As this setting can not be made in the UI you have to create the App via API. This blog uses REST API.
The setting to enable Application Roles can not be changed after creation.
App without Application Roles:

App with Application Roles.
The difference is the additional Application Roles tab and the User/Group handling is is now in the application role tab:
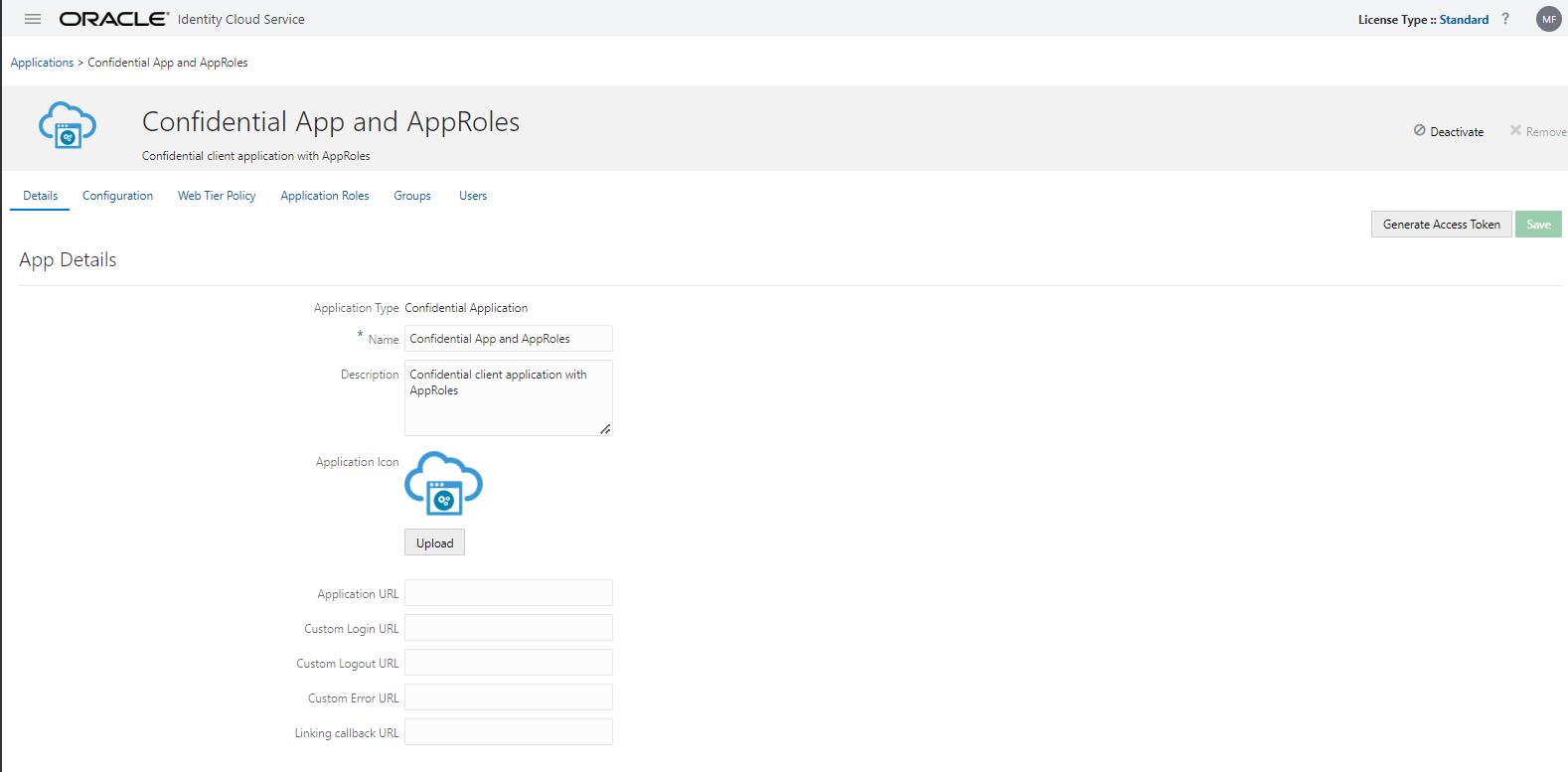
Setup:
1. Create App for use of Application Roles (minimal settings and already activated):
curl –location –request POST ‘https://idcs-9f7a0xxx.identity.oraclecloud.com/admin/v1/Apps’ \
–header ‘Content-Type: application/json’ \
–header ‘Authorization: Bearer eyJ4NXQjUzI1NiI…’ \
–data-raw ‘{
“schemas”: [“urn:ietf:params:scim:schemas:oracle:idcs:App”],
“basedOnTemplate”: { “value”: “CustomWebAppTemplateId” },
“displayName”: “Confidential App and AppRoles”,
“description”: “Confidential client application with AppRoles”,
“clientType”: “confidential”,
“isUnmanagedApp”: true,
“isOAuthClient”: true,
“active”: true,
“allowedGrants”: [“client_credentials”]
}’
2. Create Application Roles
App Roles can not be created via UI, so here again REST (needs AppID, see value:
url –location –request POST ‘https://idcs-9f7xxx.identity.oraclecloud.com//admin/v1/AppRoles’ \
–header ‘Content-Type: application/json’ \
–header ‘Authorization: Bearer eyJ4N…’ \
–data-raw ‘{
“displayName”: “Custom Role1”,
“adminRole”: false,
“description”: “Custom Role1”,
“public”: false,
“app”: {
“value”: “1729053..”
},
“schemas”: [
“urn:ietf:params:scim:schemas:oracle:idcs:AppRole”
]
}’
3. Assign Users or Groups to Application Roles:
Users and/or IAM/IDCS groups can be assigned via UI of the App or upload or REST calls.
Here for upload: https://docs.oracle.com/en/cloud/paas/identity-cloud/uaids/importing-users-and-groups-oracle-application-roles.html
After this step it looks like (here one direct user assignment and two group assignments):

Users are the users assigned directly and assigned through groups. Click on Users opens a pop-up windows which differentiates these two types of assignment.
The tabs with Groups and Users is different to the Application Role tab but shows only the assignments in Application Roles in a different way:
Here the group tab (shows the assigned groups in Application Roles):

Here the user tab (shows the direct assigned users and users through groups in Application Roles):

4. Query these Information via API
Query the AppRoles of an App (here without admin role)
curl –location –request GET ‘https://idcs-9f7xxx.identity.oraclecloud.com//admin/v1/AppRoles?filter=app.value eq “d4f53…” and adminRole eq false’ \
–header ‘Authorization: Bearer eyJ4NXQjUz…’
Query the Granted AppRoles to an IAM domain/IDCS group
url –location –request GET ‘https://idcs-9f7xxx.identity.oraclecloud.com//admin/v1/Grants?filter=app.value eq “d4f53…” and grantee.type eq “Group”‘ \
–header ‘Authorization: Bearer eyJ4NXQjUz…’
and to user
url –location –request GET ‘https://idcs-9f7xxx.identity.oraclecloud.com//admin/v1/Grants?filter=app.value eq “d4f53…” and grantee.type eq “User”‘ \
–header ‘Authorization: Bearer eyJ4NXQjUz…’
or more general queries like /admin/v1/Grants?filter=grantee[value eq “{{user_id}}” and type eq “User”]