Most enterprises have an established authentication system which is their leading system for authentication of users and optionally handling authorization.
In newer platforms like Oracle Cloud Infrastructure (OCI) a common requirement is to integrate authentication within the existing IAM. In OCI there is a choice: to use either local, isolated login or to integrate in one or more leading authentication systems or both. Integration is supported on standards and templates.
The most commonly used authentication integration is SAML. SAML relies on two parties, the Service Provider who requests an authentication and the Identity Provider who assures an authentication.
However, connecting an IDP and using this IDP for Authentication or SSO implies in the default configuration that a logout from OCI triggers a global logout from IDP as well. So a user has to do a full logon next time, persistent session information would have been deleted. MFA will also be retriggered if configured on IDP.
In this post, we guide you through the process to configure the IDP integration without using a global logout. EntraID will be used as an example in the screenshots.
OCI SAML SSO Configuration
OCI allows configuration of different authentication options. They can work in parallel to allow a user to choose their prefered method or it can be customized depending on used applications, risk level, domain etc. Amongst the authentication options is the configuration of SAML. SAML relies on two parties, an Identity Provider who assures the login and a Service Provider who uses the assurance and maps it to a SP user. SAML Identity Provider (IDP) will be used in this blog as Authentication or SSO.
OCI IAM Doc: https://docs.oracle.com/en-us/iaas/Content/Identity/home.htm
SAML Config for using an IDP for OCI: https://docs.oracle.com/en-us/iaas/Content/Identity/identityproviders/add-saml-identity-provider.htm
SAML enables besides the SSO the configuration of the so called global logout. In this case the SAML SP calls after a logout in the SP the logout URL from the IDP. In OCI configuration the cascading logout is the ootb config when using metadata.xml file from the IDP:
https://docs.oracle.com/en-us/iaas/Content/Identity/identityproviders/add-saml-identity-provider.htm#
The following blog describes customization of the logout process to not cascade the logout of the SAML IDP. This configuration option can be used for both, new IDP configs and existing ones.
Check Status Quo:
Assumption is you have created or maintained the IDP with the import of the metadata.xml file. Then the configuration of IDP would look like this and cascade the global logout:
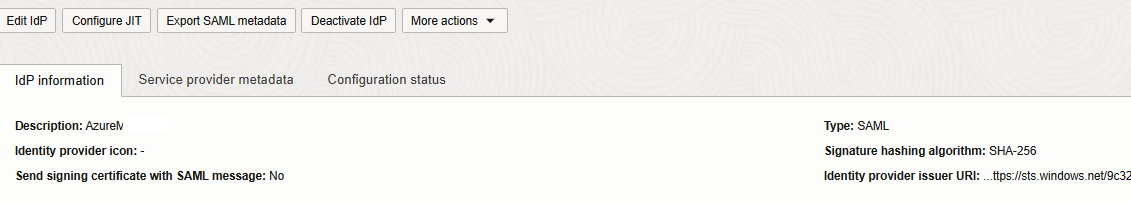
In difference the config looks like this if you already disabled the cascading logout (aka global logout).
It is noted in the description field that global logout is disabled.

This can be checked using an API Call.
At the moment there are 2 options for using the API, IAM domain CLI (based on API Key) or IDCS (based on OAuth). Both have an overlapping set of functionalities.
There is a postman collection which provides a quick start on using the IDCS based API. If using this, domain/IDCS license has to be checked as postman counts as an external app and there are different limits of numbers of Apps per domain type. IDCS based API can be used for IDCS based tenants and IAM based ones.
Howto IDCS : https://docs.oracle.com/en-us/iaas/Content/Identity/tutorials/rest/rest_postman.htm
Domain Limits: https://docs.oracle.com/en-us/iaas/Content/Identity/sku/overview.htm
HowTo CLI: https://docs.oracle.com/en-us/iaas/Content/Identity/tutorials/cli/cli_identity-domains.htm
For the case that the IDCS Rest API should be used:
As call a https get can be used. Here the number of returned attributes is reduced as not all are of interest.
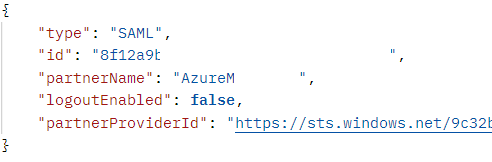
Get <domainURL>/admin/v1/IdentityProviders/<idpid>?attributes=partnerName,partnerProviderId, logoutenabled
Sample Result (internal attribute for global logout is called logoutEnabled):
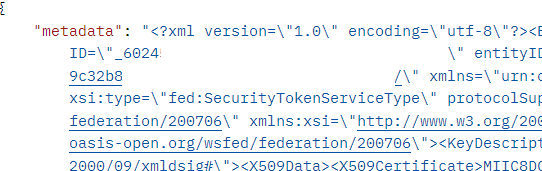
Also the metadata could be retrieved. This call returns only a result if metadata import has been used. If not the single attributes like cert have to be requested in the call.
A call looks likes this: <domainURL>/admin/v1/IdentityProviders//<idpid>?attributes=metadata
Sample Result
….
Change Config to disable cascade of logout
As all values are available with API a change could be done with API. This might be the only way when using e.g. terraform provider. Using this way requires to not only toggle the logoutEnabled attribute but also requires to modify the other attributes like removing metadata and setting signing attributes etc.
The easiest way is using the UI. Select the IAM domain where the SAML federation is configured and select the IDP. In my case AzureM:
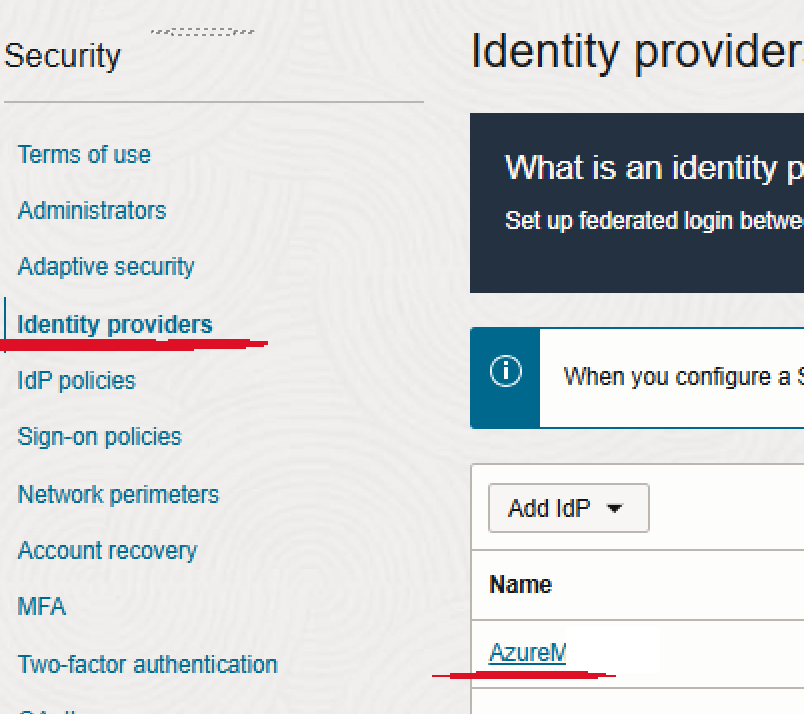
Go for Edit in IDP:

Switch to “Enter IDP Data” (marked here with a red circle) and provide the information from IDP. These data can be retrieved from the metadata.xml file.
The last input field is Enable Global Logout. Leave this empty if you do not want to cascade.
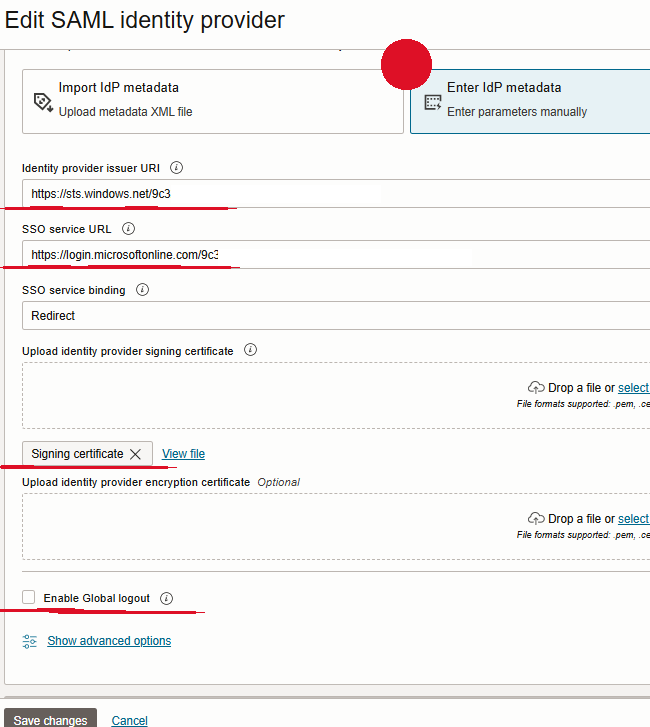
The input fields underlined in red are the minimum input values the federation needs. If browser-based uploads are not allowed which are required in the UI for the certificate then API can be used instead. Not showing here but the call is documented in this link:
https://docs.oracle.com/en/cloud/paas/iam-domains-rest-api/op-admin-v1-identityproviders-post.html
or with CLI: https://docs.oracle.com/en-us/iaas/tools/oci-cli/3.54.4/oci_cli_docs/cmdref/iam/identity-provider/create.html
Switching to the manual input mode allows you to toggle the setting afterwards also in an existing configuration.
Troubleshooting
- Global Logout config is not shown:
Switch in UI to “Enter IDP data manually” - Toggle of global logout has no effect:
The metadata file needs to be overwritten with either a modified one with no logout links and no logout config (not shown in this blog) or the config has to be entered manually and saved.
Check setting of metadata attribute in API. If still set then delete the value - IDP can not be modified:
Check if the user used (OAuth client or OCI IAM user) has appropriate entitlements. IAM has roles and user needs to be assigned, e.g. IAM Domain Admin. See:
https://docs.oracle.com/en-us/iaas/Content/Identity/roles/understand-administrator-roles.htm - Creating a test IDP raises error like “duplicate IDP” :
SAML requires distinct entity-IDs within one IAM domain / IDCS. Another IAM domain (e.g. a Free one) could be created for testing if numbers of free domains are not exhausted.