Most enterprises have an established authentication system which is their leading system for authentication of users and optional authorization. For managing the access to an application or system and for the privileges or roles within an application or system a central governance system is used. This can be automated with a provisioning system or done manually by e.g. a helpdesk. In the blog IAM is used as abbreviation for these functionalities.
In new platforms like Cloud, applications like ERP or systems like VMs have introduced a requirement to integrate these at least for authentication within the existing IAM. In the case of Oracle Cloud Infrastructure (OCI) there is a choice: to use either local, isolated login or to integrate in one or more leading authentication system or both. Integration is supported on standards and templates.
The most commonly used authentication integration is SAML. SAML relies on two parties, the Service Provider who requests an authentication and the Identity Provider who assures an authentication. The trust between these parties is build based on signing.
However, there may be different cases for different users. An App login may be different than OCI console login. The user may bookmark access or use some dashboards or portals from his Identity Provider. So, this requires organizations to configure in their SAML configuration both cases: calling login from an App/OCI console or from an Identity provider. The first one is called Service-Provider initiated, the second case is called Identity Provider initiated.
In this post, we guide you through the process to configure IDP initiated login with EntraID as an example.
OCI SAML SSO Configuration with Entra ID
OCI allows amongst other options to configure Identity Provider (IDP) as Login/SSO Authentication method. The ootb config with OCI initiated login is described in this tutorial:
https://docs.oracle.com/en-us/iaas/Content/Identity/tutorials/azure_ad/sso_azure/azure_sso.htm
The generic OCI IAM Doc can be found here: https://docs.oracle.com/en-us/iaas/Content/Identity/home.htm
and SAML Config for using an IDP for OCI is described in the following link: https://docs.oracle.com/en-us/iaas/Content/Identity/identityproviders/add-saml-identity-provider.htm
The configuration as described in above tutorial works fine and uses the OCI Gallery App in EntraID and OCI metadata of an IAM domain or an IDCS instance. This is a configuration is an extract of the config in EntraID which is created in this way:
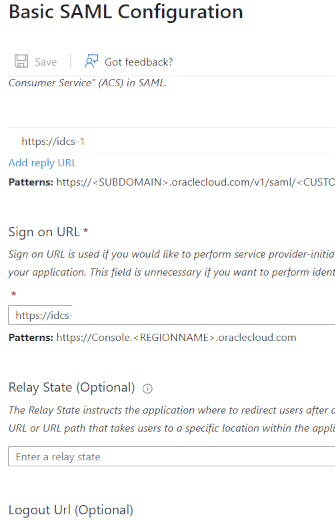
Expected values not provided within the OCI metadata file have a short description in the EntraID template how the input could look like.
Some suggestions for the values like the “Sign On URL” (this is the one for IDP initiated SSO) can be improved to get a more seamless SSO experience. This configuration is covered in this blog.
With additional security checks when an URL in the browser for OCI is provided the automation of the IDP initiated login needs to be refined in some cases to point to the right target. Means as mentioned in the template the configuration with “console.Regionname.oraclecloud.com” may interrupt the flow because it is not clear for the OCI console which auth option for the SSO flow is intended. In one tenant e.g. the same entity ID (here Entra ID) can be used in several domains at the same time. Consequence is the flow stops until the user makes the choice. As the IAM domain might entitle the same EntraID user for different authorizations it makes sense to do this differentiation. Sample for having same EntraID two times is using an IAM testdomain and an IAM proddomain for the same user.
History: The Entra ID template was developed in the time of having IDCS as PaaS service and OCI Console native IAM. Therefor a further config is not foreseen in the template.
The Sign on URL is mandatory for EntraID config and therefore marked with a star (Screenshot from Entra ID template):

EntraID does not prove if this config works, it only checks for valid URL syntax.
Example for IDP initiated login
For an user in EntraID a dashboard is available which shows accessible applications, like OCI, for the authenticated user. Generic link is: https://myapps.microsoft.com/
A screen for the user with one App may look like this:
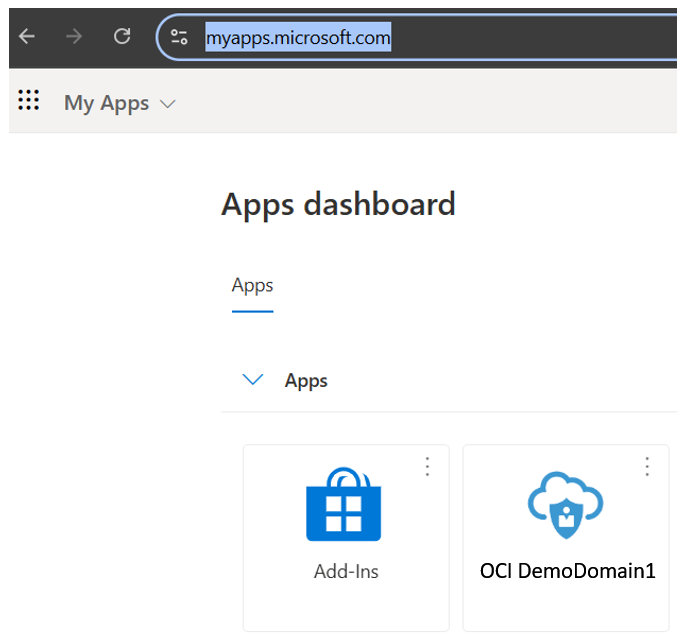
OCI DemoDomain1 is here the name for the App which integrates OCI. The integrated OCI tenant uses two domains, one is the default one and one is called DemoDomain1. To get the IDP initiated flow working the config of the “Sign on URL” needs:
- Specification for the Service Provider (SP), here OCI, to start the SSO flow:
https://idcs-abc123.identity.oraclecloud.com/fed/v1/sp/initiatesso
idcs-abc123 has to be replaced with your domain URL - Specification which IDP should be used in the domain:
providerid=https://sts.windows.net/efg567
https://sts.windows.net/efg567 has to be replaces with EntraID entity (e.g. from metadata of EntraID) - Sepcification where to go after successful login in OCI:
returnurl=https://cloud.oracle.com/home?tenant=tenantname&domain=DemoDomain1®ion=eu-amsterdam-1
replace tenantname with your tenantname, replace DemoDomain1 with your OCI IAM domainname, replace eu-amsterdam-1 with the home region of your tenant - IMPORTANT: do a URL encode of the whole string, looks somehow like:
https:// idcs-abc123.identity.oraclecloud.com/fed/v1/sp/initiatesso?providerid=https%3A%2F%2Fsts.windows.net%2Fefg567
%2F&returnurl=https%3A%2F%2Fcloud.oracle.com%2Fhome%3Ftenant%3Dtenantname %26domain%3DDemoDomain1%26region%3Deu-amsterdam-1 - Copy the URL encoded string in the Entra ID input field of “Sign On URL”
For test login to https://myapps.microsoft.com/ with a user who is assigned to the EntraID Application. Click on the OCI icon, this opens a new window and starts the flow. At the end of the flow the user gets the console screen of OCI which may look like this:
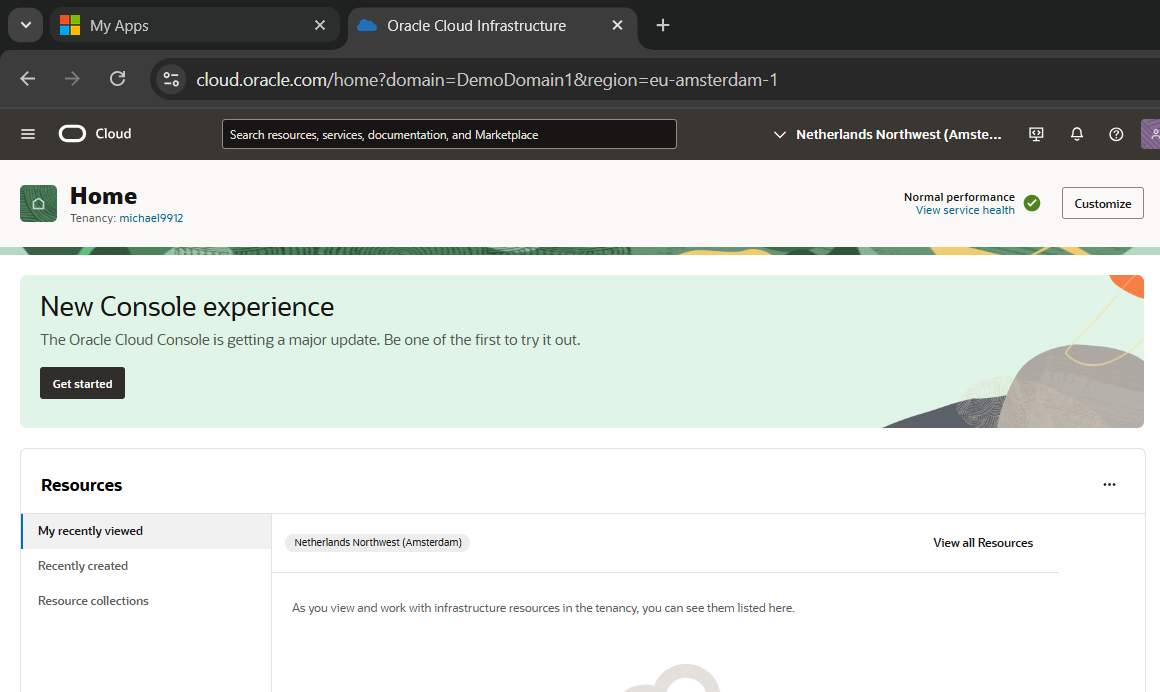
Other targets in OCI can be configured in a similar way by using a different config for the returnurl, e.g. my-profile to redirect the user to his profile after successful login.
Troubleshooting
- SSO works not at all:
Please check if gallery Entra ID template was used. Means from the screenshot the “Oracle Cloud Infrastructure Console” Application
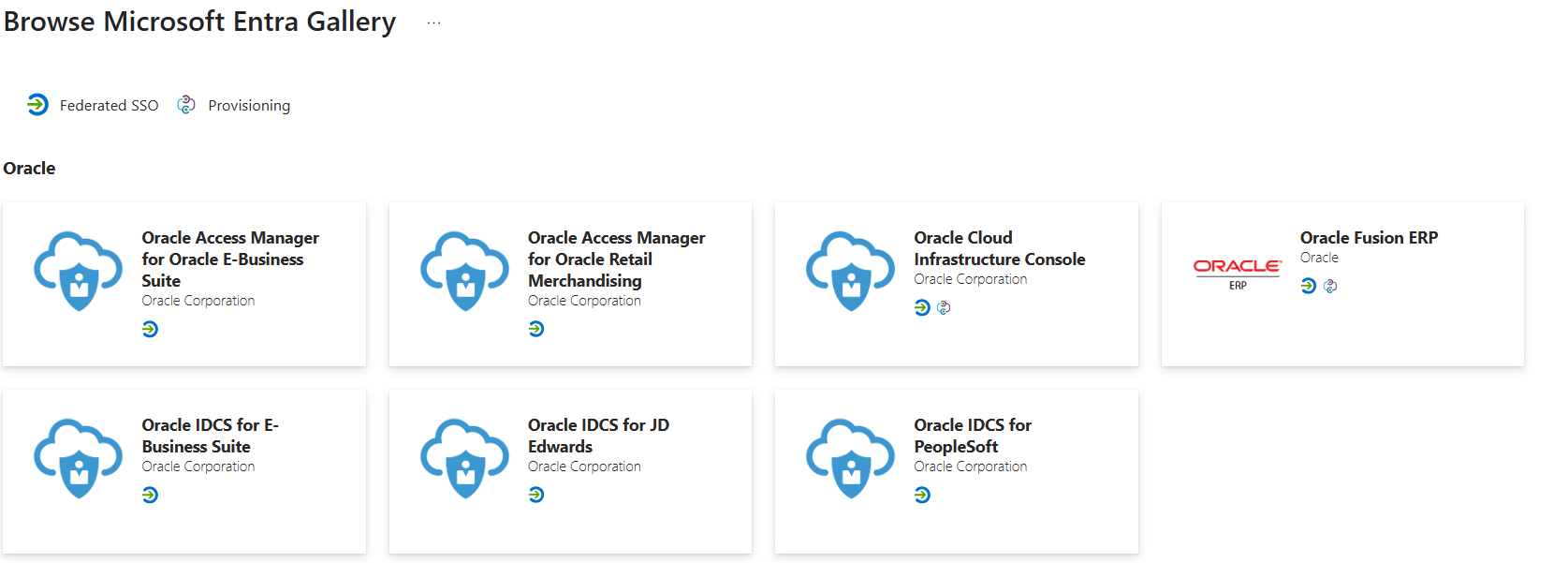
- SSO works but throws an error:
Go for the ctx message in the error screen of OCI (needs read of source of webpage, e.g. with the Devtools from Browser) and decode the value to get a hint in the error (e.g. user not found, user not unique, certificate expired etc.
- SSO works but stops at OCI login selector of the intended IAM domain:
- The Sign On has to be URL encoded, see above step 4
- The Sign On URL misses or has a miss-spelling of region, domain or home URL
- The Browser relies on “old” cookies. Go for an incognito window to get a clean environment and test or clear all cookies and test. The flow is extremely sensitive to cookies.