The latest update to Oracle Access Governance introduces powerful AI automations to enhance operational efficiency and help organizations achieve their compliance goals. Additionally, built-in Access Guardrails help streamline access bundle creations, enforce policies, and can reduce risk.
AI for Access Bundles accelerates application onboarding
Oracle Access Governance expedites application onboarding with AI access bundle creation, mining, and recommendations. This automation simplifies entitlement management, uncovers optimal access patterns, and uses generative AI to assign meaningful descriptors for access bundles. By reducing manual input, it enables a faster and more secure access control model by keeping the permission catalogue concise. As seen in Figure 1, with a few simple clicks, an Application Owner can accept the access bundle recommendation or manually override it.
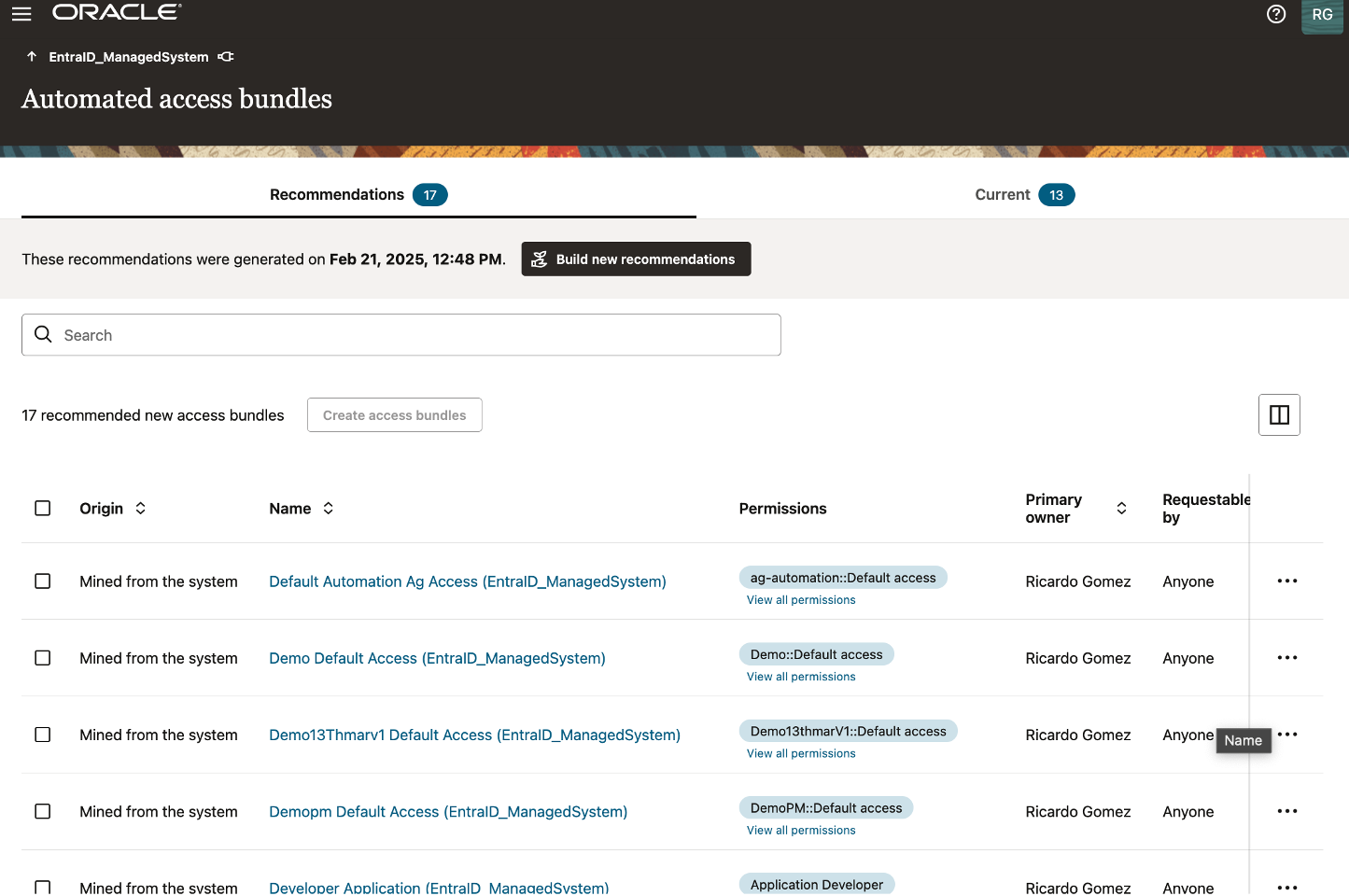
Enhancing Security with Access Guardrails
Oracle Access Governance also introduces Access Guardrails to proactively enforce access constraints based on user attributes and existing permissions (Figure 2). Access Guardrails enable application owners and security administrators to prevent unauthorized access by helping ensure that requests comply with predefined policies before they are even submitted. Additionally, they provide approvers with critical contextual information, allowing them to make better informed decisions during the approval process.
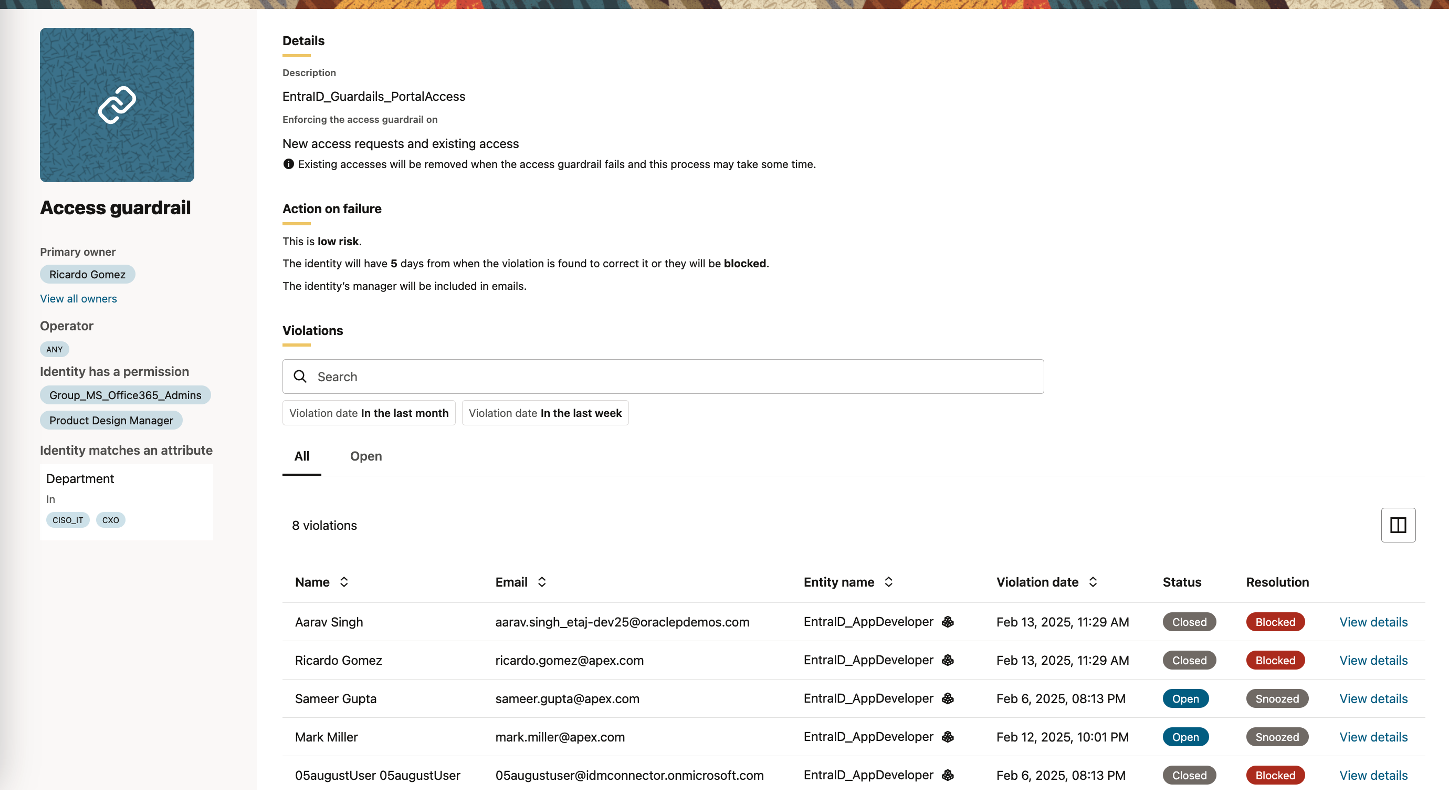
By incorporating risk categorization (Figure 3), organizations can establish granular access control policies and define appropriate remediation actions based on the level of risk associated with an access request. High-risk access can be automatically blocked, while low-risk scenarios can be flagged for further review or marked as violations. This proactive enforcement reduces security gaps, minimizes the risk of excessive access, and helps organizations achieve their compliance goals.
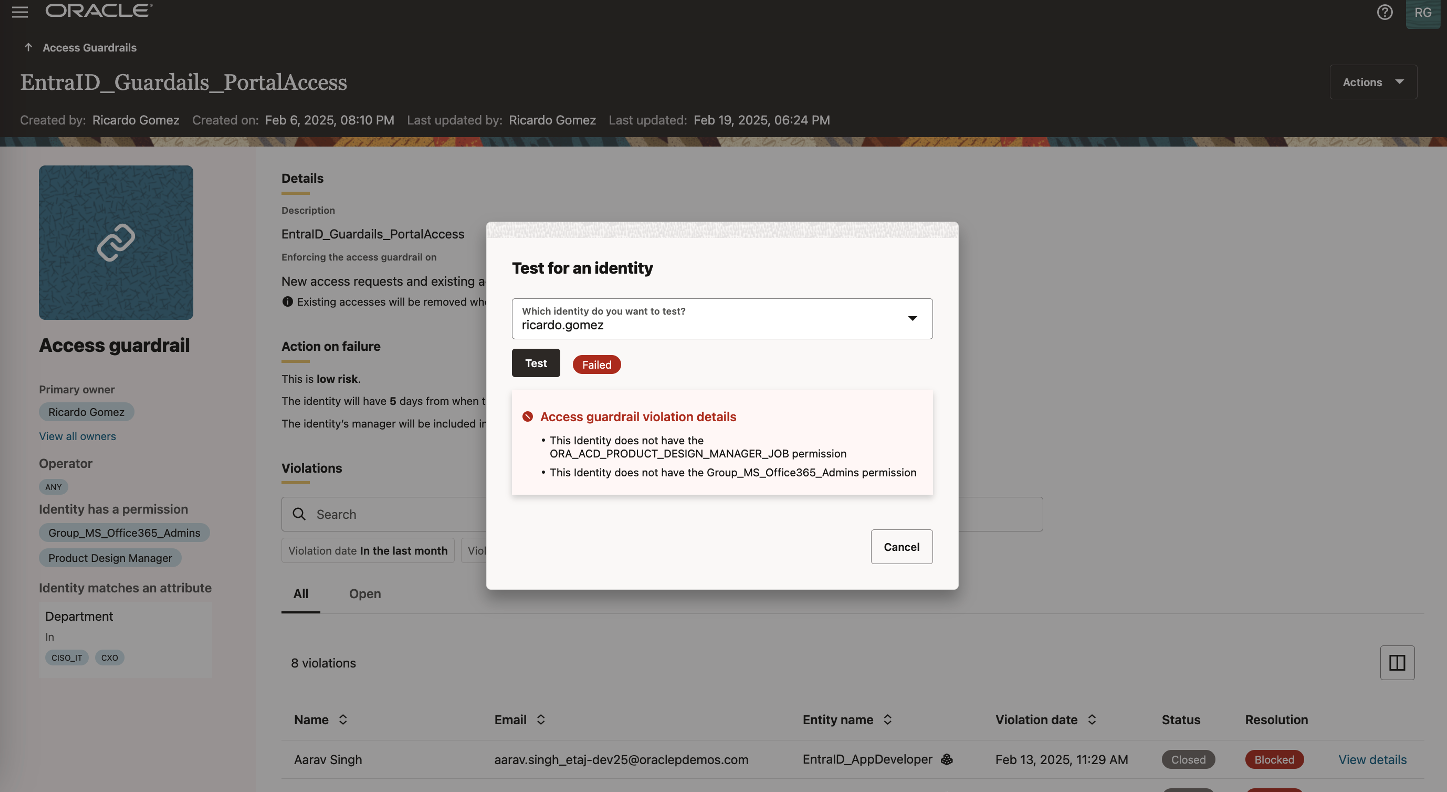
Embedding Access Guardrails as part of the request process stops unauthorized access before it is granted, reducing the reliance on downstream remediation efforts such as periodic audits and system-wide Segregation of Duties (SOD) reviews. Hence, Access Guardrails strengthen security and governance while also reducing operational overhead. Additionally, Access Guardrail Violations Reports provide insights into pertinent security risks (Figure 4).
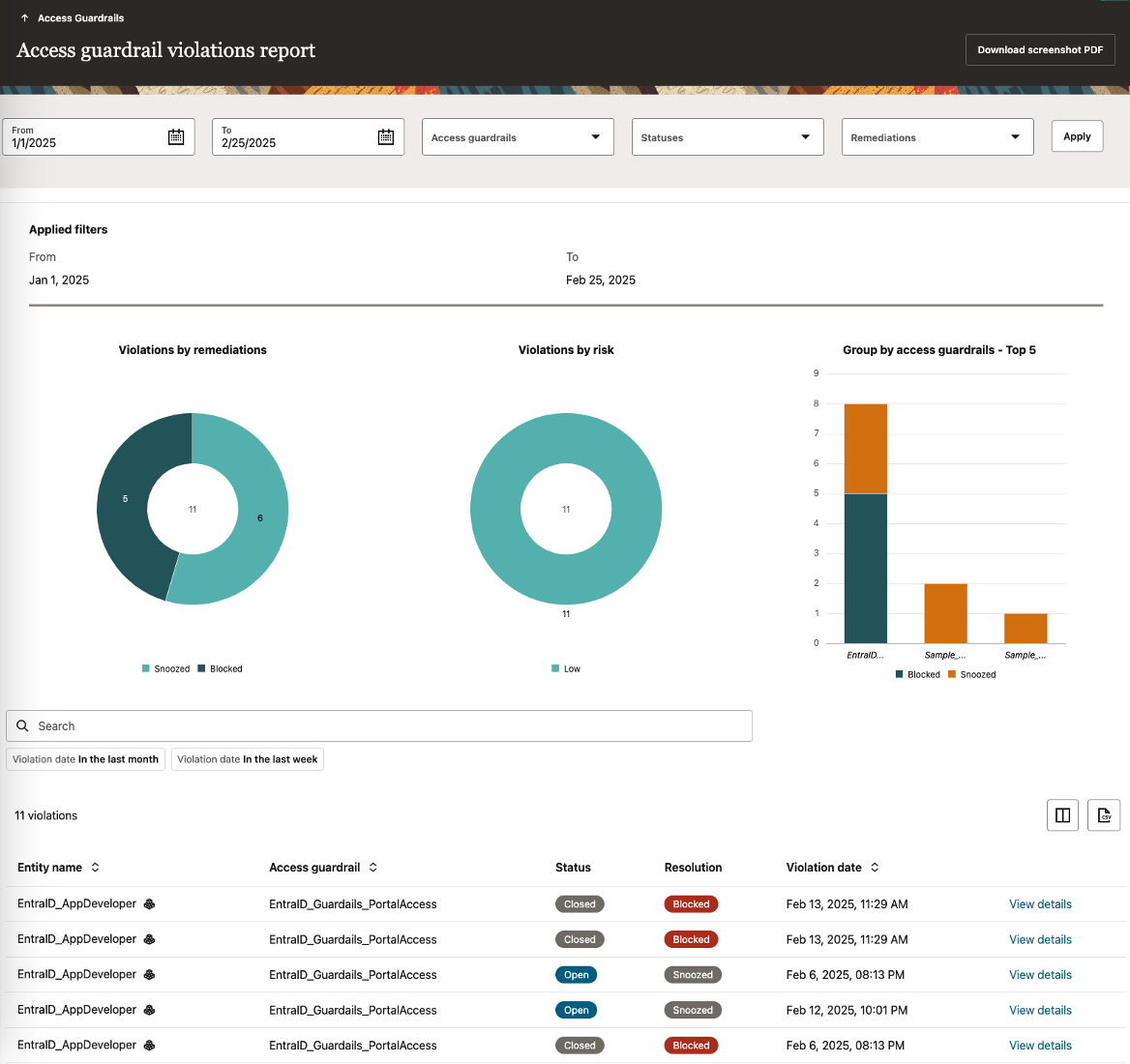
Mitigating Security Risks with Immediate Access Revocation
Managing access throughout the user lifecycle is critical for maintaining security and compliance adherence. The latest updates to Oracle Access Governance bring improvements to account lifecycle management, such as manually revoking access, activating or disabling accounts, and managing user accounts more efficiently. These enhancements help reduce administrative overhead and equip response teams with tools to quickly act on access requests.
With the Emergency Termination feature in Access Governance, service desk and security teams can instantly revoke user access across all managed systems in critical situations. HR system terminations may have processing delays, leaving systems vulnerable to access that is no longer authorized. However, with Oracle Access Governance, organizations can proactively revoke access, protecting sensitive data even before formal HR updates are completed.
Expanded Identity Orchestration Capabilities
New integrations:
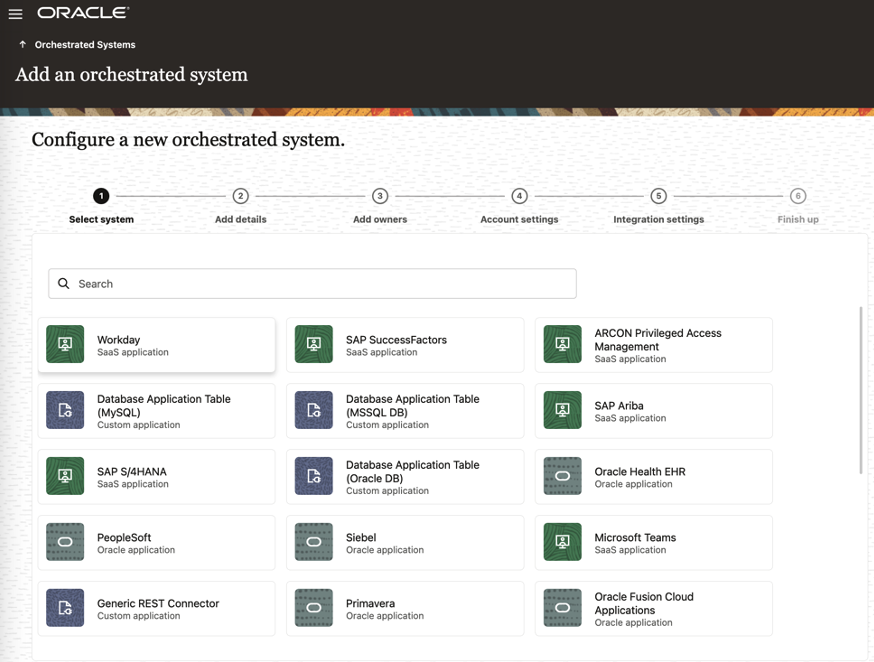
Oracle Access Governance further expands integrations (Figure 6) with critical platforms, allowing for identity orchestration across a broader range of enterprise systems. While Access Governance has native integrations with other Oracle products, Access Governance also extends governance to enterprise applications with direct connectivity, handling identity lifecycle management across Oracle and non-Oracle environments.
- Workday & SAP SuccessFactors: Access Governance supports Workday and SAP SuccessFactors, offering out-of-the-box integrations for these services as authoritative sources and/or managed systems. Workday and SAP SuccessFactors are leading Human Capital Management (HCM) solutions, widely used for employee data management, payroll, and workforce planning. Organizations using Workday or SAP SuccessFactors for HR-driven identity management can now automate identity provisioning, role assignments, and access certifications directly within Oracle Access Governance.
- ARCON Privileged Access Management (PAM): With privileged accounts potentially posing significant security risks, Access Governance now integrates with ARCON PAM via API-based provisioning and management. ARCON PAM is a third-party security solution designed to control, monitor, and manage privileged access to critical IT infrastructure, reducing the risk of insider threats and unauthorized access. This enables automated onboarding, role-based access control, and lifecycle management of privileged accounts within ARCON PAM, helping organizations centralize privileged access governance, enforce security policies, and mitigate insider threats.
Enhanced transformation rules
Oracle Access Governance introduces improved logic and validation capabilities, which provide advanced, flexible transformations of identity and account values. With this update, application owners can use Java (GraalVM) code and newly introduced helper functions to create sophisticated transformation rules. This increased customization helps consistently enforce complex organizational policies during identity provisioning and reconciliation, reducing manual intervention and improving data accuracy.
Conclusion
The latest updates to Oracle Access Governance provide automations to help organizations achieve compliance adherence, increase operational efficiency, and reduce costs across enterprise systems.
AI-powered access bundle automation accelerates app onboarding, and Access Guardrails enforce security policies to mitigate unauthorized access. Likewise, immediate access revocation improves security responsiveness, and integrations with Workday, SAP SuccessFactors, and ARCON PAM further expand and unify governance across Oracle and non-Oracle systems. Additionally, enhanced transformation capabilities further simplify policy enforcement and reduce manual effort.
As security challenges grow, Oracle Access Governance continues to evolve, providing organizations with intelligent, automated, and scalable access control solutions. For more information on Oracle Access Governance, see the following resources:
- Oracle Access Governance
- Oracle Access Governance Product Tour
- Datasheet: Oracle Access Governance
- Oracle University: Implementing Oracle Access Governance
- Hands on: Oracle Access Governance LiveLabs
- What’s New for Oracle Access Governance
- Oracle Identity Governance and Administration Integrations Exchange
- Blog: Enhanced visibility into access with Oracle Access Governance
- Blog: Oracle Access Governance optimizes identity orchestration and enables unlimited integrations with generic connectors
- Blog: Oracle Access Governance adds support for OCI group membership reviews, orphan account management, and more integrations
- Blog: Oracle Access Governance adds identity life-cycle management and expanded targets
- Developer Coaching: Oracle Access Governance

