For government agencies considering a cloud solution for their critical workloads, having a clear understanding of the shared responsibility and how to work alongside a cloud service provider (CSP) is vital to helping ensure a secure cloud environment. Additionally, misunderstanding the shared responsibility model has its own severe implications for cloud customers, resulting in potential data leaks, misconfigured services, and more. This blog aims to clear some of the confusion surrounding the shared responsibility model, providing a high-level overview of some of the key responsibilities for Oracle Cloud Infrastructure (OCI) and Oracle Government Cloud customers.
What is the shared responsibility model in Oracle Government Cloud?
The shared responsibility model is a framework that outlines what OCI provides and what Oracle Government Cloud customers must actively manage, configure, and test. The shared responsibility model helps define how customers can work with Oracle to help ensure data security, government compliance, resilience, and more in their Oracle Government Cloud solution. In short, OCI is responsible for the security of the cloud, and the customer is responsible for security in the cloud.
The shared responsibility model helps Oracle Government Cloud customers:
- Streamline government compliance: leverage our accredited cloud environments—like our FedRAMP High-accredited US Government Cloud—compliance tools, and landing zones
- Establish a more secure cloud framework: configure Oracle’s enterprise-grade Identity and Access Management (IAM) tools at scale
- Define responsibilities: a clear division of responsibilities helps customers avoid security blind spots in a customer’s cloud solution
OCI offers a wide array of features, tools, and resilient infrastructure purpose-built for sensitive workloads as part of a shared responsibility model for cloud operations.
OCI’s role and responsibilities
As a trusted CSP serving the public sector, OCI provides customers with a secure, compliant, and highly available foundational cloud infrastructure to host sensitive workloads. However, customers retain responsibility for how they design, plan, architect, secure, and operate their applications and data in the cloud, including the incorporation of high availability and disaster recovery (DR) strategies and managing identity and access policies. While not an exhaustive list, the following section gives a broad overview of the responsibilities OCI typically covers in an Oracle Government Cloud solution.
1. Resilient cross-region infrastructure
Oracle Government Cloud regions are separated into fault domains (FD), which are groupings of hardware and infrastructure, within one or more data centers called availability domains (AD). A collection of ADs in a single geographic location makes up a region.
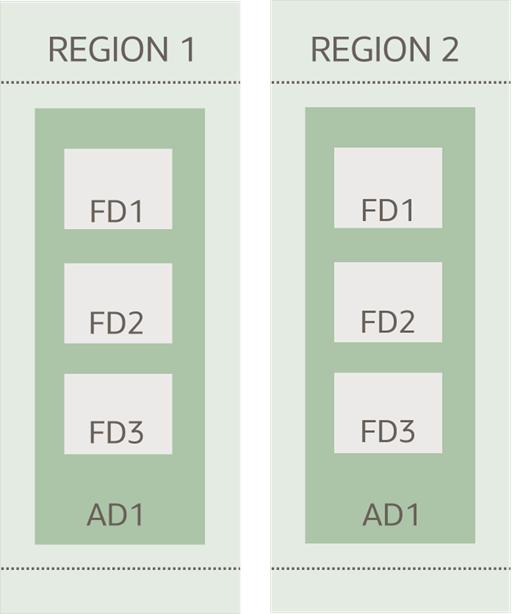
As part of Oracle’s two-region strategy, we provide Oracle Government Cloud customers with the following:
- Physically and logically isolated regions for high availability
- Redundancy at the network, power, and data center levels for resiliency
- Region-to-region communication capabilities
- Region’s subscription capability, which allows for DR capabilities
2. Disaster recovery capabilities
Oracle Government Cloud offers powerful DR capabilities that enable customers to rapidly restore their applications to full operational status after a disaster, which can occur in various forms such as a natural disaster, a network outage, or an application failure. We offer services such as:
- Cross-region block volume backups, which enable block volume replication across regions
- Object storage replication, which enables replicating objects to a subscribed region
- Oracle Database Tools such as Recovery Cloud Service, Data Guard, and GoldenGate
These are tools, not configurations. It’s the customer’s responsibility to design and implement a DR strategy based on best practices, test it regularly, and ensure the application architecture supports failover.
3. Identity and Access Management
Oracle’s essential enterprise-grade IAM provides authentication and authorization for all Oracle cloud resources and services. Below are some of the features of Oracle IAM:
- Role-based access control (RBAC), which controls user access to tasks that would normally be restricted to superuser
- Multi-factor authentication (MFA), which requires the use of more than one factor to verify a user’s identity
- Support for external Identity Providers (IdPs) with Security Assertion Markup Language (SAML), Open Authorization (OAuth), or Lightweight Directory Access Protocol (LDAP)
- Common Access Card (CAC) authentication support with identity domain
4. Compliance & security tooling
Government agencies must adhere to strict security and government compliance requirements in an evolving landscape. To help customers remain compliant and help keep protect sensitive data safe from cyberattacks, Oracle Government Cloud offers tools, features, and landing zones for compliant security architecture, including:
- Log management and audit trails
- Threat detection and response (e.g., Oracle Cloud Guard)
- Encryption at rest and in transit (enabled by default with the option to disable)
- Cybersecurity Maturity Model Certification (CMMC) Level 2 and Level 2 Informational Guides
- CMMC Level 1 and Level 2 Controls Checklists
- OCI Core Landing Zone: Includes baseline configurations and rules delivered using a standardized Infrastructure-as-Code (IAC) template designed to help meet CMMC requirements
- Oracle’s Cloud Native Secure Cloud Computing Architecture (SCCA) Landing Zone: Using cloud native infrastructure services, the automation provided by the SCCA Landing Zone enables Department of Defense mission owners to establish a compliant security architecture in just a few hours or days, instead of months
Oracle ensures compliance and security tools are compliant; the customer ensures their usage is compliant. Customers must turn on these tools and tune them for their workloads, review audit logs, and react to incidents.
Customer responsibilities
The customer and their cloud architects building on the cloud have vital responsibilities. This section describes common areas where government customers must act in an Oracle Government Cloud.
1. Designing for resilience
OCI provides highly available native services such as load balancers, redundant networks, and multi-FD regions for resilience. To build a resilient application in an Oracle Government Cloud environment, the customer must:
- Architect stateless services so that any service instance can handle requests interchangeably
- Use active-active or active-passive replication by following an appropriate DR approach
- Perform regular DR tests to validate assumptions
- Build architectures that are compliant with relevant agency requirements
While OCI is responsible for resiliency of the cloud, the customer is responsible for resilience in the cloud. Customers make the decision to replicate data across regions based on the mission criticality of the application or data hosted in the cloud. If data is deemed critical that cannot sustain an outage, it’s the customer’s responsibility to ensure data replication across regions to ensure backup strategies.
2. Managing IAM at scale
IAM services are only as good as how they’re configured. While OCI provides IAM, it’s the customer’s responsibility to configure roles, permissions, federations, and group policies. It’s imperative to remember that a misconfigured policy can expose sensitive data, even in a Federal Risk and Authorization Management Program (FedRAMP) High-certified cloud environment.
The customer must:
- Federate existing IdPs (Okta, Active Directory, etc.) if they need to integrate with their existing identity service provider
- Rotate keys and credentials in a timely manner
- Establish least-privilege access models based on zero trust principles
- Create additional domains as needed to further control access
Neglecting IAM hygiene in Oracle Government Cloud environments can result in privilege escalation, data exfiltration incidents, or being non-compliant with relevant regulations.
3. Data classification & encryption strategy
Oracle cloud encrypts data with customer-managed or Oracle managed keys. The customer determines:
- Which data needs Key Management Service (KMS)-level protection using Oracle Vault
- Retention policies and archival practices
- Which ports need to be open on the network and the necessary gateways to enable data coming into internal networks (VCN)
- The lifecycle of sensitive or mission-critical datasets
4. Continuous compliance
It’s the responsibility of the customer to ensure continued compliance with relevant regulatory agencies. While Oracle Government Cloud solutions are compliant with a number of programs—for example, US Government Cloud is accredited at FedRAMP High, and Oracle US Defense Cloud is accredited at Defense Information Systems Agency (DISA) Impact Level 2/4/5 (IL2, IL4, and IL5)—the customer does not inherit the accreditation.
To ensure continued compliance with relevant regulations, customers must:
- Map application controls to compliance frameworks for continued compliance
- Monitor configuration drift
- Patch application layer vulnerabilities
- Submit evidence during audits
Read more about Oracle global cloud compliance.
Real-world analogy: building a house
To use a construction analogy, let’s think of Oracle cloud as a “residential builder” and a government agency as the “homeowner.” As the builder, Oracle provides:
- A solid foundation: Infrastructure as a Service (IaaS)/Platform as a Service (PaaS)
- Reinforced walls: security infrastructure
- Fire alarms: monitoring tools
- Locks on the doors: IAM
As the homeowner, the customer decides:
- Home furnishings: Compute, Oracle Kubernetes Engine (OKE)
- Where to store valuables: Object, Block, File Storage
- Who gets a key to the house: IAM, Vault
Conclusion: tools do not equal implementation
In Oracle Government Cloud, Oracle and the customer work in conjunction to help ensure the customer’s cloud environment is secure and resilient. We give the customer the regions, keys, alarms, and network. The customer must unlock resilience by building across regions, enable logging, secure identities, and test DR strategies.
Oracle’s job is to offer secure, compliant, and high-performing building blocks. The customer’s role is to assemble and operate these blocks responsibly. This is the heart of the shared responsibility model. By understanding and embracing the shared responsibility model in Oracle Government Cloud, customers can ensure their cloud environments are compliant, agile, and prepared for threats, whether natural, operational, or cyber.
