Original post can be found on the Oracle Cloud Security blog.
I’m happy to start my Oracle Cloud blogging journey by talking about OCI Bastion service, a new, cloud-native security service that was released recently on Oracle Cloud Infrastructure (OCI). OCI Bastion is a fully managed service providing secure and ephemeral Secure Shell (SSH) access to private target resources in OCI, such as compute hosts (Linux or Windows), MySql DB, ATP, and OKE v2 clusters. The service is provided at no additional cost within your OCI tenancy and aligns with Oracle’s strategy to deliver cost effective solutions that are easy for organizations to implement and address their security responsibilities.
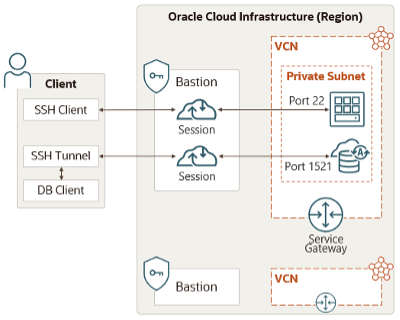
Let’s start with how OCI Bastion service enables the organizations to get rid of the complex networking architecture that traditionally involves jump hosts or bastion hosts to protect access to their private target resources. OCI Bastion service, like other security services offered by OCI, enables organizations to create and maintain a stronger security posture. For example, OCI Bastion is essential to access private target resources in tenancies with stricter resource controls. You can use a bastion session to access compute instances in compartments that are associated with a Maximum Security Zone, as these instances cannot have public endpoints.
Provisioning
The documentation and architecture center are great places to get started with this service. Like any other OCI cloud-native service, OCI Bastion integrates with OCI Identity and Access Management (IAM) and allows the organization to control who can manage a bastion or a session.
Setting up OCI Bastion is a very straight-forward process, whatever the private target resource is. There are only three high-level steps to follow:
- Create a bastion
- Create a session in the bastion to the private target resource
- Use the session metadata to login to the private target resource
That’s it! It is as simple as that! Now, let’s look at each of these steps in detail.
Creating a bastion
OCI Bastion is a regional service, so in order to connect to a private target resource in a region, a bastion must be created in the same region. Bastion provisioning happens within minutes. Each bastion can then provide access to target resources within a particular VCN. When creating a bastion following the steps in the documentation, you should ensure that the bastion name you provide is unique per region and per tenancy. The target subnet must either be the same as the target resource’s subnet, or it must be a subnet from which the target resource can be accessed.
Features like Maximum Session Time-to-Live (TTL) and CIDR Block Allowlist provide an additional layer of security. CIDR Block Allowlist lets you restrict the IP address ranges from where the SSH connections are allowed to access the private target resources. This list should be as narrow as possible, to limit the IP addresses that can access the private target resources. Maximum Session TTL refers to maximum amount of time that any session on this bastion can remain active. TTL at the bastion level will help ensure that none of the sessions created in the context of that bastion have TTL more than the bastion.
Creating a bastion session
The next step is to create a bastion session. The OCI Bastion service allows you to create two types of sessions. Here are some key differences between them.
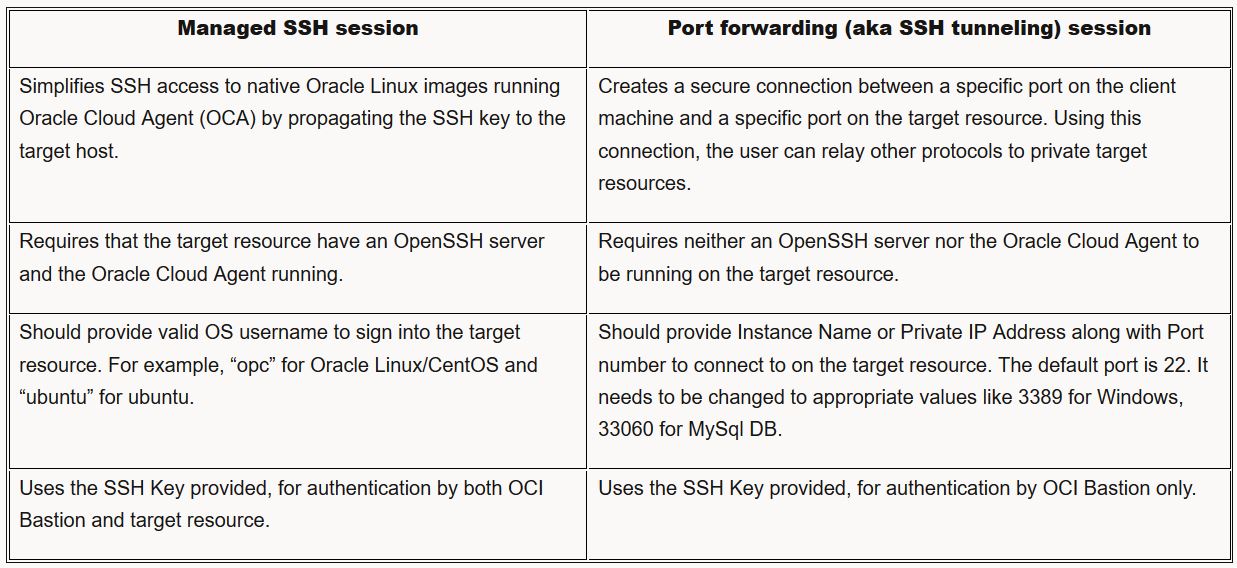
Note: As stated in the documentation, the Bastion plugin is disabled by default and must be enabled before creating a Managed SSH session. If you see errors like “Plugin Bastion not present for instance <instance_ocid>”, make sure to configure a Service Gateway and NAT gateway in the VCN of the private target resource, as this is used by the Bastion plugin. Furthermore, be aware that when enabling the plugin, it takes some time to transition from disabled -> invalid -> enabled.
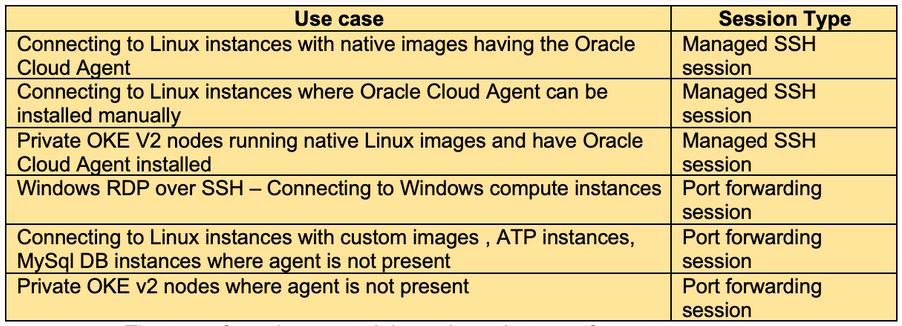
With the session type determined, create a session in the bastion. The Maximum Session Time-to-Live is configurable at the session level as well (default is what is set at bastion level; the minimum is 30 mins).
Use the session metadata to login to the private target resource
The last step is to connect to the private target host through Bastion using the session that we just created. Following the steps in the documentation, we will have to retrieve the SSH command from session metadata, replace the placeholders with actual values, and then run the SSH command to login to the private target resource.
Before you begin this step, ensure that the ingress rule is added on the target subnet (i.e., the one you used when you created the bastion) to allow the TCP traffic into the subnet from the private endpoint IP address of the bastion. Specify the port based on the target resource, e.g., 22 for Linux, 3389 for windows, 33060 for MySql and so on.

Sample SSH command for Managed SSH session
ssh -i <privateKey> -o ProxyCommand=”ssh -i <privateKey> -W %h:%p -p 22 ocid1.bastionsessionoc1.iad.amakec3@host.bastion.us-ashburn-1.oci.oraclecloud.com” -p 22 opc@10.0.1.157
Sample SSH command for Port forwarding session
ssh -i <privateKey> -N -L <localPort>:10.0.1.240:3389 -p 22 ocid1.bastionsession.oc1.iakeakeadp@host.bastion.us-ashburn-1.oci.oraclecloud.com
In the sample SSH commands, the OCID corresponds to that of the bastion session used for the connection to the private target resource and the second part of the host FQDN (in the above example, host.bastion.us-ashburn-1.oci.oraclecloud.com) is region specific, as OCI Bastion is a regional service.
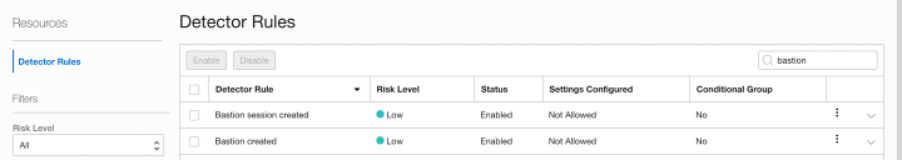
One of the benefits of the OCI Bastion service is that, being a cloud-native service, it integrates seamlessly with other services like OCI Audit, OCI Events, OCI Monitoring, OCI Notification and so on. OCI Bastion is also tightly integrated with Oracle Cloud Guard, where the activity detector rules can be enabled to detect bastion creation and bastion session creation actions by end users. You can refer to Paul Toal’s blog post New inclusive services that help deliver a more secure cloud for more details on how the out-of-the-box integration provided between these OCI native services make OCI customers more secure.
To summarize, OCI Bastion is a fully oracle-managed, regional service, provided at no additional cost. The service allows you to create SSH sessions to access private target resources within OCI.
If you want to try out OCI and OCI Bastion service, remember you can sign up for a free trial, which not only gives you access to try out many of the OCI services, but also gives you access to our Always-Free Oracle Cloud Free Tier services.
