Original Publish date : 9/21/2020
Below are the steps to create an internal CA using keystore and sign your server certificate :
Pre-requisites:
– Install JDK 15.
– Use the keytool commands to create an internal CA and a self-signed certificate for your server.
– You can then create a certificate request (CSR) for your self-signed certificate and sign it with the internal CA you created earlier.
Commands Used:
Detailed Steps:
Step 1:
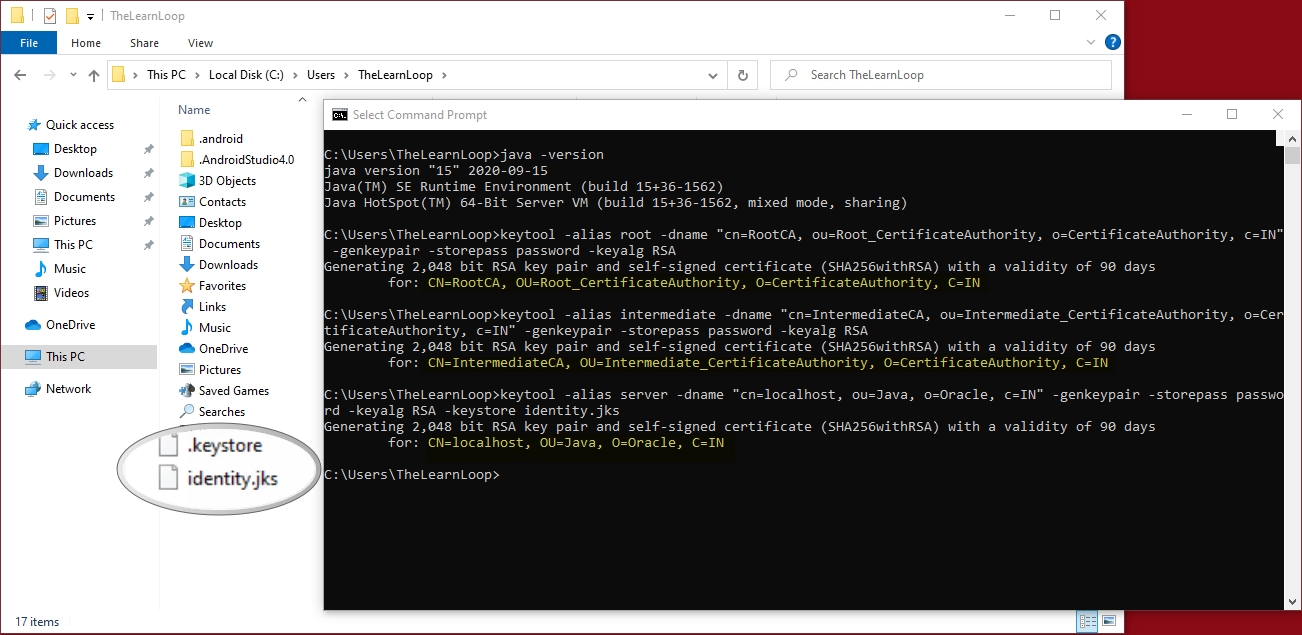
Create 3 self-signed certificates :
CA_Root
- keytool -alias root -dname “cn=RootCA, ou=Root_CertificateAuthority, o=CertificateAuthority, c=IN” -genkeypair -storepass password -keyalg RSA
CA_Intermediate
- keytool -alias intermediate -dname “cn=IntermediateCA, ou=Intermediate_CertificateAuthority, o=CertificateAuthority, c=IN” -genkeypair -storepass password -keyalg RSA
Server Certificate
- keytool -alias server -dname “cn=localhost, ou=Java, o=Oracle, c=IN” -genkeypair -storepass password -keyalg RSA -keystore identity.jks
Step 2:
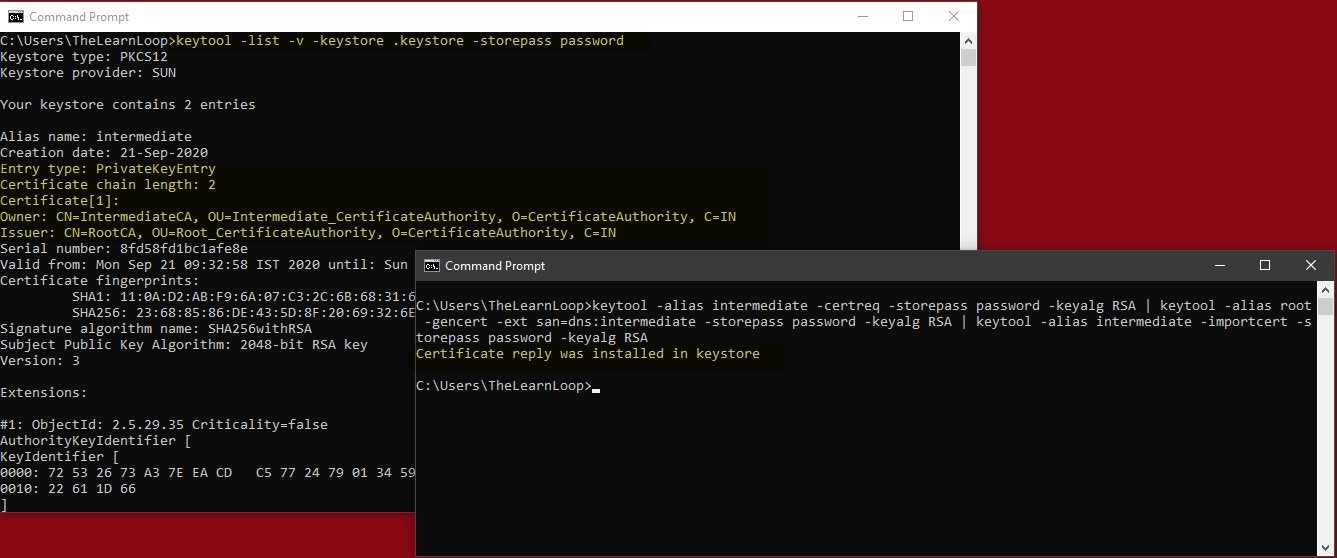
Create a certificate request (CSR) for CA_Intermediate
Sign it with CA_Root using the gencert option.
Then use the importcert option to create a chain of root and intermediate :
- keytool -alias intermediate -certreq -storepass password -keyalg RSA | keytool -alias root -gencert -ext san=dns:intermediate -storepass password -keyalg RSA | keytool -alias intermediate -importcert -storepass password -keyalg RSA
Step 3:
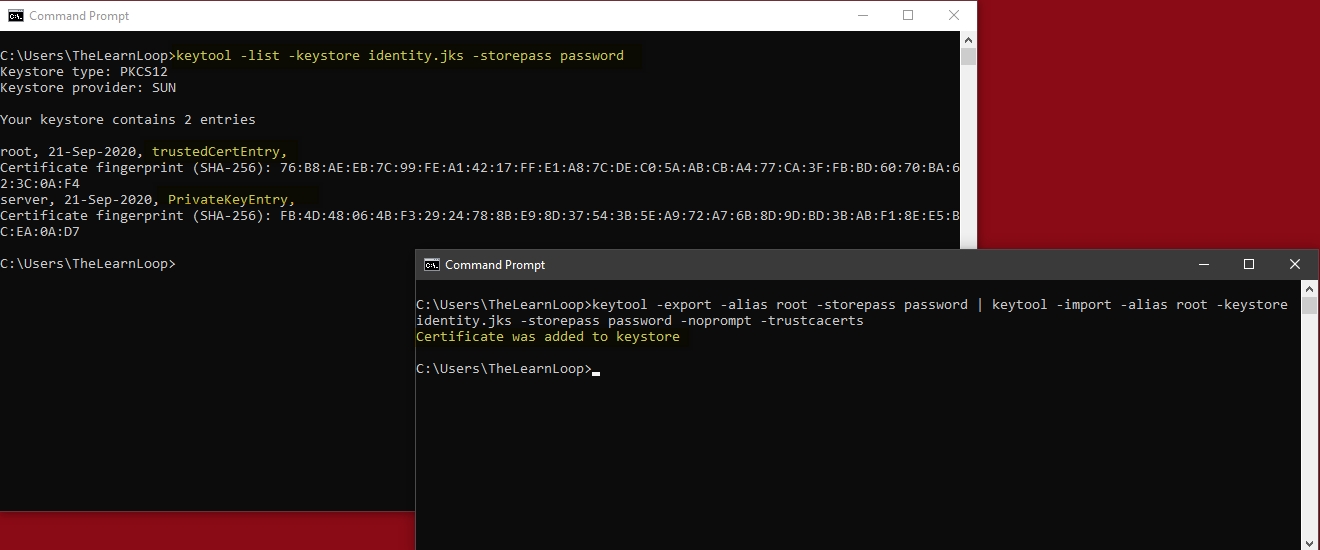
Export the root certificate of CA_Root and import it to identity keystore which has your self-signed server certificate.
- keytool -export -alias root -storepass password | keytool -import -alias root -keystore identity.jks -storepass password -noprompt -trustcacerts
Step 4:
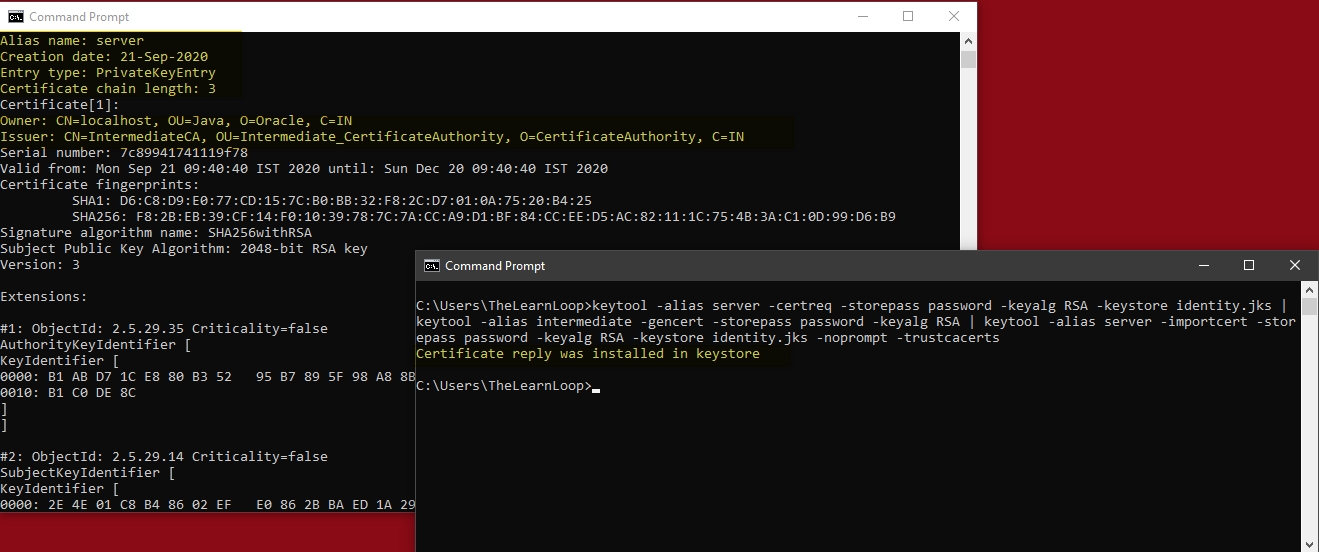
Create a certificate request (CSR) for your server certificate
Sign it with CA_Intermediate using the gencert option.
Then use the importcert option to create a chain of server, intermediate and root:
- keytool -alias server -certreq -storepass password -keyalg RSA -keystore identity.jks | keytool -alias intermediate -gencert -storepass password -keyalg RSA | keytool -alias server -importcert -storepass password -keyalg RSA -keystore identity.jks -noprompt -trustcacerts
Step 5:
You can optionally delete the root certificate of CA_Root from your identity keystore. (We need it only for chaining)
- keytool -delete -alias root -keystore identity.jks -storepass password
List the identity keystore :
- keytool -list -v -keystore identity.jks -storepass password
Step 6:
Create a trust keystore with root and intermediate certificate:
- keytool -export -alias intermediate -storepass password | keytool -import -alias intermediate -keystore trust.jks -storepass password -trustcacerts -noprompt
- keytool -export -alias root -storepass password | keytool -import -alias root -keystore trust.jks -storepass password -trustcacerts -noprompt
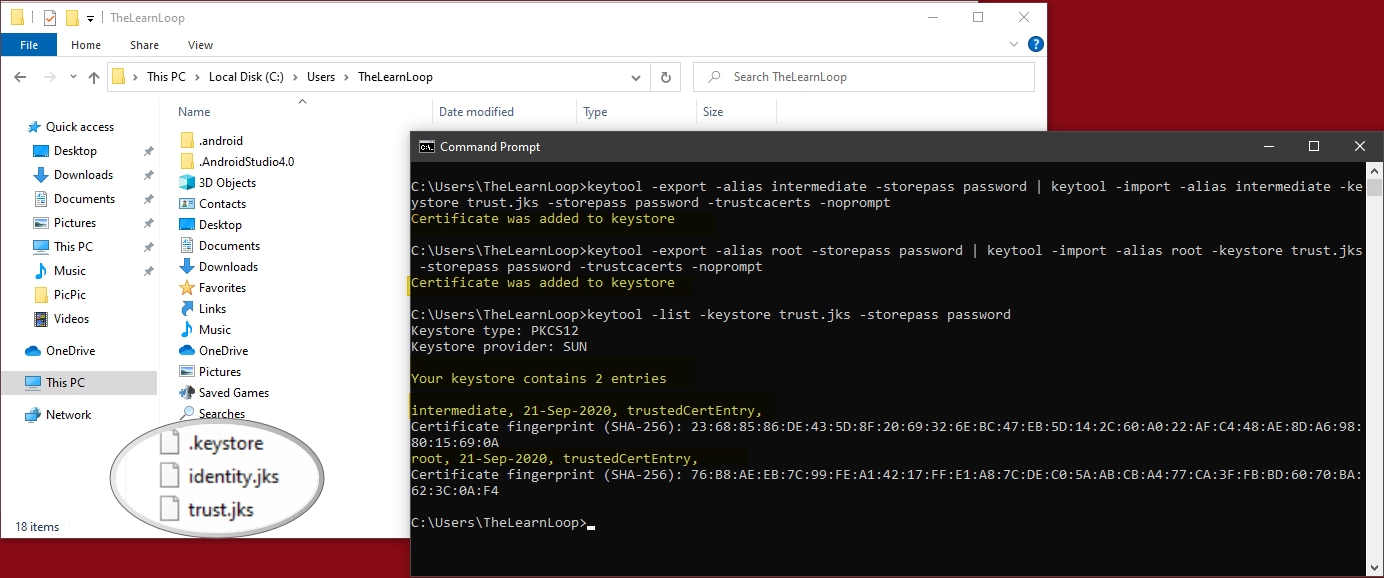
List the trust keystore :
- keytool -list -v -keystore trust.jks -storepass password
Quick Demo :
var tag = document.createElement(‘script’);
tag.src = “https://www.youtube.com/iframe_api”;
var firstScriptTag = document.getElementsByTagName(‘script’)[0];
firstScriptTag.parentNode.insertBefore(tag, firstScriptTag);
var player;
function onYouTubeIframeAPIReady() {
player = new YT.Player(‘player’, {
height: ‘360’,
width: ‘640’,
playerVars: { ‘rel’:0, ‘autoplay’: 1, ‘controls’: 1 },
videoId: ‘wh8ga5GHd0Q’,
events: {
‘onReady’: onPlayerReady,
‘onStateChange’: onPlayerStateChange
}
});
}
function onPlayerReady(event) {
//Uncomment to autoplay function
//event.target.playVideo();
}
var done = false;
function onPlayerStateChange(event) {
if(event.data === YT.PlayerState.ENDED) {
stopVideo();
}
}
function stopVideo() {
player.stopVideo();
document.getElementById(“player”).style.display = “none”;
document.getElementsByClassName(‘fluid-width-video-wrapper’).style.padding = “0”;
}
var tag = document.createElement(‘script’);
tag.src = “https://www.youtube.com/iframe_api”;
var firstScriptTag = document.getElementsByTagName(‘script’)[0];
firstScriptTag.parentNode.insertBefore(tag, firstScriptTag);
var player;
function onYouTubeIframeAPIReady() {
player = new YT.Player(‘player’, {
height: ‘219’,
width: ‘386’,
playerVars: { ‘rel’:0, ‘autoplay’: 1, ‘controls’: 1 },
videoId: ‘wh8ga5GHd0Q’,
events: {
‘onReady’: onPlayerReady,
‘onStateChange’: onPlayerStateChange
}
});
}
function onPlayerReady(event) {
//Uncomment to autoplay function
//event.target.playVideo();
}
var done = false;
function onPlayerStateChange(event) {
if(event.data === YT.PlayerState.ENDED) {
stopVideo();
}
}
function stopVideo() {
player.stopVideo();
document.getElementById(“player”).style.display = “none”;
document.getElementsByClassName(‘fluid-width-video-wrapper’).style.padding = “0”;
}
var tag = document.createElement(‘script’);
tag.src = “https://www.youtube.com/iframe_api”;
var firstScriptTag = document.getElementsByTagName(‘script’)[0];
firstScriptTag.parentNode.insertBefore(tag, firstScriptTag);
var player;
function onYouTubeIframeAPIReady() {
player = new YT.Player(‘player’, {
height: ‘219’,
width: ‘386’,
playerVars: { ‘rel’:0, ‘autoplay’: 1, ‘controls’: 0 },
videoId: ‘wh8ga5GHd0Q’,
events: {
‘onReady’: onPlayerReady,
‘onStateChange’: onPlayerStateChange
}
});
}
function onPlayerReady(event) {
//Uncomment to autoplay function
//event.target.playVideo();
}
var done = false;
function onPlayerStateChange(event) {
if(event.data === YT.PlayerState.ENDED) {
stopVideo();
}
}
function stopVideo() {
player.stopVideo();
document.getElementById(“player”).style.display = “none”;
document.getElementsByClassName(‘fluid-width-video-wrapper’).style.padding = “0”;
}
