Original Publish date : 9/22/2020
Below are the steps to create a Wildcard with SAN certificate and sign it with an internal CA :
Pre-requisites:
– Install JDK 15.
– Use the keytool commands to create an internal CA and a Wildcard with SAN certificate for your server.
– You can then create a certificate request (CSR) for your certificate and sign it with the internal CA you created earlier.
Commands Used:
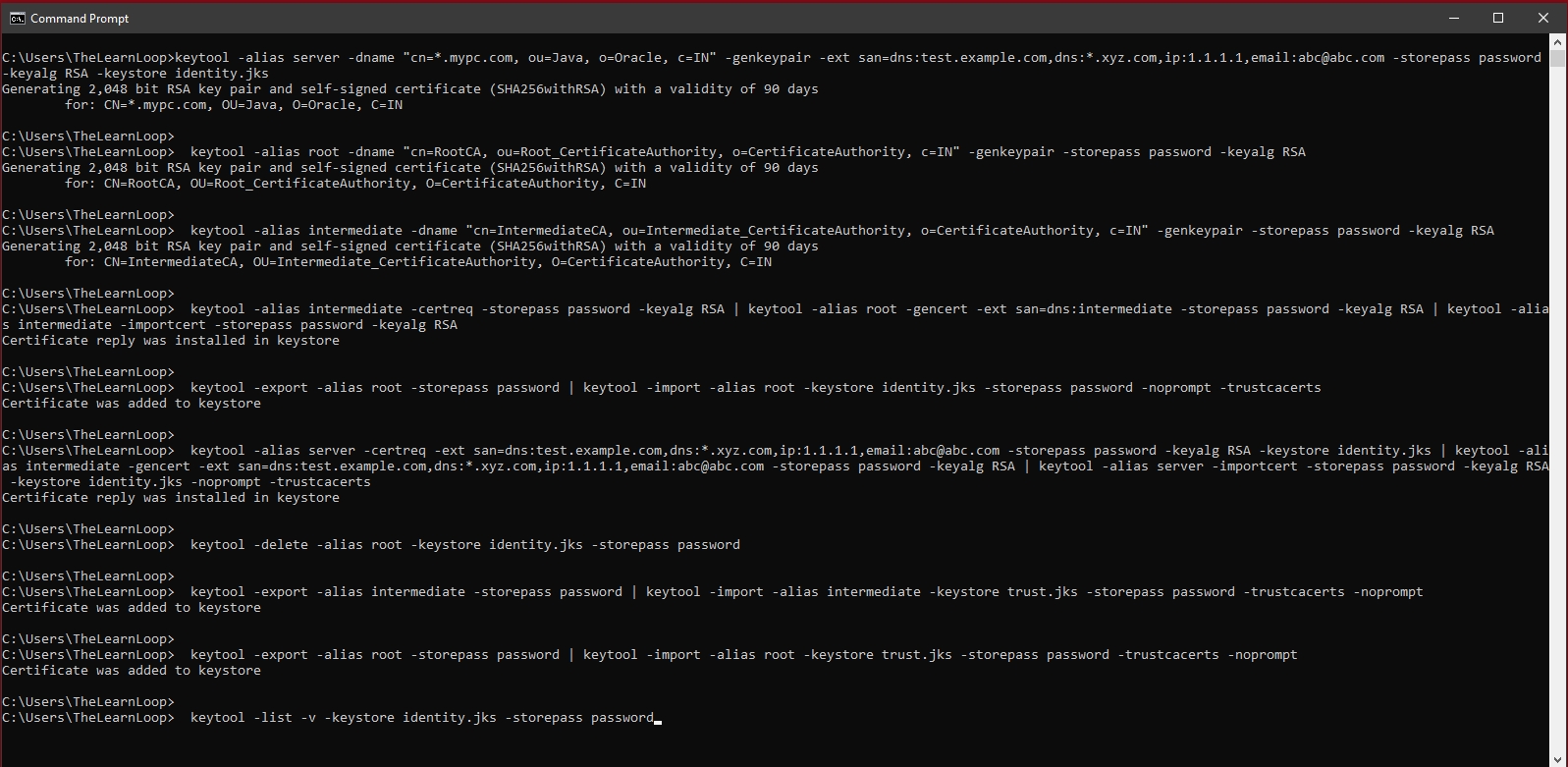
To quickly create a Wildcard with SAN certificate, just copy all the above commands and run it in cmd-promt/shell :
Detailed Steps:
Step 1:
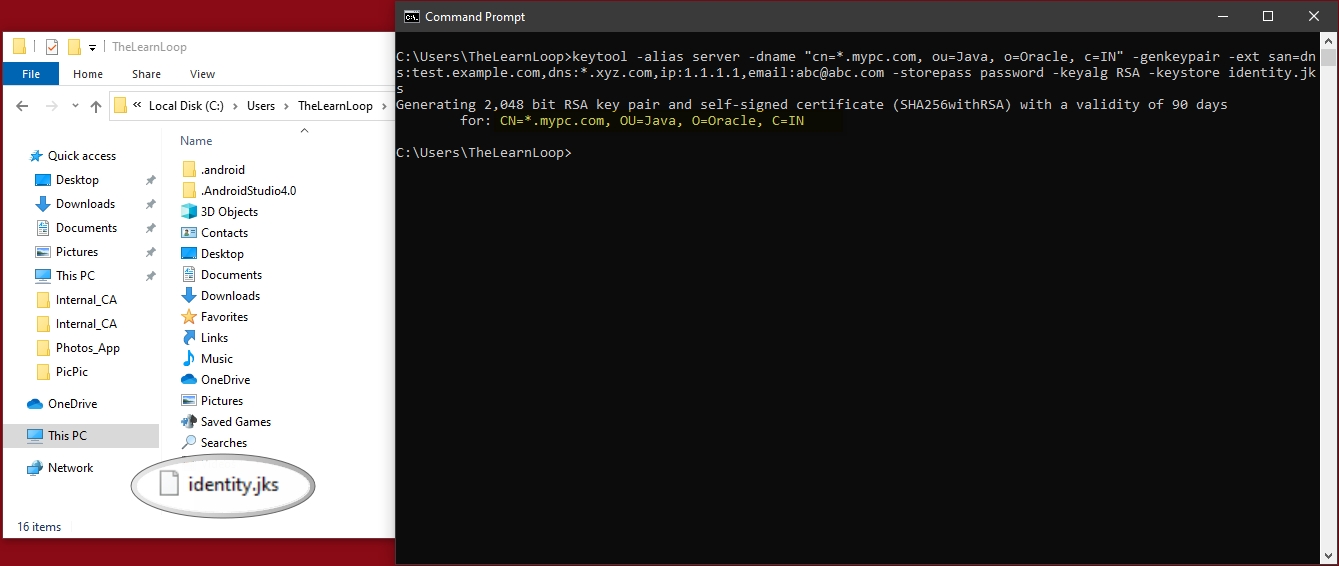
Create a keypair for your wild card and SAN certificate:
- keytool -alias server -dname “cn=*.mypc.com, ou=Java, o=Oracle, c=IN” -genkeypair -ext san=dns:test.example.com,dns:*.xyz.com,ip:1.1.1.1,email:abc@abc.com -storepass password -keyalg RSA -keystore identity.jks
Step 2:
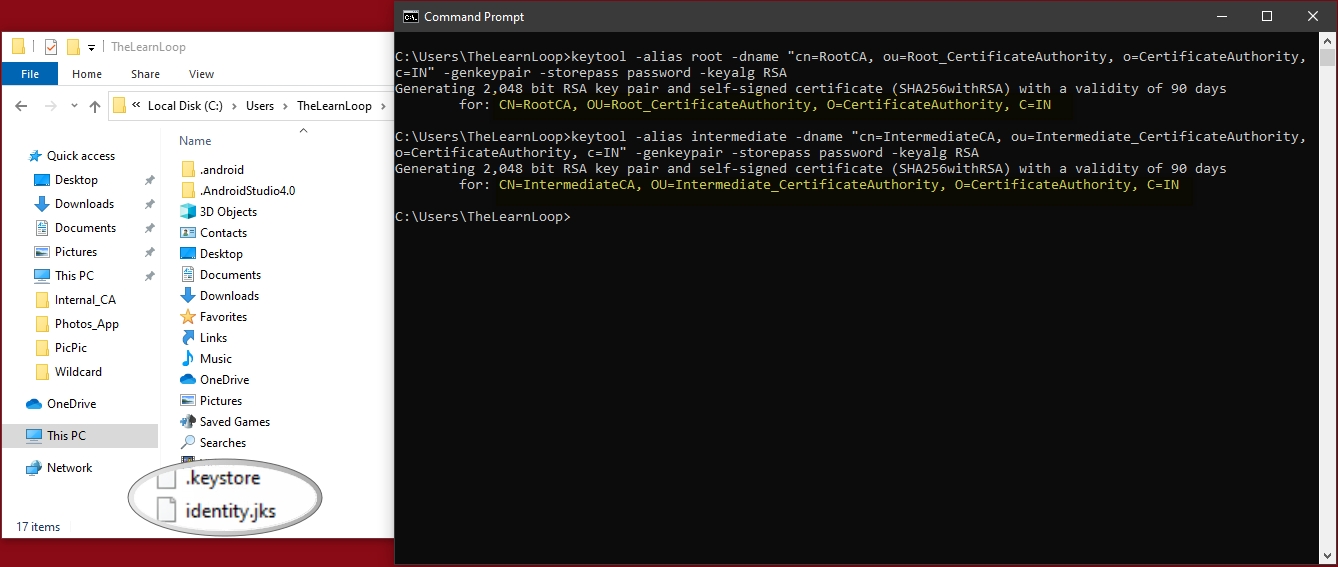
Create intermediate and root keypairs. We need this to create an internal CA.
- keytool -alias root -dname “cn=RootCA, ou=Root_CertificateAuthority, o=CertificateAuthority, c=IN” -genkeypair -storepass password -keyalg RSA
- keytool -alias intermediate -dname “cn=IntermediateCA, ou=Intermediate_CertificateAuthority, o=CertificateAuthority, c=IN” -genkeypair -storepass password -keyalg RSA
Step 3:
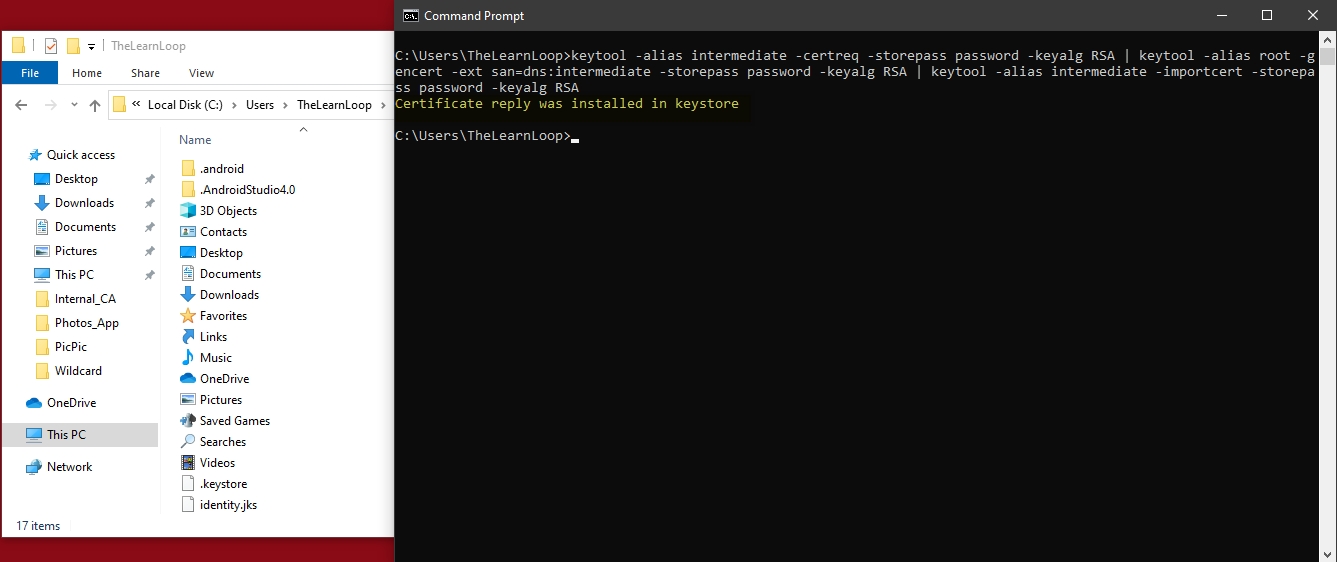
Create a certificate request (CSR) for intermediate certificate and create a chain for intermediate and root
- keytool -alias intermediate -certreq -storepass password -keyalg RSA | keytool -alias root -gencert -ext san=dns:intermediate -storepass password -keyalg RSA | keytool -alias intermediate -importcert -storepass password -keyalg RSA
Step 4:
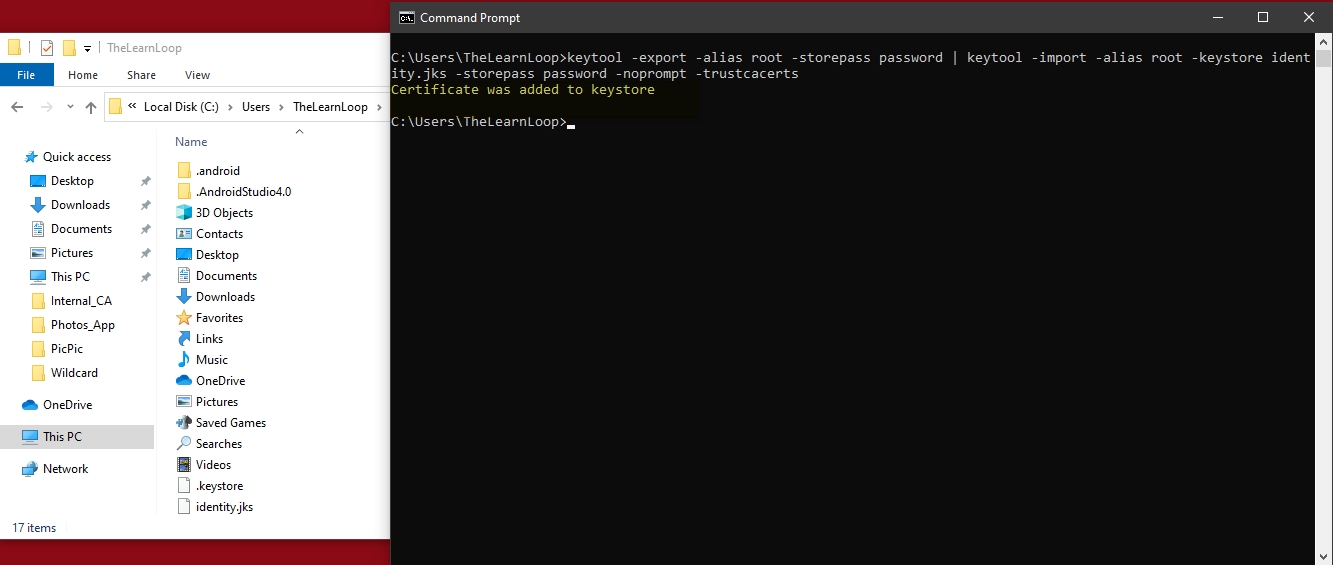
Export the root certificate and import it to the identity.jks :
- keytool -export -alias root -storepass password | keytool -import -alias root -keystore identity.jks -storepass password -noprompt -trustcacerts
Step 5:
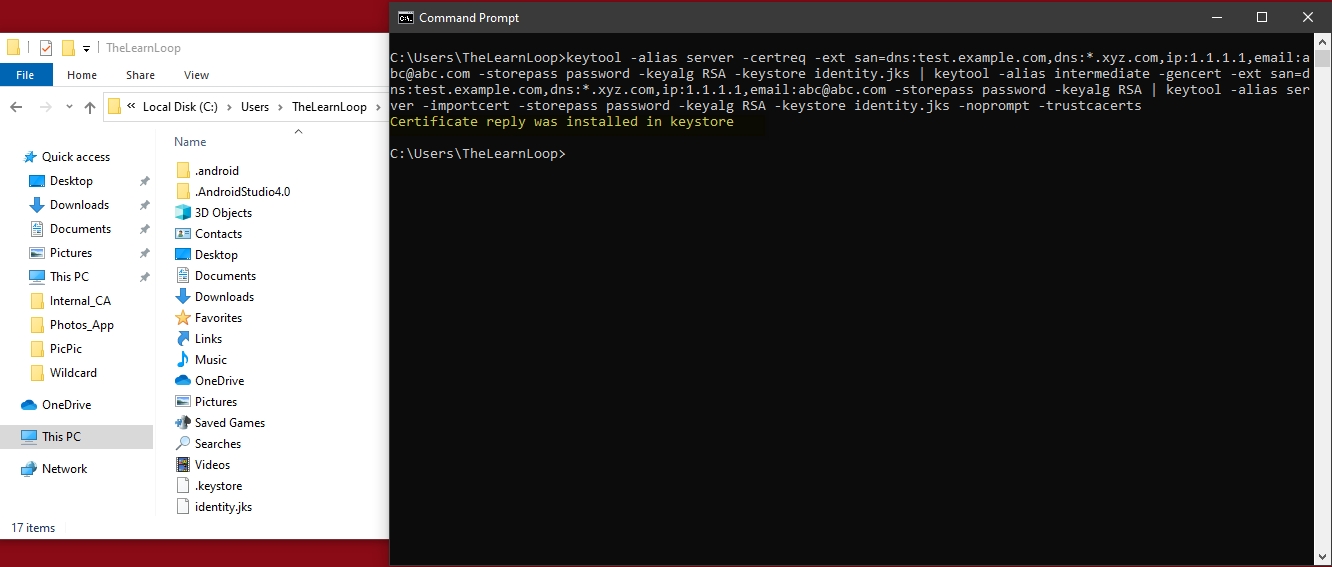
Create a certificate request (CSR) for your server certificate and sign it with intermediate and root of your internal CA:
- keytool -alias server -certreq -ext san=dns:test.example.com,dns:*.xyz.com,ip:1.1.1.1,email:abc@abc.com -storepass password -keyalg RSA -keystore identity.jks | keytool -alias intermediate -gencert -ext san=dns:test.example.com,dns:*.xyz.com,ip:1.1.1.1,email:abc@abc.com -storepass password -keyalg RSA | keytool -alias server -importcert -storepass password -keyalg RSA -keystore identity.jks -noprompt -trustcacerts
Step 6:
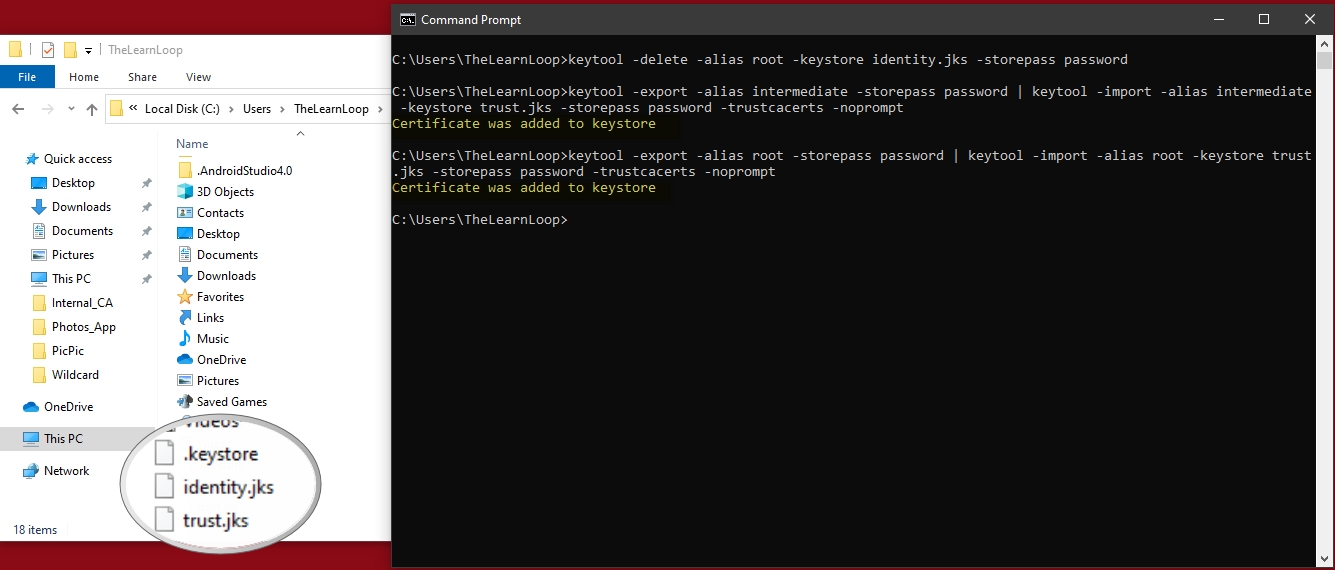
You can optionally delete the additional root cert in your identity keystore
- keytool -delete -alias root -keystore identity.jks -storepass password
Step 7:
Import the root and intermediate certificate to a new trust keystore:
- keytool -export -alias intermediate -storepass password | keytool -import -alias intermediate -keystore trust.jks -storepass password -trustcacerts -noprompt
- keytool -export -alias root -storepass password | keytool -import -alias root -keystore trust.jks -storepass password -trustcacerts -noprompt
Step 8:
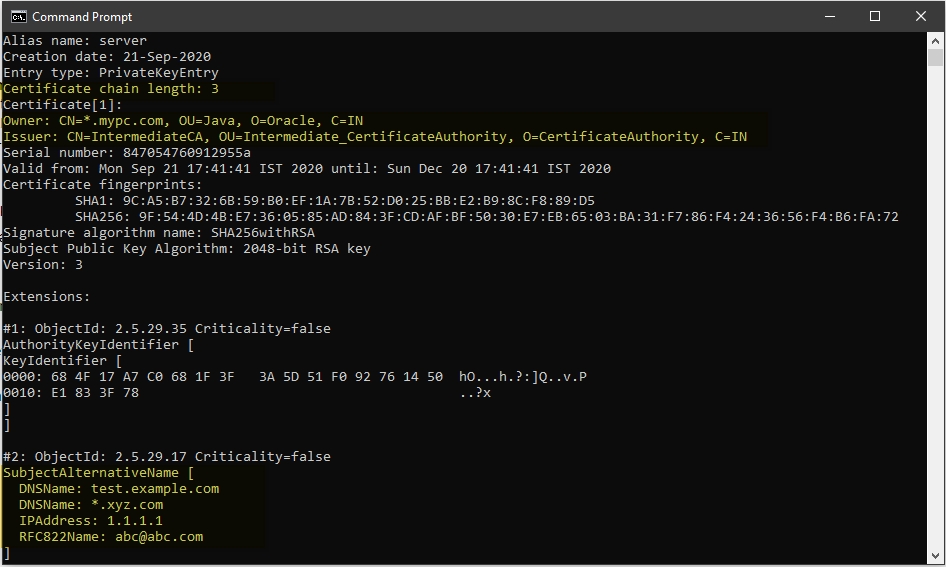
Use the following commands to list the keystore:
- keytool -list -v -keystore trust.jks -storepass password
- keytool -list -v -keystore identity.jks -storepass password