Use Case
An organization leverages Oracle Fusion Data Intelligence (FDI)’s limited availability feature, Configurable Security Context, to implement custom, granular data access controls. This feature allows the organization to restrict data visibility based on cost segments and balancing segments, ensuring users can only access financial data relevant to their assigned segments within the FDI reporting environment. By implementing custom security contexts, the organization can maintain precise control over financial data access at a departmental level.
Configurable Security Context
The Configurable Security Context feature allows security administrators to define custom security contexts. These contexts are applied to custom application roles.
The steps below show how to use the Security Configuration feature in application roles to achieve custom, granular data access controls.
1. Custom Role Creation
Create two custom application roles:
- CustomCostSegment: For controlling access based on cost center
- CustomSecBalSegmentRole: For controlling access based on balancing segments
2. Security Context Configuration
For both the roles, set up Security Configurations. This tab is enabled only when the Configurable Security Context feature is enabled.
- Provide the Name of the custom context.
- Select the attribute on this context that should work. (Expand the subject areas and then folders to select the particular attribute)
- Mention the fact which needs to be secured.
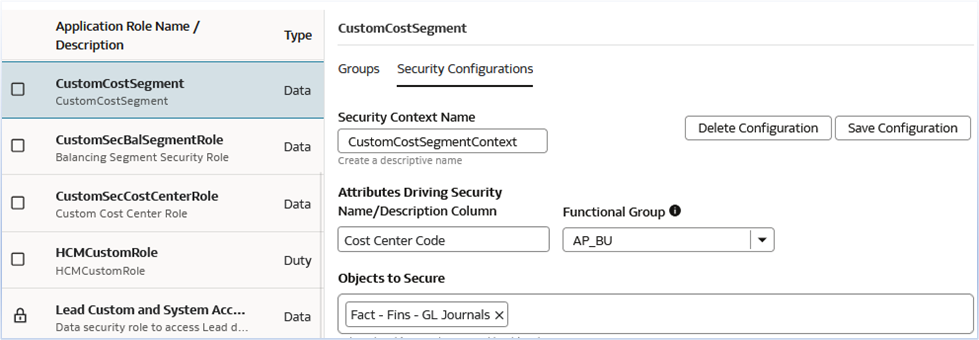
For CustomCostSegment:
- Context Name: CustomCostSegmentContext
- Attribute Selection: Cost Center attributes from subject areas
- Secured Facts: Relevant financial metrics
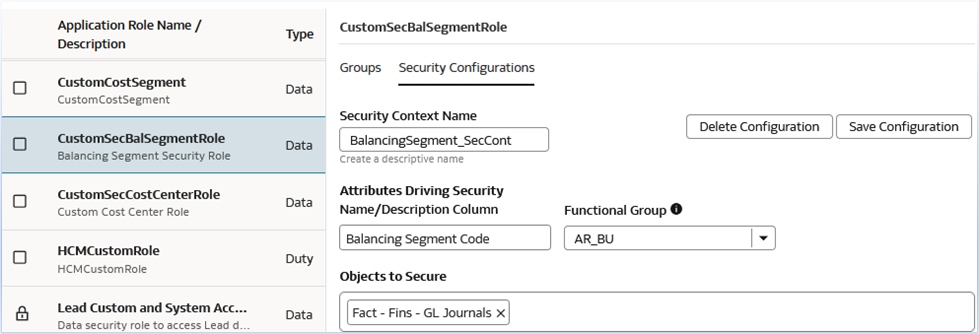
For CustomSecBalSegmentRole:
- Context Name: BalancingSegment_SecCont
- Attribute Selection: Balancing Segment attributes
- Secured Facts: Relevant financial metrics
Functional group: This is an optional field. By choosing the functional groups associated with each security filter, you can control how the filters are combined using the OR and AND operators. All the filters in the same functional group are combined using the OR operator and all sets of filters in different functional groups are combined using the AND operator.
Publish the Model: Click Publish Model to initiate the publishing process. Wait until the publishing activity is completed before proceeding.
3. Group Management
- Create security group Config_Sec
- Add relevant users to the group
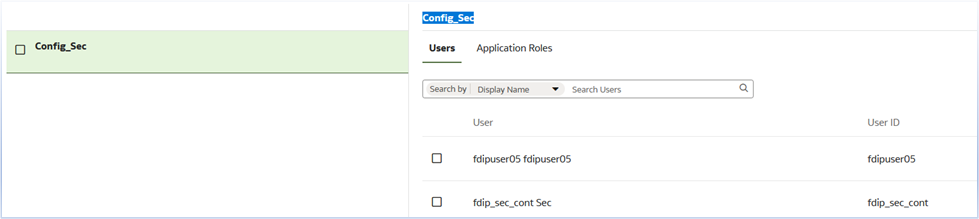
- Map custom application roles to the group:
- CustomCostSegment
- CustomSecBalSegmentRole
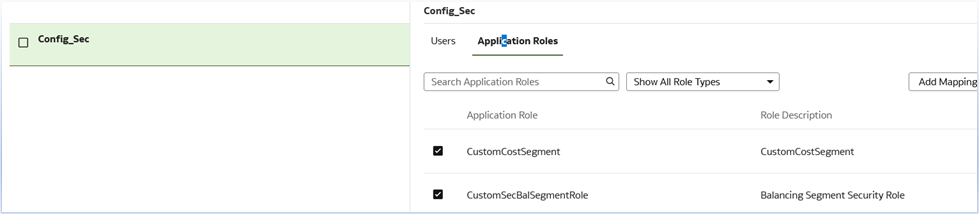
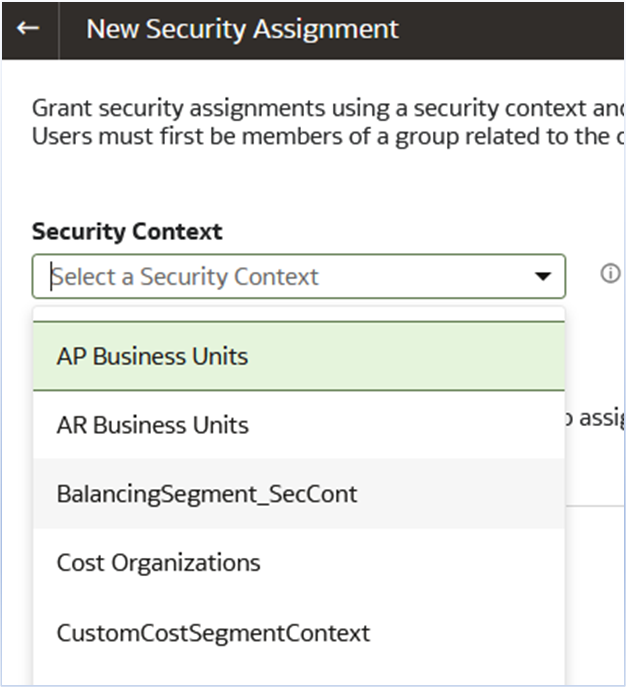
Security Assignments
TheSecurity Context drop-down menu now shows the custom contexts created in the previous steps.
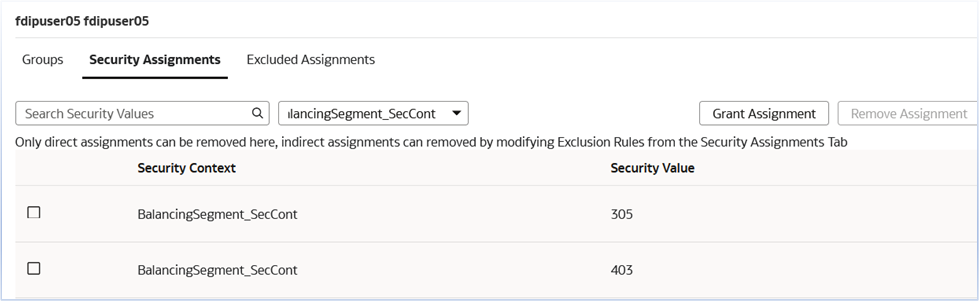
- Select the BalancingSegment_SecCont context and select the balancing segment code which should be visible to that user.
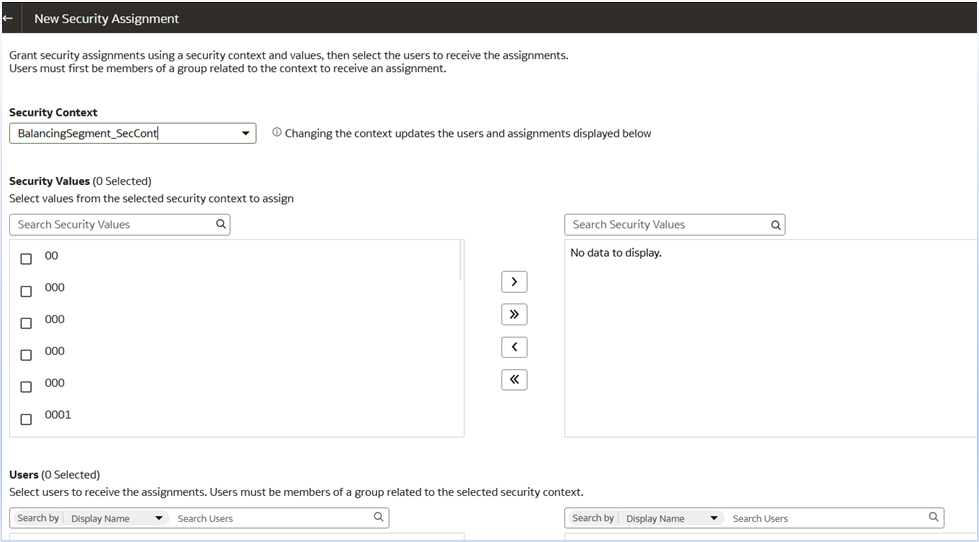
For BalancingSegment_SecCont:
- Assign specific balancing segment codes (e.g., 305,403)
- Configure security values for data access
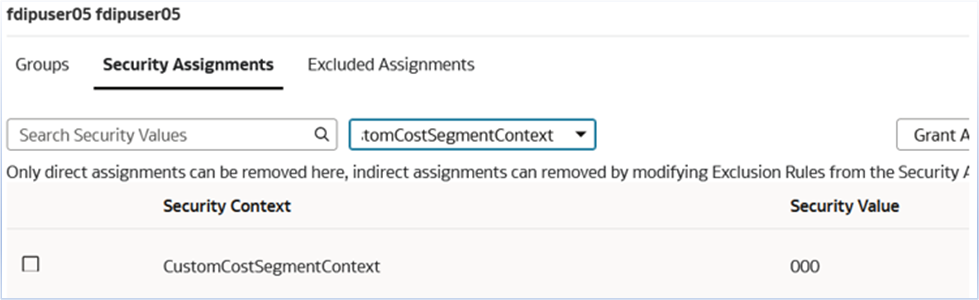
For CustomCostSegmentContext:
- Assign specific cost center codes (e.g., 000)
- Configure associated security values
On the user tab, select the user, and verify the security assignments of the group.
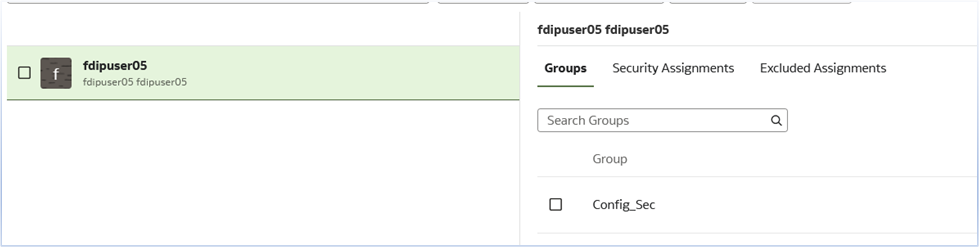
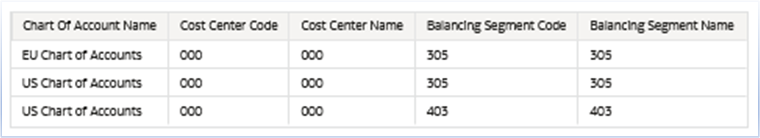
In this example, Balancing Segment 305, 403, and Cost Center 000 are assigned to this user. Note that this user must have the required duty roles to access these subject areas. For more details, see the documentation.
Validation
1. Log in with the user included in the custom group.
2. Verify that the user has the required duty roles
3. Create sample reports to validate:
- Data should only show transactions for cost center 000
- Data should only show transactions for balancing segment 305 and 403
- If functional groups aren’t selected, full outer join results are shown
Call to Action
Take action now to enhance your data security with the Configurable Security Context feature limited availability feature in Oracle Fusion Data Intelligence (FDI). By enabling this feature, creating custom roles, configuring security contexts, and setting up proper user group mappings, you can ensure precise control over data access based on cost segments and balancing segments. Implement this solution to strengthen your organization’s security while maintaining operational efficiency.
Now that you’ve read this article, try it yourself and let us know your results in the Oracle Analytics Community, where you can also ask questions and post ideas.
