The blog was co-written by Derrick Gooch, Solution Architect, Fortinet. Derrick is an experienced Solution Architect at Fortinet with 19+ years working in the network and security industry. His strong background in Information Technology, Architecture, Operations, System Deployment, and Automation has enabled customers develop and reimage their cloud network and security fabric.
The increasing Digital Transformation trend in applications moving from on-premises to the cloud has seen significant revenue growth in the global cloud markets. According to Fortune Business Insights, the global cloud computing market is projected to grow from $405.65 Billion (in 2021) to $1,712.44 Billion by 2029. This growth is driven, in part, by core business-critical applications such as Oracle E-Business Suite (EBS) moving from on-premises data centers to Oracle Cloud Infrastructure (OCI). This growth has led to a significant increase in online connections to the cloud—a trend that continues to rise. Another area driving online traffic is the post-pandemic trend of an increase in remote workforce. In 2022, McKinsey found that 58% of American workers report having the opportunity to work remotely. A similar trend reported by Buffer is that 97% of employees interviewed would like to work remotely. More recently organizations are requiring their workforce come back to the office at least few days in a week. The net effect is a workforce that has increasingly become distributed in the way in which they access the corporate network and systems.
Industry Impact and Security Implications
These two trends have security implications for organizations. Clearly, companies need to provide remote employees with access to business-critical applications such as Oracle EBS. However, the threat of resulting security breaches is real and costly. For example, the World Economic Forum has estimated costs from cybercrime at a staggering $2.2 trillion in 2023 and that number is likely to increase by nearly 5X to $10.5 trillion by 2025. Yet, organizations don’t have the personnel to stem the tide: as many as 73% of organizations reported that they had at least one intrusion/breach over the past year that can be attributed to a gap in cybersecurity skills. One way to provide a secure environment for remote workers is by only allowing secured endpoints. Technologies such as IPSec and SSL VPN are well proven, but they are not without challenges. Both are tunneling technologies that give endpoints access to the entire network. While this access can be locked down through security policies, a minor misconfiguration or vulnerability can open a significant door to attack. This leads many companies to shift focus toward granular application access using Zero Trust Network Access (ZTNA).
Fortinet ZTNA
FortiGate has provided network security for over 20 years. Leveraging that extensive industry experience and development, FortiOS has been recognized as best-of-breed for both Next-Generation Firewall (NGFW) and SD-WAN. FortiOS provides continuity of experience and features across all public and private cloud environments. This, in conjunction with centralized configuration and policy management, greatly simplifies security implementation and operations.
FortiClient is a Fabric Agent, deployed to endpoints, providing many security features, including AI-based next-generation anti-virus (AV), endpoint quarantine, application firewall, sandbox integration and ransomware protection.All of these features are centrally controlled by FortiClient Endpoint Management System (EMS). Additionally, EMS serves as a ZTNA controller. OS-specific Zero Trust Tagging rules are configured on EMS, and pushed to FortiClient, using endpoint profiles. Based on these policies, FortiClient scans the endpoint to determine security posture and assign tags. EMS then uses an API fabric connector to FortiGate in order to share these Zero Trust Tags, which are used by FortiGate as part of a ZTNA Access Proxy Policy. uses an API fabric connector to FortiGate in order to share these Zero Trust Tags, which are used by FortiGate as part of a ZTNA Access Proxy Policy.
Securing Oracle EBS Apps with Fortinet ZTNA
One of the most common applications to be secured at the network perimeter is an Oracle EBS R12 Application running on OCI. Implementing Fortinet ZTNA allows administrators to leverage better real-time visibility into application security. Furthermore, ZTNA enables policies for role-based access to multiple sets of users (e.g. internal divisions and external clients). The Fortinet ZTNA solution improves security to meet compliance of the customer’s acceptable use policy through unmatched, real-time visibility into their applications. With FortiGuard Application Control, customers can quickly create policies to allow, deny, or restrict access to applications, or entire categories of applications.
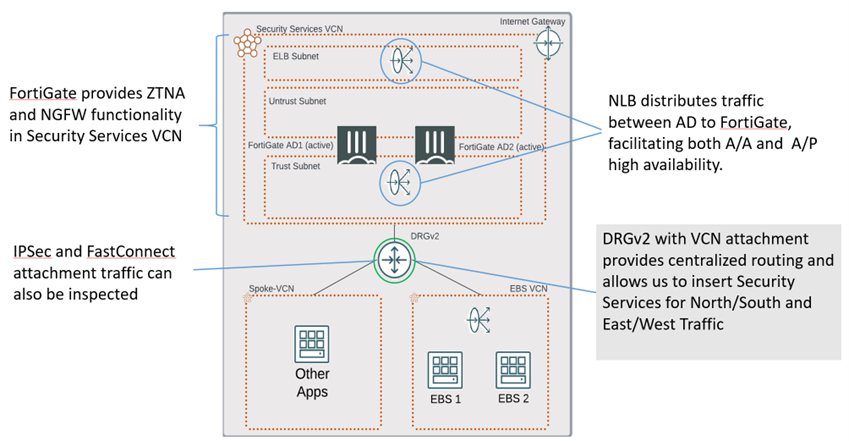
Figure-1: FortiGate Architecture for EBS on OCI
ZTNA’s solution capabilities for Oracle EBS R12 on OCI include:
- User Identity is authenticated per connection. Strong Authentication (MFA) and Single Sign-on (SSO) are supported.
- Device Identity is verified per session; Device Posture is verified in real time.
- Granular user access is allowed only to necessary applications and data.
- Applications are hidden from the Internet behind Access Proxy.
To see these solutions in action, feel free to contact the Oracle Solution Centers (www.oracle.com/osc) through your Oracle Account Representative and ask how to engage the OSC in validating any of these solutions before you make an investment. Also, learn more about Fortinet and OCI at: https://www.oracle.com/cloud/partners/fortinet/

