The increasing Digital Transformation trend in applications moving from on-premises to the cloud has seen significant revenue growth in the global cloud markets. According to Fortune Business Insights, the global Cloud Computing Market is projected to grow from $405.65 Billion (in 2021) to $1,712.44 Billion by 2029. This growth is driven, in part, by core business-critical applications such as Oracle E-Business Suite (EBS) moving from on-premises data centers to Oracle Cloud Infrastructure (OCI). Organizations realize cloud modernization benefits such as enhanced availability, accessibility, performance, cost-optimization, and improved real-time analytics. The increase in core applications moving to the cloud, has led to a significant increase in online connections to the cloud—a trend that continues to rise.
Another area driving online traffic is the post-pandemic trend of an increase in remote workforce. During the pandemic, in 2020, most of the labor workforce in the U.S. started to work remotely. In the wake of this, many companies and employees realized unexpected benefits ranging from increased productivity to higher work life satisfaction. In 2022, McKinsey found that 58% of American workers report having the opportunity to work remotely. A similar trend reported by Buffer is that 97% of employees interviewed would like to work remotely. More recently organizations are requiring their workforce come back to the office at least few days in a week. The net effect is a workforce that has increasingly become distributed in the way in which they access the corporate network and systems.
Industry Impact and Security Implications
These two trends have security implications for organizations. Clearly, companies need to provide remote employees with access to business-critical applications such as Oracle EBS. However, the threat of resulting security breaches is real and costly. For example, the World Economic Forum has estimated costs from cybercrime at a staggering $2.2 trillion in 2023. That number is likely to increase by nearly 5X to $10.5 trillion by 2025. Yet, organizations don’t have the personnel to stem the tide: as many as 73% of organizations reported that they had at least one intrusion/breach over the past year that can be attributed to a gap in cybersecurity skills. Couple these risks with the challenges facing organizations to cater to a remote workforce, the following key points need consideration:
- Organizations need to provide remote employees access to core business-critical applications such as Oracle EBS, while granting access only through secured endpoints.
- Technologies such as IPSec and SSL VPN, are well proven, but they are based on tunneling technologies that give endpoints access to the entire network.
- While this access can be locked down using security policies, a minor misconfiguration or vulnerability can open a large door to attack.
- This leads many companies to shift focus toward granular application access using Zero Trust Network Access (ZTNA).
Aside from the economic and social implications of these paradigm shifts many challenges abound. Cybersecurity professionals and attackers have seen the attack surface area grow and shift as a result of these changes.
In addition to providing access to applications, organizations need to make sure that endpoints are safe and compliant with security policies. With the advent of IoT leading to more and more connected devices, remote workers’ endpoints often share network resources with unprotected and even malicious hosts. It has never been more important to protect the integrity of endpoints and applications.
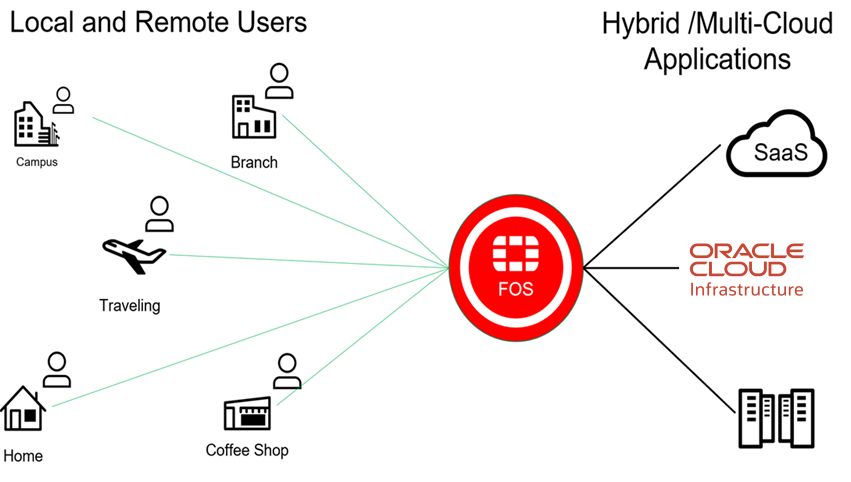
Figure-1: Remote employees connected to hybrid cloud applications in distributed datacenters.
Oracle E-Business Suite
Oracle EBS is a portfolio of integrated business applications that enable organizations to make better decisions, reduce costs, and increase performance. EBS applications provide solutions for customer relationship management, service management, financial management, human capital management, project portfolio management, advanced procurement, supply chain management, value chain planning, and value chain execution.
Oracle Exadata Database Service on Dedicated Infrastructure
Oracle Exadata Database Service on Dedicated Infrastructure is a virtual machine (VM) cluster that runs on Oracle Exadata racks in OCI. Alternatively, customers can choose Exadata Cloud@Customer, which offers Exadata Database Service and/or Autonomous Database deployed in customers’ data centers.
Fortinet ZTNA
FortiGate has provided network security for over 20 years. In that time, FortiOS has grown to become best-of-breed for both Next-Generation Firewall (NGFW) and SD-WAN. Many of Fortinet’s 650,000 customers have leveraged FortiOS to protect their cloud estate. As 69% of customers have resources deployed across multiple public and private clouds, FortiOS’ continuity of experience and features as well as centralized configuration and policy management greatly simplify security implementation and operation.
FortiClient is a Fabric Agent, deployed to endpoints, providing many security features, including AI-based next-generation anti-virus (AV), endpoint quarantine, application firewall, sandbox integration and ransomware protection. All of these features are centrally controlled by the FortiClient Endpoint Management System (EMS). In addition to these features, EMS also serves as a ZTNA controller. OS-specific Zero Trust Tagging rules are configured on EMS, and pushed to FortiClient, using Endpoint Profiles. Based on these policies, FortiClient scans the endpoint to determine security posture and assign tags. EMS then uses an API Fabric Connector to FortiGate in order to share these Zero Trust Tags, which can be used by FortiGate as part of a ZTNA Access Proxy Policy.
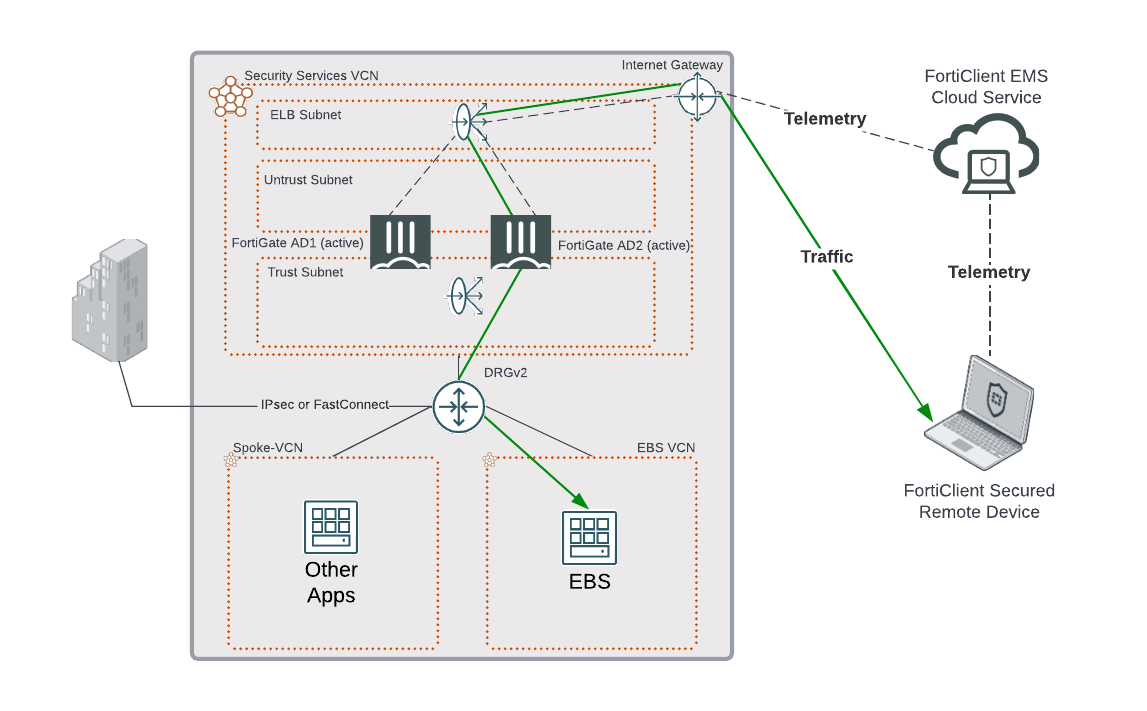
Figure-2: Common deployment scenario with Fortinet’s ZTNA and FortiGate securing Apps
Figure 2 depicts a very common deployment scenario, in which FortiGate is deployed in a Security Services Virtual Cloud Network (VCN). This architecture uses a public Network Load Balancer (NLB) in OCI to receive and distribute ZTNA traffic to FortiGate. Fortinet’s ZTNA solution also supports Full User Authentication including using SAML integrated with LDAP.
To address this hybrid/multi-cloud security use case, we set up an Exadata Database Service on Dedicated Infrastructure in the Oracle Solution Center. Then we setup the Oracle EBS R12 application on an OCI virtual machine. We ensured sample application data stored in the database could be accessed via the EBS application. To front end the EBS application we setup a load balancer and configured EBS to be enabled with SSL. Fortinet ZTNA solution used the applications HTTPS URL for its testing.
Securing Oracle EBS with Fortinet ZTNA
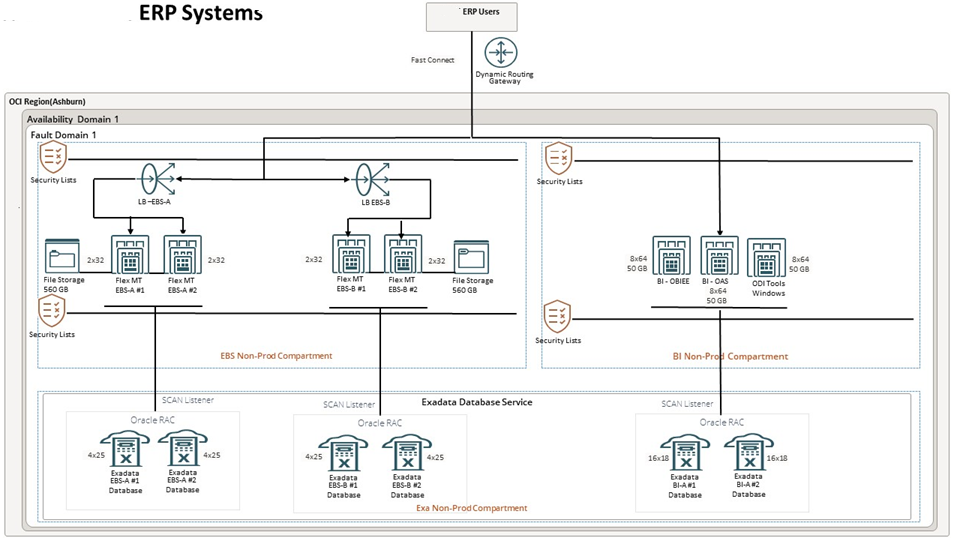
Figure-3: Oracle E-Business Suite Deployment on Oracle Cloud Infrastructure
The application we are securing at the network perimeter is an Oracle EBS R12 Application (with optional Oracle Analytics Platform) running on OCI as shown in Figure 3. Note that this is an EBS R12 deployment that has been deployed on an OCI VM. The application is secured using Fortinet ZTNA to leverage better real-time visibility into application security. Furthermore, ZTNA enables policies for role-based access to multiple sets of users (e.g. internal divisions and external clients).
The Fortinet ZTNA solution improves security to meet compliance of the customer’s acceptable use policy through unmatched, real-time visibility into their applications. With FortiGuard Application Control, customers can quickly create policies to allow, deny, or restrict access to applications or entire categories of applications.
Multicloud to Multi-Point
The Fortinet Security Fabric is designed as a platform from which to secure the entire attack surface area. Each component (Firewall and Endpoint Protection) of Fortinet’s ZTNA solution can stand on its own to provide best-of-breed security capabilities.
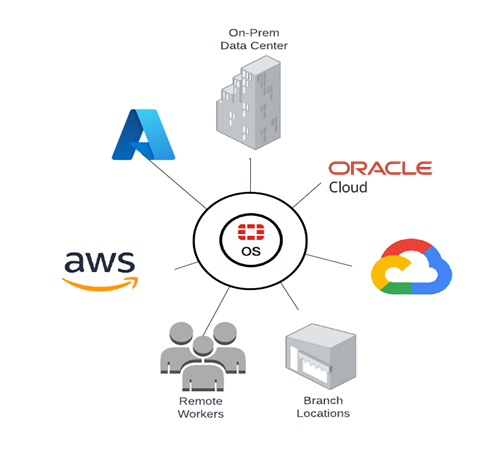
Figure-4: Multicloud to Multi-Point
When all components are integrated together, the whole is greater than the sum of the parts. This example shows EBS deployed in OCI, but Fortinet’s ZTNA architecture can integrate with multiple FortiGates across multiple public and private clouds to secure applications, no matter where they are deployed.
How does the Fortinet ZTNA Solution for Oracle EBS Work?
The Zero Trust Network Access Solution for EBS can be setup using the 5-step process below:
- First, we verify the trust relationship between the FortiClient EMS, the endpoint, and FortiGate. From the FortiClient EMS cloud, we look at the client endpoint to see that it is indeed joined to the EMS; and we see a serial number there. Then, we log into the client endpoint which, in this case, is a Windows 10 workstation. Under zero trust telemetry, we verify that it is managed by the client cloud by verifying that the same serial number is also seen at the client endpoint. In order to look at the client user information through the client EMS, we have zero trust tags instead of the client username and email id information, along with the client hostname. These tags are associated with this endpoint based on policy rules set for the client EMS.
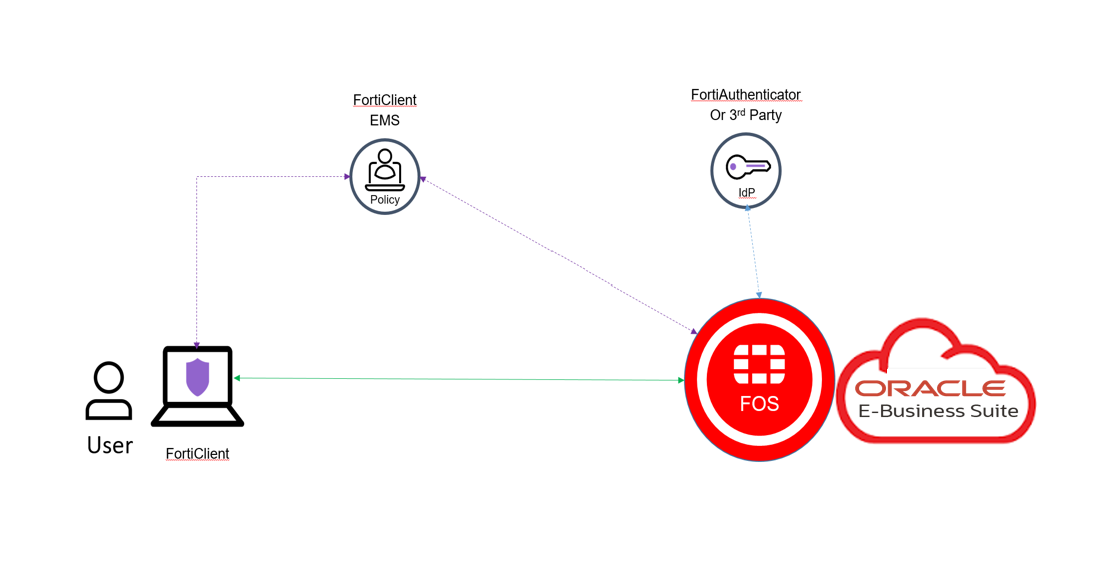
Figure-5: Components of the working solution
- Second, we take a look at the client endpoint. Here we can see all the tags, as well as other information such as the IP address, serial number, the ZT, and other details about how the device is configured.
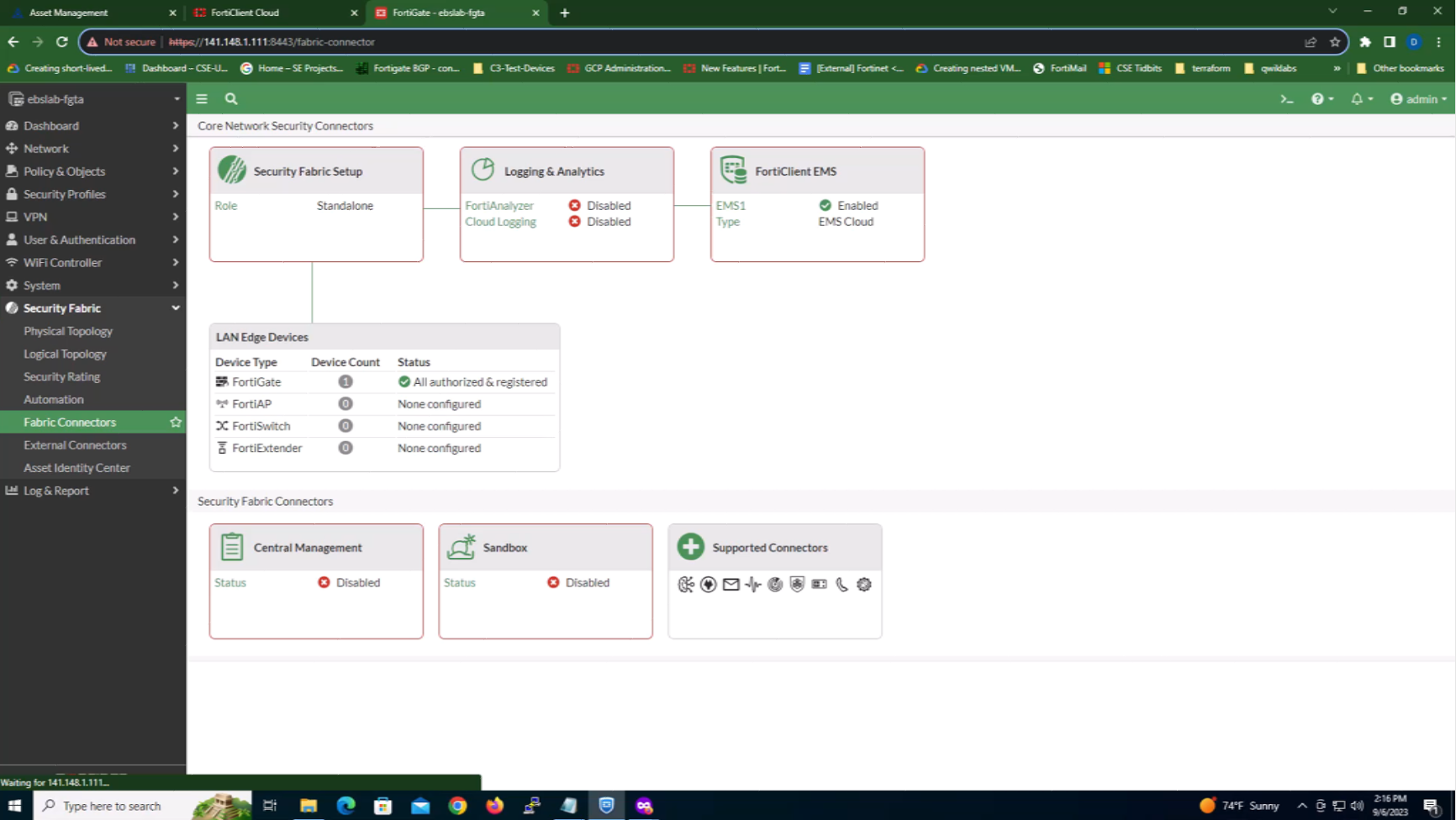
- Third, now that we’ve established the trust relationship between the FortiClient EMS and the client endpoint, we establish the trust relationship between the FortiClient EMS and FortiGate. From the administration console, there are multiple devices that are joined to the FortiClient EMS. Then, from the FortiGate console, we look for the specific device serial number for the FortiClient. When this serial number is found, we can check the status of the security fabric’s connectors that connect to the client EMS. From the FortiClient EMS cloud, log into the FortiGate using the same cloud account (via support.fortinet.com) as the EMS system.
- Fourth, now that we have the trust relationship established between all the devices, we proceed to configure ZTNA on FortiGate. We then navigate over to ‘policy and objects’, where we have two options – “ZTNA Servers” and “ZTNA Tags”.
- Configuring ZTNA Servers: To configure the ZTNA server, the external IP address in this case is the private IP address used on port one. Traffic inbound to this cluster actually hits a network load balancer and is forwarded to this FortiGate which is on the backend. Use this virtual IP to configure and look for anything coming in through this IP address on port 443, which is then forwarded to and acts as our backend server. The service is HTTPS and we match the application URL as apps.example.com to start at the root directory here, so anything from the root directory is allowed. A load balancer is setup in front of our EBS cluster.
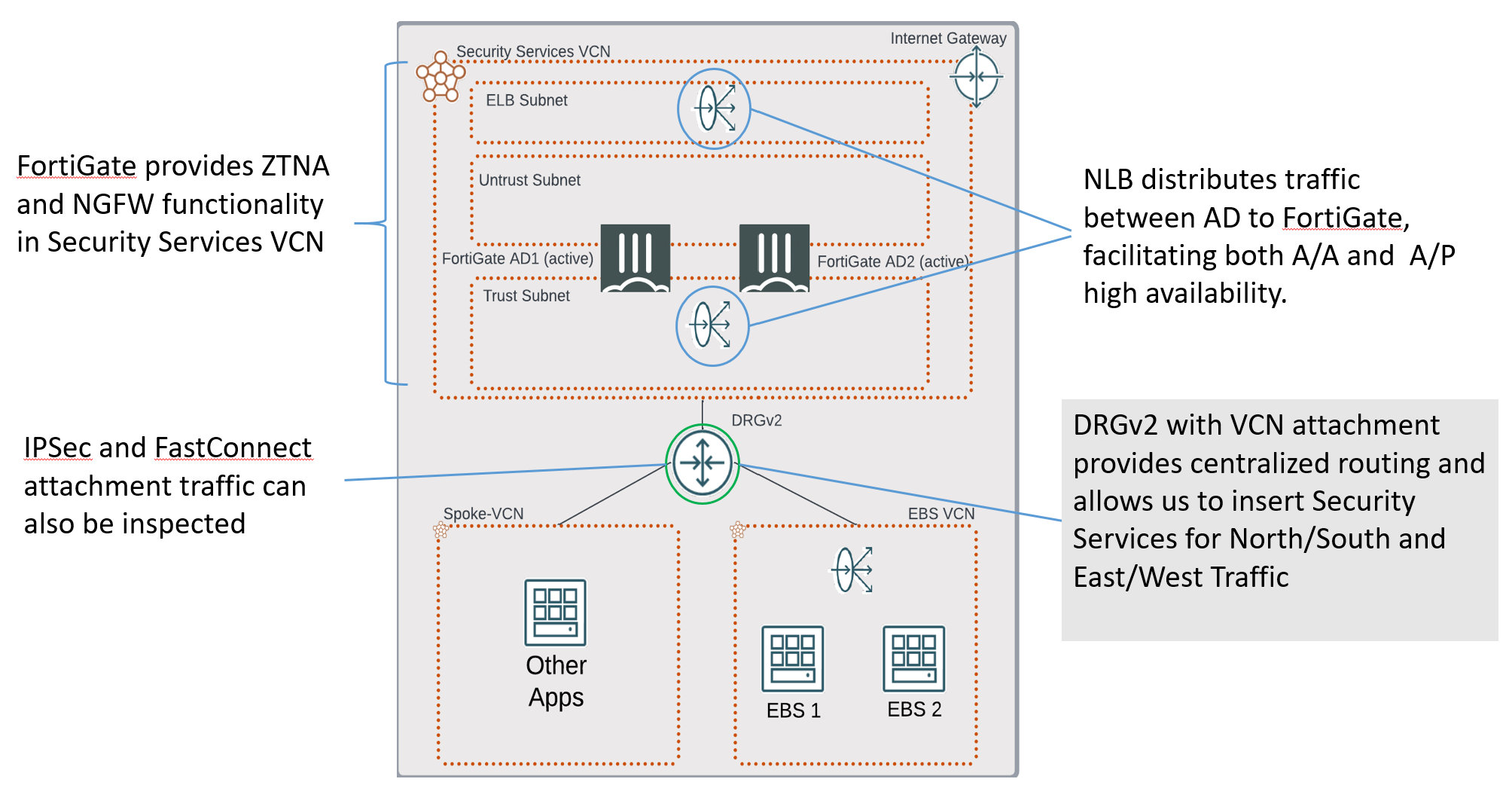
Figure-6: Fortinet ZTNA for Oracle EBS
- Configuring ZTNA Tags: Now that we’ve looked at the server, let’s look at the tags. As discussed, you can see that these are the tags that are shared from the FortiClient EMS server. These will be used in our proxy policy (and objects proxy policy). The first policy to setup is the policy managed as a ZTNA policy. We look for source IP addresses from remote users. These addresses may change and hence don’t need to be locked down, due to the use of certificates issued by FortiClient EMS to the client endpoint. The user in this case is also validated using the LDAP connection. Then from the endpoint itself, we look for these tags as resources in the form of managed tag and test tag. The destination is defined (in the ZTNA server) as the IP address to a DNS server. Additionally, there is also an option to configure any of the standard FortiGate Next-Gen Firewall Security profiles here. The destination is now setup and reachable.
- Last, from a browser window, we try to access the EBS application using the HTTPS URL apps.example.com. The user is asked for the certificate to be used to access this application. The user can accept this certificate because the user authentication policy is already applied to the FortiGate. Then on entering the user’s login information, the user is allowed to login to Oracle and access the EBS application. From there, we go back and enable our policy, created in step 4. This acts as a firewall and weighs all application traffic based on the policies in policy order. If it matches the policy, it will stop looking and perform whatever action that policy tells it to do. If, for instance, the policy is edited to have a different tag for the same source information which corresponds to a rule set up to look for vulnerable applications on the client endpoint. When we now enable this policy, it will flag that endpoint as being vulnerable, and, in this case, the action was to deny that traffic, since we encountered this vulnerable tag. To confirm, we additionally look at the vulnerability scan and actually found a highly vulnerable version of a program through this scan. The end user gets a “ZTNA Access Denied” when trying to access the EBS Application, because of the tags.
Fortinet ZTNA Solution Capabilities for Oracle EBS
ZTNA’s solution capabilities for Oracle EBS R12 on OCI include:
- User Identity is authenticated per connection. Strong Authentication (MFA) & Single Sign-on (SSO) is supported.
- Device Identity is verified per session.
- Device Posture is verified in real time.
- Granular user access is allowed only to necessary applications and data.
- Applications are hidden from Internet behind Access Proxy.
The Oracle Solution Center Advantage
This paper was developed in the Oracle Solution Center (OSC). The OSC is a centralized global organization with twelve state-of-the-art locations worldwide where customers architect, customize, and test solutions. High-value customer solutions are demonstrated through Oracle products and services and partner competencies to match your complex business requirements and technology needs. OSC is where customers can test truly cross-platform architectures, be it OCI, Oracle Exadata Cloud @Customer, multicloud or on-premises engineered systems, all in one secure, scalable, and interoperable environment.
To meet evolving business and technology challenges quickly, OSC provides a wide range of accelerated services that highlight Oracle products and services and complementary Partner products as needed. Key services include Architecture Reviews, TCO/ROI Analyses, Proofs of Concepts, Customized Demonstrations, and Workshops to support a dynamic VAD/VAR, ISV, and System Integrator community. To leverage the Oracle Solution Center for your complex multicloud scenarios, contact your local Oracle Account Manager.
To see these solutions in action, feel free to contact the Oracle Solution Centers (www.oracle.com/osc) through your Oracle Account Representative and ask how to engage the OSC in validating any of these solutions before you invest.
Learn more about Fortinet and OCI: https://www.oracle.com/cloud/partners/fortinet/
Resources
Fortinet Resources:
https://www.fortinet.com/products/public-cloud-security/OracleCloud
https://docs.fortinet.com/ztna
https://docs.fortinet.com/cloud-solutions/oci
Oracle Resources:
https://www.oracle.com/cloud/partners/fortinet/
https://www.fortinet.com/products/public-cloud-security/OracleCloud
Oracle Solution Center: www.oracle.com/osc
This blog was co-written by Derrick Gooch, Solution Architect, Fortinet. Derrick is an experienced Solution Architect at Fortinet with 19+ years working in the network and security industry. His strong background in Information Technology, Architecture, Operations, System Deployment, and Automation has enabled customers develop and reimage their cloud network and security fabric.

