Contributor: Pankaj Agrawal
Many of the logs collected in OCI Logging Analytics service (Logging Analytics) include public IP addresses which could have some level of threat associated with them. Learning about the possible threats early can help separate and mitigate them. Logging Analytics provides automatic threat intelligence enrichment for your logs.
When the log data is ingested, Logging Analytics annotates the logs with the indication that there is a threat related to this log data based on the information from Oracle Threat Intelligence Service. Logging Analytics is integrated with Oracle Threat Intelligence to automatically receive the threat feed as the logs are ingested. The feature is available for all the log sources in the regions where both Logging Analytics and Oracle Threat Intelligence services are enabled.
Once threats are identified, here is a summary of follow-up tasks to perform:
- Use the associated field and label to search for the logs containing potential threats. Drill down to specific log records. View more details about the threat in the Threat Intelligence service console.
- Use the advanced log analytic tools to identify patterns or groups in the threats to help generate insights.
- After threat indicators are identified, create and save a matching search. Create a detection rule to run at ingest-time and generate alerts when the threat indicators are detected.
To get started, enable the threat intelligence enrichment feature in the Logging Analytics Geolocation function, specifically the Field Enrichment Option of a log source.
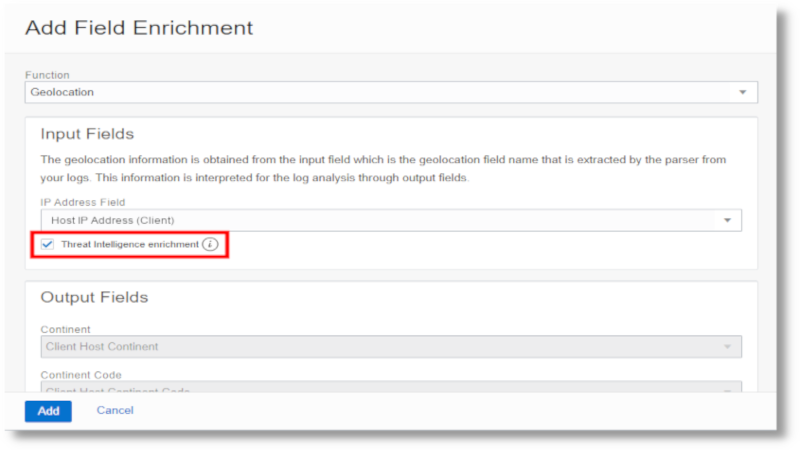
For complete steps to access the field enrichment option, see Logging Analytics Documentation.
Search for Threat Actors, Know Your Enemy
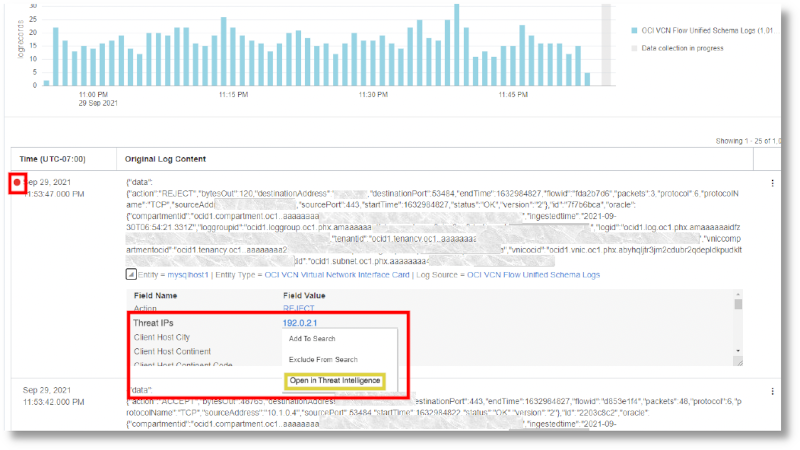
During the ingestion of the log data, if the IP address value associated with the IP Address field of the function is flagged as a threat, then it is added to the Threat IPs field and displayed as below:
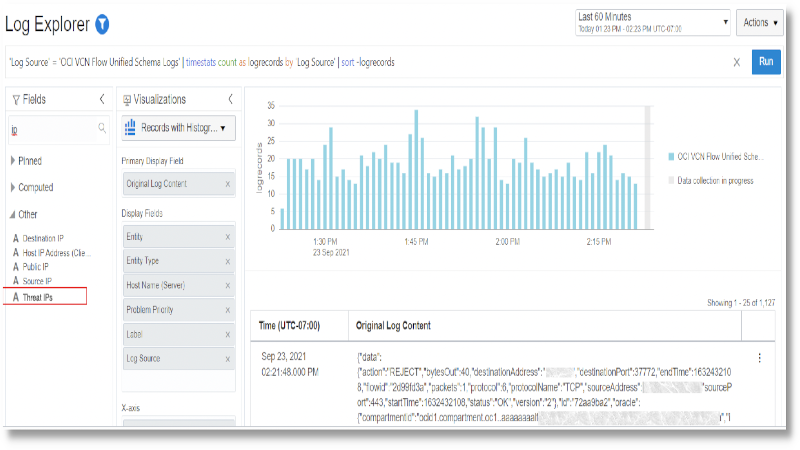
Use the field to filter the logs that have threats associated with them:
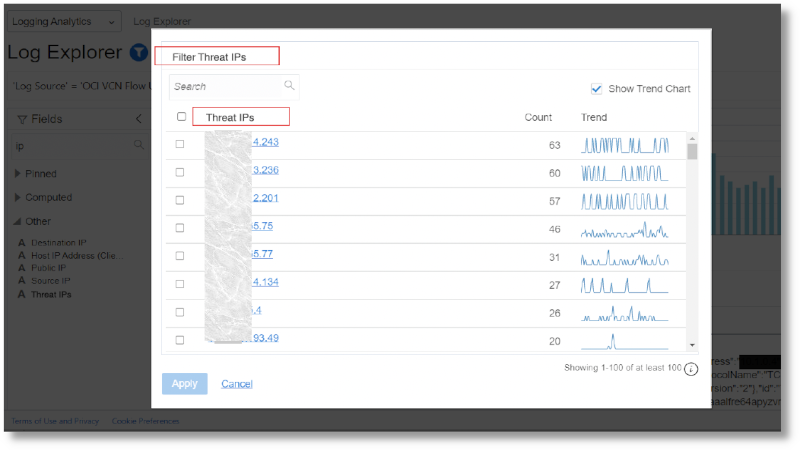
To learn more about filtering logs using fields in the log content, see Logging Analytics Documentation.
The log records annotated with threats will also have a Threat Intelligence Finding label with a problem priority High that can be used in your search. Additionally, the log records that have problem priority High associated with them have a red dot in the row. This makes those log records more prominent in their appearance in the table, making it easy to spot and analyze them.
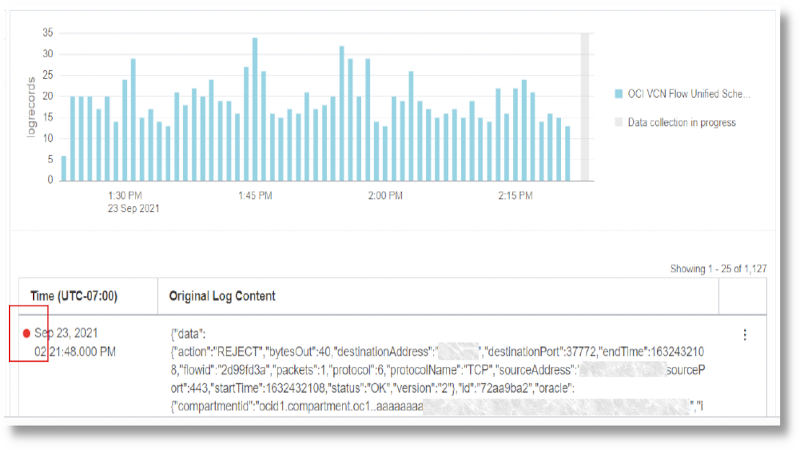
To obtain more information about the threat, open the Threat IPs in Oracle Threat Intelligence:
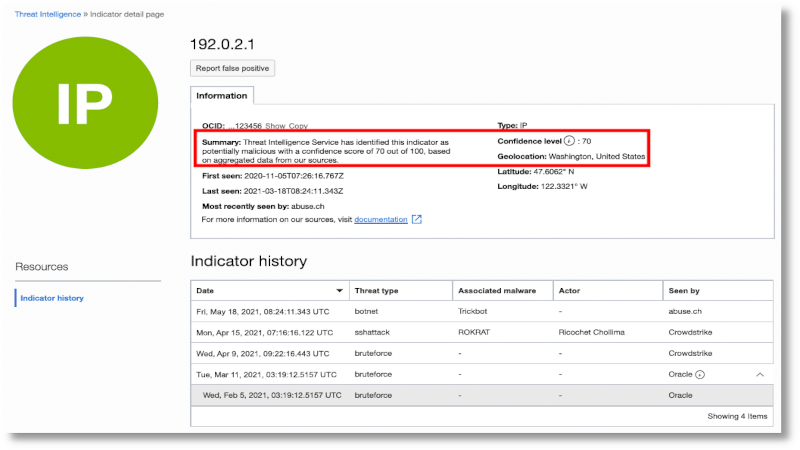
The following example shows the details of a threat with a confidence level of 70. Overall confidence refers to the likelihood that an indicator might be associated with malicious behavior. A value of 0–100 represents how confident Threat Intelligence is that the indicator might be associated with malicious activity.
Understand the Threat Patterns
With the availability of three key parameters such as Threat IPs field, Threat Intelligence Finding label, and problem priority High associated with the logs, perform advanced analytics of the threat using options like Cluster, Link, Link by Cluster and Cluster Compare. These advanced Logging Analytics tools can help group the threats based on the confidence level and the threat types.
Logging Analytics provides the lookup TIS Threat Feeds which is a repository of the recognized malicious IP addresses that can be used for log enrichment with additional parameters at query-time. See Query Search.
Get Real-Time Alarms upon Detecting Pre-Identified Threat Actors in the Ingested Logs
When a continuous log collection is set up, it becomes critical to get notified of incoming threats as soon as your logs are ingested. Once the IP addresses that pose a threat have been identified using an analysis described in the previous sections, you can use this valuable information to set up alert notifications.
- Create a detection rule to detect log records that have threatful IP addresses at ingest-time. The detection rule can be based on the label Threat Intelligence Finding and more additional filters like entity type and log source. See Detect Predefined Events at Ingest Time and Allow Users to Perform Ingest Time Alert Rule Operations.
- Create an alert in the Monitoring service which gets triggered every time the filter parameters are encountered in the ingested logs. See Create Alerts for Detected Events.
With this, the detection of pre-identified threats is near real-time.
To summarize, the integration of Logging Analytics with Threat Intelligence Service is a great step towards helping pin down malicious IP addresses, which are one of the major threat actors identified in the security industry. Logs enable the automation of a security strategy to mitigate threats.
For more help and examples on advanced analytics, see Logging Analytics Documentation:
- Clusters Visualization
- Cluster Compare Utility
- Link Visualization
- Link By Cluster
- Typical Advanced Analytics Use Cases
