OCI Application Performance Monitoring provides application observability through a distributed tracing service, enabling end-to-end visibility into the performance and availability of every component in the application.
Oracle Threat Intelligence Service aggregates threat intelligence data across many different sources and manages this data to provide actionable guidance for threat detection and prevention in Oracle Cloud Guard and other Oracle Cloud Infrastructure services. See Threat Intelligence for more details on its specific capabilities.
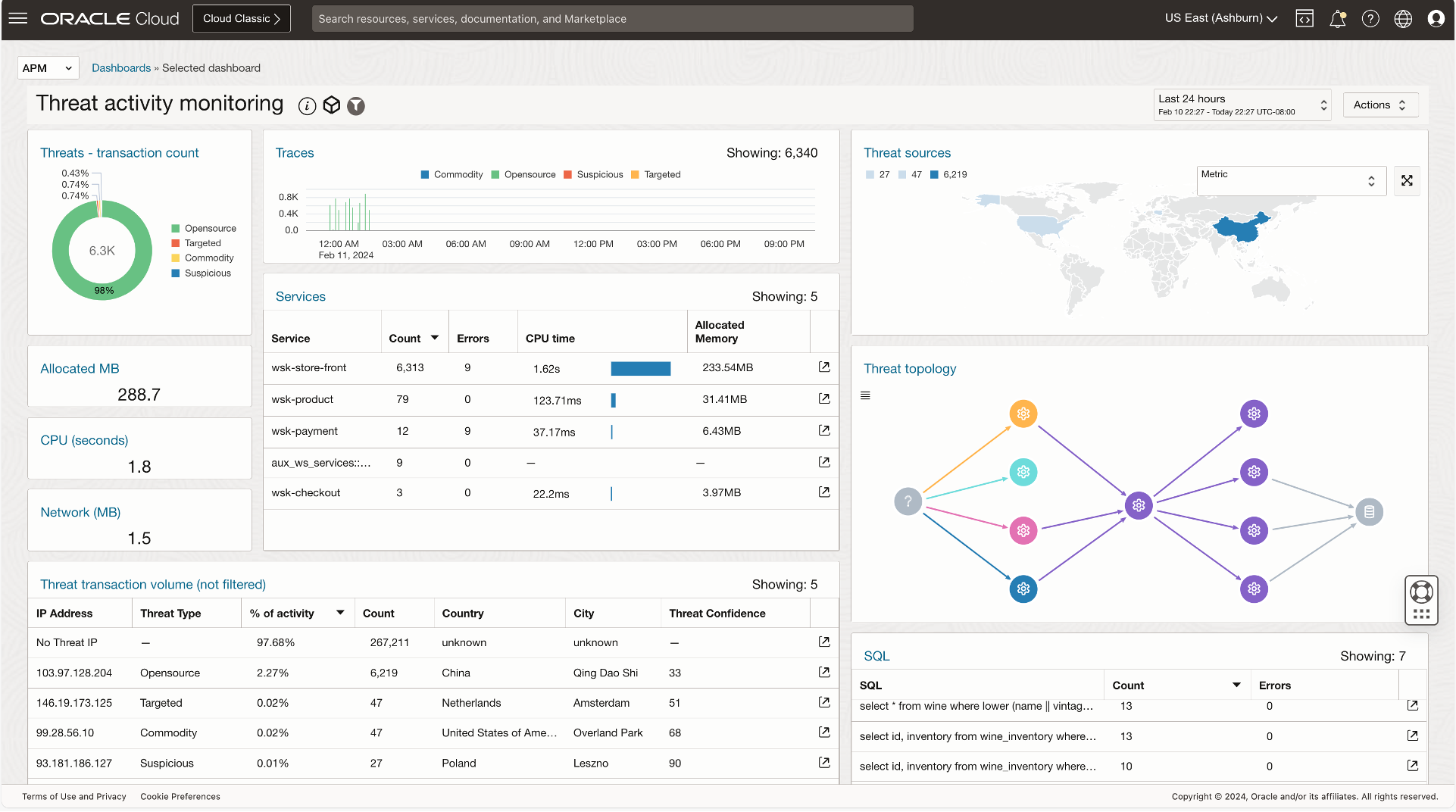
A new integration has been released that enables application transaction data from APM to be enriched with Threat Intelligence data. Customers can now utilize the APM instance-level monitoring to get visualization and alerting when sources that have been identified as threats access an application and/or infiltrate its backend.
With Threat Activity Monitoring, users of OCI APM can obtain near real-time alerts for each suspicious UI activity, REST call, or other interaction with an application. A second set of alerts can be fired when the suspicious interaction reaches deeper into the application. The Threat activity monitoring dashboard visually displays penetration into backend services, execution of sensitive code, and even data retrieval from databases.
To see what this new integration can do for you, view the 7-minute video demonstrating how potential damage from clients identified as threats is evaluated to prevent potential damage: Application Security – Threat activity monitoring with OCI APM
Key advantages of the solution:
- Access alerts: Early alerts based on threat type and confidence score
- Penetration alerts: Alert on invocation of sensitive downstream components and data sources
- Out-of-the-box dashboard: Visualize threats and threats and all impacted components in one view
- Cost metrics: Assess the application cost (CPU, network memory) of high-volume attacks
- Contextual drill down: Punch out to the APM Trace Explorer for next-level investigation.
- Analytics: Use Trace Explorer to find earlier interactions, and similar usage patterns, to identify new threats
This capability is available to OCI APM customers to use at no additional cost.
For more information on:
Resources
