We’re pleased to share the general availability of Bring Your Own Certificate (BYOC) in MySQL HeatWave Service (MHS) on Oracle Cloud Infrastructure (OCI).
By default, all MySQL connections are secured through a MHS-defined certificate. BYOC extends the service by allowing users to select their own certificates to be used by the MySQL Server. With a few clicks, you can now set up your secured connections for MySQL HeatWave Service. The service facilitates both mutual TLS (requiring a connection wallet for the client) and one-way TLS, allowing clients to connect without necessitating a wallet. The latter option is particularly beneficial for accommodating legacy applications that may pose challenges in terms of modification to support wallets.
Certificates signed by a reputable Certificate Authority (CA) offer extra confidence to client applications, ensuring they are communicating with the intended database host and bolstering security against Man-in-the-Middle (MITM) attacks.
Key Highlights:
DB System Creation Flow:
During the initial DB System setup, choose the option to configure user-defined certificates to your specific requirements right from the beginning.
Update Option:
If you already have an established Database System and wish to reinforce its security by integrating user-defined certificates, the update option discussed later provides a straightforward solution.
Getting started
Create DB System with security certificate
In the OCI console, navigate to Databases, MySQL HeatWave, and on the DB Systems page, click Create DB Systems to go through the workflow to create a DB System. To configure secure connectivity, scroll to the bottom of the page and click on Show advanced options.
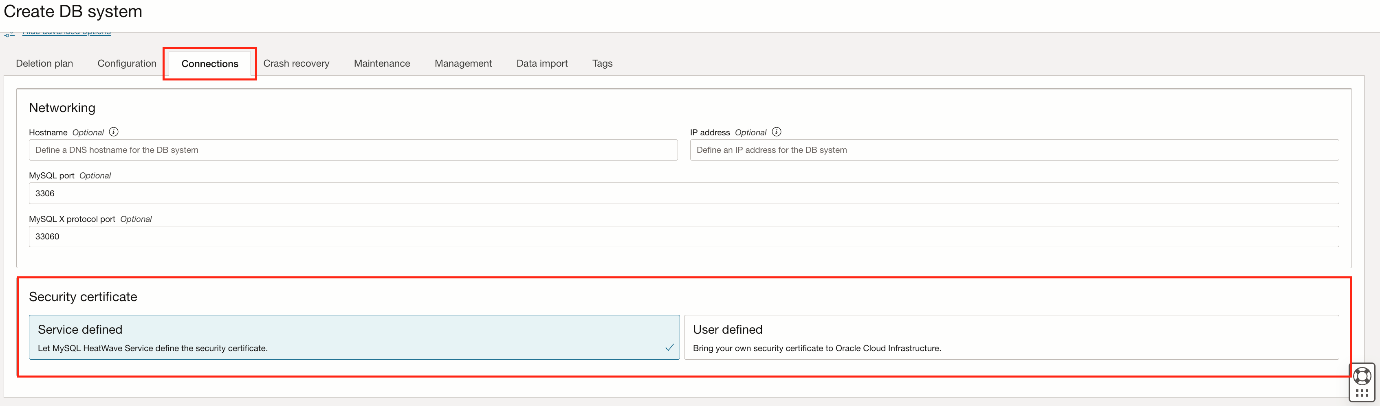
In the Connections tab, choose between letting MHS define a security certificate and selecting your own. In the User defined section, you can choose the certificate from a list or enter the Certificate Oracle cloud unique identifier (OCID).
Service defined
If you select Service defined, MHS will use a self-signed security certificate for establishing secured connections.
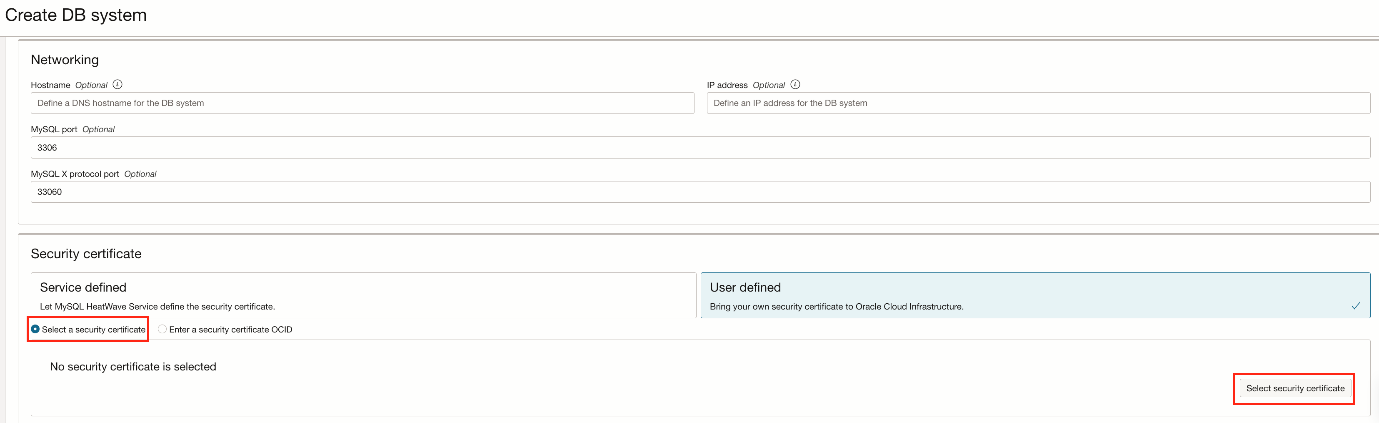
User Defined, select from a list
Mark Select a security certificate and click on Select security certificate.
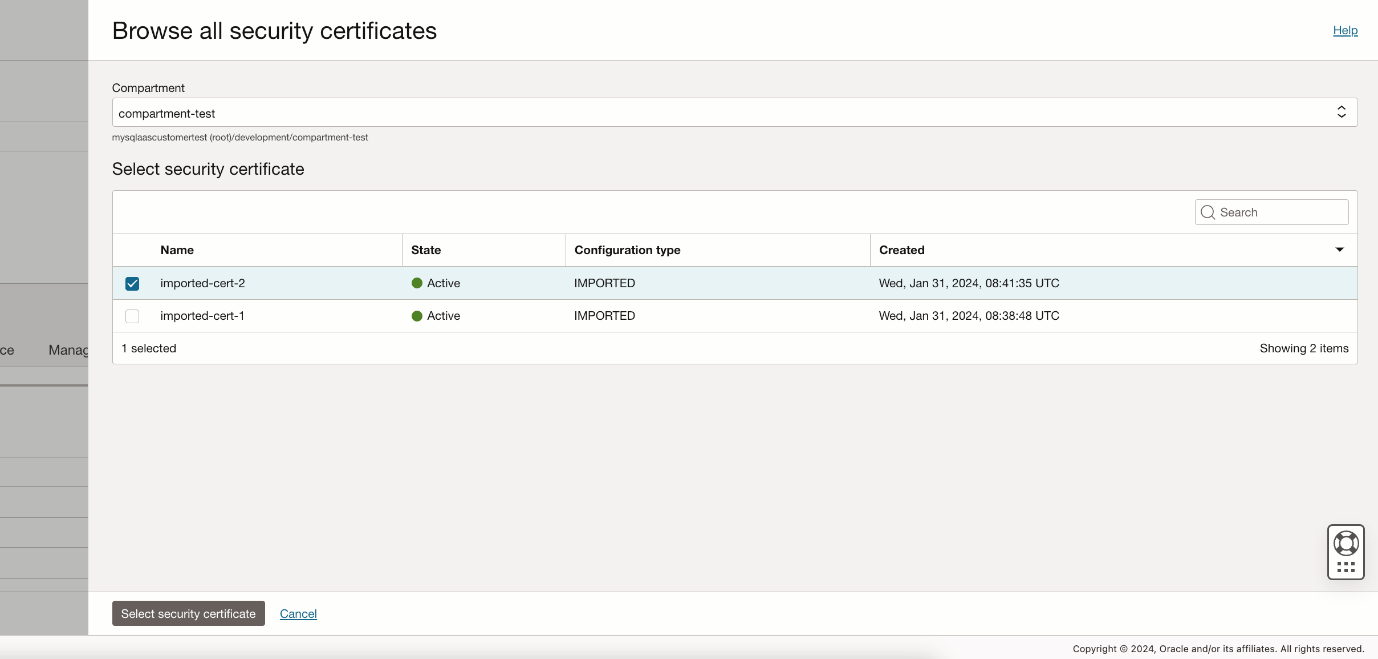
In the modal window you can browse and select the certificates by compartment.
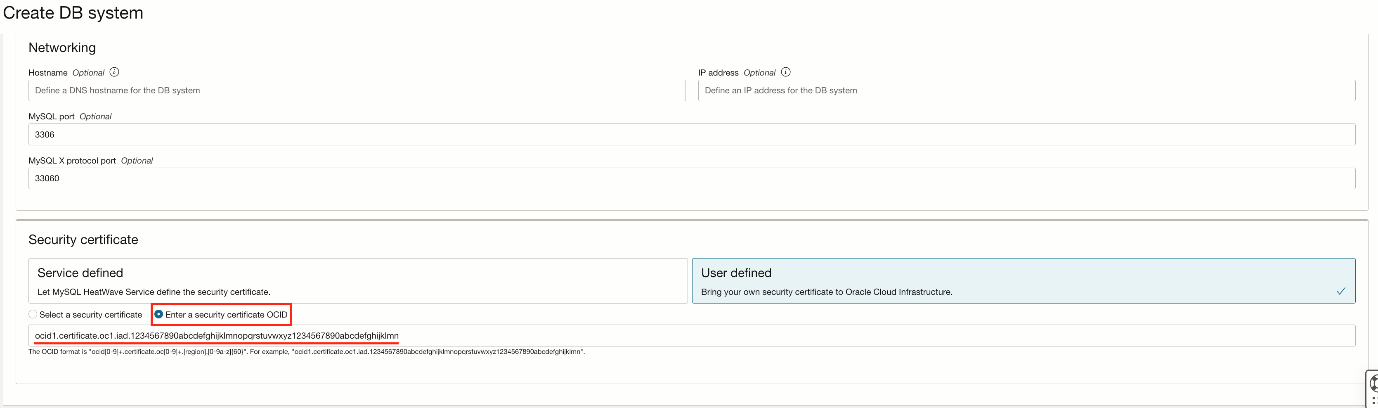
User Defined, input the certificate OCID
Lastly, you can input the certificate OCID, instead of choosing the certificate from a list. Entering the OCID can be quicker or the only option if your user permissions are limited and you can’t browse the certificates by a specific compartment.
Choose the option Enter a security certificate OCID and enter the OCID in the field.
Additional notes and pre-requisites
Security certificates are managed in the OCI Certificates Service and must have the appropriate policies configured. You need to create a dynamic group, activate resource principal in MHS, craft the necessary policy for the desired DB Systems, and leverage the enabled resource principal to retrieve the certificate from the OCI Certificate Service. For additional information, refer to:
- Documentation on how to dynamic groups and required policies.
- Documentation on how to create a Certificate.
- Documentation on how to create a Certificate Authority.
- Documentation on how to create a CA Bundle.
If you choose a revoked or expired certificate, the DB system creation succeeds, but the MySQL connections will fail. You can update the security certificate of an existing DB system, as explained in the section Update DB System as explained below.
Update DB System security certificate
You can change the security certificate of an existing DB system. You can update from Service defined to User defined, and vice versa. In the OCI console, navigate to Databases, MySQL HeatWave, and on the DB Systems page, click the DB Systems resource of your interest and to go DB system details page select the connections tab and under security certificate, and click on edit.
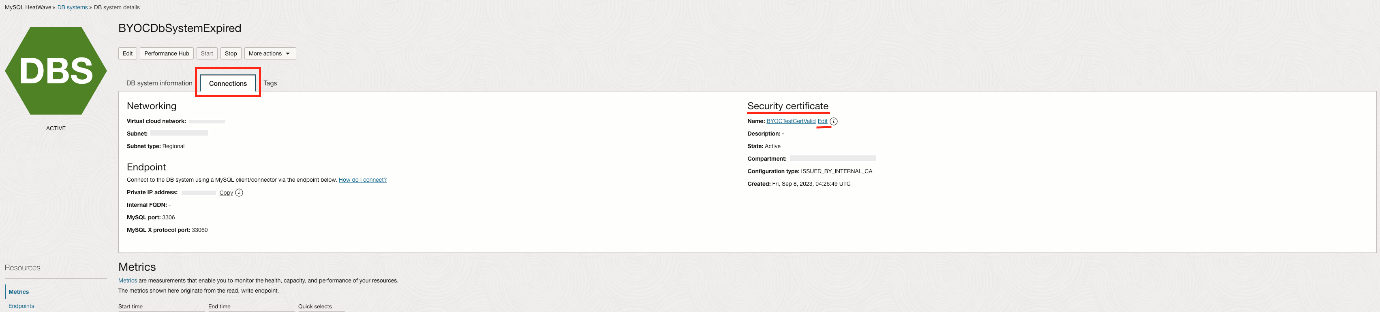
The Edit link brings you to the same options displayed during Create DB system. You can choose between Service and User defined, and when in User defined, you can select the certificate from a list or input the certificate OCID in the field.
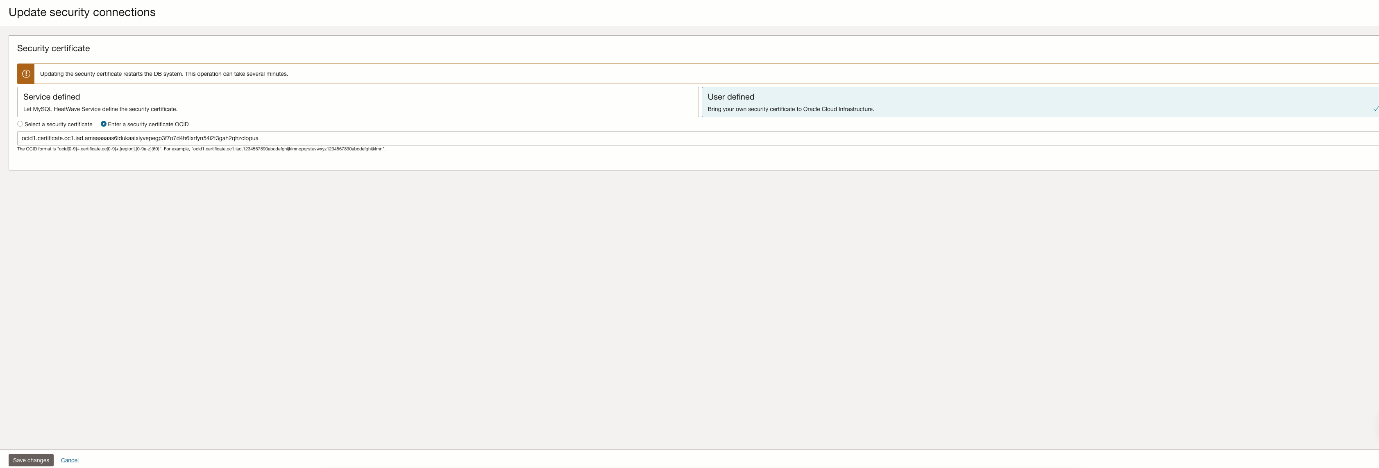
Once you’re finished, you save the changes. The operation restarts the DB system and can take several minutes.
Configuring Encrypted Connections
In certain MySQL setups, it may be necessary to employ encrypted connections, for instance, to meet regulatory mandates. This segment outlines the configuration options available in MHS that facilitate this requirement, providing various levels of control:
It’s possible to instruct specific client programs to demand an encrypted connection, irrespective of whether the server allows it, but doesn’t insist on encryption.
To activate a client program, making it necessitate an encrypted connection regardless of whether the server mandates encryption, utilize an –ssl-mode option with a value of REQUIRED, VERIFY_CA, or VERIFY_IDENTITY. For instance:
mysql --ssl-mode=REQUIRED
mysqldump --ssl-mode=VERIFY_CA
mysqladmin --ssl-mode=VERIFY_IDENTITY
Additionally, individual MySQL accounts can be configured to function exclusively over encrypted connections.
To configure a MySQL account to be usable only over encrypted connections, include a REQUIRE clause in the CREATE USER statement that creates the account, specifying in that clause the encryption characteristics you require. For example, to require an encrypted connection and the use of a valid X.509 certificate, use REQUIRE X509:
CREATE USER 'username'@'%' IDENTIFIED BY '<password>' REQUIRE X509;
For accounts created with a REQUIRE X509 clause, clients must specify –ssl-cert and –ssl-key. In addition, –ssl-ca is recommended so that the public certificate provided by the server can be verified. For example:
mysql --host <DBSystemEndpointIPAddress> -u <Username> -p --ssl-key=client-key.pem --ssl-cert=client-cert.pem --ssl-ca=ca.pem --ssl-mode=REQUIRED -P 3306 -u myadmin -p
For the client certificate, you should create a new certificate through the OCI Certificates service. This new certificate must have the same CA as the certificate provided in “User Defined” during the DB system creation.
The client certificate’s private key and certificate pem files should be provided in –ss-key and –ssl-cert parameters.
For more details on using encrypted connections, see Using Encrypted Connections.
Summary
With this new feature, you can embark on a journey where your database security aligns perfectly with your specific security requirements.
Whether creating a new database or updating an existing one, adapt the configuration to your evolving security requirements and bolster the security of your database with personalized certificate settings, ensuring a robust defense against potential threats.
Dive in and start configuring Bring Your Own Certificate (BYOC) effortlessly!
Try MySQL HeatWave Service with BYOC today. If you don’t have an OCI account, visit here and create one for free.
To learn more about MySQL HeatWave, visit here.
Additional Resources
- Hands-on Lab: Get Started with MySQL HeatWave and Feel the Difference
- Videos: Getting Started with MySQL HeatWave
- Blogs: MySQL HeatWave
- Documentation: MySQL HeatWave

