Introduction
In our previous blog post, we introduced the concept of Bring Your Own Certificate (BYOC) for HeatWave MySQL, highlighting its benefits and implementation. In this follow-up, we delve deeper into the critical policy and security requirements necessary to leverage this feature effectively. Ensuring robust security and compliance, BYOC allows users to select their own certificates for MySQL connections, enhancing protection against potential threats such as Man-in-the-Middle (MITM) attacks. This post will guide you through the essential steps, including configuring dynamic groups, activating resource principals, and crafting the necessary policies within the Oracle Cloud Infrastructure (OCI) Certificates Service, to securely integrate user-defined certificates into your HeatWave MySQL environment.
High level steps
- Create a dynamic group to group HeatWave MySQL DB systems as principal actors.
- Create a policy to grant the dynamic group to read the certificates. This way, the DB system resource can access the Certificate resource.
- Add CERTIFICATE_READ permission to user. CERTIFICATE_READ is the minimum required permission. You can also use leaf-certificate or leaf-certificate-family resource types, which includes CERTIFICATE_READ. See Policy Reference for Certificates Service.
Step 1
Create a dynamic group to group resource type ‘mysqldbsystem’
- Go to Identity & Security and click on Dynamic Groups.
Figure 1: Dynamic Groups menu
- Click on Create Dynamic Group and provide the name, description and a matching rule containing the resource type mysqldbsystem.
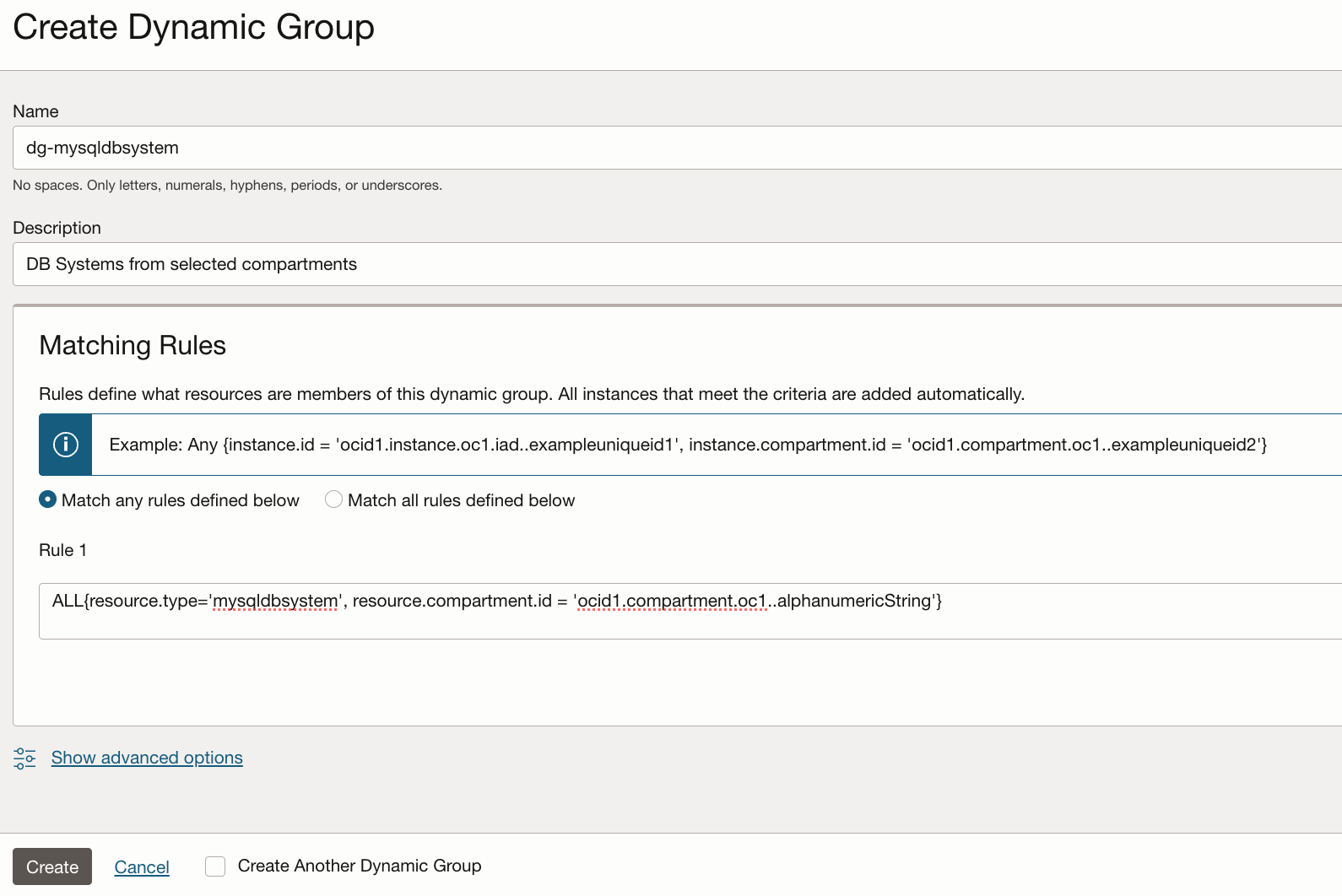
Figure 2: Create Dynamic Group
The following example shows a matching rule including all HeatWave MySQL DB systems in the defined compartment:
ALL{resource.type='mysqldbsystem', resource.compartment.id = 'ocid1.compartment.oc1..alphanumericString'}
- Click on Create
Step 2
Create a policy to allow the dynamic group to read the certificates
- Go to Identity & Security and click on Policies.
Figure 3: Policies menu
- Select a compartment, click Create Policy and enter the policy on the next screen. The following example shows a policy allowing the dynamic group to read certificates in the defined compartment. Allow dynamic-group dg-mysqldbsystem to read leaf-certificate-family in compartment development
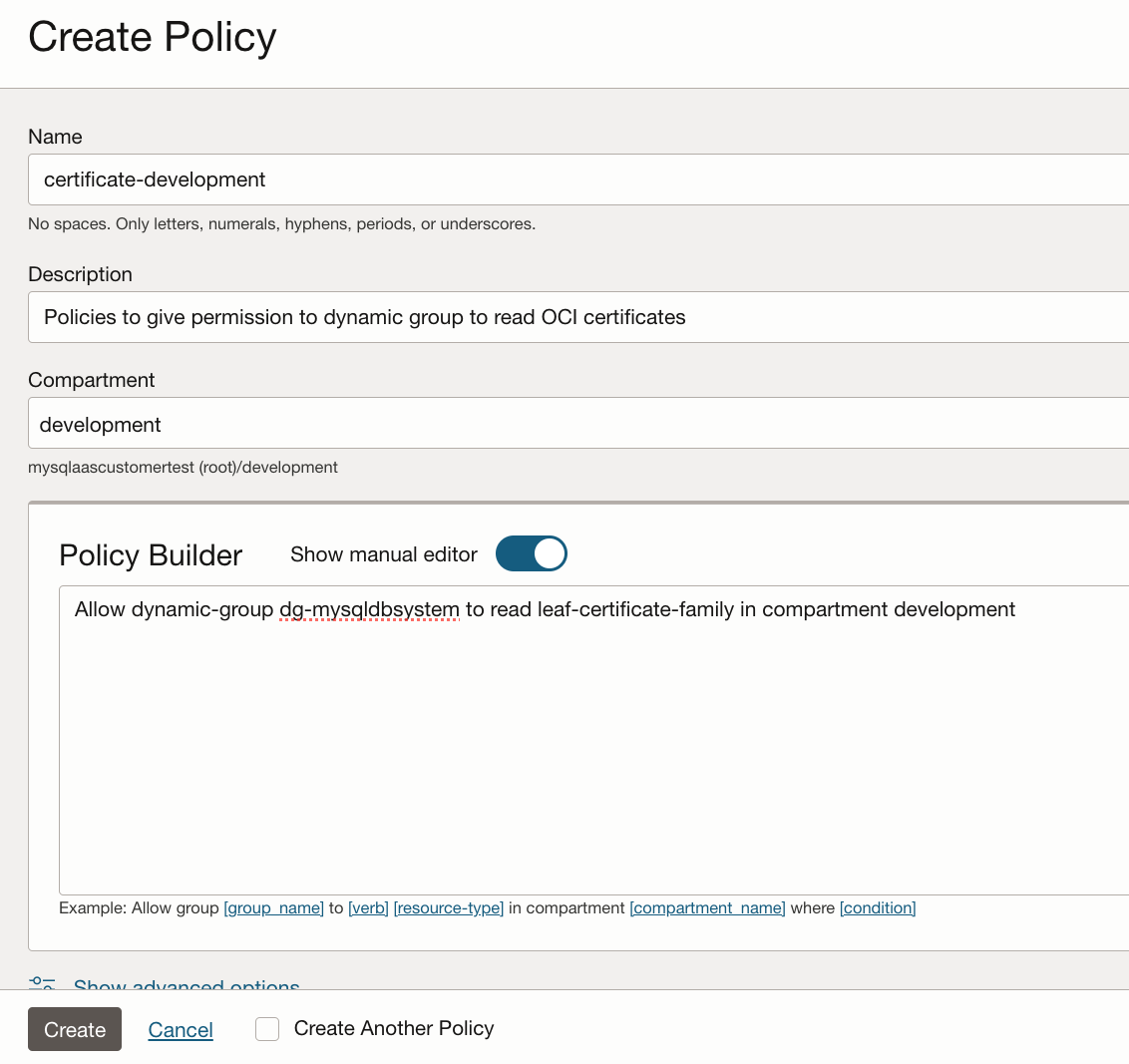
Figure 4: Create Policy
- Click on Create
Note: “dg-mysqldbsystem” and “development” are only examples. You can choose any name. The dynamic group name must match the one you created, and the compartment must be where the certificates are created.
Step 3
Add CERTIFICATE_READ to user
CERTIFICATE_READ is the minimum required permission. You can also use leaf-certificate or leaf-certificate-family resource types, which includes CERTIFICATE_READ. See Policy Reference for Certificates Service.
Similar to creating a policy to allow the dynamic group to read certificates, create another policy with the following statement:
Allow group <group_name> to {CERTIFICATE_READ} in compartment <compartment_name>
Using policy resource type should also work:
Allow group <group_name> to read leaf-certificates in compartment <compartment_name>
Additional note
This article’s scope is to guide you on setting up policies and permissions for BYOC. For more details on certificates set up in the OCI Certificates service, see these other documentation.
Refer to This documentation on how to create a Certificate.
Refer to This documentation on how to create a Certificate Authority.
Refer to This documentation on how to create a CA Bundle.
For more information, see Resource Principals and Mandatory policies and permissions. To understand better dynamic groups and policies, see Managing Dynamic Groups and How Policies Work.
Additional Resources
