Introduction
This is the first part in a 6-part series of blogs that discusses the common topics for the Oracle Access Manager (OAM) WebGate component.
In no specific order the topics will include but are not limited to:
- Certification
- Software Downloads
- Installation
- Configuration
- Registration
- Highly Available Architecture
- Communication
- Changing Simple to Cert mode
This series of blogs will focus on the Oracle Access Manager (OAM) 12.2.1.4.0 version of the Access server and its certified and supported components.
The Oracle Access Manager Team recommends being at the latest product version release, patch-set, and Bundle Patch that is available for the specific component being used. This helps ensure that you have the latest fixes/product functionality and helps avoid unnecessary rediscovery of known issues.
- Stack Patch Bundle for Oracle Identity Management Products (Doc ID 2657920.1)
- OAM Bundle Patch Release History (Doc ID 736372.1)
Overview
Interchangeable Terms
|
A WebGate is a web-server plug-in for Oracle Access Manager (OAM) that intercepts HTTP requests and forwards them to the Access Server for authentication and authorization.
It communicate with the Access Manager server using the secure Oracle Access Protocol (OAP). Policies are created and maintained by administrators through the Oracle Access Management console, which acts as the central Policy Administration Point (PAP). These policies are stored in the Policy Store, using an Oracle database. As an authenticated user tries to access different applications and resources, the runtime Access Manager server acts as Policy Decision Point (PDP) evaluating whether the user is authorized to access a particular resource. It then conveys that information back to the WebGate for enforcement. Every action gets logged for audit purposes. It is a Policy Enforcement Point (PEP) deployed with Web Server and communicates to OAM Servers (Policy Decision Point – PDP). WebGates communicate to OAM Access Server on proxy port (default value 5575) and default security mode OPEN. Securing communication between OAM Servers and clients (WebGates) means defining the transport security mode for the Network Access Protocol (NAP), also known as the OAP, channel.
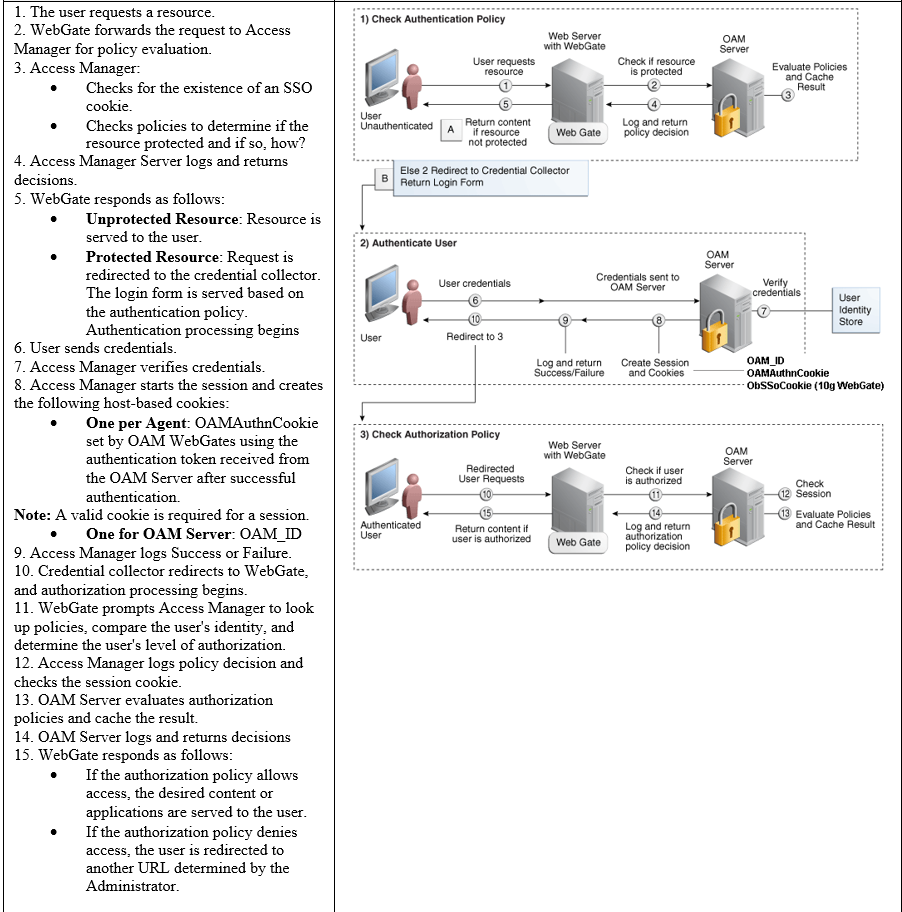
Single Sign-On (SSO) Login Process With OAM WebGates And The Embedded Credential Collector (ECC)
Access Manager authenticates each user with a customer-specified authentication method to determine the identity and leverages information stored in the user identity store.
This topic is based on using the default Embedded Credential Collector with OAM Agents (Resource WebGates) protecting resources.
Access Manager authentication supports several authentication methods and a number of authentication levels. Resources with varying degrees of sensitivity can be protected by requiring higher levels of authentication that correspond to more stringent authentication methods.
When a user tries to access a protected application, the request is received by Access Manager which checks for the existence of the SSO cookie.
After authenticating the user and setting up the user context and token, Access Manager sets the SSO cookie and encrypts the cookie with the SSO Server key (which can be decrypted only by the SSO Engine).
Depending on the actions (responses in Access Manager 11g) specified for authentication success and authentication failure, the user may be redirected to a specific URL, or user information might be passed on to other applications through a header variable or a cookie value.
Based on the authorization policy and results of the check, the user is allowed or denied access to the requested content. If the user is denied access, she is redirected to another URL (specified by the Administrator in WebGate registration).
The below figure shows the processes involved in evaluating policies, validating a user’s identity, authorizing the user for a protected resource, and serving the protected resource. This example shows the OAM Agent flow. There are slight variations with 12c WebGates/Access Clients.
Process overview: SSO Login Processing With Embedded Credential Collector And OAM Agents
Wrap Up
The OAM WebGate is a software/plugin installed on the HTTP Server and act as a Policy Enforcement Point (PEP). The OAM WebGate is a gatekeeper to secure the resources and manage all interactions with the user who is trying to access the resources. All the Authentication & Authorization policies are stored in a database accessed by the OAM Server. The OAM Agent ask the OAM Server if a user can get the access to a particular resource. If the OAM Server accept, the user will receive the resource that were demanded.
WebGate: Installed on the HTTP Server. The OAM WebGate acts as a Policy Enforcement Point (PEP). It intercepts incoming requests to protected resources and communicates with the OAM Server to enforce authentication and authorization policies.
Policy Enforcement Point (PEP): The WebGate component, functions as a PEP. It’s responsible for intercepting requests to resources and enforcing access policies based on instructions from the OAM Server.
Securing Resources: The primary role of the WebGate is to secure resources by enforcing access policies. This involves checking the user’s authentication status and determining whether the user is authorized to access the requested resource.
User Interaction: When a user attempts to access a protected resource, the OAM Agent/WebGate comes into play. It manages the interaction between the user and the access control mechanism, ensuring that the user goes through the appropriate authentication and authorization steps.
Authentication and Authorization Policies: These policies, which dictate who can access what resources under what conditions, are stored in a database that is accessed by the OAM Server. The OAM Server manages these policies and communicates with the OAM WebGate to enforce them.
This 6-part series of blogs will help provide a central location for the common topics related to the Oracle Access Manager (OAM) WebGate component.
List of Upcoming Blogs
- Oracle Access Manager (OAM) WebGate Guide -Part2 – Certification
- Oracle Access Manager (OAM) WebGate Guide -Part3 – Software Downloads/Installation/Configuration/Registration
- Oracle Access Manager (OAM) WebGate Guide -Part4 – Highly Available Architecture
- Oracle Access Manager (OAM) WebGate Guide -Part5 – Communication
- Oracle Access Manager (OAM) WebGate Guide -Part6 – Changing Simple To Cert Mode
Related Articles:
- Introduction Simplify Knowing Your Identity and Access Management – This is an introduction to a 6-part series that deals with ways to improve many aspects of an Administrators Duties; such as upgrade, maintenance and overall ease of resolving environment issue with Oracle products.
