Introduction
Last month I wrote a blog titled “Oracle Access Manager (OAM) product’s User Identity Stores”. As promised this month’s blog will cover the Steps to Register a System Identity Store other than the Out of box (OOB) default System store, the embedded Weblogic Server.
General Concept
During the initial WebLogic Server domain configuration using the Oracle Fusion Middleware Configuration Wizard, the Embedded LDAP is configured as the one and only user identity store for Oracle Access Management. For the purpose of this blog, we will only be speaking about how to set up the remote User Store as the System Store. A key point to remember is that only one User Identity Store can, and must be, designated as the System Store.
Initially, a System Administrator user must log in to the Oracle Access Management Console using the WebLogic Administrator credentials set during initial configuration. However, your enterprise might require independent sets of Administrators: one set of users responsible for Oracle Access Management administration and a different set for WebLogic administration.
At A High Level
The process of defining and configuring an external LDAP as the System store is a little different than it was in 11g as in 12c the IAMSuiteAgent is no longer used or available. Because of this the OAMAdminConsoleScheme will not need to be changed unless the OAM console is protected by a WebGate. For more details about the IAMSuiteAgent is discussed in a prior blog “Oracle Access Manager 12c-Insights To The OAM Console And The IAMSuiteAgent”
Steps
- Set Identity Store as System
- Configure an External LDAP as an Authentication Provider in the Oracle WebLogic Server
Steps When Protected by a WebGate
- Set Identity Store as System
- Set LDAP Authentication Module that the OAMAdminConsoleScheme uses
- Configure an External LDAP as an Authentication Provider in the Oracle WebLogic Server
Prerequisites
The following criteria are the prerequisites for the steps to be followed:
- A User with valid Oracle Access Management System Administrator credentials. Since this is a Out of Box configuration the username is “weblogic” and the group is “Administrator”
- The Identity store has already been registered and tested. For this test we will be using Oracle Unified Directory (OUD).
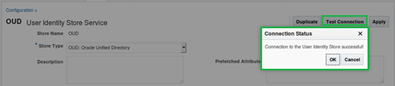
- That you are now going to make this store the System Identity Store and that the current System Identity Store is the OOB embedded LDAP. Note that the UserIdentityStore1 Access and System Administrators has a group of “Administrators” and a user of “weblogic”.

- Another way to validate that the embedded LDAP store (useridentitysore1) is by searching in the <OAM_HOME>/oam/server/config/oam-config.xml file. First make a copy of this file to be used later to compare after the changes are made. Then Search for
“<Setting Name=”IsSystem” Type=”xsd:boolean”>true</Setting>“
The following is what is seen in an Out of box install …
<Setting Name=”LDAP” Type=”htf:map”>
<!– LDAP Authentication Configuration. Default to embedded LDAP –>
<Setting Name=”UserIdentityStore” Type=”htf:map”>
<Setting Name=”Name” Type=”xsd:string”>UserIdentityStore1</Setting>
<Setting Name=”Type” Type=”xsd:string”>LDAP</Setting>
<Setting Name=”LDAP_URL” Type=”xsd:string”>ldap://ldap-host:7001</Setting>
<Setting Name=”SECURITY_PRINCIPAL” Type=”xsd:string”>cn=Admin</Setting>
<Setting Name=”SECURITY_CREDENTIAL” Type=”xsd:string”>{AES}F8E3A9FAD9D662F753D842979423ED3D</Setting>
<Setting Name=”USER_SEARCH_BASE” Type=”xsd:string”>ou=people,ou=myrealm,dc=base_domain</Setting>
<Setting Name=”GROUP_SEARCH_BASE” Type=”xsd:string”>ou=groups,ou=myrealm,dc=base_domain</Setting>
<Setting Name=”USER_NAME_ATTRIBUTE” Type=”xsd:string”>uid</Setting>
<Setting Name=”LDAP_PROVIDER” Type=”xsd:string”>EMBEDDED_LDAP</Setting>
<Setting Name=”UserIdentityProviderType” Type=”xsd:string”>OracleUserRoleAPI</Setting>
<Setting Name=”IsPrimary” Type=”xsd:boolean”>true</Setting>
<Setting Name=”IsSystem” Type=”xsd:boolean”>true</Setting>
<Setting Name=”RoleMappings” Type=”htf:map”>
<Setting Name=”Role Security Admin” Type=”htf:map”>
<Setting Name=”Groups” Type=”xsd:string”>Administrators</Setting>
<Setting Name=”Users” Type=”xsd:string”>weblogic</Setting>
</Setting>
<Setting Name=”Role System Monitor” Type=”xsd:string”>Monitors</Setting>
<Setting Name=”Role Application Administrator” Type=”xsd:string”>Operators</Setting>
<Setting Name=”Role System Manager” Type=”xsd:string”>Deployers</Setting>
Steps To Define/Configure …
An External LDAP As An OAM System Identity Store
Set Identity Store as System
1. Open a new browser session and access and login into the OAM console as the weblogic user
http://servername.domain:port/oamconsole
Example -http://<HOSTNAME>.<DOMAIN>.com:<PORT>/oamconsole
2. Navigate to System Configuration tab, User Identity Stores
3. In the section “Default and System Store” select the drop-down arrow for “System Store”
4. Select the Store that will be defined as the System store (in this case OUD)
5. Add system administrator Roles
- In the “Access System Administrator” section select the “Add” button.
- A Windows will open called “Add System Administrator Roles” , in the Name field, enter * (asterix) to search all users and groups or search for a specific name.
- Select the user or group and add them as system administrators. (in this case user.1”)
6. Apply….the following pop up is displayed
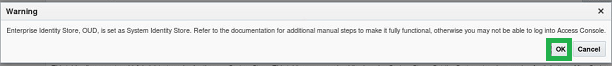
7. Select OK button
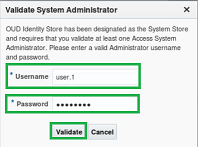
9. A pop up asking you to Validate the System Administrator will appear…
Enter a valid admin user (The user from Step 5) and password.
10. Select the validate button
11. A confirmation windows will appear.

- This completes the first of three parts, Setting the Identity Store as System
Configure an External LDAP as an Authentication Provider in the Oracle WebLogic Server
The Oracle WebLogic Server includes LDAP Authentication providers to give access to user information contained in several common LDAP identity stores.
It includes LDAP Authentication providers for identity stores such as Oracle Internet Directory, Oracle Virtual Directory, Oracle Unified Directory, and more. The full set of included LDAP Authentication providers are as follows:
- Oracle Internet Directory Authentication provider
- Oracle Virtual Directory Authentication provider
- Oracle Unified Directory Authentication provider
- iPlanet Authentication provider (for Oracle Directory Server Enterprise Edition)
- Active Directory Authentication provider
- Open LDAP Authentication provider
- Novell Authentication provider
- Generic LDAP Authentication provider
Each LDAP Authentication provider stores user and group information in an external LDAP server. They differ primarily in how they are configured by default to match typical directory schemas for their corresponding LDAP server. For information about configuring the Oracle Internet Directory and Oracle Virtual Directory Authentication providers to match the LDAP schema for user and group attributes.
WebLogic Server does not support or certify any particular LDAP servers. Any LDAP v2 or v3 compliant LDAP server should work with WebLogic Server. The following LDAP directory servers have been tested:
- Oracle Internet Directory
- Oracle Virtual Directory
- Oracle Unified Directory
- Oracle Directory Server Enterprise Edition (formerly known as Sun iPlanet)
- Active Directory shipped as part of the Microsoft Windows platform
- Open LDAP
- Novell Directory Service (NDS)
Steps
2. Select tab Providers -> Authentication. Notice …
DefaultAuthenticator
DefaultIdentityAsserter
Trust Service Identity Asserter
3. Select the Default Authenticator and change the Control Flag from REQUIRED to SUFFICIENT and save
4. Return to Security Realm; myrealm; Providers tab
5. Click on New to add new Authentication Provider
6. In the Type section select the drop down and choose the desired type. (In this case its OracleUnifiedDirectoryAuthenticator) …select OK
7. You should now see the new Authenticator listed, select it
8. Change control flag from OPTIONAL to SUFFICIENT for the Authentication Provider added above, select “SAVE”
9. Select Provider Specific tab and enter the external LDAP server details
Do not forget to change “User Base DN” and “Group Base DN” as per your External LDAP and save
10. Return to Security Realm;myrealm;Providers tab.
11.Click Reorder and order the providers as follows:
DefaultAuthenticator
OUDAuthenticator
DefaultIdentityAsserter
Trust Service Identity Asserter
-Select OK
12. Restart the WebLogic Admin Server and all managed servers in the IDM domain.
Only if the OAM console is protected by a WebGate
1. Refer to the section previously covered … “Set Identity Store as System”
2. Set LDAP Authentication Module that the OAMAdminConsoleScheme uses
a. Navigate to the back to the Launch Pad. Under the “Access Manager Section select, Authentication Schemes.
b. Edit the OAMAdminConsoleScheme, record the Authentication Module (LDAP)
c. Navigate to System Configuration tab, Access Manager Settings section, expand Authentication Modules, expand LDAP Authentication module
d. Edit the LDAP module
e. Change the User Identity Store from UserIdentityStore1 to the desired Identity store. Select the Apply button
3. Refer to the section previously covered … “Set LDAP Authentication Module that the OAMAdminConsoleScheme uses”
Oracle Documentation
Oracle® Fusion Middleware Administrator’s Guide for Oracle Access Manager with Oracle Security Token Service 11g Release 1 (11.1.1) Part Number E15478-06, Chapter 5
Managing Common Data Sources
Known Issue
Interesting thing to consider, I saw this while testing prior to this blog as well as in the past were once all the steps were done, you could access and log into the OAM console application, but then you would see a blank page.
This is covered in Oracle Access Manager 11g R2PS3 (OAM 11.1.2.3) OID Set As System Store Now OAM Console Page is Blank Empty White (Doc ID 2458138.1)
The solution from this KM note will work, but I dug a little deeper and found another solution.
The cause is that for some reason was the system store information was not saved correctly (unsure why). This was done in step 5 Add system administrator Roles. Even thought the Confirmation was successful it set the System store to a remote LDAP server. Unfortunately it did not have then new user and group, it kept the default user/password of “weblogic/password” and the Group of “Administrators”
What I did was create a Group in the external LDAP that was being used for the System store called “Administrator” and added the user defined in the previous steps (user.1) into that group. Now I was able to see the OAM console, no more blank page.
You could have also created a user called “weblogic” with the same password as in the imbedded ldap server to achieve the same results.
Once this was done I could now add the user and group I wanted (step 5 Add system administrator Roles) and remove the weblogic user and Administrators group.
As a prerequisite you may want to consider adding a group called administrators and a user called weblogic to the target external LDAP server.
Wrap up
Only one User Identity Store can (and must) be designated as the System Store. The Out of Box System Identity Store is the Weblogic embedded LDAP. This is used to authenticate Administrators signing in to use the Oracle Access Management Console, remote registration tools, and custom administrative commands in WLST. The supplied steps/information were tested with the Oracle Access Server (OAM) application, version 12.2.1.4.0.
As with any new concept you are going to implement, test in a lower environment. Validate and record what steps worked. Test multiple time and refine your documentation before implementing in production.
Related Articles:
- Understanding The Oracle Access Manager (OAM) User Identity Store – This blog covers the basic concepts of the Oracle Access Manager (OAM) product’s User Identity Stores.
le
