Enabling Trail File Encryption in GoldenGate is simple. With encrypted Trail Fils, the critical business data bases on the database records are secured. Note that the metadata (table names) is still visible for filtering purposes. Protecting the business data is important for many reasons: Compliance and legal requirements, Risk Mitigation, Enhanced Security and Data Integrity, and Trust & Confidence are some of them.
On the source GoldenGate deployment, you only must create a Master Key. Note that the Master Key is stored in a local Wallet, located in $OGG_VAR_LIB/wallet by default.
AdminClient(SRC)> ADD MASTERKEY
Even easier, you can use the WEB-UI instead of using AdminClient:
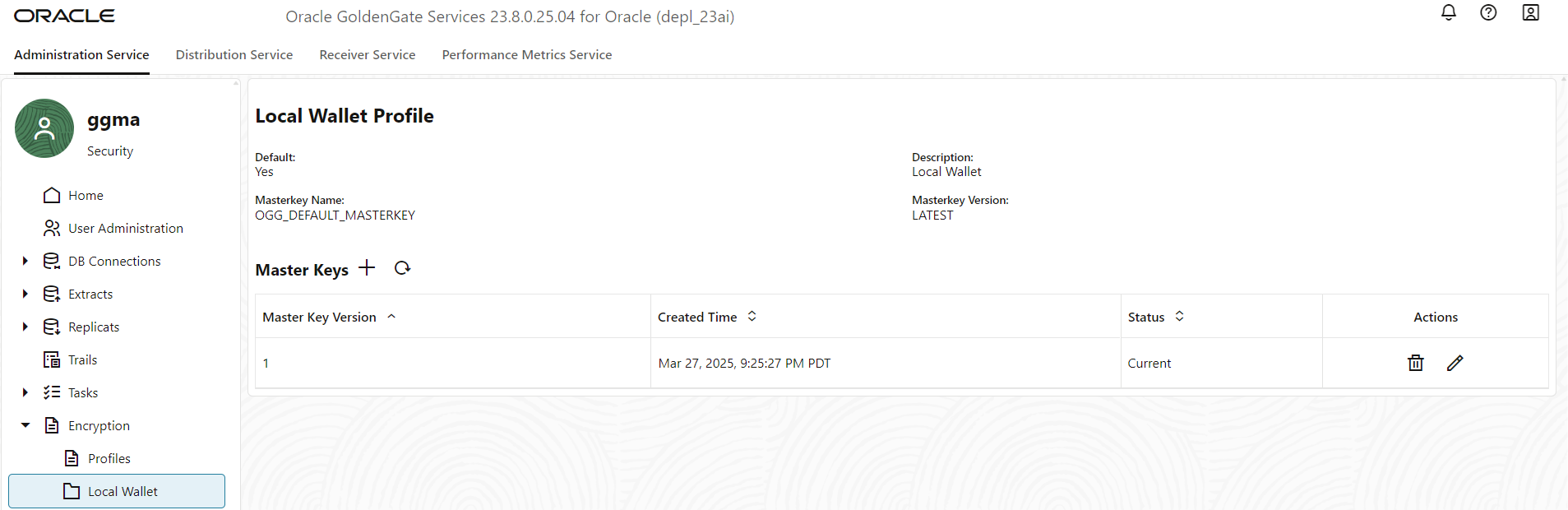
With GoldenGate Trail File Encryption, each Trail File generates a Data Encryption Key (DEK) that is used to encrypt the business data within the Trail File. While Extract encrypts the Trail File with this key, Replicat uses it for decryption. This DEK is encrypted using the Master Key. Therefore, the Master Key needs to be shared with the target destination. You have to securely transfer the Master Key from the $OGG_VAR_LIB/wallet directory to the GoldenGate target deployment.
With the created Master Key, you can specify the Encryption Algorithm within the Extract parameter file. You can choose from the AES128, AES192, and AES256 algorithms. Note that you place the ENCRYPTTRAIL keyword before the EXTTRAIL:
EXTRACT EXTA
USERIDALIAS ggnorth
ENCRYPTTRAIL AES256
EXTTRAIL north/ea
DDL INCLUDE MAPPED
TABLE hr.*;
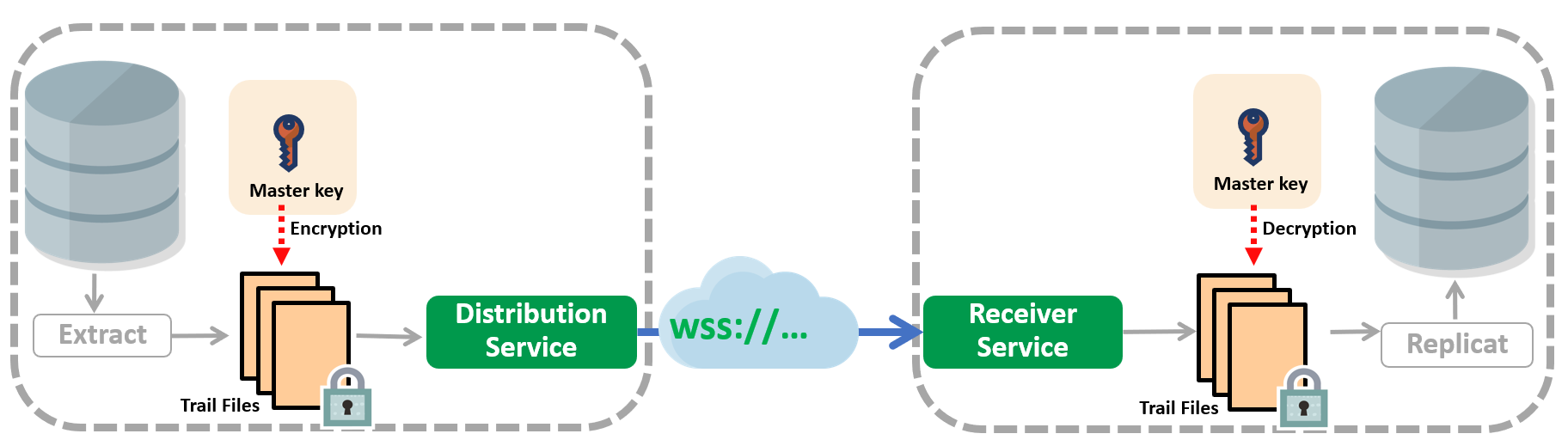
Once the Trail File is encrypted, manual configuration of the DistPath is unnecessary. By default, the DistPath uses the Local Wallet Encryption Profile, which reads the encrypted data and transmits it to the target GoldenGate deployment.
For enhanced security, it is recommended to secure the DistPath with the WebSocket Secure (WSS) protocol, ensuring the data is transmitted with a high level of protection.
There is nothing to configure for Replicat. Replicat uses the Master Key and automatically identifies the Encryption Algorithm to decrypt the Trail File.
When using the Local Wallet Encryption Profile, the Master Key, as the name implies, is local to the GoldenGate deployment. It is the administrator’s responsibility to copy the Master Key wallet to the target system. This task must be performed during implementation and whenever the Master Key is rotated.
If a Key Vault Management system, such as the Oracle Cloud Infrastructure Key Management System (OCI KMS) or Oracle Key Vault (OKV), is used, these processes are automated. The Master Key is securely managed within the Key Vault and never leaves the system. The GoldenGate source and target deployments retrieve the Master Key information through a REST API call to the Key Vault Server.
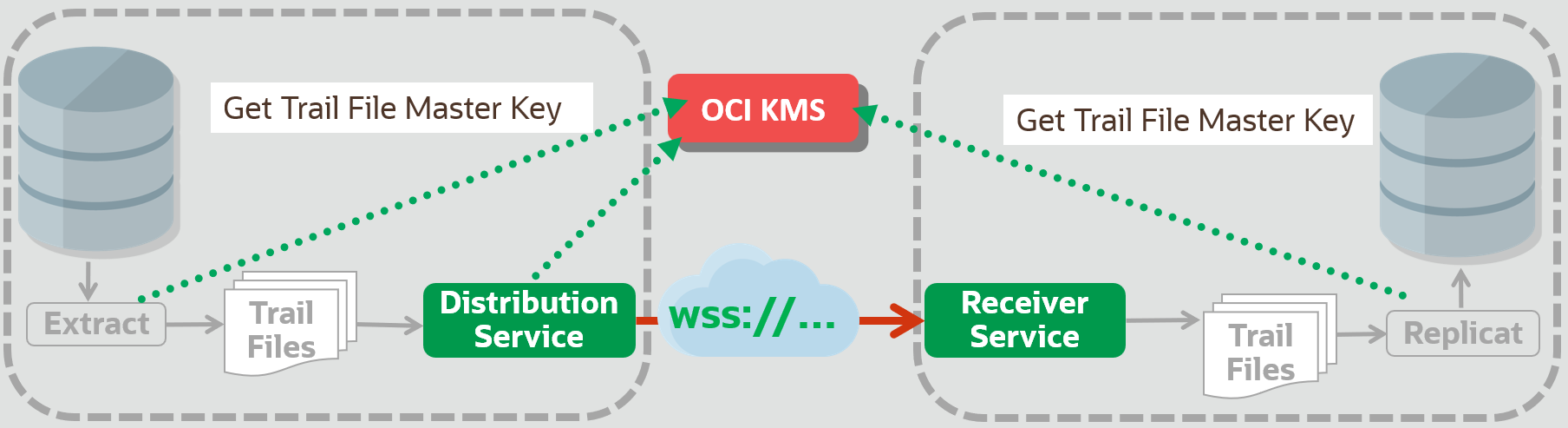
In summary, Key management Systems provide the following advantages:
- No Master Key is stored locally within any GoldenGate deployment.
- Manual key management is eliminated, as there’s no need to copy or exchange Master Key wallets.
- The Oracle Key management integration allows for the management of multiple Master Keys, which can be particularly useful in large-scale or extended GoldenGate environments.
The implementation using OCI-KMS (or OKV) is very similar to the Local Wallet setup. The Security Administrator specifies the “connection” to the Service management system. Both Encryption Profiles, from GoldenGate source and target deployments, are retrieving the Master Key information remotely.
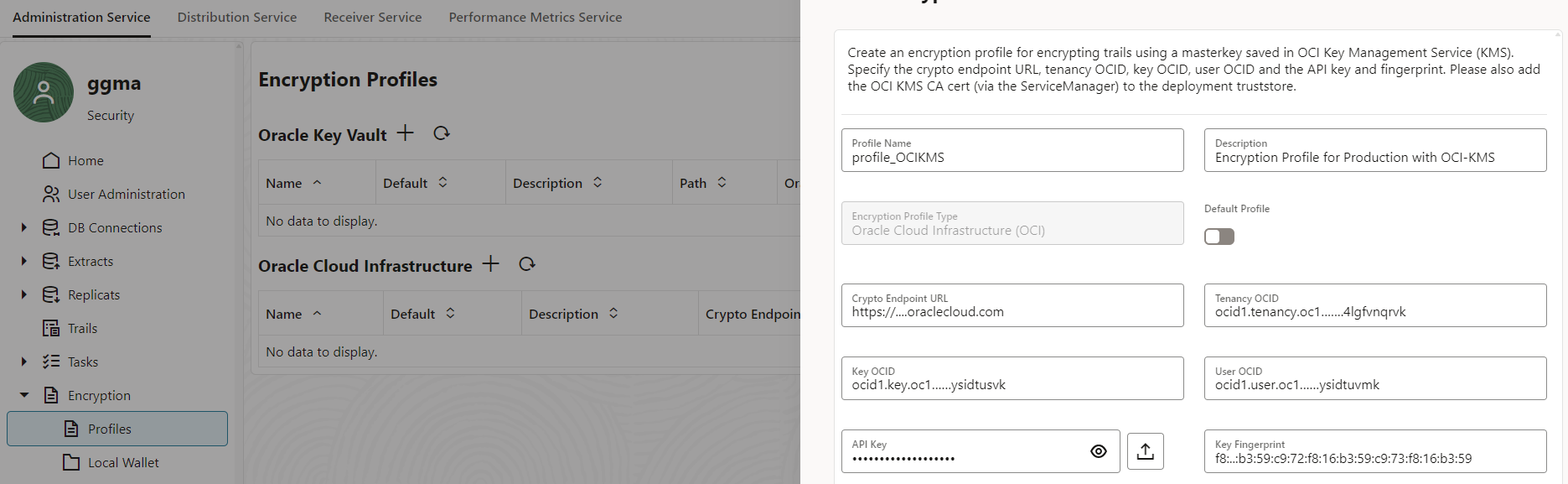
If you set the Encryption Profile as the default, the steps will be the same as those for the Local Wallet Encryption Profile. However, if you don’t want to use the OCI-KMS Encryption Profile as the default, you will need to modify the Extract and Replicat processes to use this specific profile instead.
AdminClient(SRC)> ALTER EXTRACT extn ENCRYPTIONPROFILE profile_OCIKMS
AdminClient(SRC)> ALTER DISTPATH dp_n2s ENCRYPTIONPROFILE profile_OCIKMS
AdminClient(TRG)> ALTER EXTRACT reps ENCRYPTIONPROFILE profile_OCIKMS
From the GoldenGate implementation perspective, Trail File Encryption is straightforward, as it depends on the Encryption Profile in use. The Encryption Profile links to the Master Key. With the Local Wallet Encryption Profile, you simply create the Master Key on the source system and securely copy the wallet to the target system. When using Encryption Profile from Oracle Key Management systems, you need to create the Encryption Profile that retrieves the required information from the Oracle Key Management.
