OCI provides encryption of data at rest for storage and databases. This works behind the scenes so that no dedicated task is required. Key management is provided ootb by Oracle but can be changed to customer managed keys. Following blog provides an overview: https://blogs.oracle.com/cloudsecurity/post/how-oci-helps-you-protect-data-with-default-encryption
OCI supports for several services so called customer managed keys. Customer managed keys allow to have the control of the e.g. the encryption keys in some OCI services like databases. To enable customer managed keys you change the configuration of the service typically during setup in the OCI Cloud Console (UI) or script based (e.g. terraform , OCI API). Own keys like any other keys and secrets can also be used for any custom encryption in a customer applications.
For usage see: https://docs.oracle.com/en-us/iaas/Content/KeyManagement/Concepts/keyoverview.htm
and the API https://docs.oracle.com/en-us/iaas/api/#/en/key/release/
With customer managed keys it is possible to create, revoke or rotate keys on your own. Keys are stored in OCI Vault which is a FIPS140-2 compliant HSM. Vault is either in a dedicated hardware partition (Virtual Private Vault), a shared hardware partition (Vault) or software based. Besides your security requirements it’s a difference in costs and features.
Helpful information is provided in the FAQ:
https://www.oracle.com/security/cloud-security/key-management/faq/
OCI Vault supports as a feature of customer managed keys the import of own keys. This can be useful if you need the same key across different vendors or have special requirements in key generation.
Importing a key needs to specify the Vault and optionally the key. With rotate you can create a new key version. The difference between key and key version is that importing a key will generate a key and a key version, with new version ‘only’ a new key version in an existing key container.
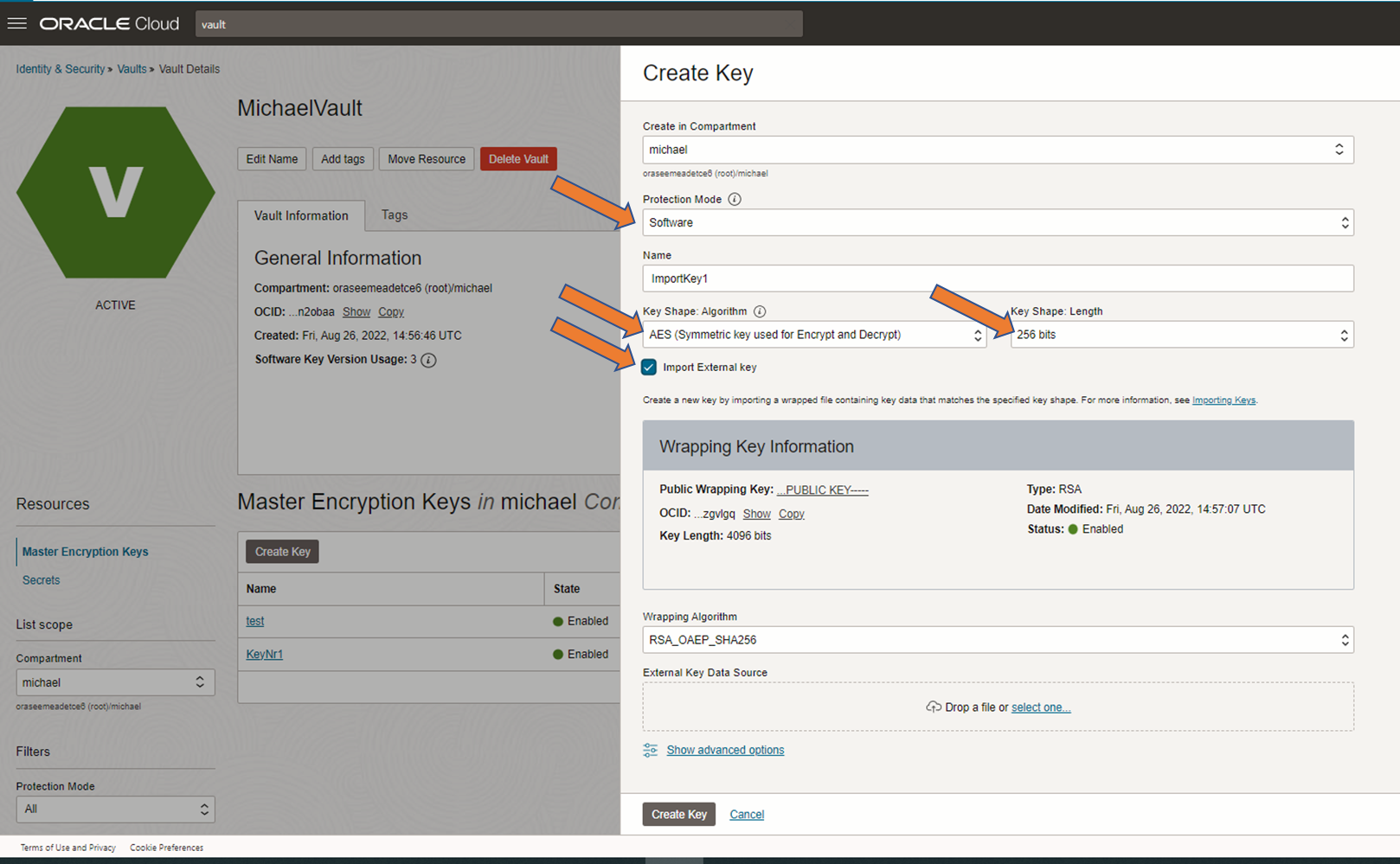
Screen importing a key in a vault, here Software-protected and AES256
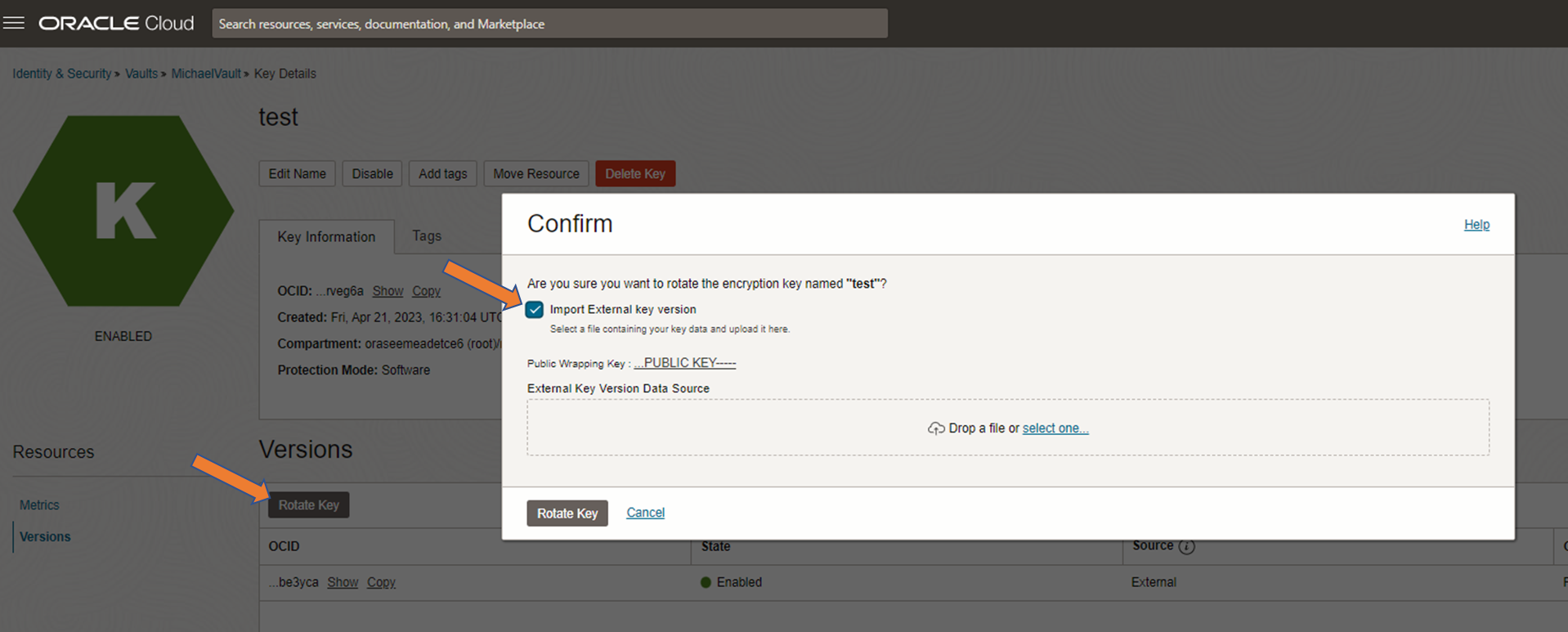
Screen import key version with “Rotate Key”
To import a key or key version you have to wrap your key with the public key of the Vault. See steps below for this. The steps to import an own AES key are described in documentation: https://docs.oracle.com/en-us/iaas/Content/KeyManagement/Tasks/importing_symmetric_keys.htm
For an import using the OCI console (UI) it might be unclear how to do this and which formats have to be used if you are not the key/encryption specialist. The following desciption provides a quick test for importing an AES256 key or key version. Btw 256 is max key length for DB encryption.
Some points upfront
- Don’t be confused with some notes in documentation: “You cannot import key material for keys protected by software.” This does not mean that you can’t use Vault SW protected key (this blog will use this config)
- And don’t be confused with “you cannot import AES keys that are longer than 128 bits.”. AES256 can be imported (this blog will use this key length).
- Finally if you use openssl for wrapping you do not have to patch if you use e.g. the default openssl in some distributions like 3.0.2
(https://docs.oracle.com/en-us/iaas/Content/KeyManagement/Tasks/to_configure_and_patch_openssl.htm)
Here the steps:
1. Create a key/key version
From UI, go to your Vault and do a ‘Create Key’ or if it should become a key version within an existing key ‘Rotate Key’. See screenshots above.
2. Download the wrapping key of the Vault
The wrapping key can be copied in the create key dialogs shown. You have to download it to be able to apply the wrapping to your key. Extension of file is not important, a format transformation is not needed.
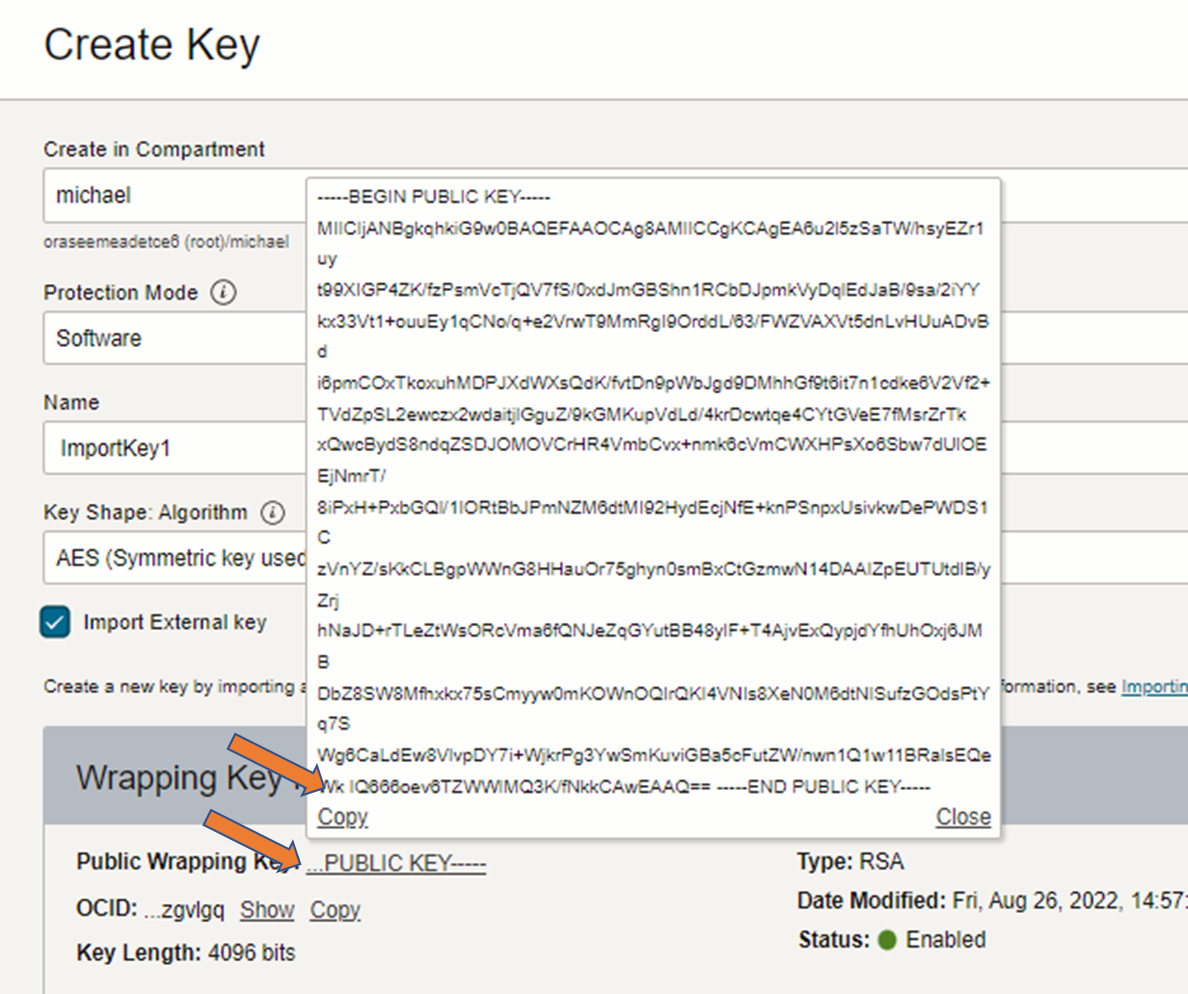
Screen to copy the wrapping key and create a file e.g. wrapping.key
3. Generate AES256 key somewhere
openssl rand ${32} > myaes.key
256 bit AES is 32 byte; key is generated as binary
4. Ensure your key is binary
5. Wrap your key
Your key is myaes.key, wrapping key is wrapping.key and output, the wrapped key should be myaeswrapped.bin
openssl pkeyutl -encrypt -in myaes.key -inkey wrapping.key -pubin -out myaeswrapped.bin -pkeyopt rsa_padding_mode:oaep -pkeyopt rsa_oaep_md:sha256
6. Upload
Select myaeswrapped.bin
no further conversion needed as this is done during the upload
6. Key can be specified or used
The key (AES256) is described as from external source
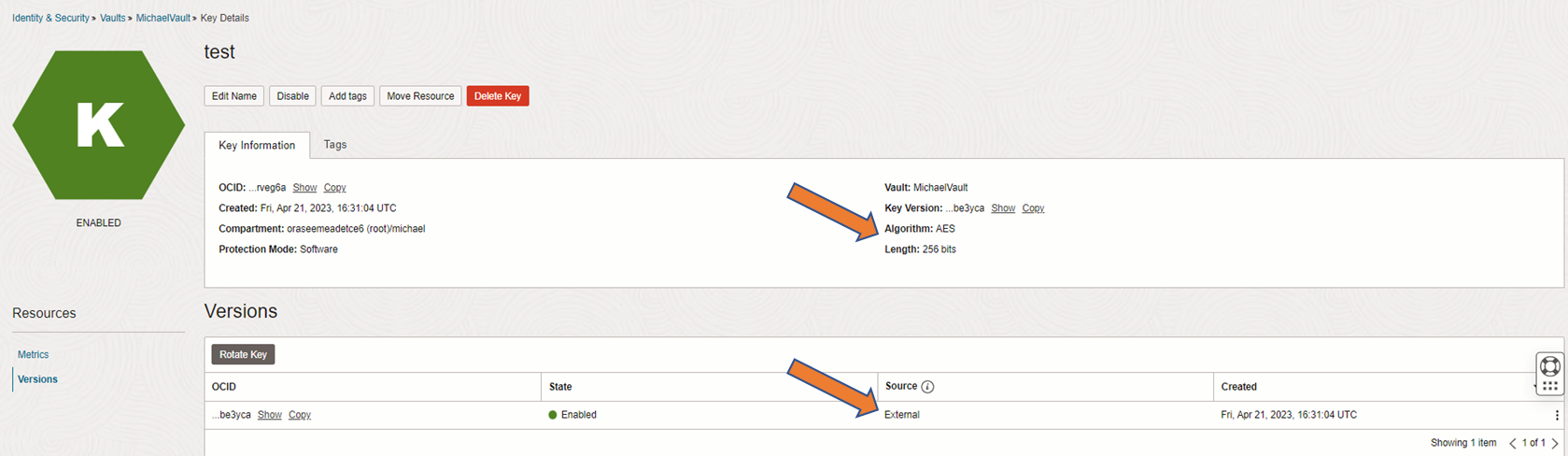
Screen showing imported keyversion in container key test
If you import a key a key version is automatically generated. The key and the key version have different OCIDs (OCI Identifiers). Within some services you can specifiy only the key (e.g. Autonomous) and on other services you can speficy the key version (e.g. DB VM).
And don’t forget you must enable the servce to access Vault by writing the appropriate policies.
Troubleshooting:
In case the import is not in the expected format a somehow generic error is shown:
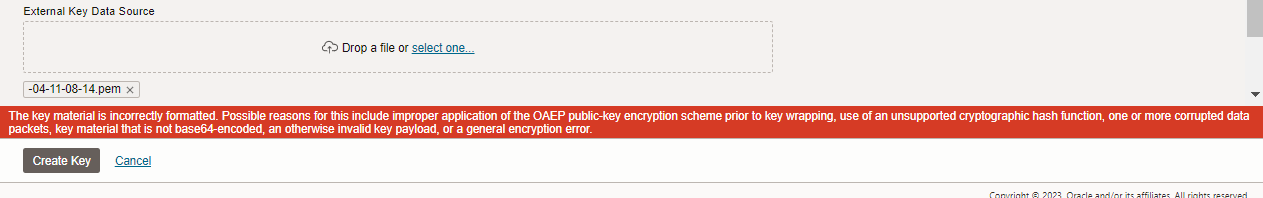
Screen showing error during import
Most common problems in uploading AES keys are:
- too old openssl version used that does not support the required wrapping
- the original key was not in the specified length as specified in UI (e.g. 256 bit)
- the original key was not in binary format or includes some metadata
- the uploaded wrapped key was not binary
- you have exceeded your quotas or service limits for Vault and/or keys
In case that import and using customer key management works and it’s intended to automate key import a setup based on provided scripts in documentation can be used:
https://docs.oracle.com/en-us/iaas/Content/KeyManagement/Tasks/importingkeys_topic-To_import_aes_key_material_as_a_new_external_key.htm