This blog assumes that you already have a keycloak integration. If not steps are outlined here:
https://blogs.oracle.com/coretec/post/ssofederation-with-keycloak-and-idcs-andor-oci-iam-domains
To enable JIT the attributes from the SAML assertion are used to create or update an OCI user and optional the OCI group-membershops. This works for user-attributes like email as well as for group-memberships and is updated during every sucessfulll SSO. The configuration requires from the IDP (here keycloak) to pass the intended attributes and group-memberships. The SP needs the mapping of the SAML attributes to user-attributes and groups. Groupnames can be different in IDP and SP.
This description uses IAM Domains. With IDCS config steps are the same but only possible with configuration using IDCS API (no UI support).
Step 1: prepare keycloak
Define some groups in keycloak. Here I use some of the realm created for the integration.
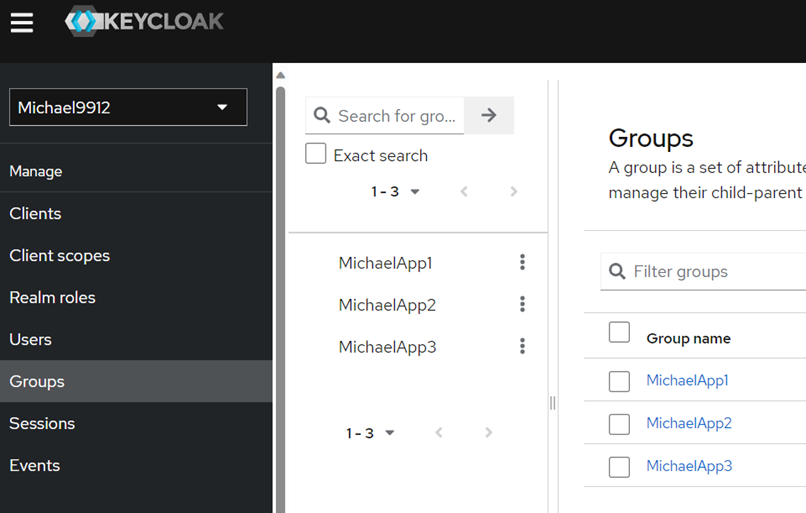
Figure: definition of keycloak groups
Assign User to one or more groups in keycloak (not shown).
Define a Client Scope for groups.
Keycloak passes ootb keycloak roles in the SAML assertion which are usually not for steering the group memberships in OCI.
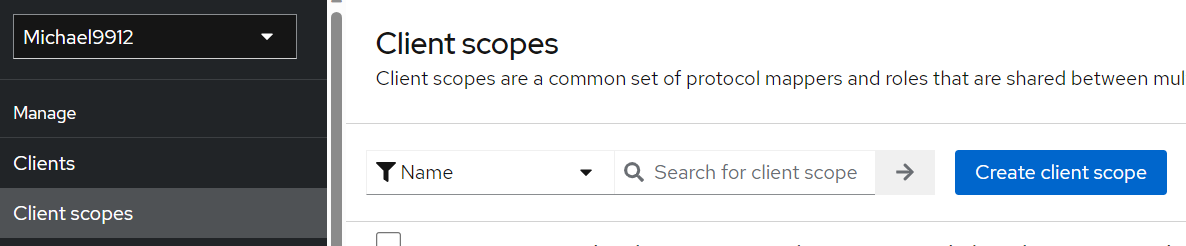
Figure Create Client Scope in keycloak
Give it a name (here groups) and select SAML as protocol.
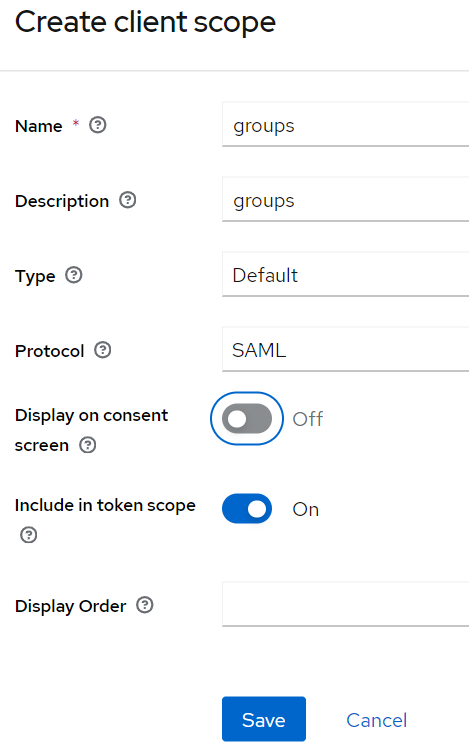
Figure Basic Config of Client Scope
After the Save in previous screen a mapper can be created in the client scope. Select Mapper.
Figure Select in Client Scope the Mapper
As groups are available as predefined mapper (group list) choose predefined.
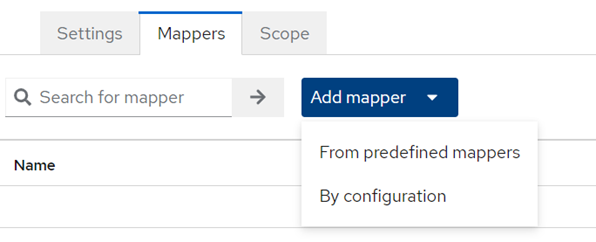
Figure Select in Client Scope the Mapper
Do mapper config, remember the attribute name as this will be needed on OCI config. As NameFormat select unspecified to avoid miss-understandings between keycloak and OCI. Select Single Group Attribute (as shown) to get all groups in one XML tag (named groups here).
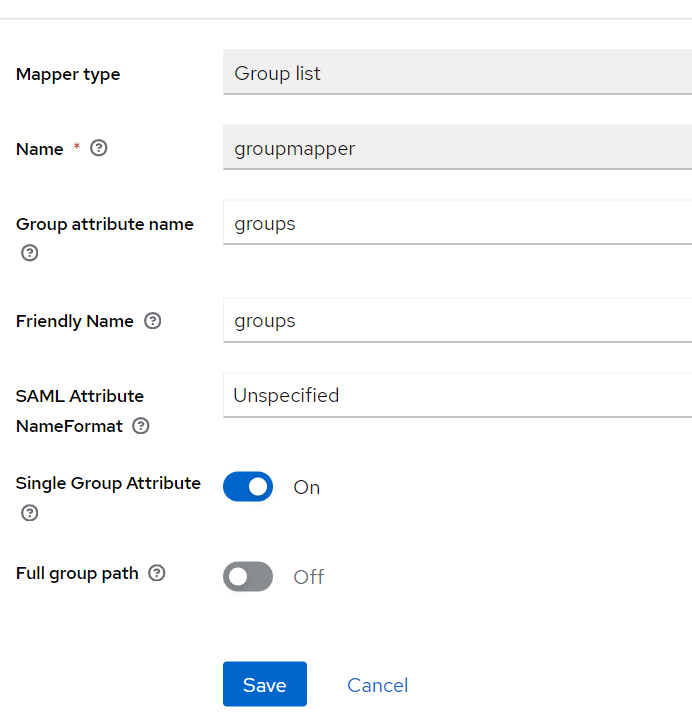
Figure Group Mapper definition
Go for the Client you created for the federation in the realm.
Figure keycloak client
Select Client Scopes and add client scope, you should be able to select the defined one some steps before.
Figure keycloak Add Client Scope
After this it should look like this:
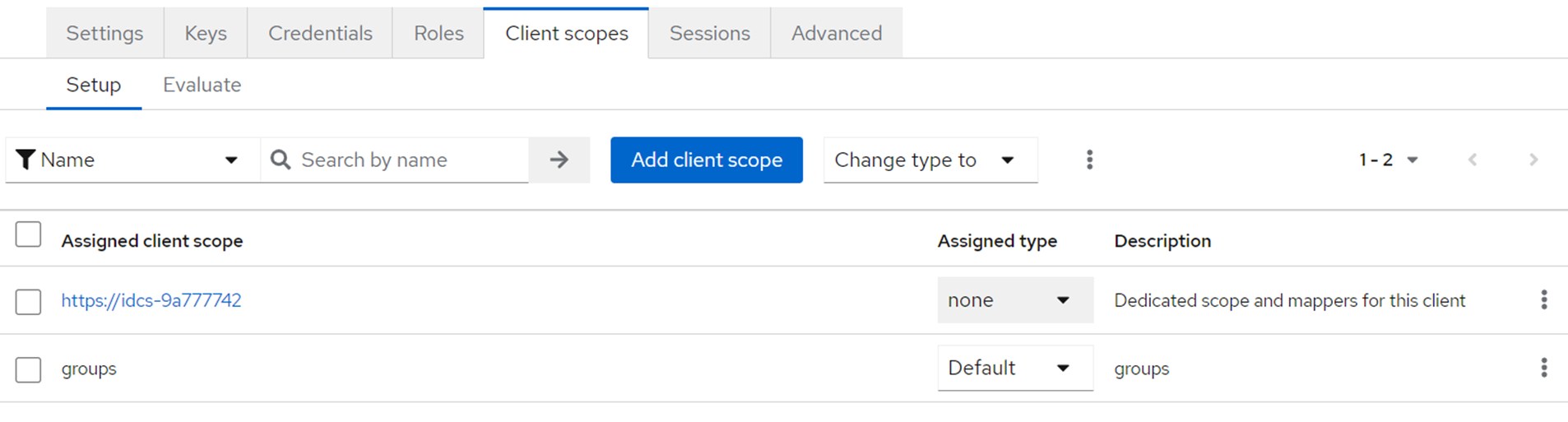
Figure keycloak Client Scope
If attributes are needed (besides groups) this config is behind the https://idcs client scope.
Now you’re done on keycloak, switch to OCI.
Step 2: Configure OCI JIT
Go for the IDP configuration of keycloak.
Select SAML JIT:
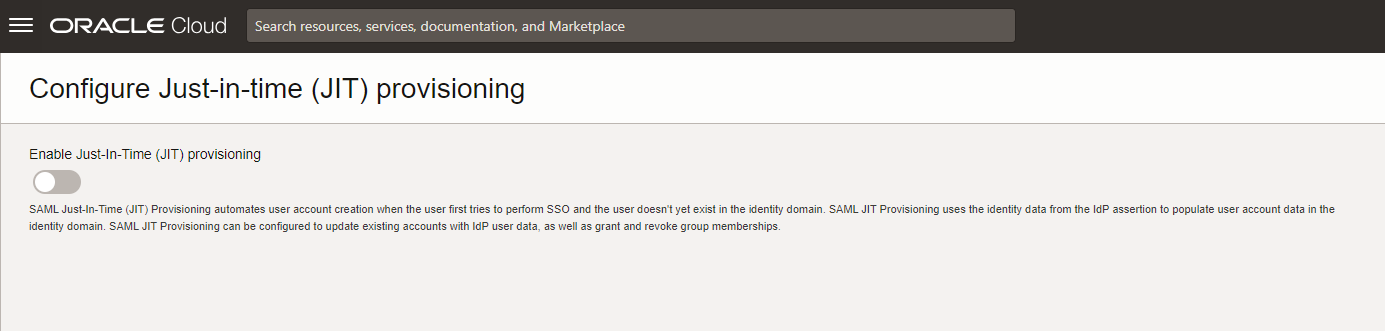
Figure enable SAML JIT
Overall Config, as the attribute section has to be configured also.
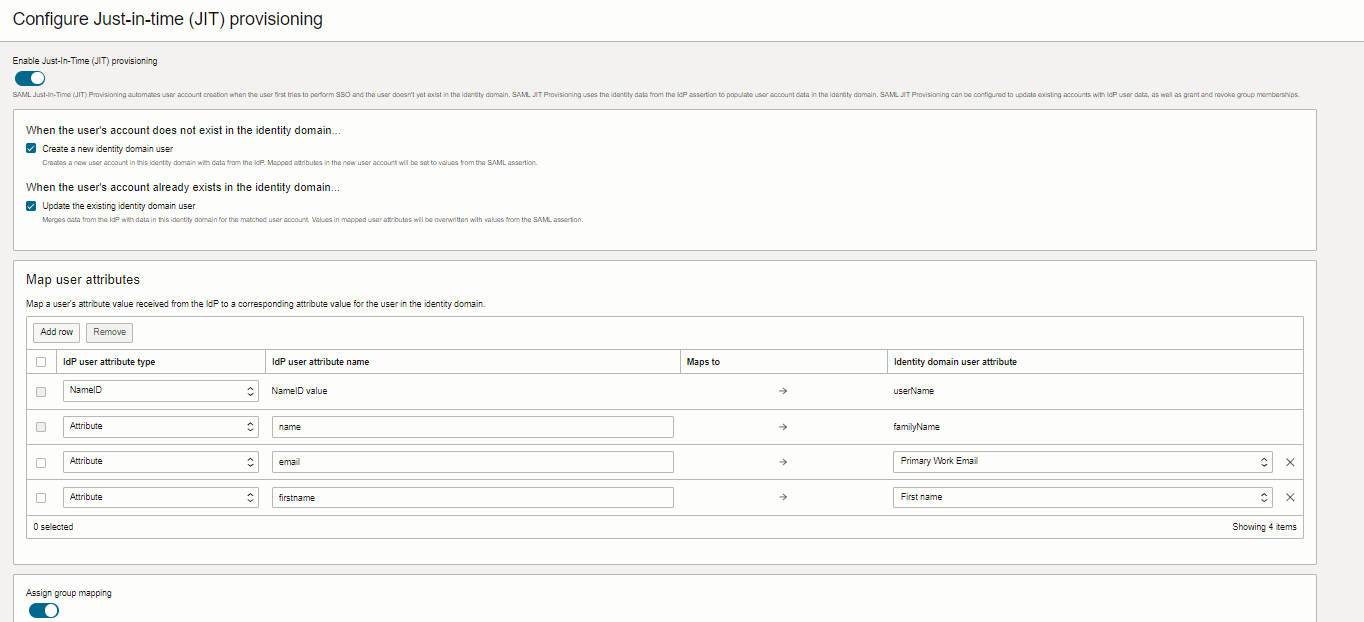
Figure enable SAML JIT Create/Update User with mandatory attribute settings
Besides Attribute mapping and rules (screen above) define the group mapping.
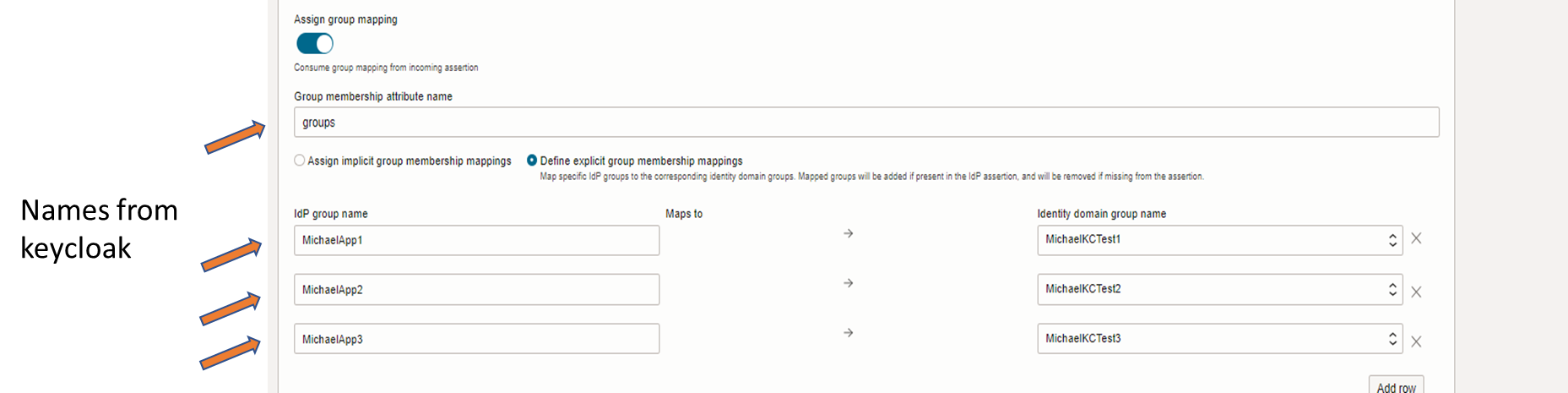
Figure SAML JIT group mappings (SAML Assertion – OCI IAM groups)
Now you’re done and can test. Depending on your configuration a user is created and/or updates after successful SSO. Check if Group Assignments have been executed.
Troubleshooting tips:
- If the SSO does not work use the Browser developer tools and debug SAML to see if all intendend information are provided by keycloak.
- IF SAML assertion looks good got for the ctx error in the SSO screen with the error and do the base 64 encoding. This shows you more information about the error.
- If groups are not assigned check config. It usually is a misspelling of attributname or groupname. The correct one for this sample with two groups would look like this:
<saml:Attribute FriendlyName=”grouplist” Name=”groups” NameFormat=”urn:oasis:names:tc:SAML:2.0:attrname-format:basic”>
<saml:AttributeValue xmlns:xs=”http://www.w3.org/2001/XMLSchema” xmlns:xsi=”http://www.w3.org/2001/XMLSchema-instance” xsi:type=”xs:string”>MichaelApp1</saml:AttributeValue
<saml:AttributeValue xmlns:xs=”http://www.w3.org/2001/XMLSchema” xmlns:xsi=”http://www.w3.org/2001/XMLSchema-instance” xsi:type=”xs:string”>MichaelApp2</saml:AttributeValue
</saml:Attribute>
Documentation for SAML JIT Config in OCI: https://docs.oracle.com/en-us/iaas/Content/Identity/identityproviders/add-saml-idp-jit-prov.htm