Oracle Cloud Infrastructure (OCI) has more than one module that provides Identity Access Management (IAM). The most prominent one is the one for login and this is already not only one IAM (older tenants) and different between older and newer (domain based) tenants.
This blog gives a quick overview about the relationship between all of them. This also fits for newer SaaS tenants, see last section in this blog.
The overview shows an IDCS based tenant (old tenant) where the
- Red boxes are OCI ootb components
- Red circles are the IAM UIs
- Blue box is for any custom applications
- Yellow is for external providers for SSO and Provisioning which are usually also IAMs; this fits also for the Azure integration (Oracle Database for Azure)
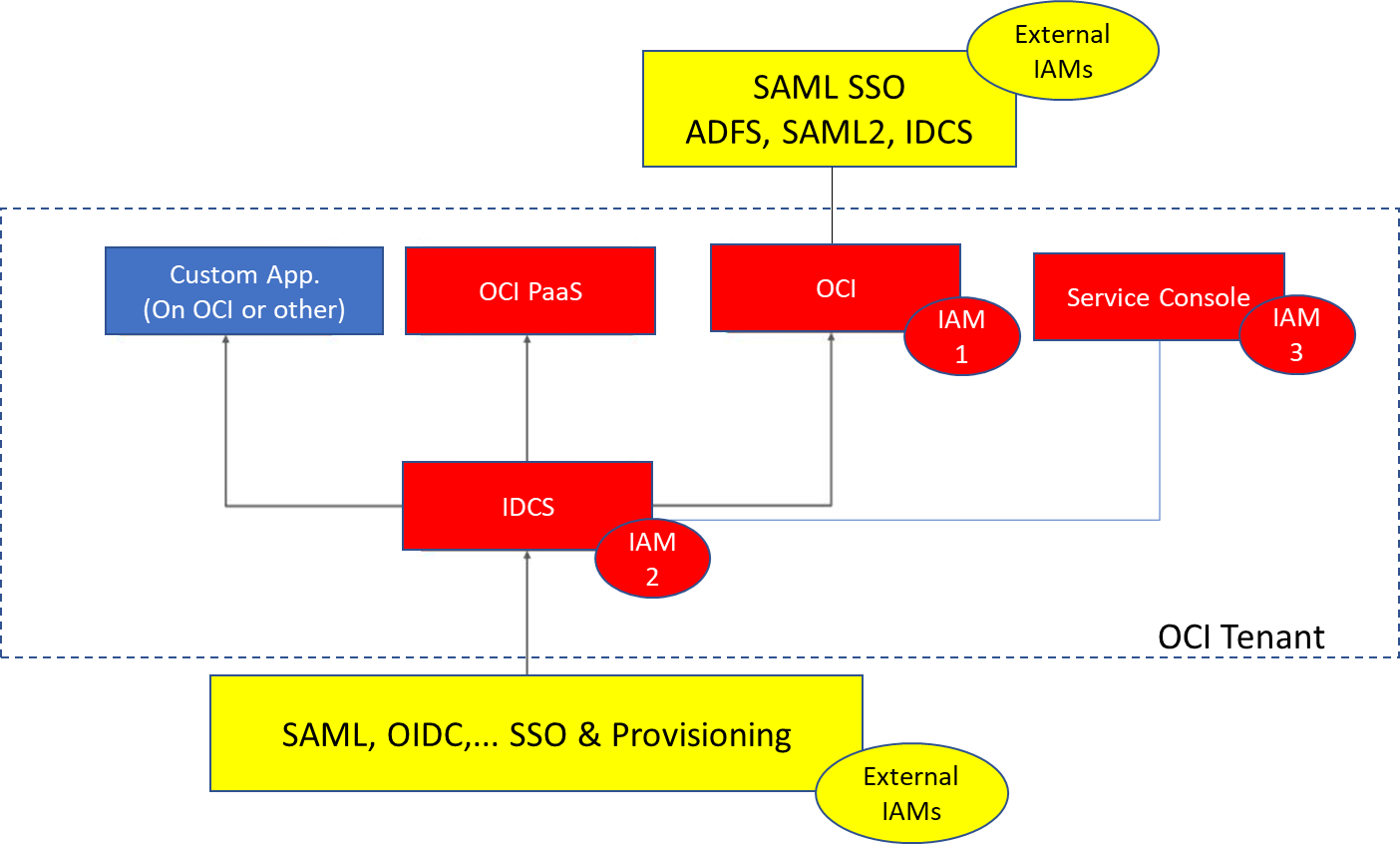
Figure IAMs in old OCI tenants
In the setup with IAM Domains IAM1 and IAM2 are replaced by IAM Domains. The conversion from OCI IAM+IDCS (old tenants) to IAM domains is scheduled and done by Oracle. For more information on this see FAQ document: https://www.oracle.com/a/ocom/docs/security/what-oci-iam-customers-should-expect.pdf
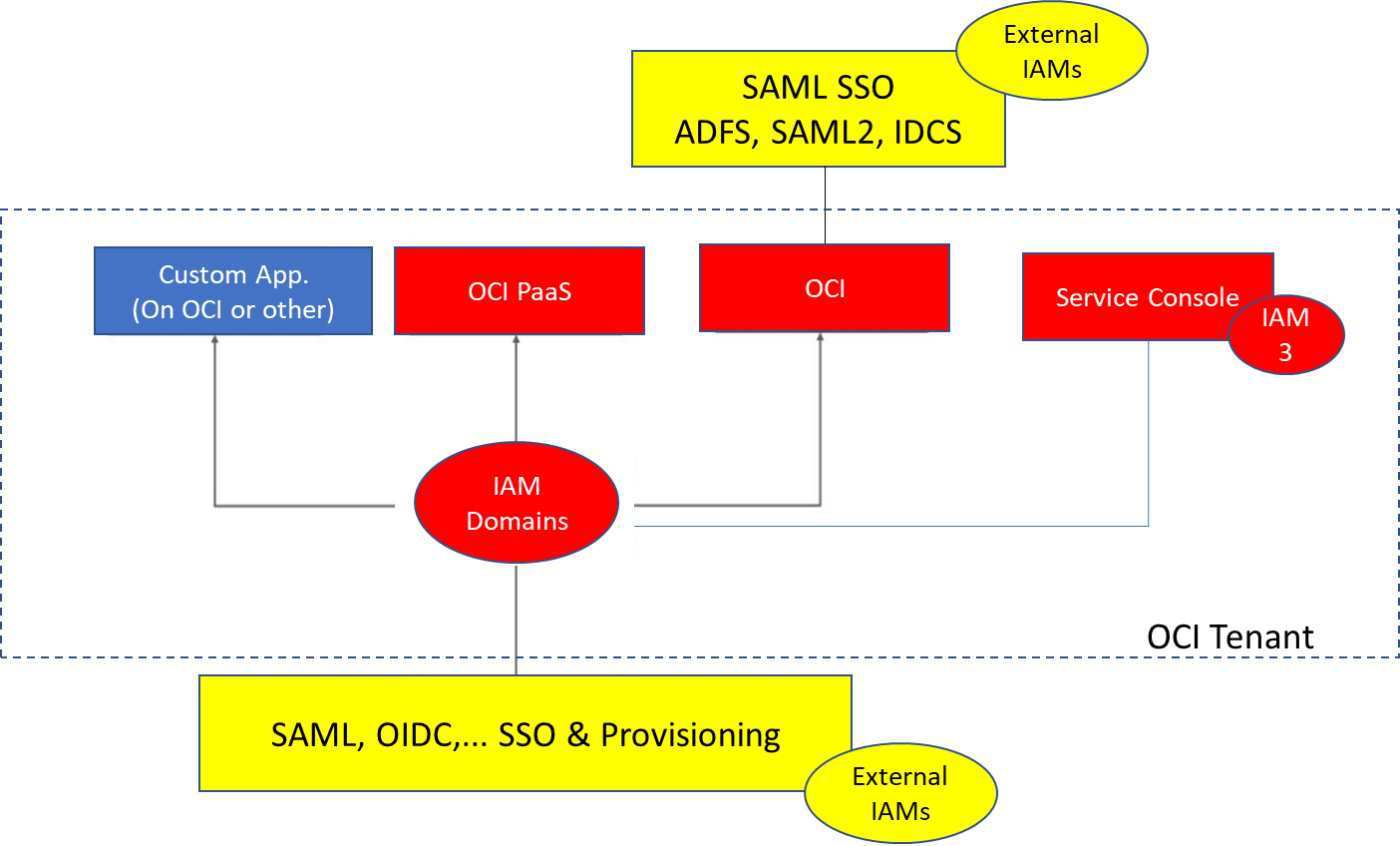
Figure IAMs with Domain based OCI tenants
Find in the following sections the three IAM UIs, OCI native IAM, IDCS and Service console. To login and use all of the three with one login IDCS login has to be used. For Service console a cloud role has to be granted to the account which is used for login.
IAM1:
This IAM (OCI native) can be accessed/used when having the appropriate OCI group with OCI policies assigned, either direct as a local OCI user or via IDCS user and group mapping in OCI federation configuration. Entitlement works as follows:
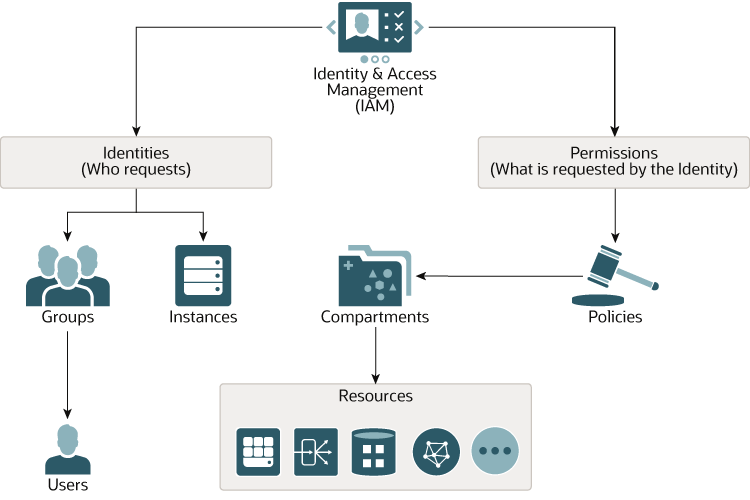
Figure IAM Authorization/Entitlements
The IAM1 UI can only fully manage (create, update, delete) local OCI users. These users can not use all PaaS services as PaaS is correlated to the IDCS instance which was used during creation of the service, e.g. Analytics Cloud (OAC). The UI of IAM1 looks as follows:
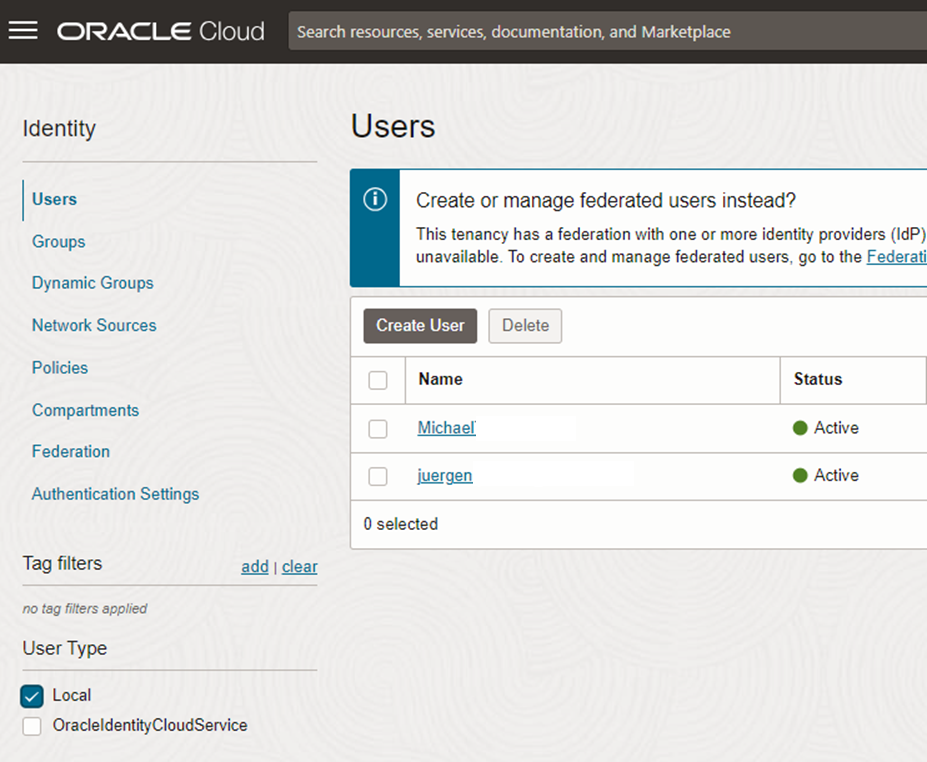
Figure OCI native/local Usermanagement
This UI is filtered (box on the left titled User Type) for OCI local Users (box “Local”). The other box “OracleIdentityCloudService” is the primordial (=in all OCI tenants) created IDCS to manage users in IDCS (here IAM2). If users in IDCS are assigned to OCI (=allowed to use OCI resources like create compute) then these users appear when the box “OracleIdentityCloudService” is checked.
Both types of users can be managed in OCI as OCI provides further features like databasepasswords. This management is limited for non local users to the userobject, means that entitlements/authorizations can only be assigned via group mapping.
Functionalities like creating Users, SSO, MFA are in local/native IAM (IAM1) as well as in OracleIdentityCloudService (IAM2). They are not the same function in different UI as they are bound to the IAM1 or IAM2. Both IAM have their own user- and configuration-store.
IAM2:
The first IDCS is the primordial one created in all OCI tenants. It does not have to be used but delivers more functionality and is needed for some PaaS services.
The functional overview is illustrated in following picture:
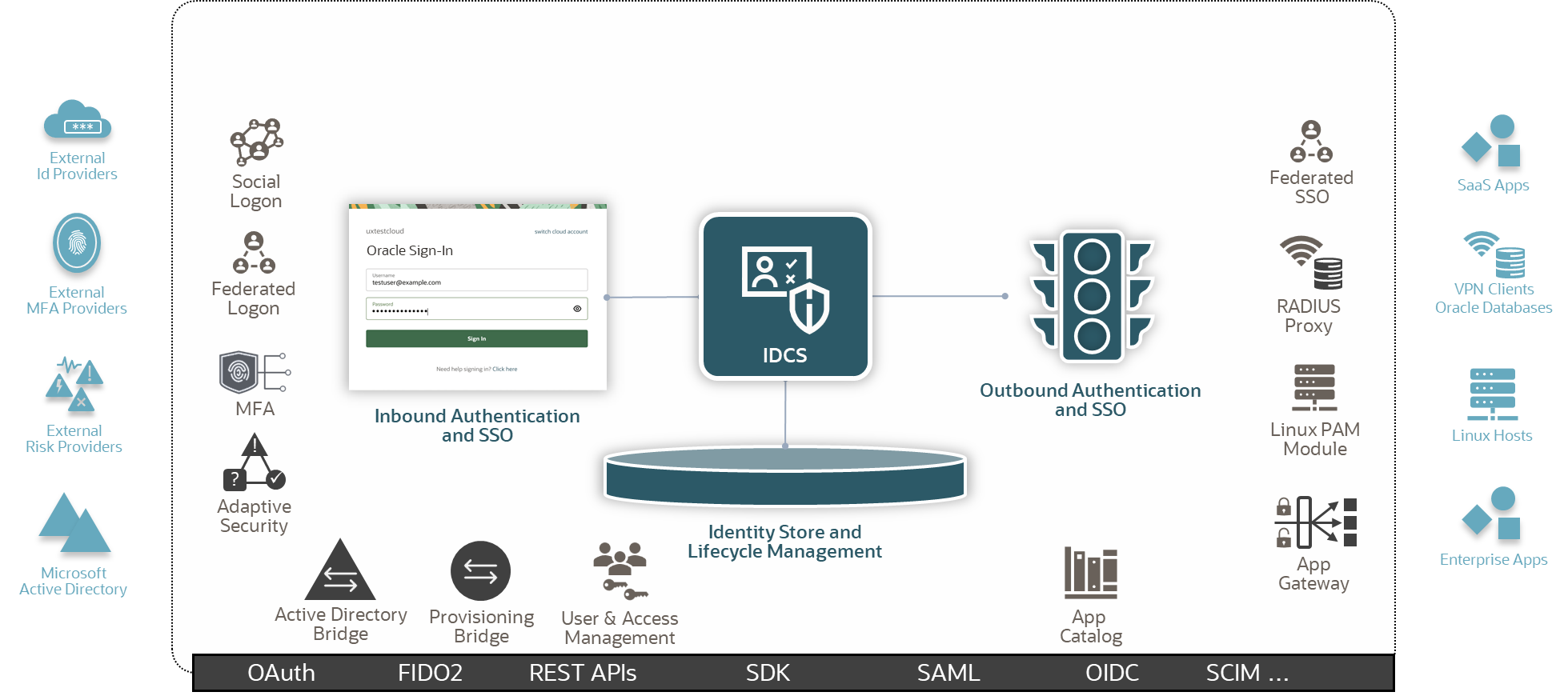
Figure IDCS Overview (IAM2)
To access IDCS the link is provided in OCI IAM in the federation section (or just search federation then you can click into the section) or can be bookmarked. The login with SSO works only if the login to OCI has been done using IDCS. The UI looks like this
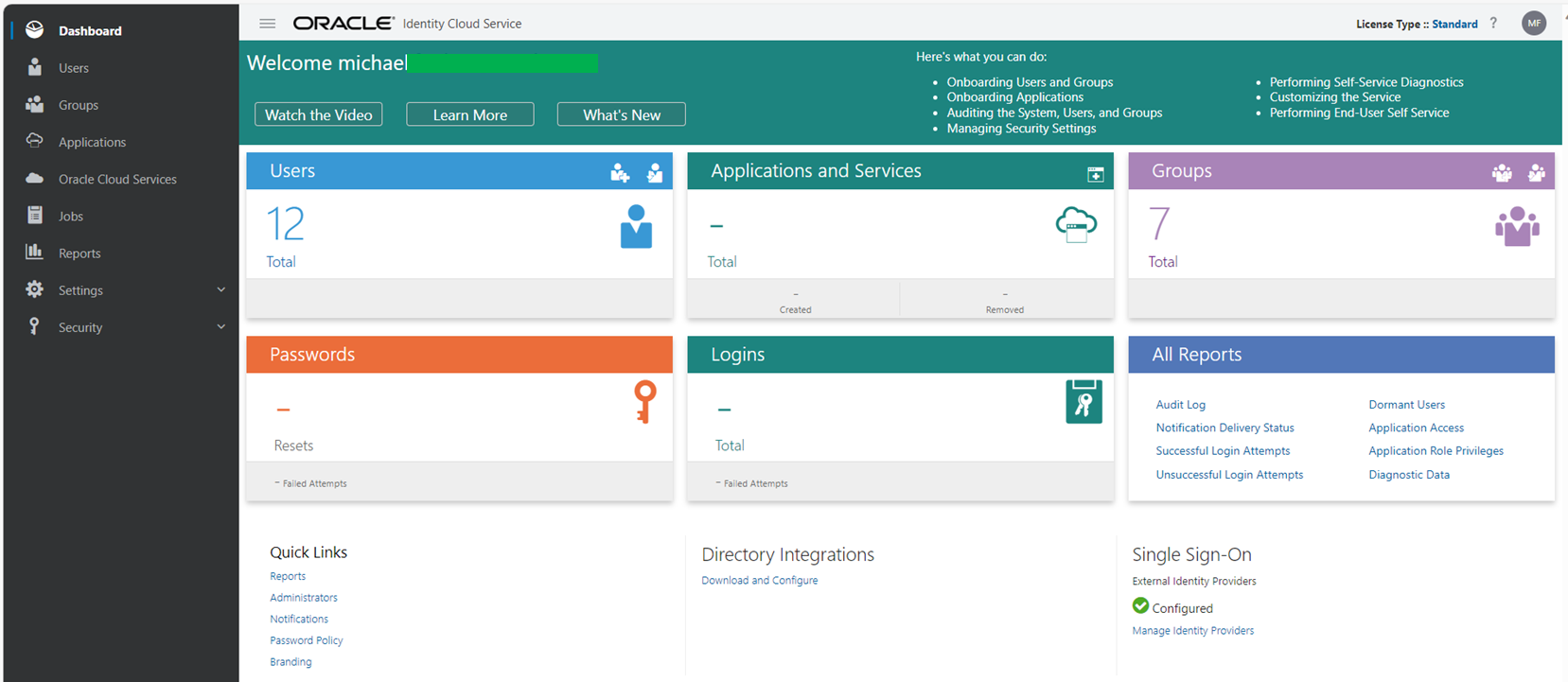
Figure IDCS UI
IAM2 also provides a self-service UI where a user can manage the recovery, email, MFA config … and gets a dashboard for all assigned applications. An IDCS user does not have OCI access, this is done by group assignments in IDCS. Here the self-service, section security to configure recovery and MFA:
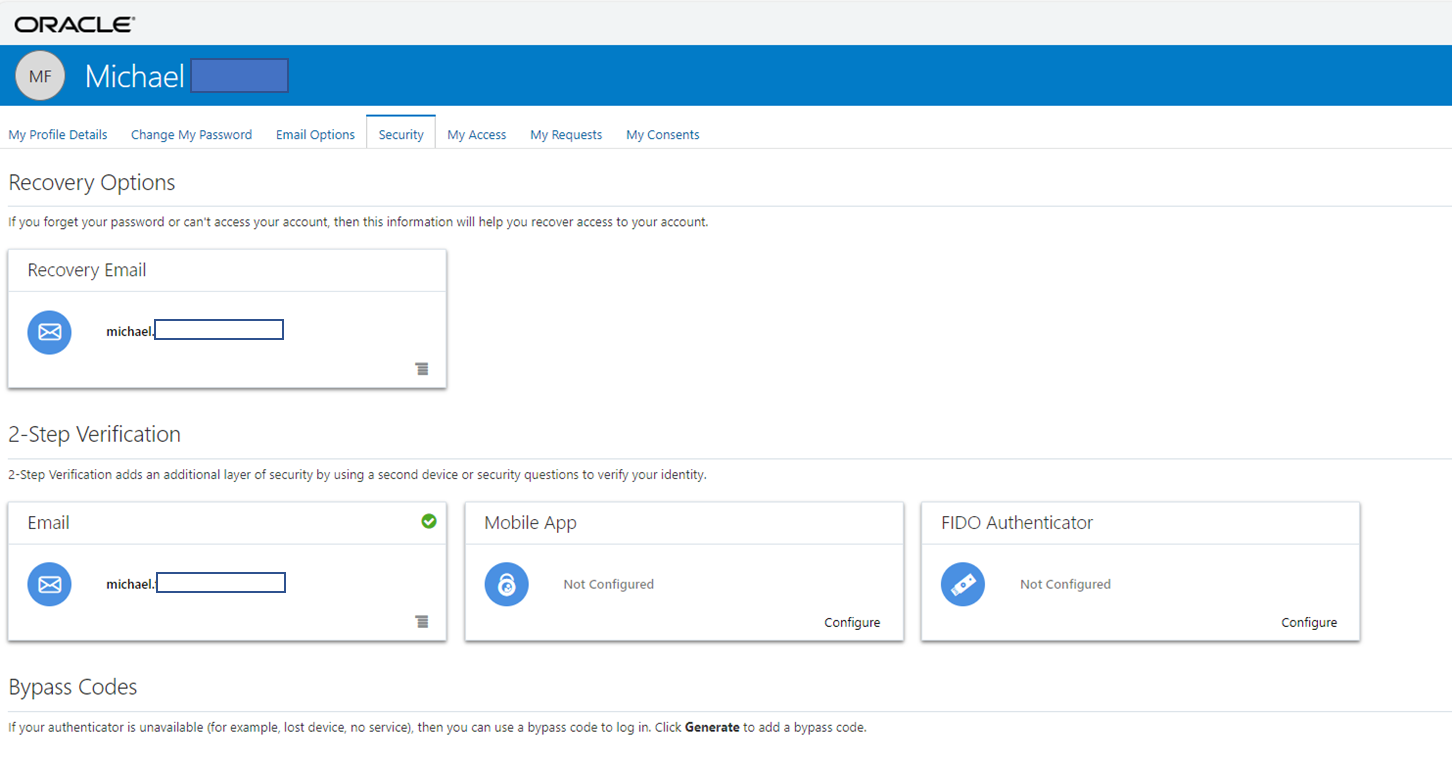
Figure IDCS Self-Service
IAM3:
IAM3 can be accessed through OCI via the user menu (see following screenshot) or through a direct link https://myservices-<tenantname>.console.oraclecloud.com/mycloud/cloudportal/dashboard
The IDCS login from the primordial instance is required.
If this entry (Service User Console) is not shown you are not entitled to use console. Please ask the tenant creator for entitlement.
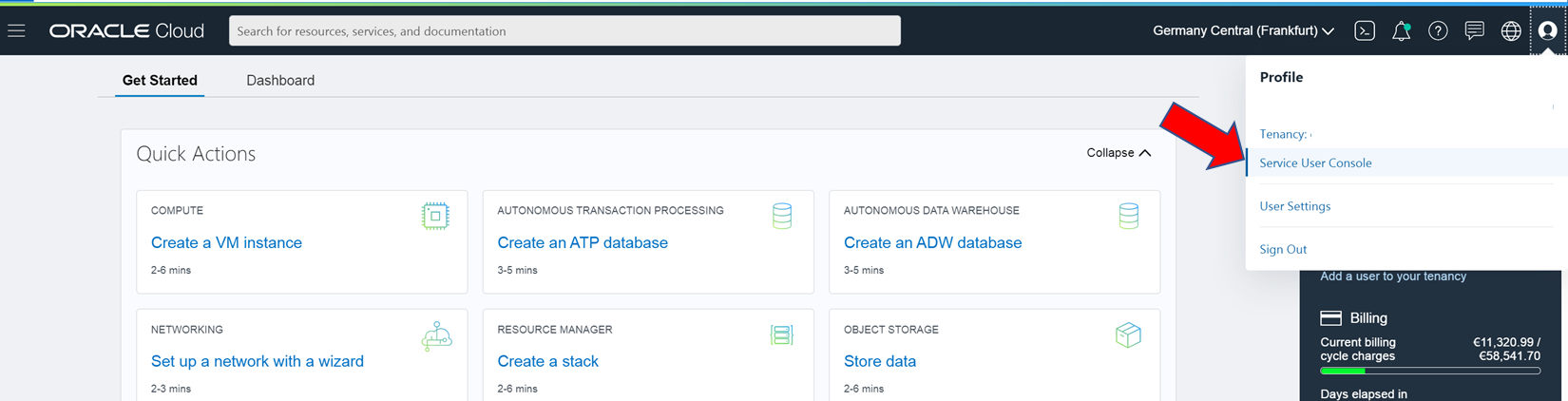
After login looks like
And there is the IAM3 in the left menu:
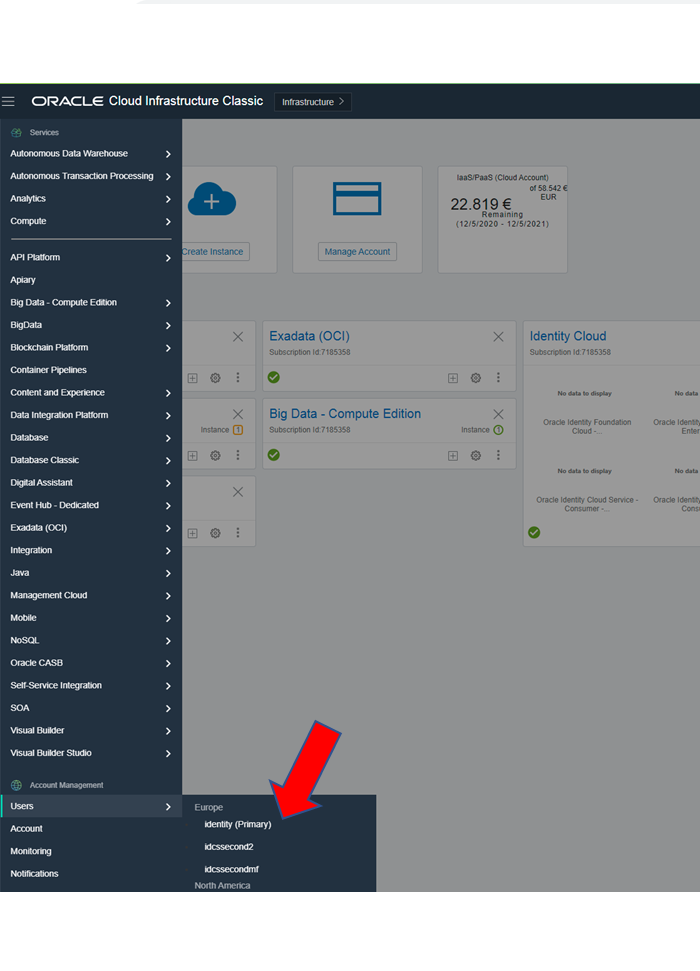
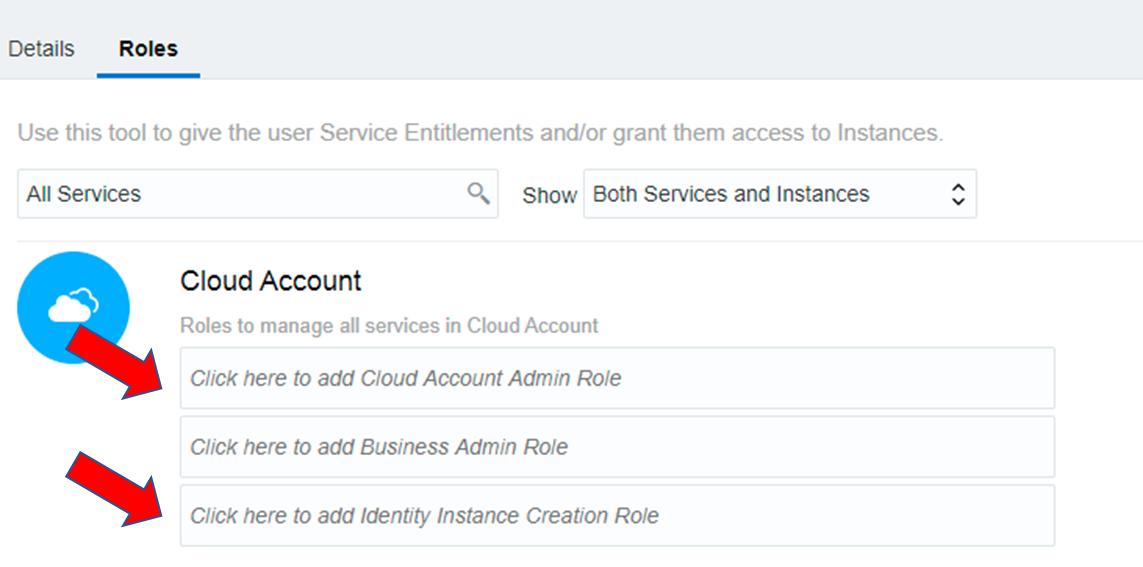
Which shows users (from IDCS) and UI is enabled for cloud role management:
|
|
|
IDCS UI can not manage the cloud Admin roles. Arrows show how to achieve Cloud Admin Role and become an IDCS instance creator.
The User Management is via IDCS, there is a button for direct IDCS access (Identity Console) which switches to IDCS UI.
Documentation: https://docs.oracle.com/en/cloud/get-started/subscriptions-cloud/csgsg/add-users-cloud-account-identity-cloud-service.html
IAM SaaS (Fusion PoDs):
Having a SaaS like Oracle Fusion HCM in the same tenant for the newer deployments as the Fusion deployment has changed over the time the picture looks like this
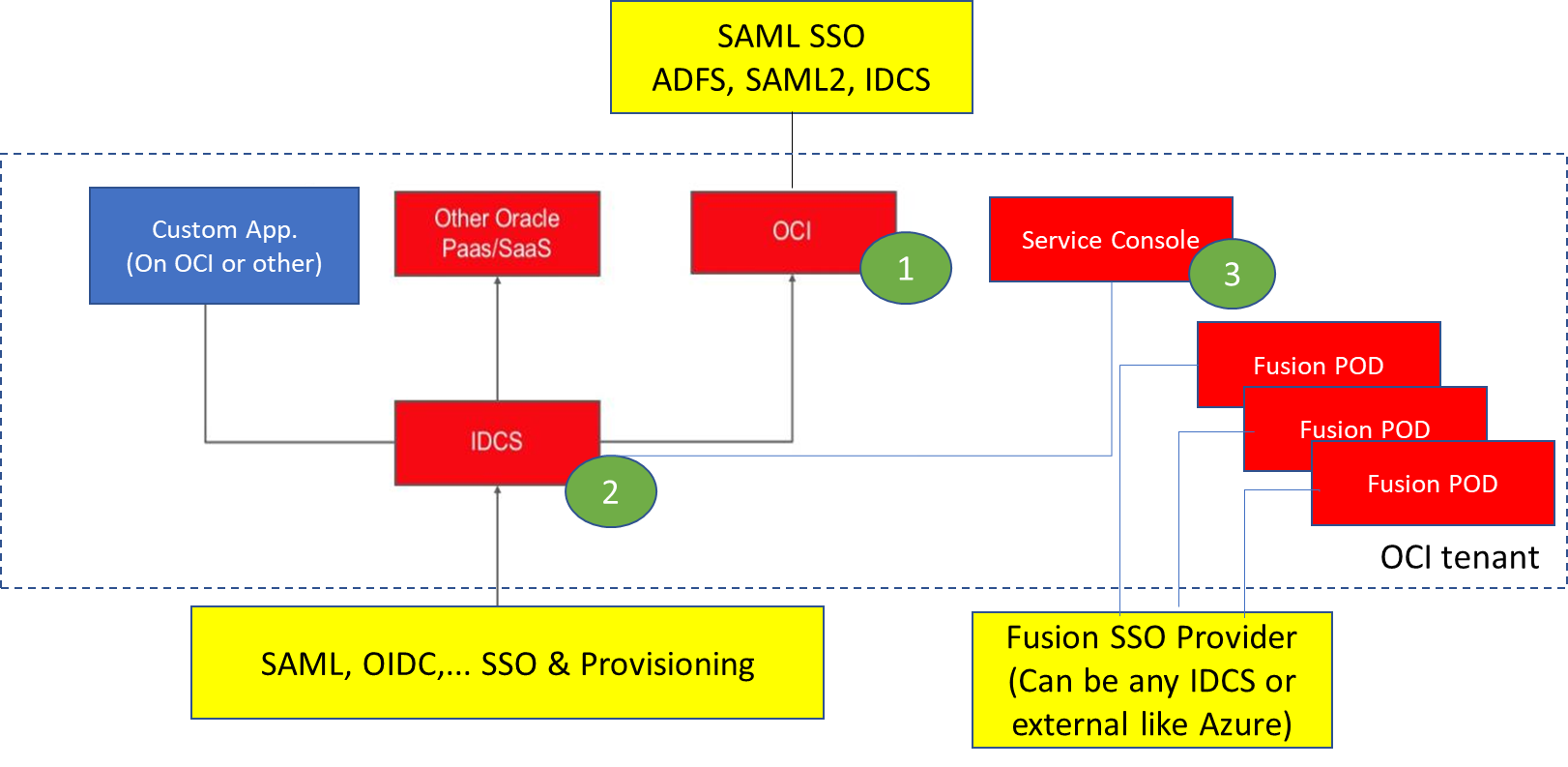
Figure with Fusion PoDs
The Fusion PoDs are deployed within one tenant and can use the OCI resources. Ootb there is on IDCS included in each PoD for connect (Identity Context of logged on user) with PaaS like IntegrationCloud (in short PaaS for SaaS). Fusion has it’s own IAM for accessing and a usermangemt within the SaaS service. As overview for a Fusion PoD this is like:
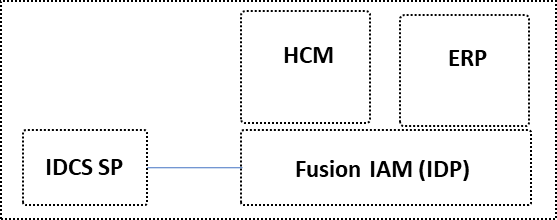
Figure with IAMs in/of Fusion PoDs
An explanation can be found in this blog: https://www.ateam-oracle.com/post/cloud-security-user-provisioning-to-fusion-applications-cloud
And the topic is outlined in MOS: Supporting Oracle Fusion Cloud Applications Service Integrations with Oracle Platform as a Service (Doc ID 2785751.1)
Go in the description for download of pdf:
Integrate an Oracle SaaS Application with Oracle PaaS — Configure federated SSO between Oracle Fusion Applications Cloud Service and your Oracle Identity Cloud Service-based PaaS account. Optionally, set up user, role, and role assignment synch.