Overview
In today’s fast-paced world of healthcare and life sciences, the race for the next breakthrough is on. From pioneering drug discoveries to groundbreaking gene editing, the key to innovation lies within vast and sensitive datasets. However, with this great potential comes a great responsibility: ensuring the utmost security and privacy of this critical information.
This is the challenge that keeps healthcare executives up at night. How do you empower your research teams with the data they need to innovate, while simultaneously guaranteeing the security and compliance that your patients and regulators demand? The answer lies in a powerful and increasingly adopted solution: the Trusted Research Environment (TRE).
This reference architecture will explore the benefits of TREs and how researchers can securely set them up on Oracle Cloud Infrastructure (OCI), providing a robust and trustworthy foundation for your most critical research initiatives.
What is a Trusted Research Environment (TRE)
A Trusted Research Environment (TRE) is a secure, controlled, and governed computing environment that provides researchers with access to sensitive data for analysis, without the data ever leaving the secure space. Think of it as a highly secure digital laboratory where research teams can work with valuable datasets, collaborate with colleagues, and leverage powerful analytical tools, all while under the watchful eye of stringent security protocols.
A TRE in a simple world is a Secure Computing Environment that holds data and enables access to it for analysis without the data leaving the TRE.
The National Institutes of Health (NIH) and National Library of Medicine (NLM) have identified 5 safes to consider when designing a Trusted Research Environment (TRE).
The core of a TRE’s safety is this Five Safes Framework, which consists of five guiding principles: Safe People (trained researchers), Safe Projects (approved ethical research), Safe Settings (secure computing environments), Safe Data (de-identified or pseudonymized data), and Safe Outputs (screened results to prevent re-identification)
|
|
Safe People |
|
|
Safe Projects |
|
|
Safe Settings |
|
|
Safe Data |
|
|
Safe Outputs |
Why Oracle Cloud Infrastructure (OCI) for TRE?
When building your TRE, the choice of your cloud provider is paramount. You need a platform that is not only powerful and scalable but also built with a security-first mindset. This is where Oracle Cloud Infrastructure (OCI) helps build your TRE environment with supreme trust.
OCI is engineered to protect your most valuable data with a multi-layered security approach that provides a secure foundation for your TRE. Here’s what sets OCI apart when we map the safe practices to OCI’s capabilities.
OCI Services and the Five Safes Framework
1. Safe People (trusted, trained researchers only)
Goal: Ensure only approved and accredited researchers can access data.
OCI Services:
- Identity and Access Management (IAM): Role-based access, least-privilege policies, federated identity with other identity providers.
- Multi-Factor Authentication (MFA): Strengthens researcher authentication.
- Key and Certificate Management: Key Vault, Hardware Security Module and centralized secret and certificate management.
- Oracle Cloud Guard: Monitors for misconfigurations or suspicious access attempts.
2. Safe Projects (only approved research is permitted)
Goal: Research projects must align with ethical, legal, and governance rules.
OCI Services:
- Tenancy and compartment-based: Resource Organization and Governance.
- IAM + Policy Enforcement: Define policies restricting access to specific datasets or environments based on project approval.
- Oracle Audit Service: Provides immutable audit logs showing which users accessed what resources and when.
- Data Catalog: Helps classify datasets, tag them with governance metadata, and track usage
3. Safe Data (privacy-preserving, de-identified data)
Goal: Protect sensitive data through pseudonymization, encryption, and minimization.
OCI Services:
- OCI Vault: Encryption key management, automatic rotation, and secret storage.
- OCI Data Safe: It is important to protect patient health information and any PII data used in the research. OCI Data Safe service helps discover and classify sensitive data, apply masking, and monitor activity. In some cases, data can be anonymized before being sent to the cloud.
- Data Encryption: Block volume, boot volume and backups are all encrypted at rest by default, Object Storage with Server-Side Encryption. Default AES-256 encryption at rest. Data in transit also encrypted using TLS 2.0.
- Application and Data Integration Service: For preparing, transforming, and anonymizing data before loading into TRE.
4. Safe Settings (secure environment to analyze data)
Goal: Provide a locked-down, monitored workspace where researchers can analyze but not extract sensitive data.
OCI Services:
- Compute Instances (VM, Bare Metal, GPU): For general purpose computing, high-performance or AI/ML workloads.
- OCI Container Engine for Kubernetes (OKE): Containerized research environments with controlled software stacks.
- Bastion Service: Provides restricted, audited SSH access into private environments.
- Virtual Cloud Network (VCN): Isolates TRE resources with subnets, firewalls, and private endpoints.
- Distributed Data Processing: OCI provides Dataflow, a spark based managed service and data science services to process large data at scale and apply AI/ML techniques.
- Oracle Secure Desktops (VDI setups): Researchers work inside OCI-hosted desktops with no local data expo
5. Safe Outputs (only non-disclosive results can leave)
Goal: Ensure that only safe, aggregated, non-identifiable results leave the TRE.
OCI Services:
- Data Loss Prevention (via partner integrations): Scans outputs before export.
- Logging & Monitoring: Provides service, application performance management (APM) and custom log service to track and monitor all aspects of data access and transformation.
- Audit Trails: Immutable logs provide oversight on what outputs are exported.
- Object Storage Pre-Authenticated Requests (PARs): Can be tightly controlled for output sharing, with short-lived tokens and policies.
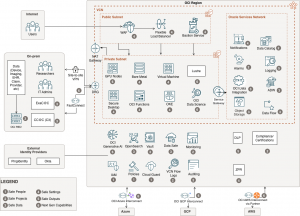
Architecture Diagram
Oracle Cloud Landing Zone for TRE
One of the key aspects of Oracle Cloud is simplicity and automation. To create a TRE environment on Oracle Cloud, customers can take advantage of Oracle Cloud Landing Zone implementation automation. This automation provides simple recipes using the most popular Infrastructure as Code tool, Terraform, for faster time to production with security, reliability, performance and operational efficiency as described above. These recipes are easily customizable. Customers can use OCI CLI, SDKs or API to configure and deploy landing zone components.
OCI delivers standardized Landing Zones framework, now available on the new OCI Landing Zones GitHub organization, your one-stop shop to accelerate your TRE on OCI. This initiative brings together the best practices across all OCI services discussed above and implementations from product and worldwide field teams across Oracle. They converge on a single, unified strategy and standard framework to support all modern and optimized TRE environments on OCI.
Landing zone framework for TRE on OCI provides blueprints, landing zone extensions (for customization), and modules such as Identity and Access Management, Networking, Observability, Monitoring, Security and Governance.
References
https://pmc.ncbi.nlm.nih.gov/articles/PMC9533202/
https://ukdataservice.ac.uk/help/secure-lab/what-is-the-five-safes-framework/