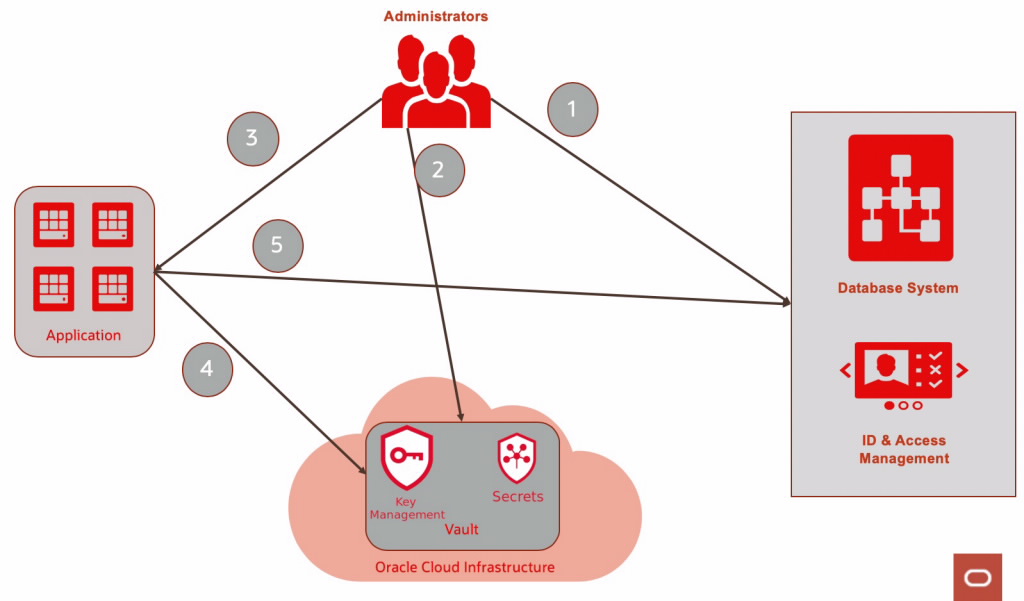
When you are designing application or configuring services in Public Cloud, many a times you need to store credentials or authentication details in configuration file or in code. As a best practice you can use Vault to store these secret data and use them in your configuration file or in code. Oracle Cloud Infrastructure (OCI) provides Vault, a managed cloud service, that provides a secure store for secrets. You can store passwords, certificates, SSH keys, or authentication token, that you use in configuration files, as secrets in OCI Vault. You can retrieve secrets from the Vault service when you need them to access resources or other services. You can also create Master Encryption Key in OCI Vault to encrypt the Secret information.
In this blog, I will show you how you can use OCI Vault Secrets to store Database User Credentials as well as Database Connection Details and demo Python script to connect to database using secrets in vault.
Advantages of secrets in Oracle Cloud Infrastructure vault
- You can centralize secrets management and only administrators will have Create, Update, and Delete permissions on secrets.
- You can rotate/update secrets/credentials without any changes in the consumer application.
- Secrets are encrypted at rest to improve security posture.
- Secrets management proliferates machine to machine communication or serverless computing by making it secure.
So let us begin with storing Database Credentials as well as DB Connection details as Secrets in OCI Vault.
Step1: Create OCI Vault
To start with, login to OCI Console using your tenancy details (name, user credential). Once logged in, go to OCI Menu >> Identity & Security >> Vault
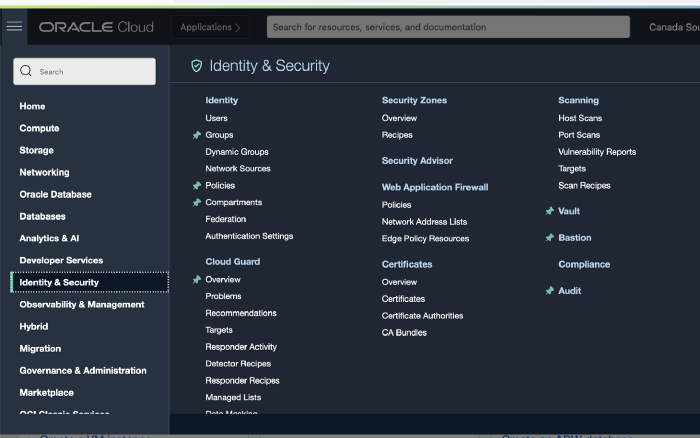
OCI Vaults are logical entities where encryption keys are created and durably stored. Click on Create Vault
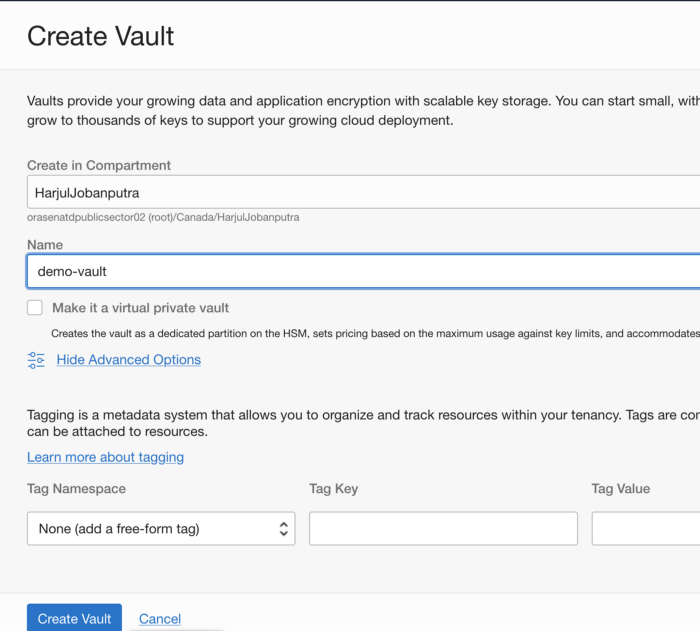
Provide Name to the Vault and choose click check box to have Virtual Private Vault (isolated partition on HSM )
Once the Vault is created, you should be able to create Master Encryption Key and store in the vault.
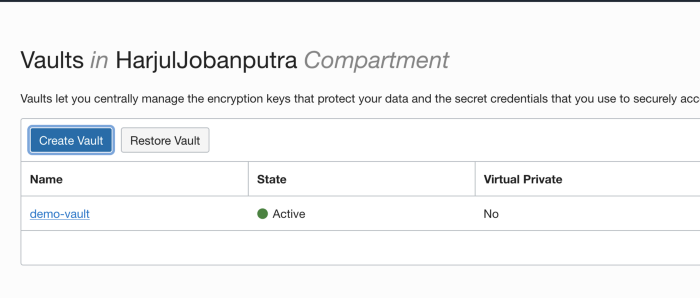
Click Vault Name.
Step2: Create Master Encryption Key
Under Resources, click Master Encryption Key.
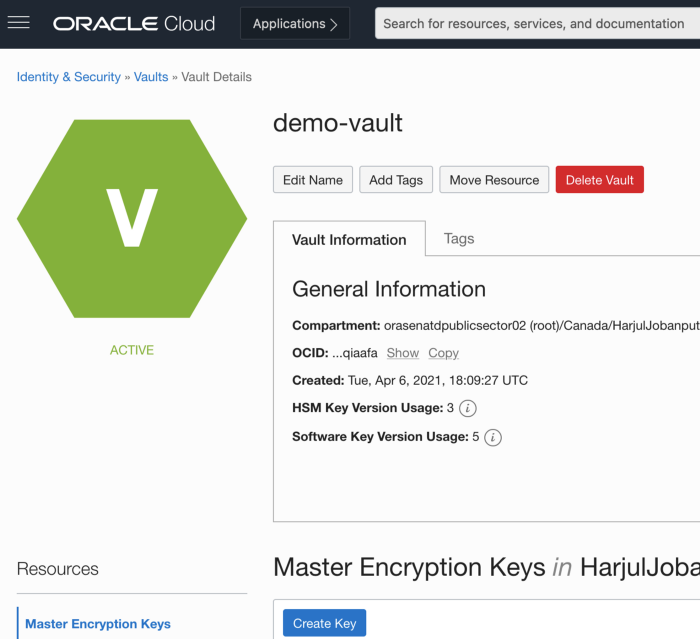
Click Create Key
In the Create Key dialog box, choose a compartment from the Create in Compartment list.
Click Name, and then enter a name to identify the key.
Select Protection Mode (HSM or Software) that decides where the encryption key persists and cryptographic operations processed.
Specify the key length, in bits, by choosing a length from the Key Shape: Length list.
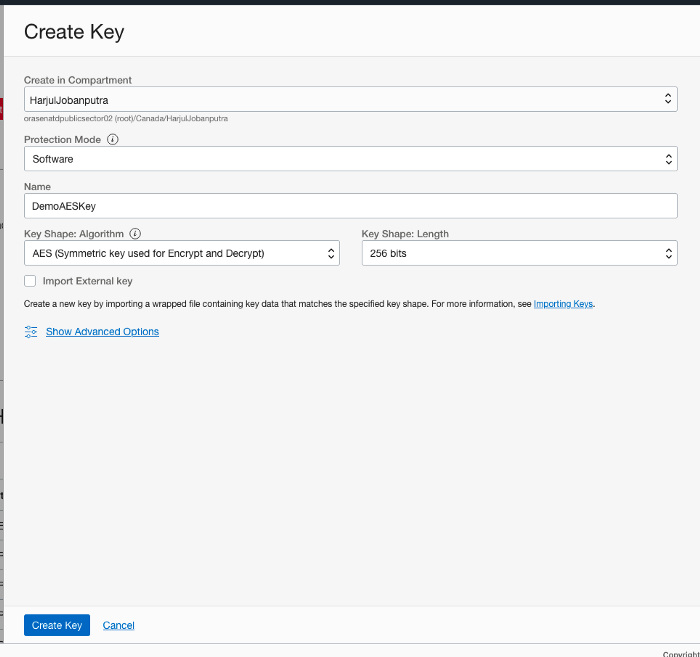
When you are finished, click Create Key.
Ensure the state changes from “Creating” to “Enabled”. Enabled state indicates you are ready to use this key with Other Oracle Cloud Services.
Step3: Create Secret to Store User Credentials
Go to OCI Vault >> Resources
Click Secrets to Create new secret
Provide following details:
- Name: Unique name to the secret
- Description: Description about the secret
- Encryption Key: Select encryption Key created in previous step. This key will be used to encrypt the secret.
- Secret Type Template: Plain-Text or Base64. You can provide secret contents in plain-text when you use the Console to create a secret or secret version, but secret contents do need to be base64-encoded before they’re sent to the service. The Console automatically encodes plain-text secret contents for you if you choose this format
- Secret Content: Provide ADMIN User’s password here.
Click Create Secret.
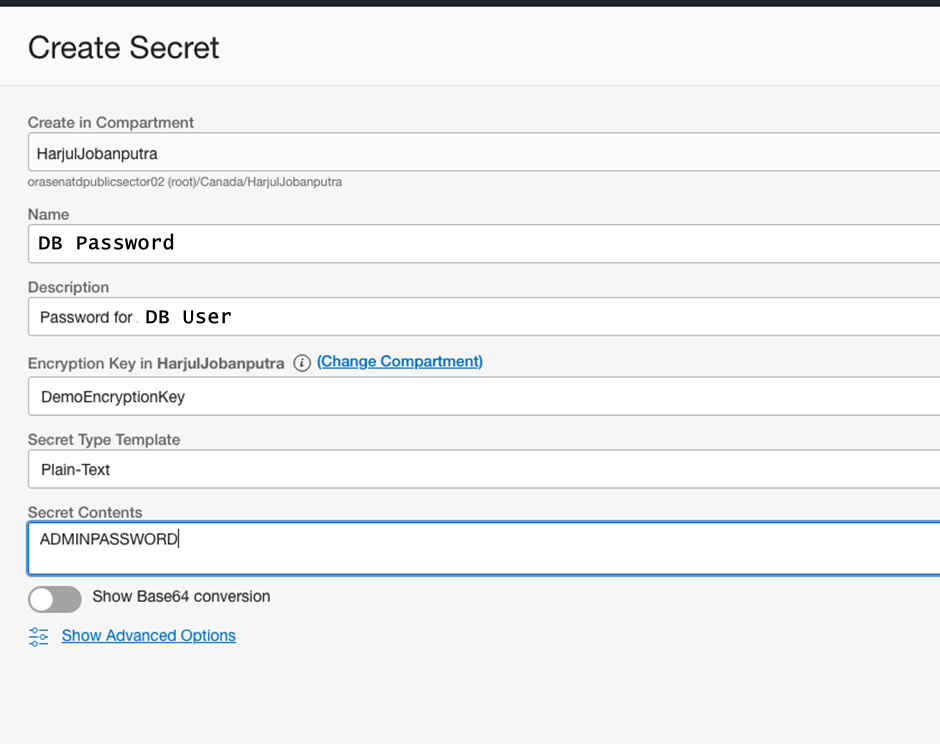
This will create the secret in the OCI Vault.
You can also define Secret Rules. There are two Rule Types:
• Secret Reuse Rule: You can either enforce the reuse rule so it applies even to deleted secrets versions, or you can allow reuse of secret contents from deleted secret versions.
• Secret Expiry: You can set how frequently you want secret contents to expire and what you want to happen when the secret or secret version expires
Now we can use Python SDK to connect to the vault and fetch the database password secret. Below code snippet showcases script to connect to the database using secret and display the timestamp from database.
Summary
In the end – this implementation is a great example of how a developer can take advantage of a myriad of relatively new cloud-native features that OCI offers and continues to build upon – Autonomous Database/DBCS/EXACS, OCI PL/SQL SDK’s, OCI Vault and more. Then, with some simple configurations we can develop an out-of-the-box, secure and DevOps friendly solution for an integration challenge that has existed over the years.
References
