We’re pleased to announce the general availability of internet protocol security (IPSec) tunnel enhancements for Oracle Cloud Infrastructure (OCI) Site-to-Site VPN service… and you should be too! We’re enabling these enhancements to address customer demands for new use cases and practical user experiences when designing and deploying Site-to-Site IPSec VPN tunnels.
These enhancements are now available in all commercial regions and coming soon to government regions. To learn more about these enhancements, configurations, use cases, and how to programmatically deploy an environment for quick functional testing using a single OCI tenancy, Libreswan VPN, Terraform, and Ansible, continue reading!
As cloud adoption continues to gain momentum in 2022, IPSec virtual private network (VPN) tunnels remain a popular option (with FastConnect) for customers to establish secure access to their hybrid-cloud environments. Customers now have more control over provisioning and greater visibility into the overall health status of the IPSec connection.
Specifically, customers can now customize phase 1 and 2 IKE proposals with a combination of parameters that include the following examples:
-
Security association (SA) lifetimes
-
Dead peer detection (DPD)
-
IKE initiation
-
Perfect forward secrecy (PFS)
-
NAT traversal (NAT-T) settings
Customers also now have access to health status and diagnostics views for tunnels, their security associations, and border gateway protocol (BGP) routing through the Oracle Cloud Console to aid in troubleshooting and monitoring.
Use cases
The IPSec tunnel enhancements for OCI Site-to-Site VPN service offer the following use cases and benefits:
-
Regulatory and compliance: Customers can now meet regulatory compliance, such as FIPS, PCI, and HIPPA, and conform to their own internal and external best practice configuration standards with flexibility to create IPSec phase 1 and 2 IKE proposals that include only approved IPSec parameters.
-
Trouble resolution: Customers are now enabled to perform more effective self-diagnosis. When OCI detects an issue that prevents the establishment of an IPSec tunnel, the Console now shows troubleshooting information regarding, error cause, downtime, and remediation steps to assist with initial tunnel setup and aid in faster recovery time during an outage. Often, fixing a connection requires changing default values of certain IPSec parameters on the OCI side, which are now available to the customer to modify through the Console.
-
IPSec tunnel visibility: With enhanced health and status views, the Console now displays if the tunnel state is up or down. Customers can also now view health status for security associations that include uptime, health status (listening or up), encryption domains, and error status from the Console for improved feedback on status of the connection.
-
Border gateway protocol (BGP) route visibility: A common design choice for routing over the tunnel is to use BGP, a scalable and dynamic way to exchange routes between OCI and customer-premises equipment (CPE). Customers can now validate and troubleshoot BGP routing from the OCI side of the IPSec connection through the Console. Tunnels that use BGP routing now show the routes received and sent to the CPE and age, best path, AS path length, and AS path.
-
Interoperability: Although IKE and IPSec are IETF standards, often interoperability issues occur between different vendors that result in failed or broken connections. With the ability to customize IPSec parameters, customers have the flexibility to create vendor supported IKE proposals and avoid potential compatibility issues with the CPE. Customers can also use the CPE configuration Helper within the Console to assist with the generation of vendor-specific CPE configurations.
Usage
You can find more information on how to set up Site-to-Site VPNs in our setup guides. Customizing parameters of the IPSec Site-to-Site VPN service can occur either during initial creation of the connection or after deployment. We encourage you to read more about this new feature and its supported IPSec customization parameters within the online documentation, release notes, and the useful links at the end of this blog.
Customers need to use version 2 of the service. A quick way to validate is checking within the Console for the <v2> indicator. For customers who currently have existing IPSec tunnels deployed using the earlier version of Site-to-Site VPN, recreating the existing VPN connection automatically uses the new version. However, this new connection needs reconfigured preshared keys, IKE version, and other IPSec connection-related settings.
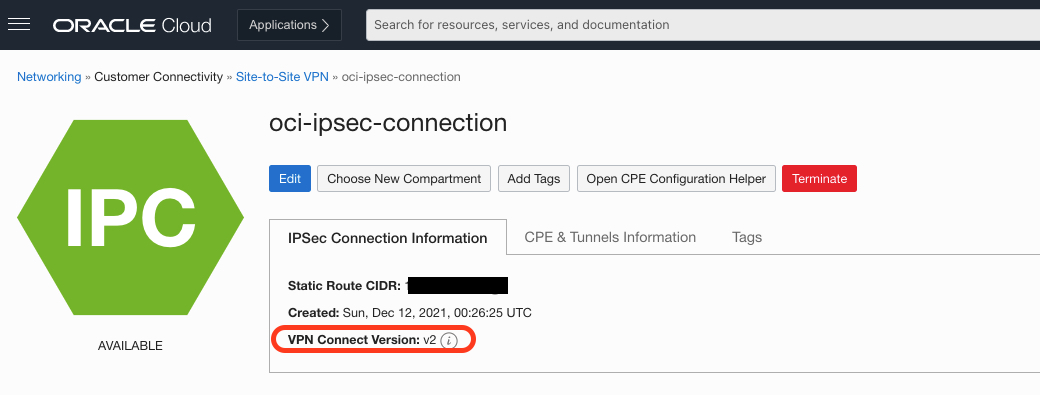
Figure 1: VPN Connect version indicator
IPSec tunnel customizations
In the Console, under Networking, Customer Connectivity, and Site-to-Site VPN, you can Create or click an existing IPSec Connection. Editing the connection allows you to select advanced options, where you can select custom IPSec parameters.

Figure 2: IPSec tunnel customizations configuration
Tunnel health and status
In the Console, under Networking, Customer Connectivity, Site-to-Site VPN, select oci-ipsec-connection.
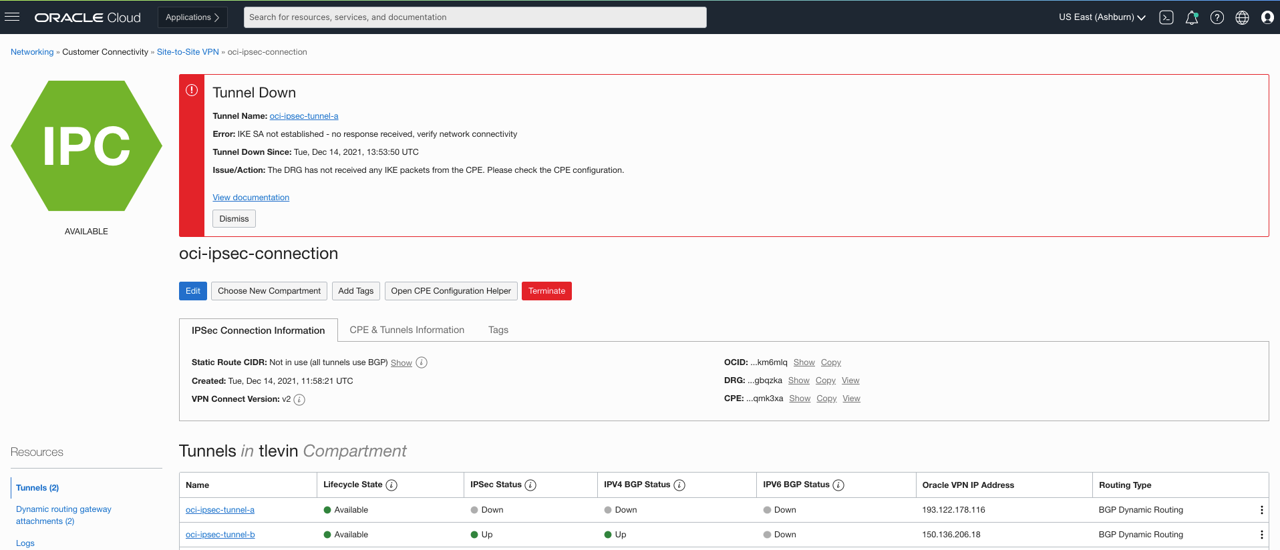
Figure 3: Tunnel health
Tunnel security associations
In the Console, under Networking, Customer Connectivity, and Site-to-Site VPN, select oci-ipsec-connection and then oci-ipsec-tunnel-a.
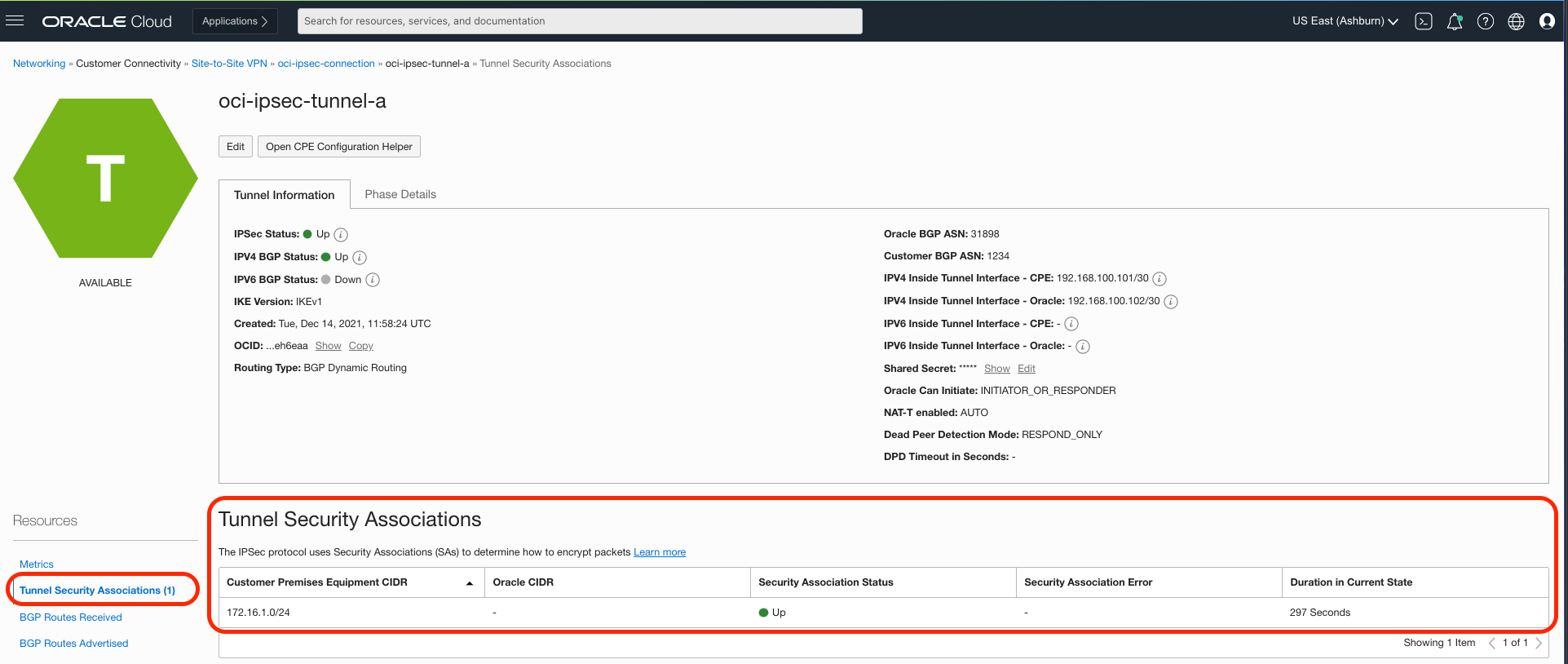
Figure 4: Security association health
BGP route visibility
In the Console, use the same path from the previous section.
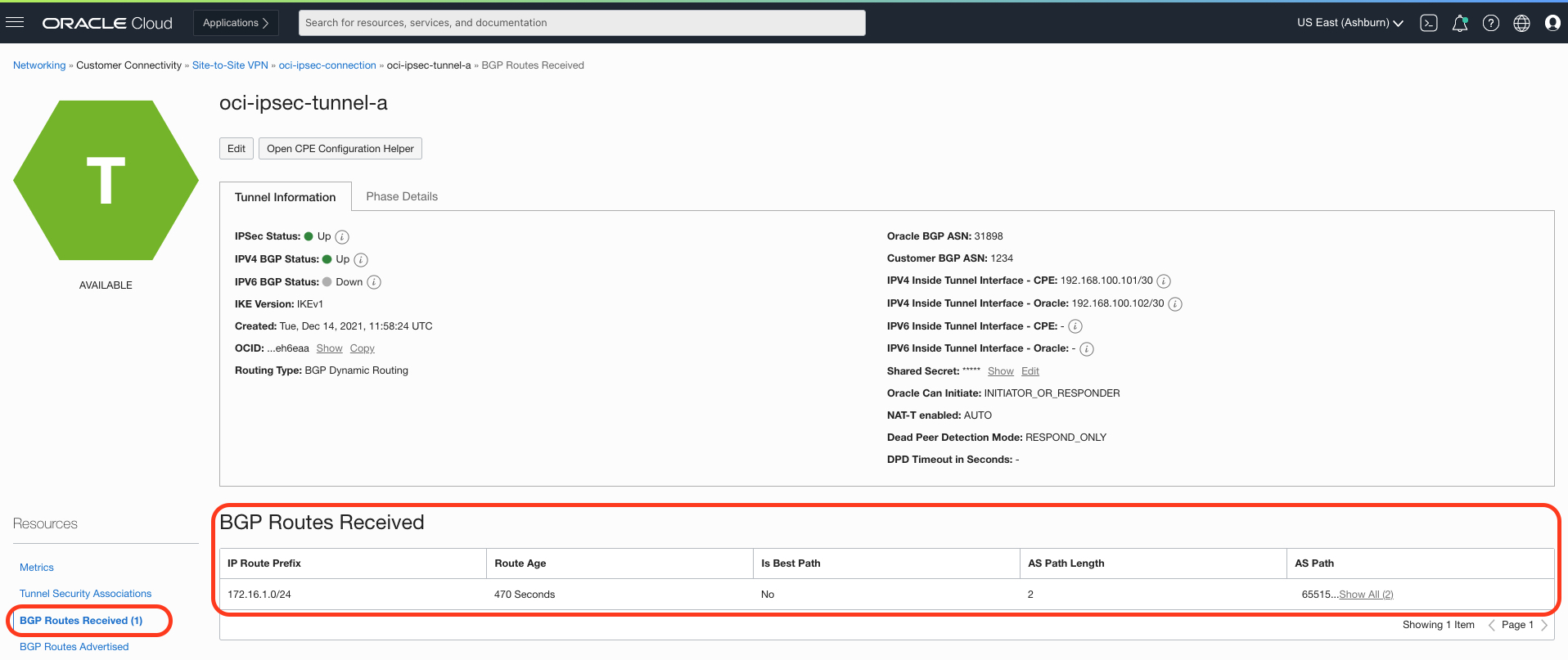
Figure 5: BGP routes received
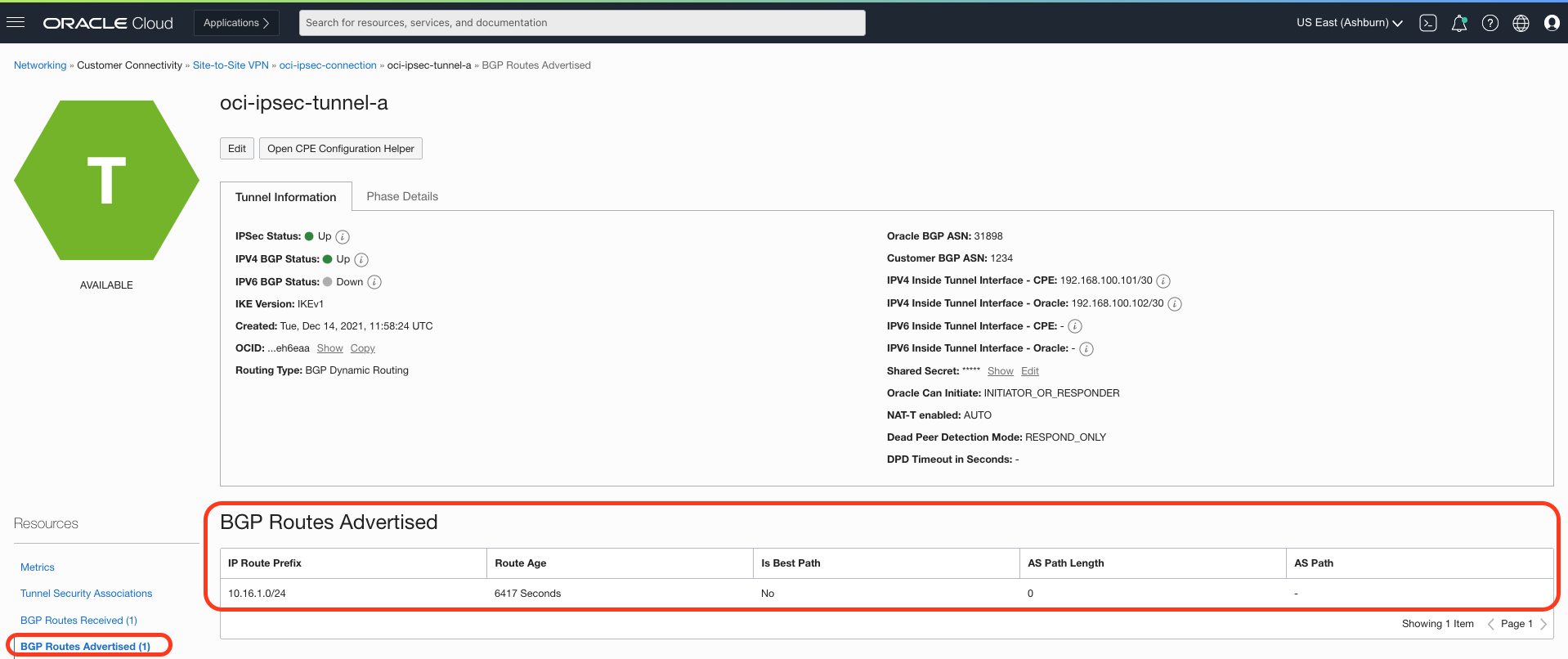
Figure 6: BGP routes sent
Take it for a spin!
Now that you have a better understanding of the use cases, configuration steps, and benefits of IPSec Tunnel enhancements, without much effort you can take OCI Site-to-Site VPNs for a test drive. Customers typically configured Site-to-Site VPNs through the Console.
However, for existing OCI users or people who sign up for an Oracle Cloud Free Tier account, automating the deployment of the following architecture is just a few keystrokes away, thanks to Terraform and Ansible’s provisioning frameworks. With the latest release of the Terraform OCI provider, the core resource oci_core_ipsec_connection_tunnels and data source oci_core_ipsec_algorithm now also include arguments and attributes related to the enhancements discussed earlier in this blog.
To get started, head over to the oci-ipsec-libreswan repository in Oracle Quick Start, our code exchange hosted on GitHub. There, you can find more details and the complete Terraform and Ansible manifests used for programmatically deploying the environment described. In no time, you can have an instant sandbox to perform Site-to-Site VPN and IPSec tunnel customization functional testing!
This process isn’t considered an OCI-validated best practice or production design. For reference architectures, we encourage you to read our documentation online in the OCI Architecture Center.
Architecture
The following architectural diagram highlights the networking and computes infrastructure used for the test. When you run it, Terraform and Ansible together deploy all components of the architecture within a single OCI tenancy across two separate VCNs.
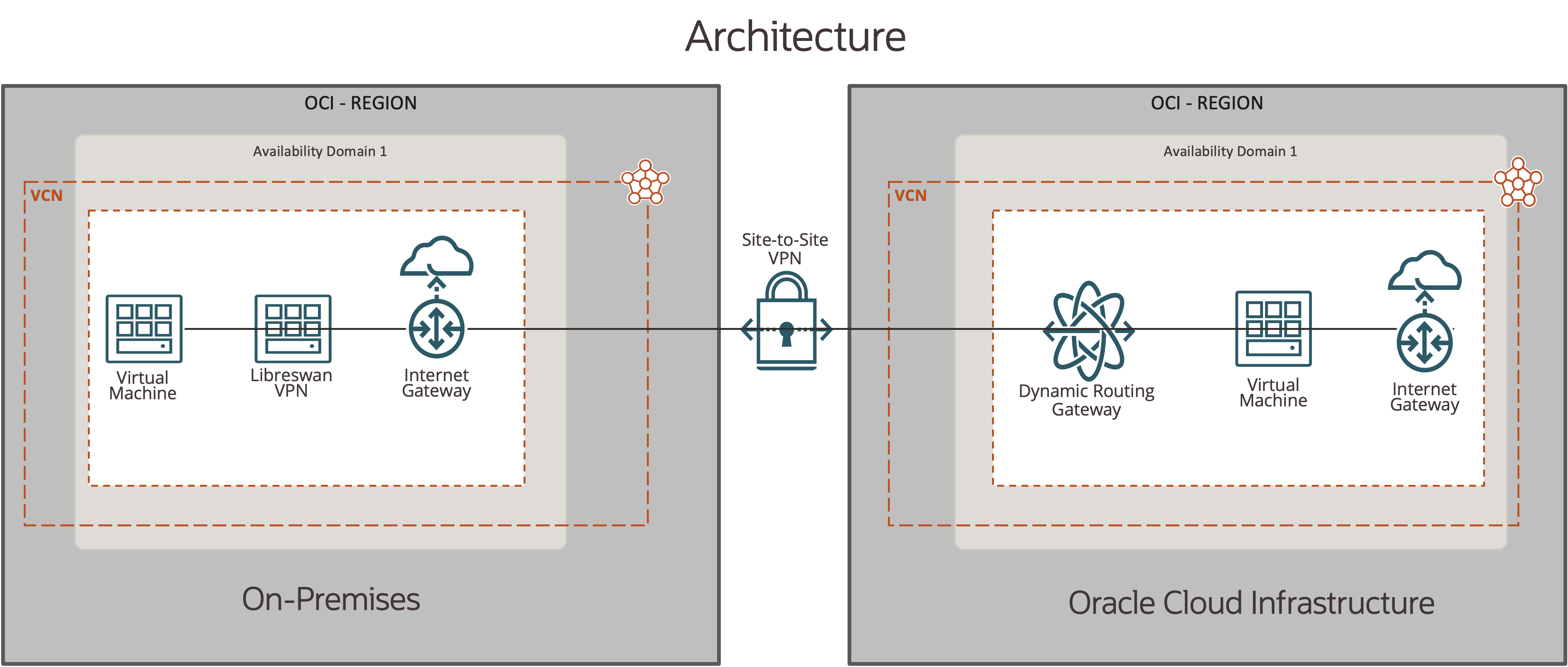
Figure 7: Test architecture
Summary of OCI Networking and Compute service
| On-premises |
Oracle Cloud Infrastructure |
|
|
Conclusion
Thank you for your interest in IPSec tunnel enhancements for OCI IPSec Site-to-Site VPN. IPSec tunnel enhancements are now supported for all OCI IPSec Site-to-Site VPN connections, giving customers the ability to create custom proposals. We encourage you to read more about this feature in the available OCI IPSec Site-to-Site VPN documentation and provide any product feedback you have.
-
Announcing multiple enhancements for Oracle Cloud Infrastructure IPSec VPNs
-
Creating a secure connection simulating on-premises environment using Libreswan on OCI
-
Connect your VPN to AWS, Azure, and GCP using each cloud’s native VPN service
