The idea of the post is to have two regions, one simulating On-Premises environment and the other Oracle Cloud Infrastructure, the article is going to provide a step-by-step procedure in order to achieve the goal of connecting both sides using LibreSwan.
Getting Started
The following components are required to create the secure connection for the test on this article:
- Two Regions of Oracle Cloud Infrastructure, one is going to be On-Premise environment and the other one OCI.
- Provision and configure Dynamic Routing Gateways (DRGs) and
- Provision and configure Customer-premises equipment (CPE)
- A Libreswan compute instance
- One compute instance in a public subnet in each region.
- One compute instance in a private subnet in each region.
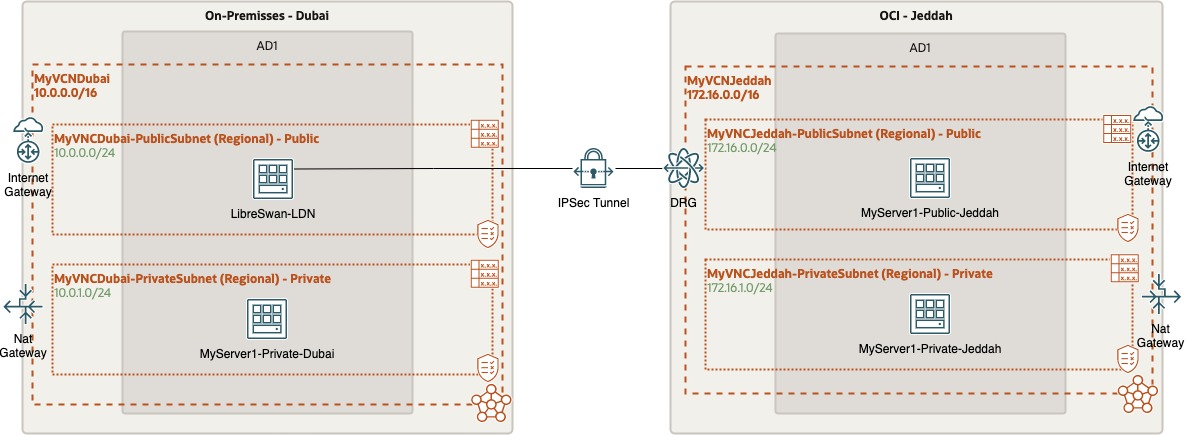
Architecture Table using LibreSwan terminology (Left/Right)
| Left Side: On-Premisses Dubai |
Right Side: Oracle Cloud Infrastructure Jeddah |
| VCN: 10.0.0.0/16 |
VPC: 172.16.0.0/16 |
| Public IP / ID: 192.123.82.87 |
DRG Public IP-Tunnel1: 140.204.35.0 |
| Internal IP: 10.0.0.148 |
CPE: 193.123.82.87 |
| Public Subnet: 10.0.0.0/24 Private Subnet: 10.0.1.0/24 |
Public Subnet: 172.16.0.0/24 Private Subnet:172.16.1.0/24 |
| Location: OCI – Uast Dubai – On-Premises side |
Location: OCI – Saudi Arabia West (Jeddah) |
Architecture Diagram
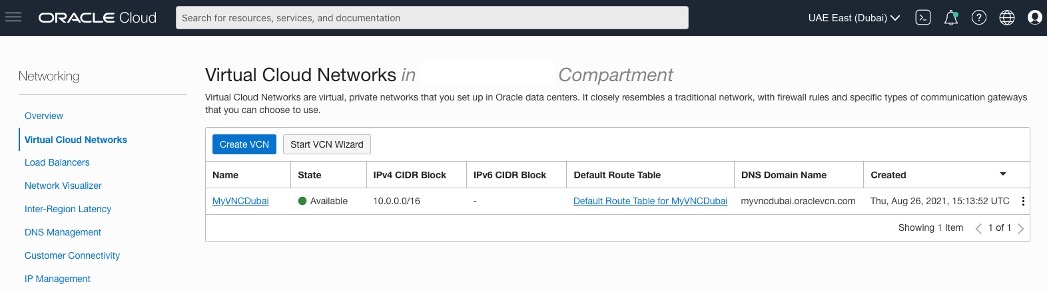
Creating VCN.
OCI – Uast Dubai – On-Premises.
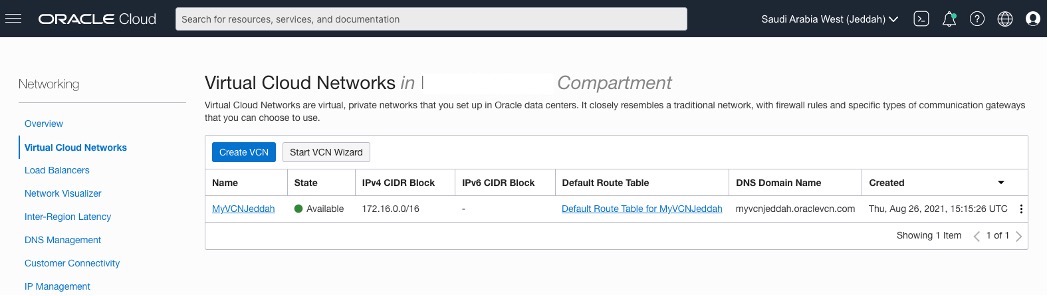
OCI – Saudi Arabia West (Jeddah).
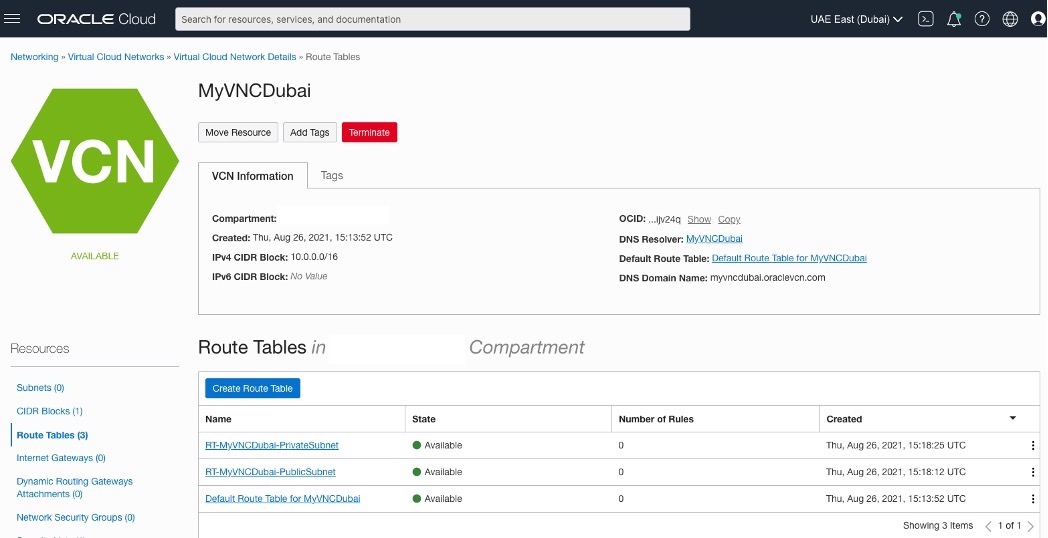
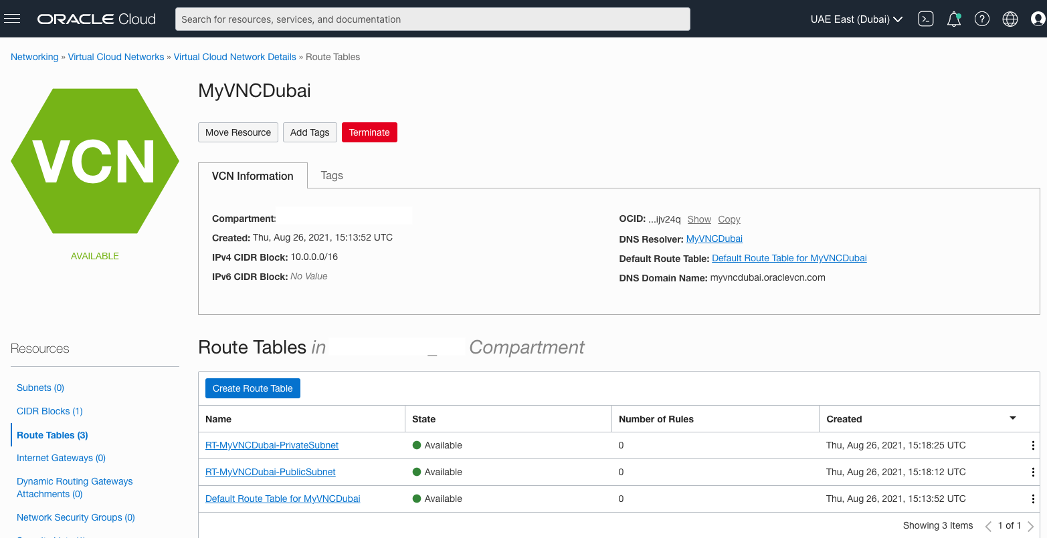
Creating two Route Table for each side.
OCI – Uast Dubai – On-Premises – One to handle public subnet and the other one to private subnet with no rules now.
OCI – Saudi Arabia West (Jeddah) – The same here.
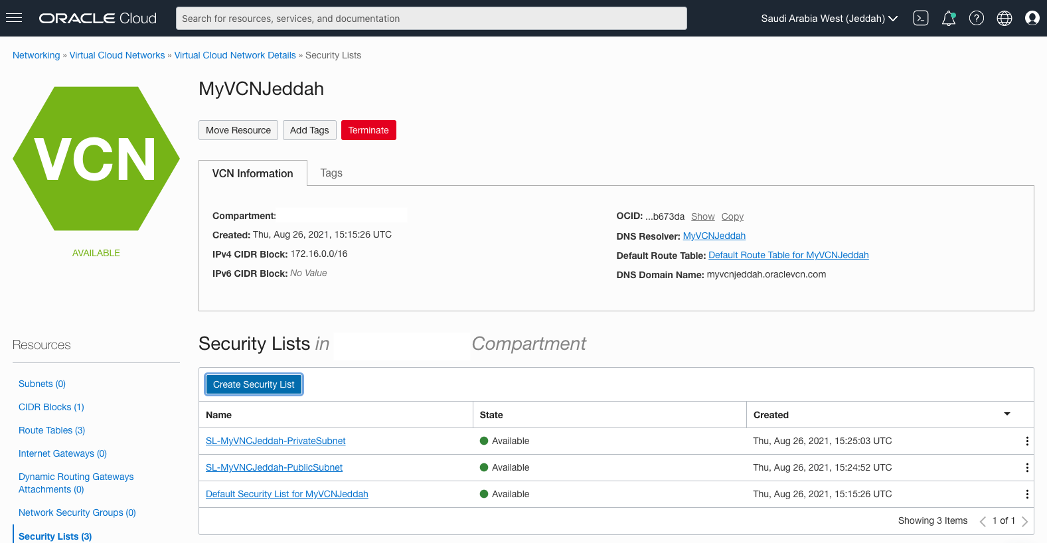
Creating two Security List for each side.
OCI – Uast Dubai – On-Premises – One security list for each subnet.
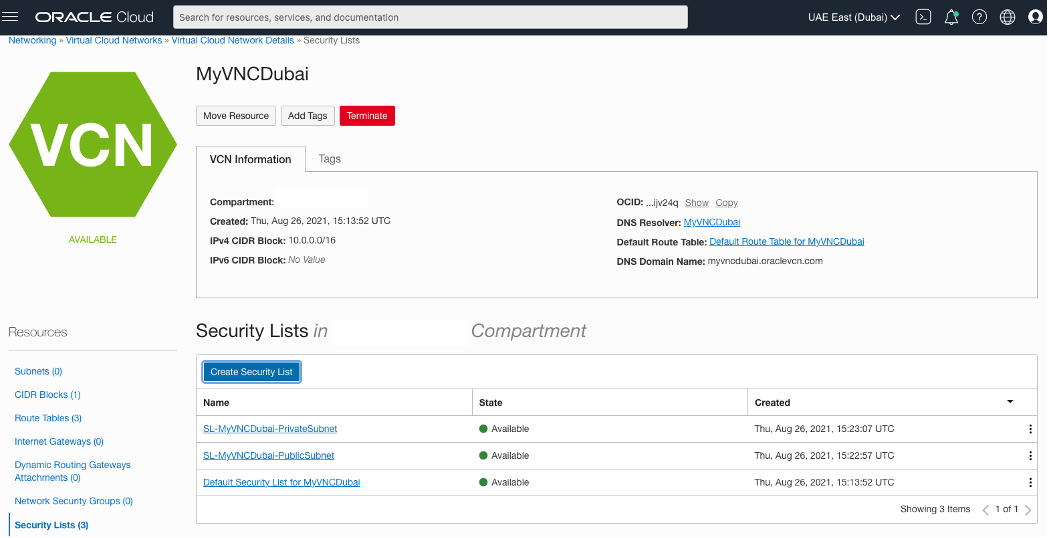
OCI – Saudi Arabia West (Jeddah) – The same here
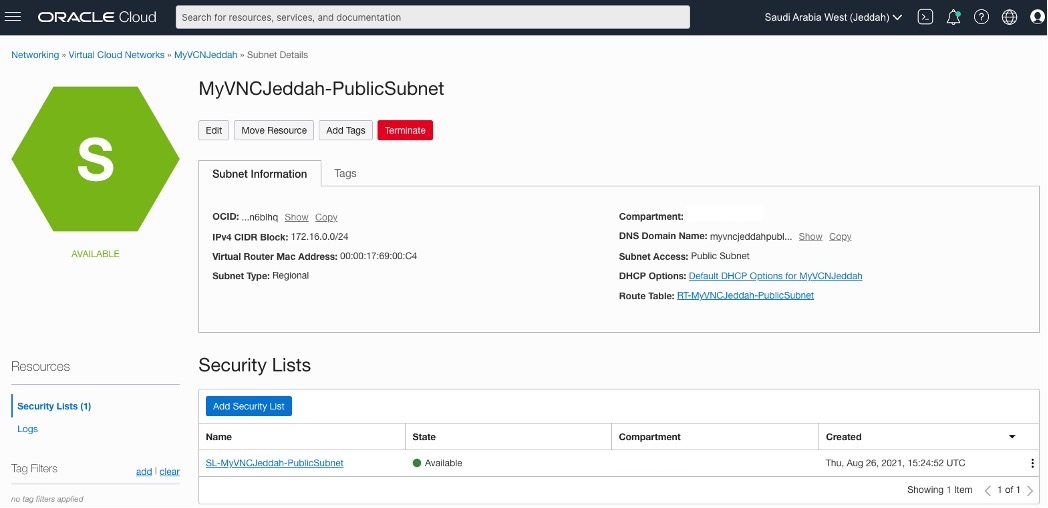
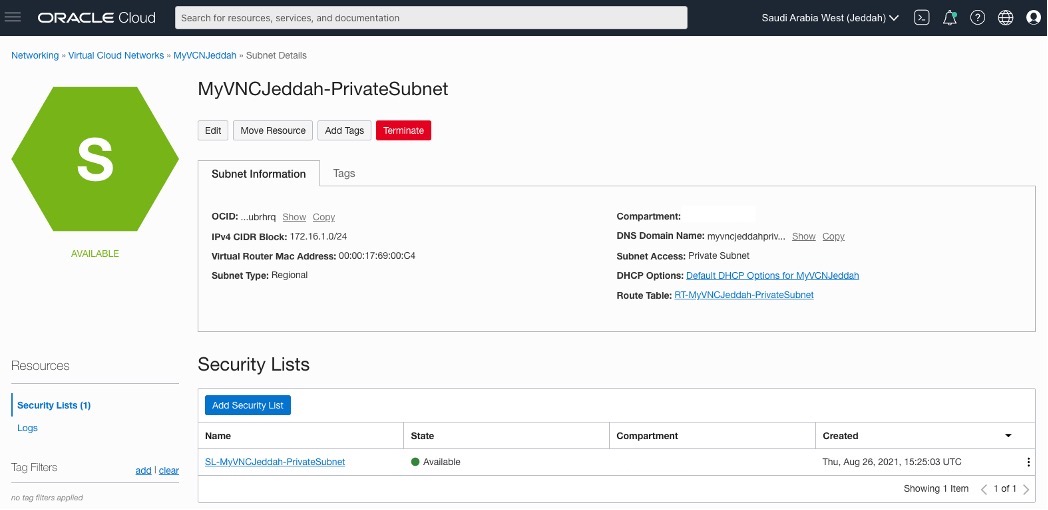
Creating two subnets (public and private) for each side
OCI – Uast Dubai – On-Premises – One for public subnet and the other for private subnet and attach the Route Table and Security List accordingly.
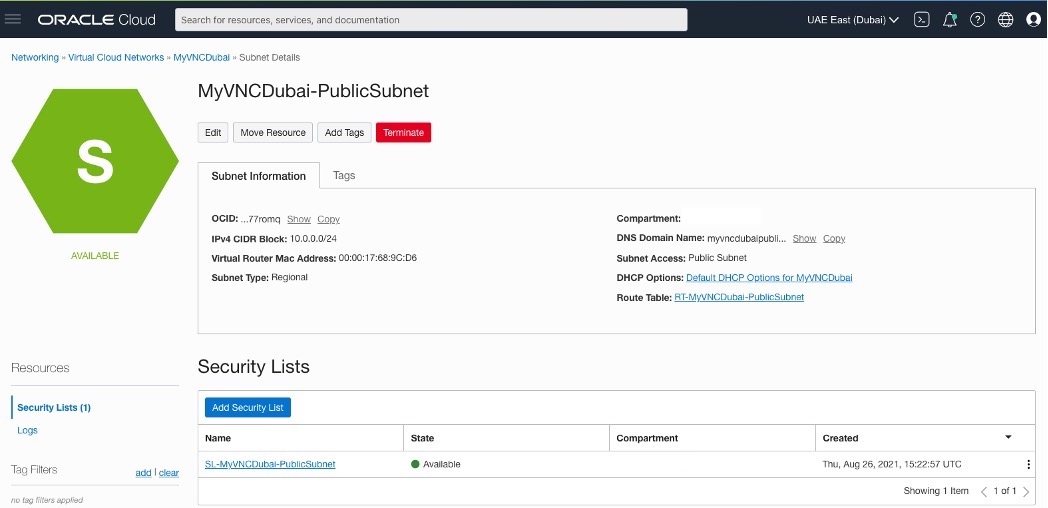
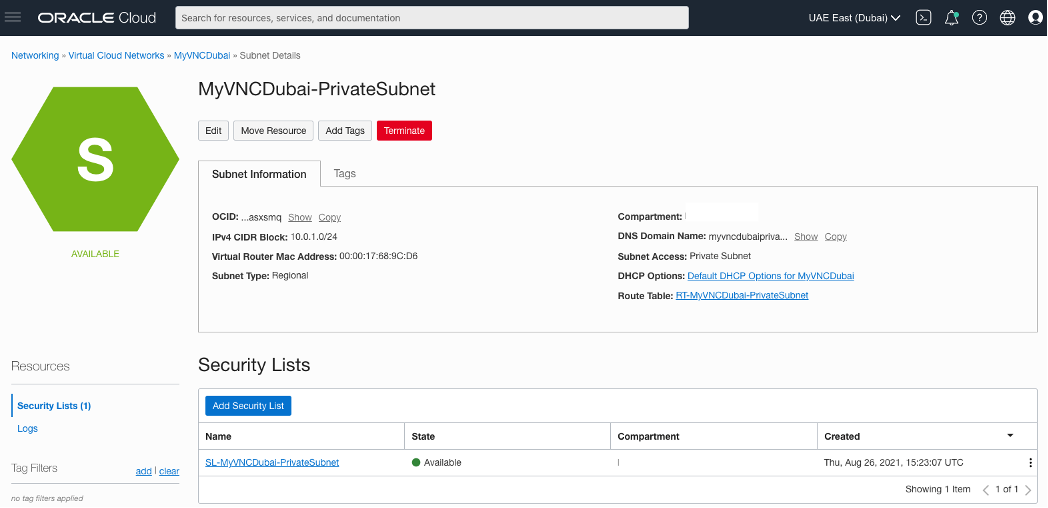
OCI – Saudi Arabia West (Jeddah) – The same here
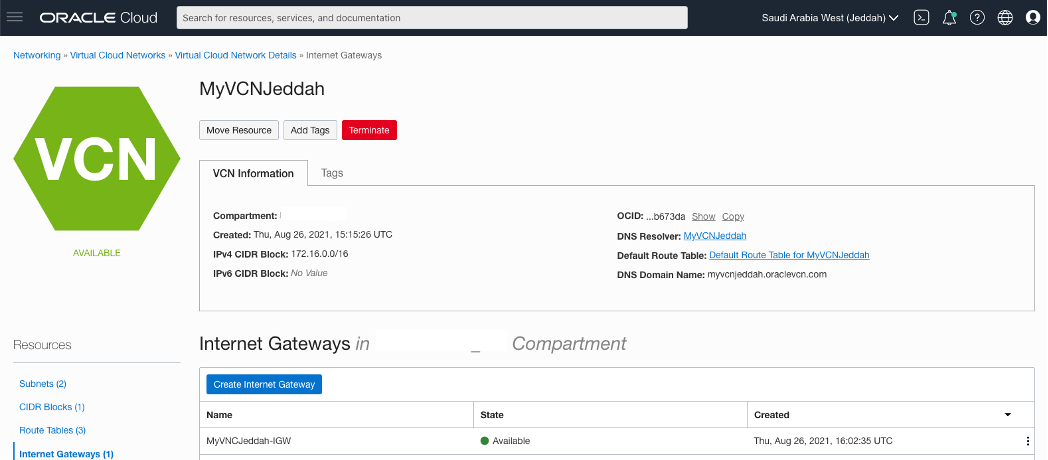
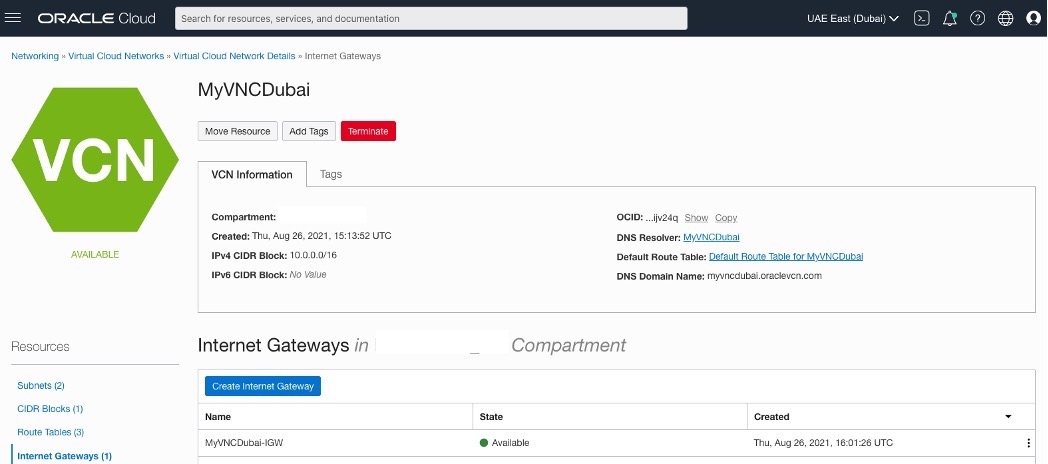
Creating an Internet Gateway for each VCN.
OCI – Uast Dubai – On-Premises.
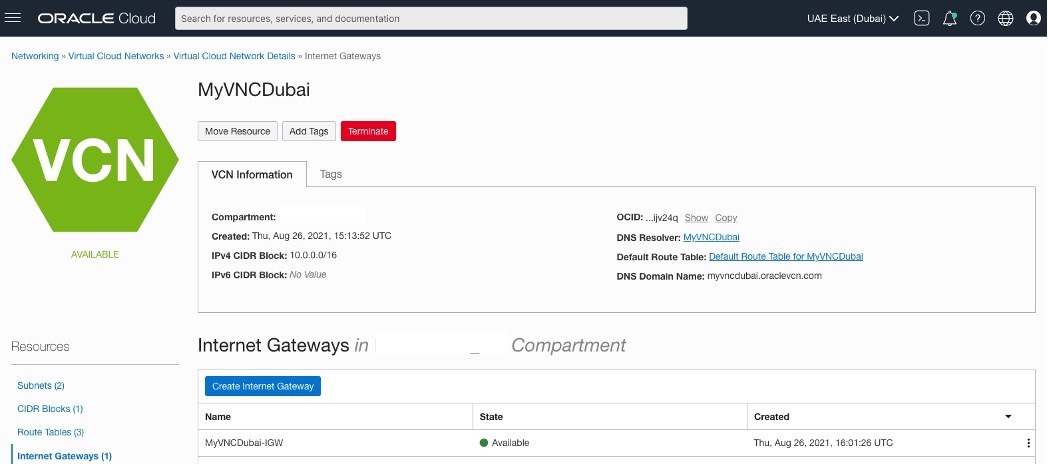
OCI – Saudi Arabia West (Jeddah).
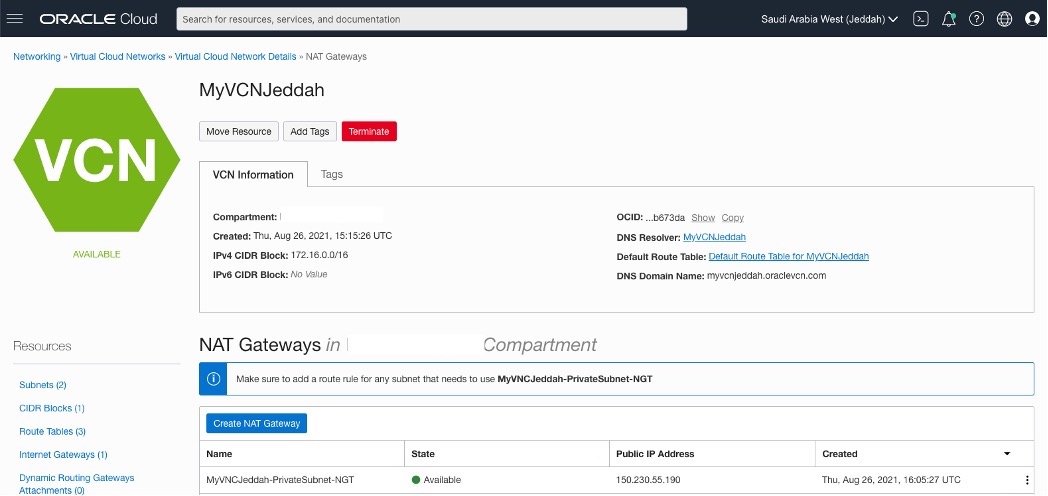
Creating a Nat Gateway for each VCN.
OCI – Uast Dubai – On-Premises.
OCI – Saudi Arabia West (Jeddah).
Lauching two Compute Instances in the OCI – Uast Dubai – On-Premises region, one in each subnet
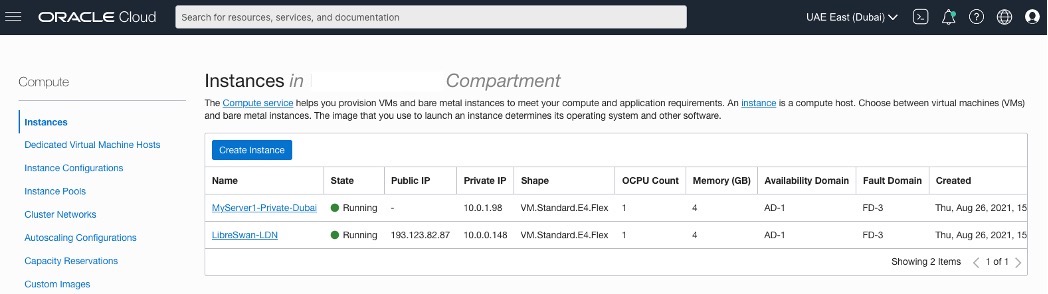
Lauching one Compute Instances in the OCI – Saudi Arabia West (Jeddah)
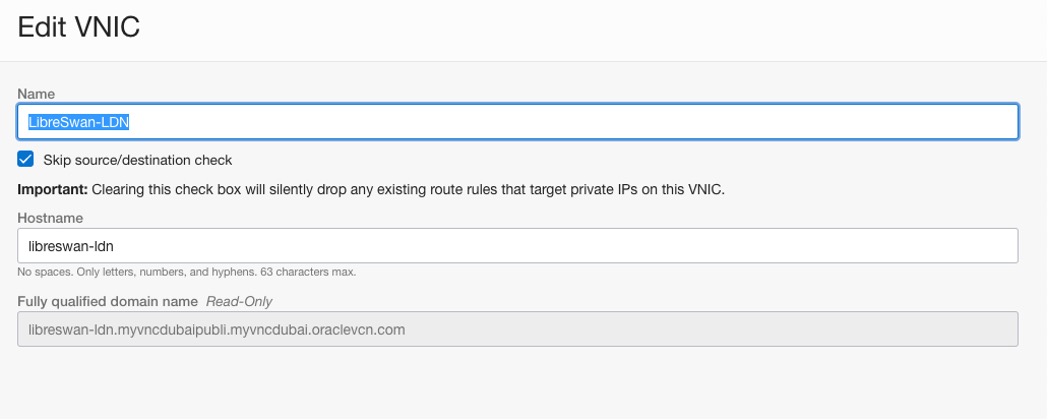
Enabling the option “Skip source/destination check” on the LibreSwan-LDN compute instance – OCI – Uast Dubai – On-Premises region.
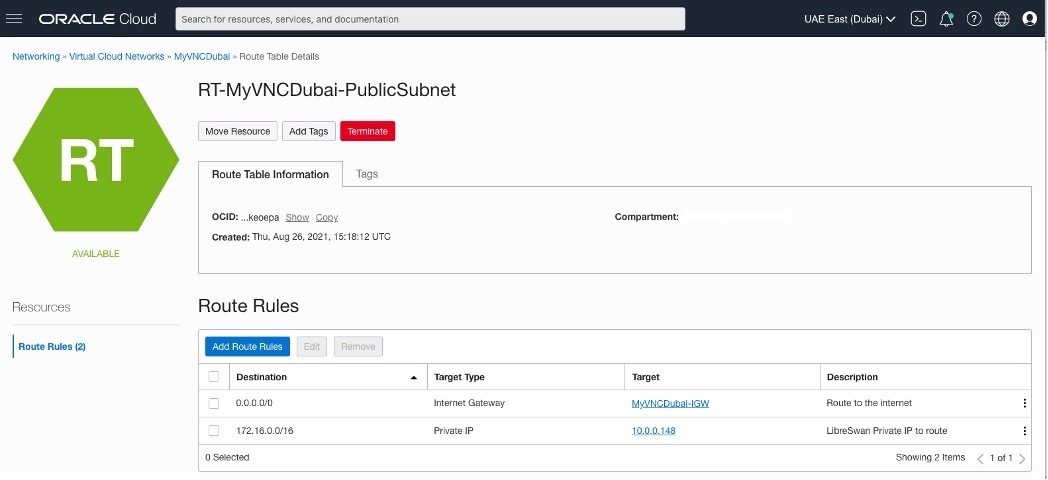
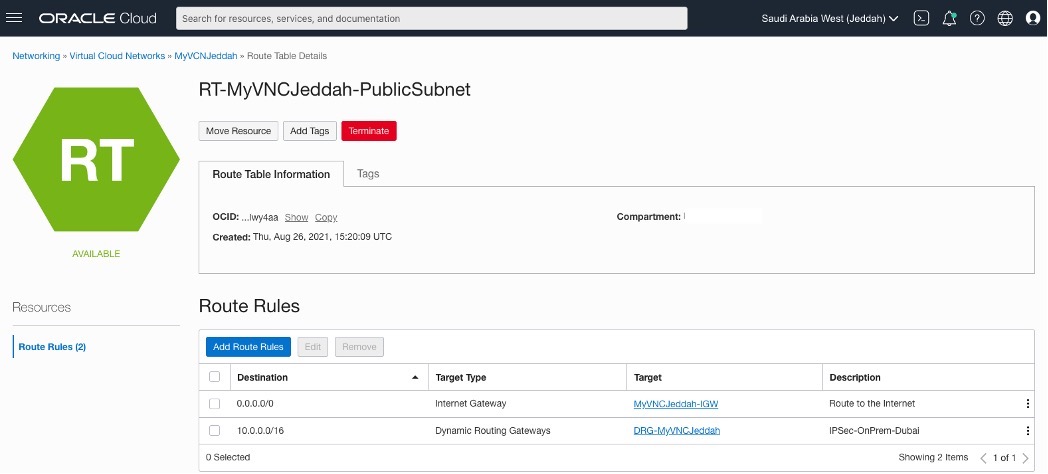
Adding Route Rules for RT-MyVNCDubai-PublicSubnet and RT-MyVNCJeddah-PublicSubnet
OCI – Uast Dubai – On-Premises.
OCI – Saudi Arabia West (Jeddah)
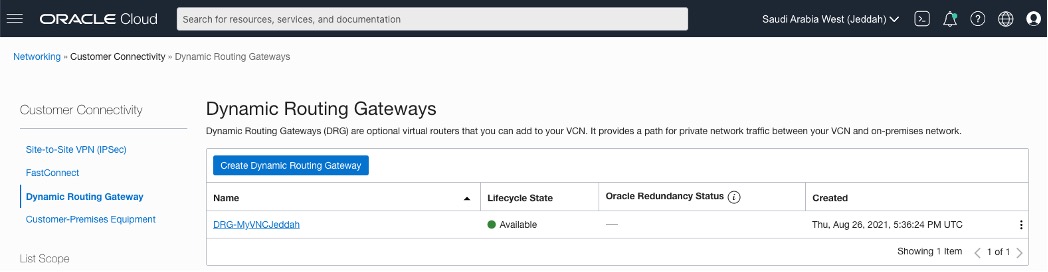
– Create DRG
– Attach the DRG to the VCN
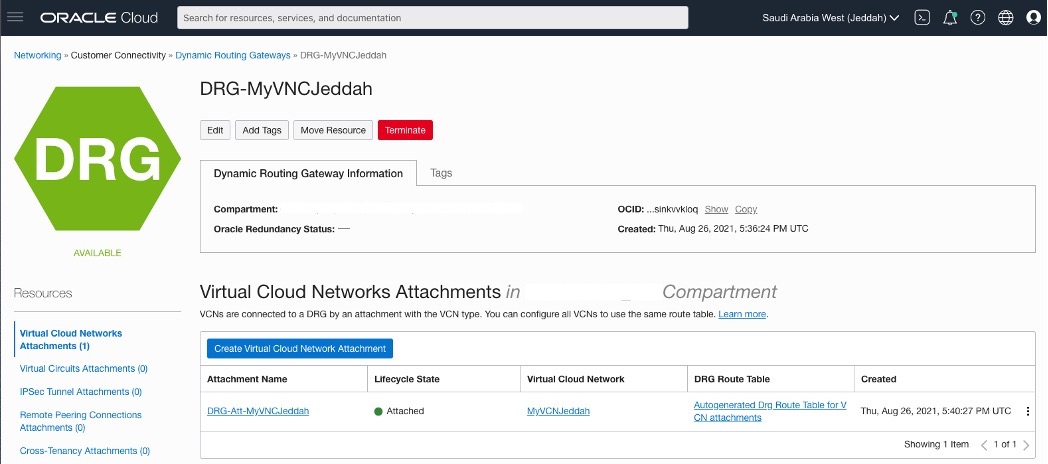
– Add the Route Rules to the Route Table
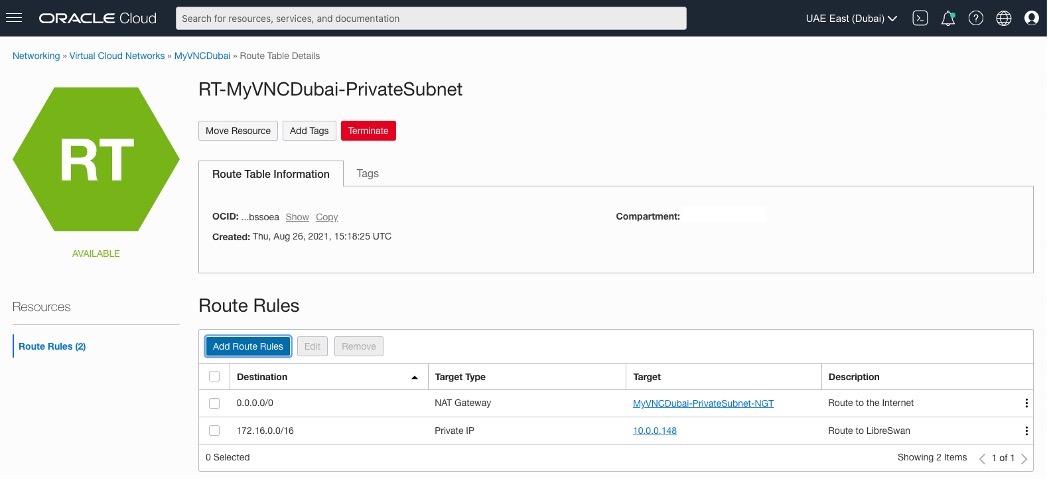
Adding Route Rules for RT-MyVNCDubai-PrivateSubnet and RT-MyVNCJeddah-PrivateSubnet
OCI – Uast Dubai – On-Premises
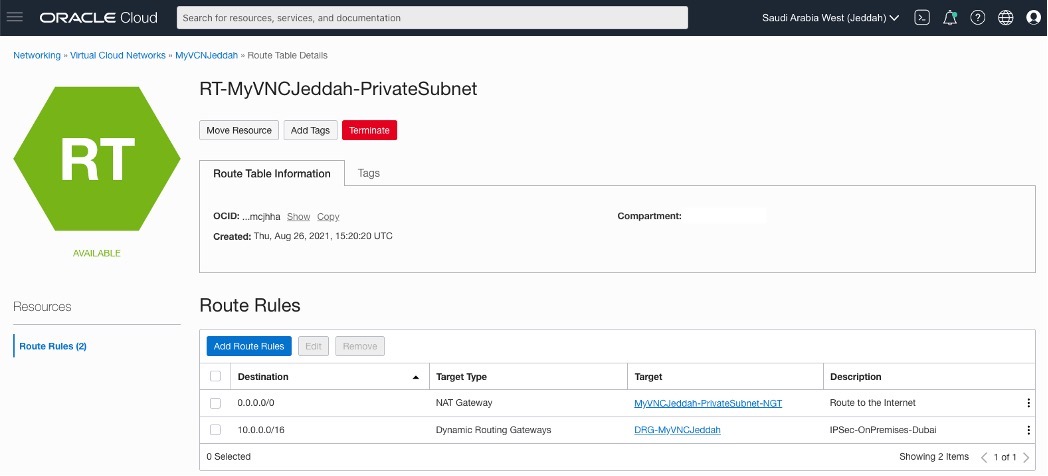
OCI – Saudi Arabia West (Jeddah)
Adding Security List Rules
OCI – Uast Dubai – On-Premises
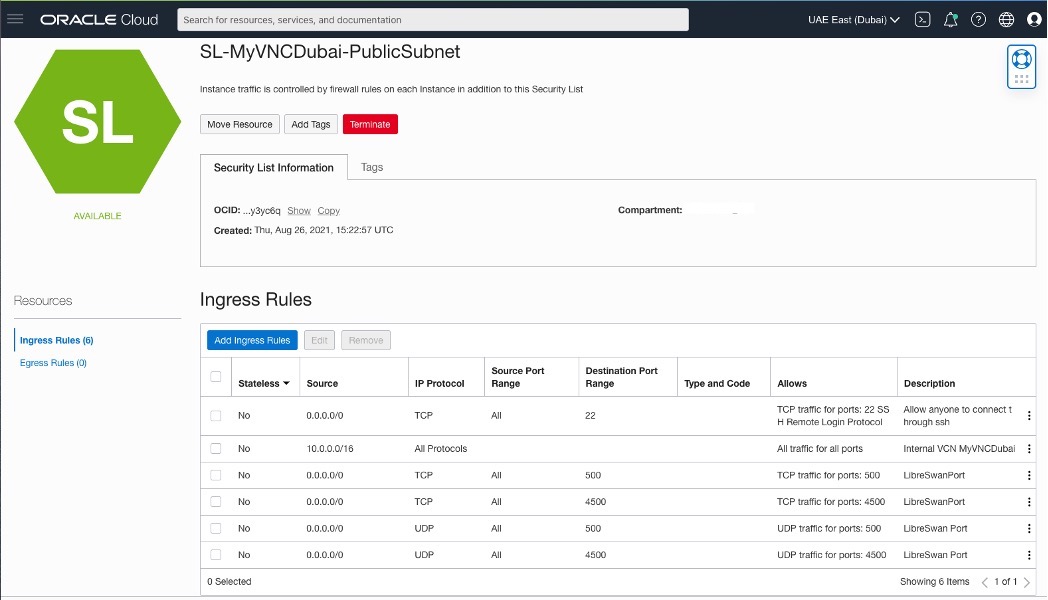
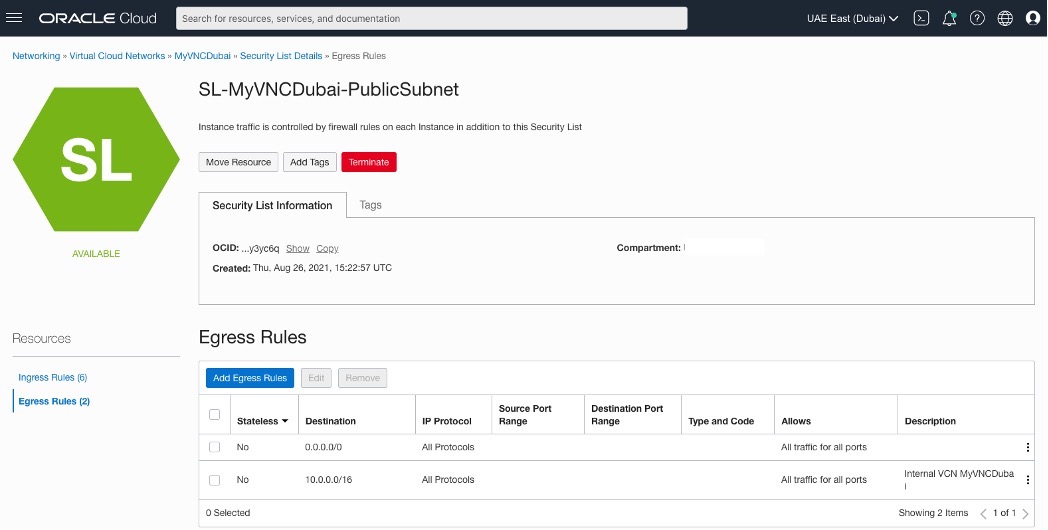
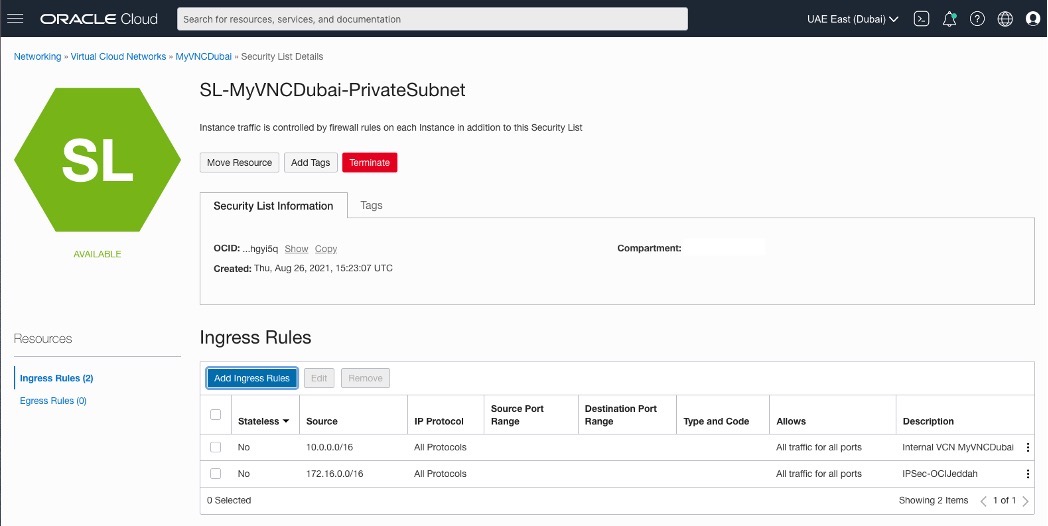
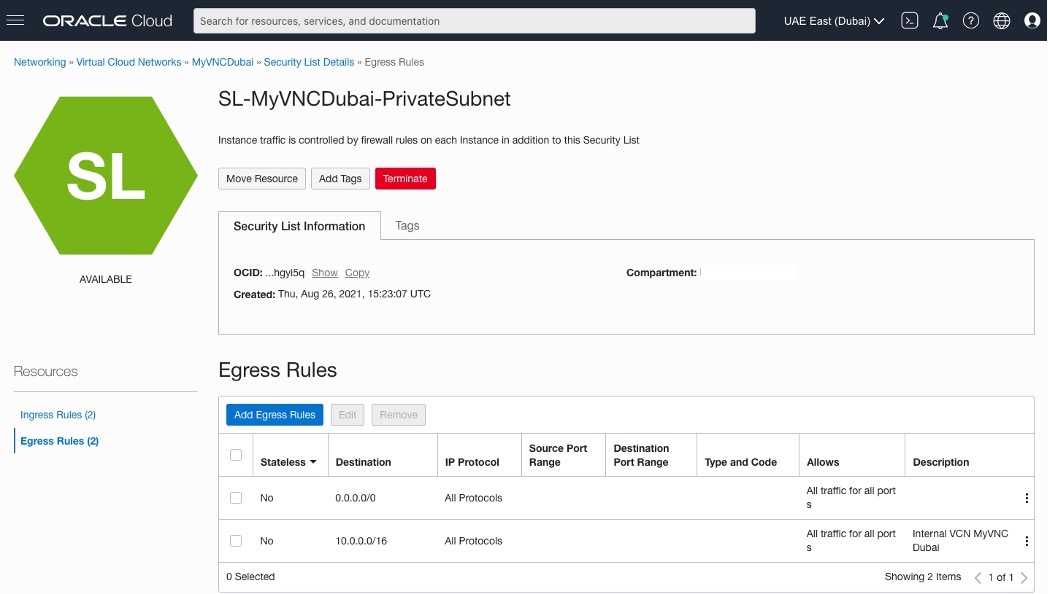
OCI – Saudi Arabia West (Jeddah)
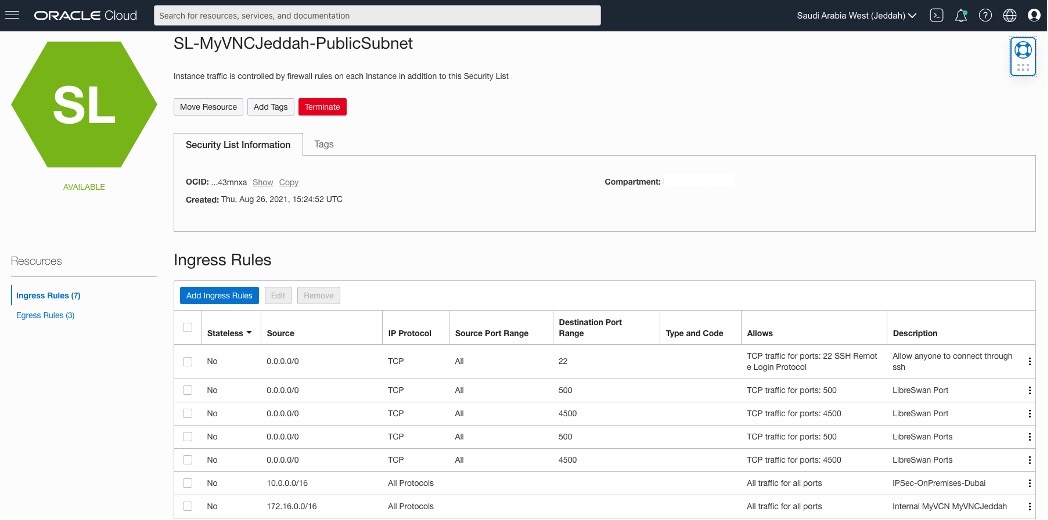
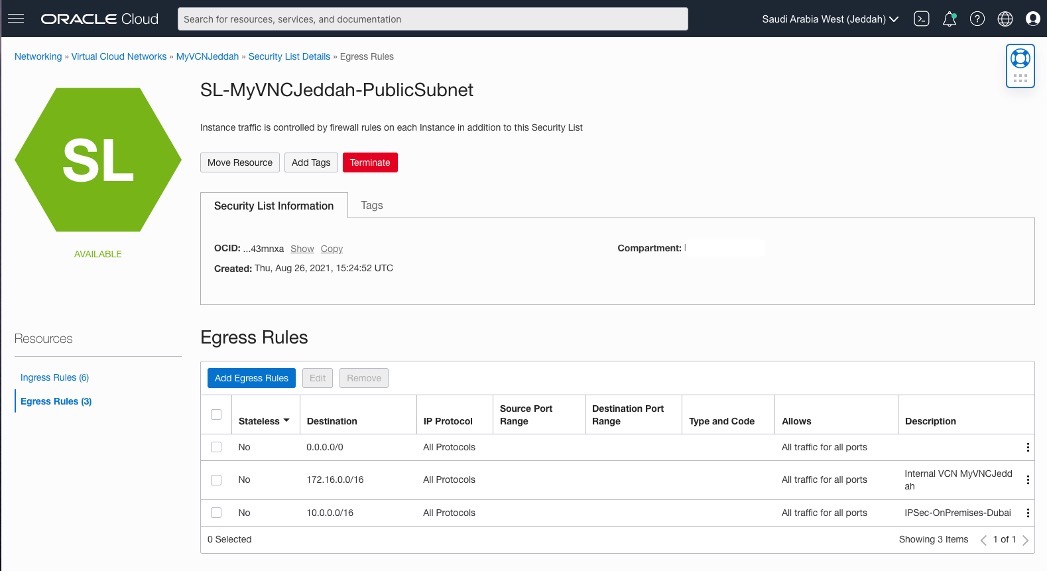
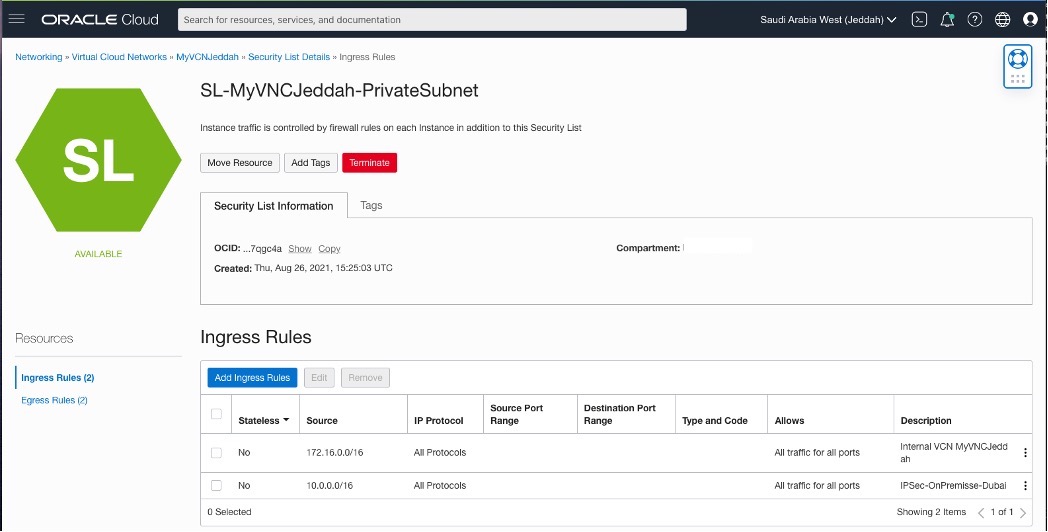
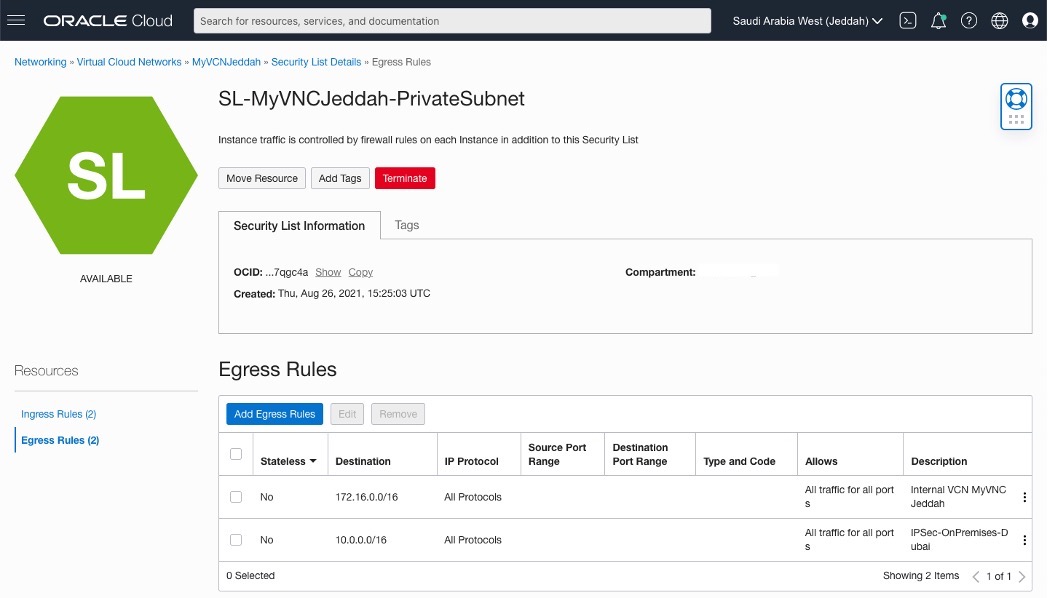
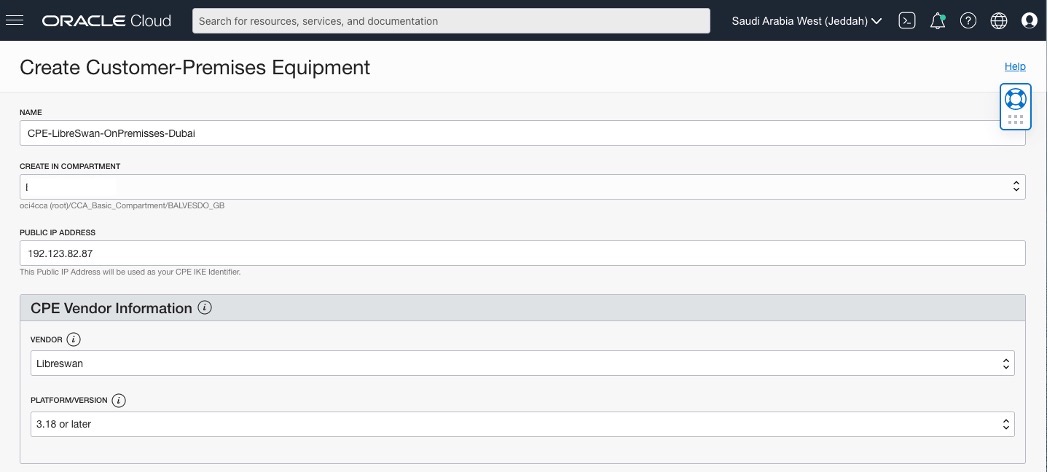
Creating a CPE(Customer-Premises Equipment) in OCI – Saudi Arabia West (Jeddah) region.
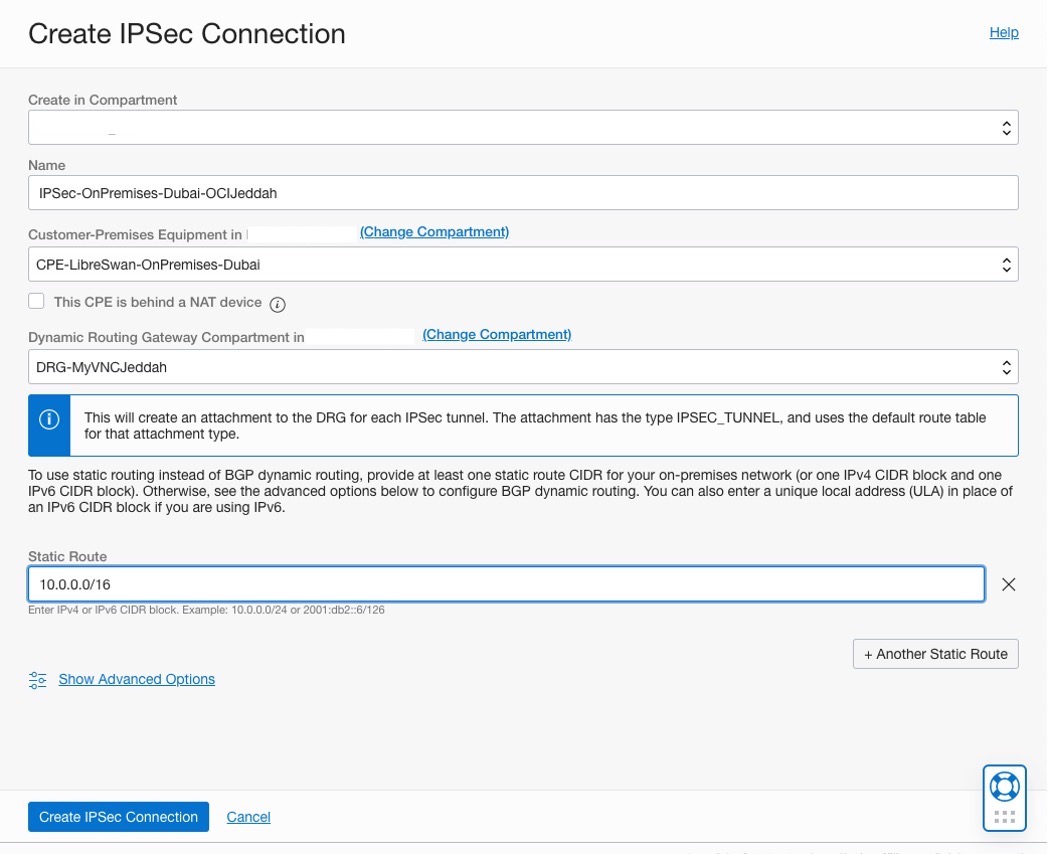
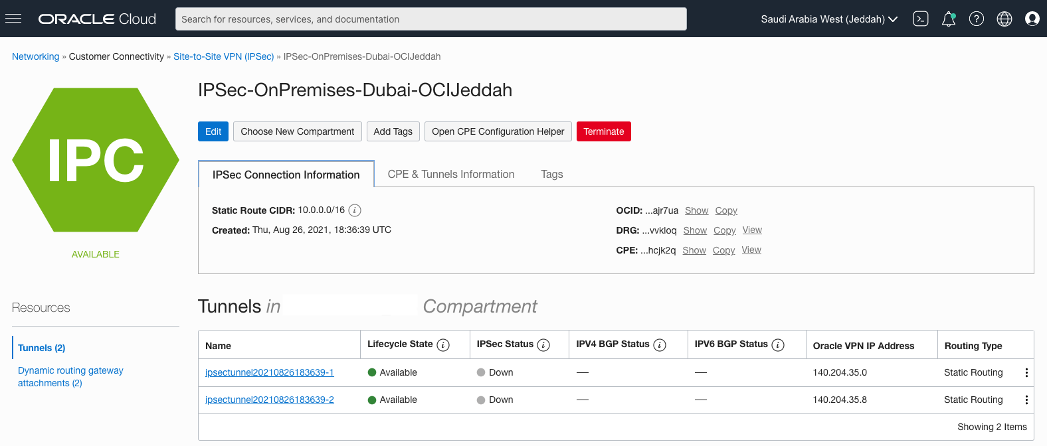
Creating an IPSec Connection in the OCI – Saudi Arabia West (Jeddah) region.
Installing LibreSwan on “LibreSwan-LDN” server – Uast Dubai – On-Premises
Connect to the server via ssh
| sudo yum -y install libreswan |
Stop and disable firewalld
| sudo systemctl stop firewalld sudo systemctl disable firewalld |
Add the lines below to the the file /etc/sysctl.conf
| net.ipv4.ip_forward = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.ens3.rp_filter = 0 net.ipv4.conf.ens4.rp_filter = 0 #IPSec net.ipv4.conf.default.rp_filter = 0 net.ipv4.conf.default.accept_redirects = 0 net.ipv4.conf.default.send_redirects = 0 net.ipv4.conf.all.rp_filter = 0 net.ipv4.conf.ip_vti0.rp_filter = 0 net.ipv4.icmp_ignore_bogus_error_responses = 0 net.ipv4.conf.default.log_martians = 0 |
Load the new content of the file /etc/sysctl.conf
| [root@libreswan-ldn ~]#sudo sysctl -p |
Remember that Dubai is Left side and Jeddah is the Righ side.
| [root@libreswan-ldn ~]# cat /etc/ipsec.conf
config setup plutodebug=all plutostderrlog=/var/log/pluto.log protostack=auto
conn oracle-dubai-jeddah authby=secret auto=start pfs=yes left=10.0.0.148 leftid=193.123.82.87 leftsubnet=10.0.0.0/16 leftnexthop=%defaultroute rightsubnet=172.16.0.0/16 right=140.204.35.0 rightid=140.204.35.0 mark=5/0xffffffff vti-interface=vti1 vti-routing=no ikev2=no # To use IKEv2, change to ikev2=insist ike=aes_cbc256-sha2_384;modp1536 phase2alg=aes_gcm256;modp1536 encapsulation=yes ikelifetime=28800s salifetime=3600s |
Edit the file /etc/ipsec.secrets to add the configuration of the tunnel
| [root@libreswan-ldn ~]# cat /etc/ipsec.secrets 140.204.35.0 193.123.82.87 : PSK “Shared Secret” |
Restart ipsec service and add/start the tunnel
| service ipsec restart service ipsec status sudo /usr/sbin/ipsec auto –start oracle-dubai-jeddah sudo /usr/sbin/ipsec auto –add oracle-dubai-jeddah sudo /usr/sbin/ipsec auto –up oracle-dubai-jeddah |
Add a route configuration
| [root@libreswan-ldn ~]#ip route add 172.16.0.0/16 nexthop dev vti1 [root@libreswan-ldn ~]# ip route show default via 10.0.0.1 dev ens3 10.0.0.0/24 dev ens3 proto kernel scope link src 10.0.0.148 169.254.0.0/16 dev ens3 proto static scope link 169.254.0.0/16 dev ens3 scope link metric 1002 172.16.0.0/16 dev vti1 |
After a few minutes is possible to see that the tunnel has been stablished.
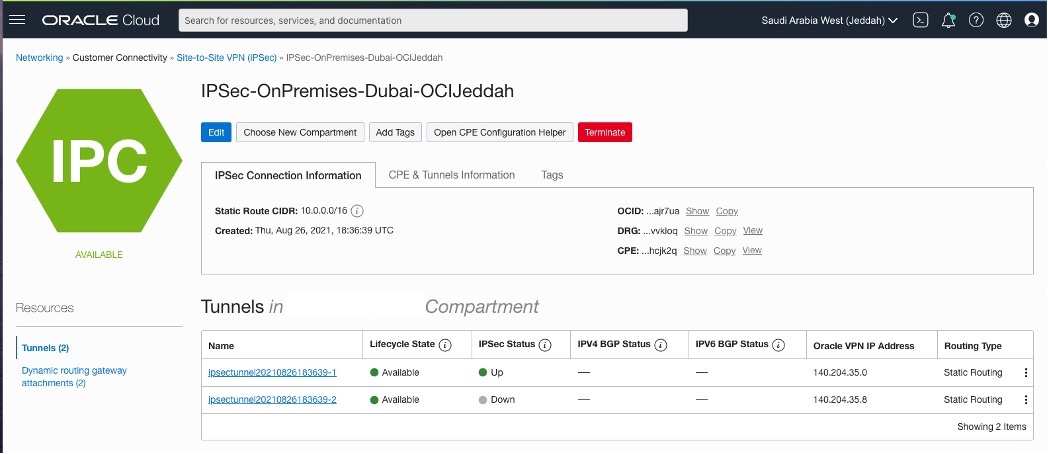
There is a conectivity between private subnets and it is possible to see that the servers can “talk” with each other.
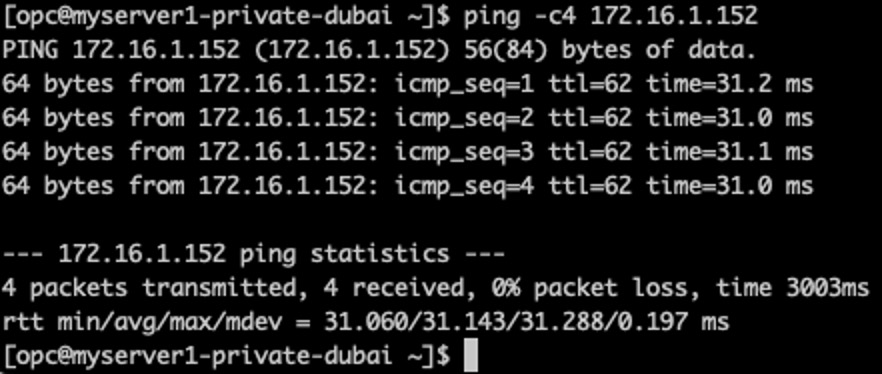
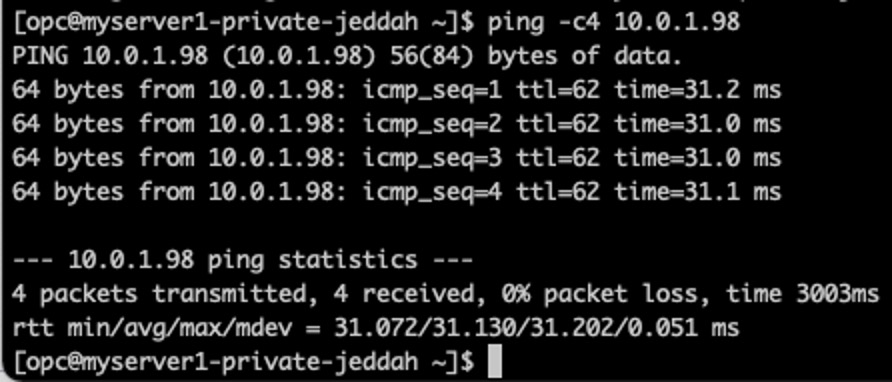
Creating a service to start the tunnel and add the route automatically on “LibreSwan-LDN” server– Uast Dubai – On-Premises
| [root@openswan-ldn ~]# cat /lib/systemd/system/myopenswan.service [Unit] Description=Start Tunnel and add routes Requires=multi-user.target After=multi-user.target
[Service] RemainAfterExit=yes User=root ExecStart=/bin/bash -c ‘/usr/bin/openswan.sh’ TimeoutStartSec=60
[Install] WantedBy=multi-user.target
[root@openswan-ldn ~]# cat /usr/bin/openswan.sh #!/bin/bash /usr/bin/systemctl start ipsec /usr/bin/sleep 10 /usr/sbin/ip route add 172.16.0.0/16 nexthop dev vti1 |
Conclusion
This post provides a step-by-step procedure for creating an encrypted site to site IPSec tunnel between an On-Premises and OCI environment. Once the configuration is done, servers from private subnets are able to communicate with each other. Additionally an automated process has been provided to create the tunnel and add the route on the LibreSwan server.