OpenID Connect (OIDC) is an open standard authentication protocol built on the OAuth 2.0 framework. It provides a secure and flexible way to authenticate and authorize users within applications and systems. You might consider OIDC discovery with Oracle Cloud Infrastructure (OCI) Kubernetes Engine (OKE) to authorize Kubernetes pods to access non-OCI resources using third-party security token services (STSes).
We’re happy to announce that OKE support for OIDC discovery is currently available in early access and will be generally available soon.
OKE OIDC Discovery
OKE has been supporting Workload Identity to enable Kubernetes pods to access OCI resources, such as a secret or a cloud storage bucket, without storing access credentials in your Kubernetes cluster. But how do you authorize Kubernetes pods on OCI to access non-OCI resources? You can soon achieve this goal with OKE OIDC discovery.
OKE OIDC discovery enables STSes running on-premises or in third-party cloud service providers (CSPs), such as Amazon Web Services (AWS) and Google Cloud Platform (GCP), to validate Kubernetes pods running on OKE clusters and authorize them to access non-OCI resources.
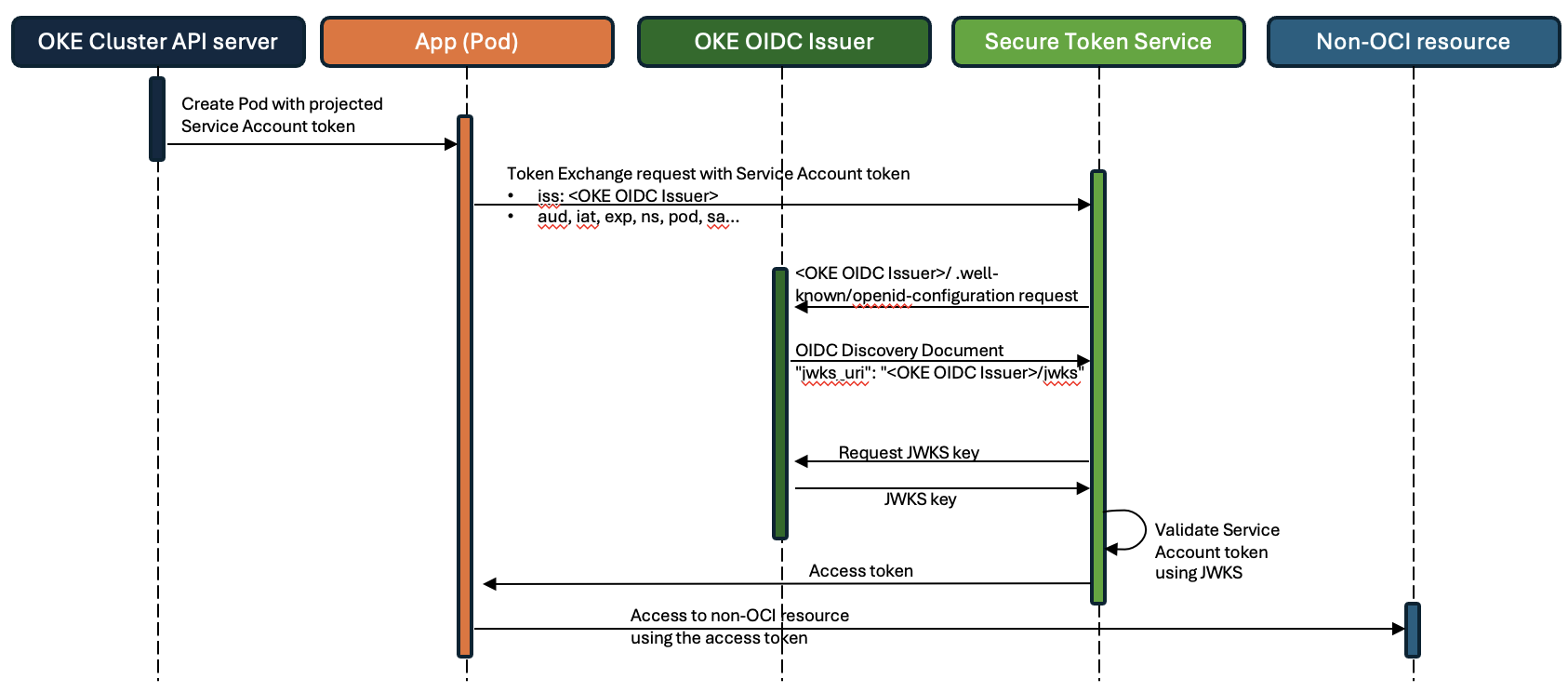
When you enable OIDC discovery for an OKE cluster, OKE exposes an OpenID Connect issuer endpoint that serves the OIDC Discovery document and the JSON Web Key Set (JWKSes). This document and public key enable third-party IDPs to validate the authenticity of pods from an OKE cluster and authorize the pods to access non-OCI resources.
The workflow moves through the following steps:
- You create pods with a Kubernetes service account token.
- Your application running on the pods requests a non-OCI resource access token to a third-party STS. The application provides the service account token to the request. The service account token contains the OKE OpenID Connect issuer URL.
- The STS gets the OIDC Discovery document and the JWKS from the OKE OpenID Connect issuer URL using the common conventional location, <issuer>/.well-known/openid-configuration.
- The STS returns a non-OCI resource access token to the application running on the pods.
Learn more
Register for the OKE OIDC discovery early access to get hands-on experience.
To learn more about OKE, see the following resources:
- Access the OKE resource center
- Get started with Oracle Cloud Infrastructure today with our Oracle Cloud Free Trial
