Recent data breaches across industries, such as the incident with Snowflake, highlight the necessity of enhancing security beyond username and password protection. One effective way to mitigate these risks and keep your environment protected is to restrict access based on IP addresses, significantly reducing the attack surface. Implementing IP-based filtering ensures that only traffic from specific IP addresses, such as those from your company’s network, your Oracle FastConnect connection, virtual private network (VPN), or a specific country, can access your system.
Oracle Fusion Cloud recommends the following native methods for IP-based filtering:
- Network access control lists (ACL)
- Web application firewall (WAF) for Fusion-based IP filtering
- Location-based access control (LBAC)
Network ACLs: Restrict access with precision and ease
One of the simplest ways to restrict access to your environment is through network ACLs. These lists deliver precise control over who can access systems by allowing only specified IP ranges in classless interdomain routing (CIDR) blocks. This self-service option is available in the Oracle Cloud Console and is activated immediately.
Each distinct environment can have its own ACL, blocking all traffic not coming from the specified CIDR blocks. If no network ACL is set up, all traffic is allowed by default, potentially exposing your systems to unauthorized access. Network ACLs operate at the network level, blocking traffic before it even reaches your environment. This method allows you to add multiple CIDR blocks or virtual cloud networks (VCNs) to the ACL, as shown in the following images.
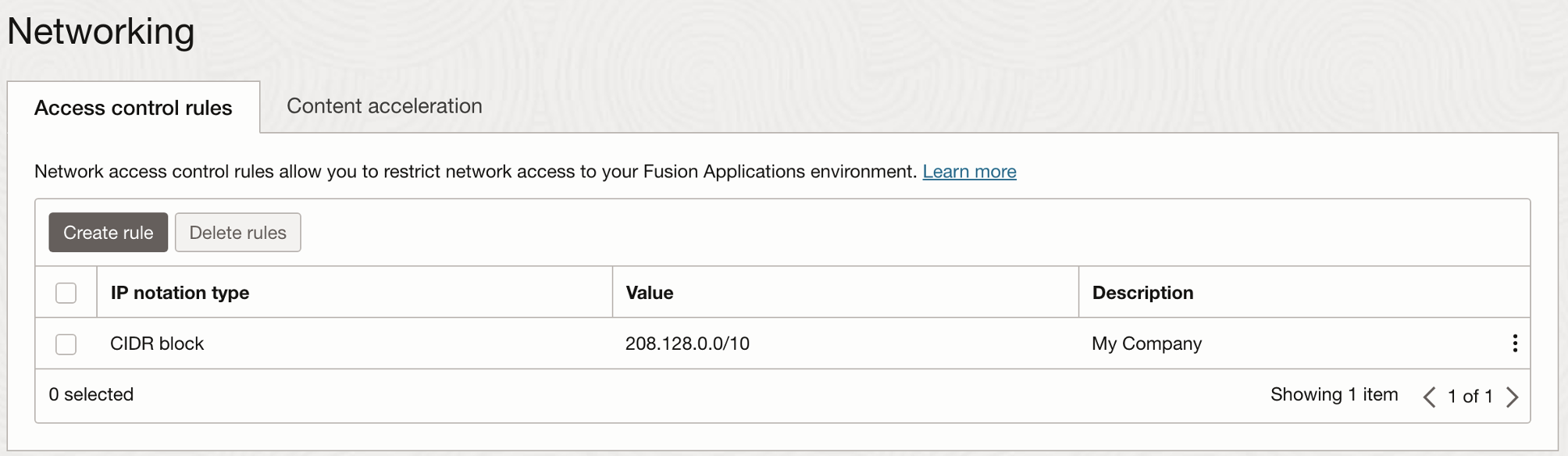
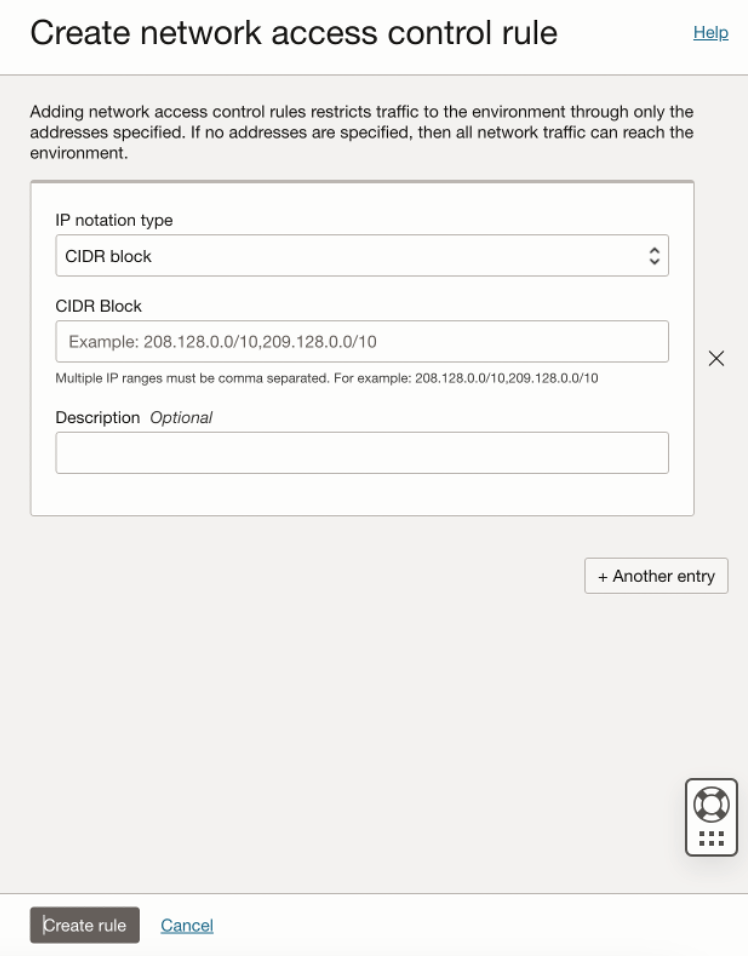
If an unauthorized attempt to access the environment from an unlisted IP is made, a 403-error screen appears, indicating forbidden access. For more details, see the network access control rule documentation.
WAF for Fusion: Enhanced IP filtering for advanced security needs
For complex security requirements, enhance your system’s defences by setting IP-based access control at the WAF layer, accessible through a service request. By default, all Fusion environments are protected by WAF for Fusion. Adjusting the WAF policy allows you to further restrict traffic, adding another layer of security. While WAF for Fusion is instrumental in controlling IP traffic, its capabilities extend to a broader spectrum of security threats, such as examples listed in the OWASP Top 10, enhancing resilience of your network against different vulnerabilities.
To implement a WAF policy-based IP filter, you must disable your network ACL.
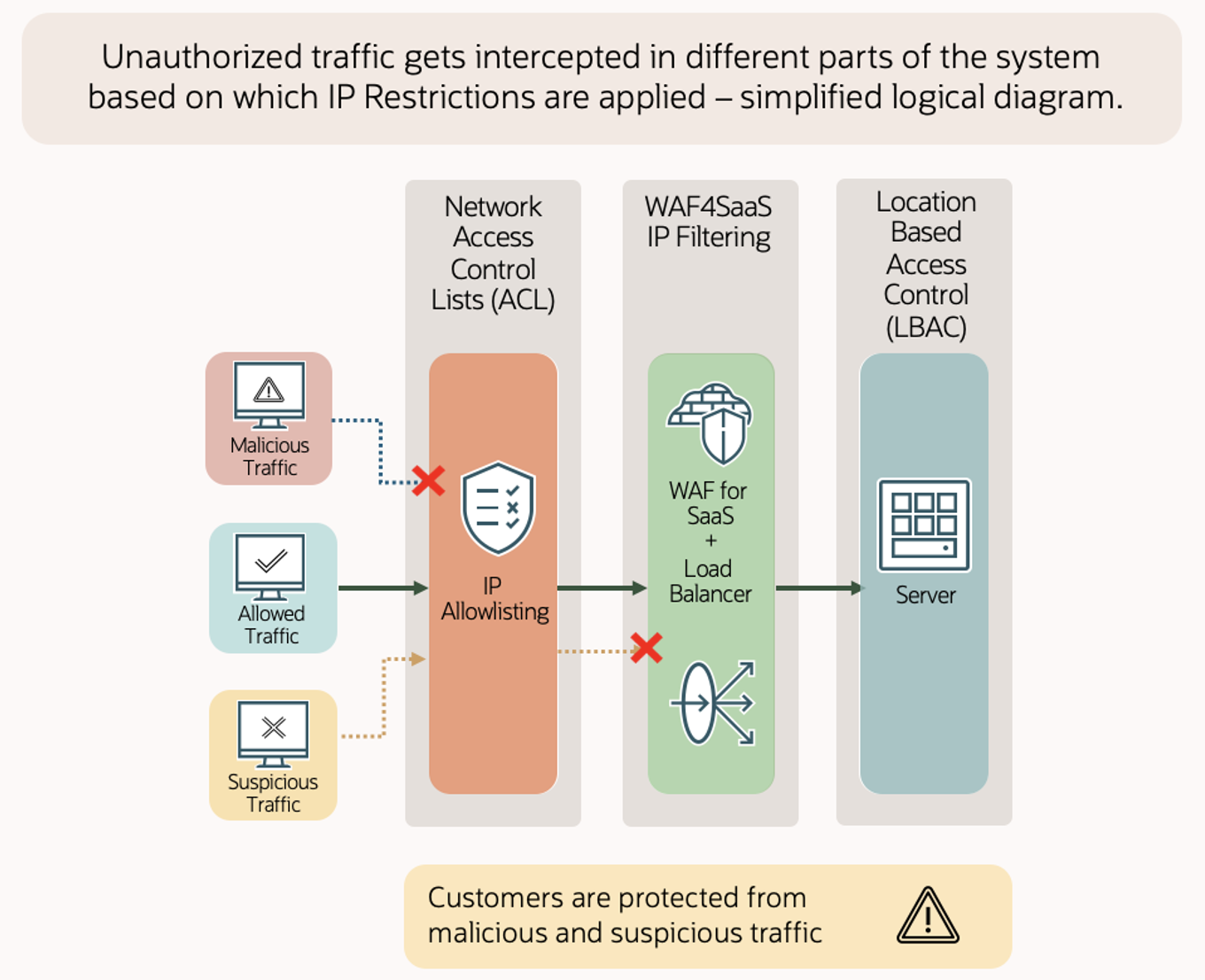
Summary
Network ACLs and WAF for Fusion are essential methods for IP filtering integral to expanding the security of your Oracle Fusion Cloud services. For a comprehensive defense, we recommend employing either network ACLs and LBAC or WAF and LBAC to ensure that your cloud environment is safeguarded against sophisticated threats.
In part 2 of our series, we explore more IP filtering methods, including WAF policy-based IP filters and LBAC, which offer enhanced security configurations to meet complex requirements, such as restricting subsets of the application to different IP ranges and geographies. These methods build on the foundation, set by network ACLs, to provide even stronger protection against unauthorized access.


