In part 1 of this series, we discussed the critical role of network access control lists (ACLs) and web application firewall (WAF) for Fusion in securing your Oracle Fusion Cloud environment. In this second part, we delve into more advanced IP-based filtering methods. In this second part, we explore the capabilities of WAF for Fusion and location-based access control (LBAC), which provide more nuanced and complex security configurations to address diverse security needs.
WAF for Fusion: Enhanced IP filtering for advanced security needs
Just like network ACLs, WAF for Fusion and software as a service (SaaS) allows traffic from specific classless interdomain routing (CIDR) blocks. However, WAF can also provide the capability to block traffic from specific CIDR blocks. For example, if you need to block traffic from 208.128.0.0/10 and 209.128.0.0/10, your service request should contain the following string:
Block CIDR <208.128.0.0/10, 11.0.0.1/24>
WAF for Fusion and SaaS also extends its functionality with the option to allow or restrict traffic based on countries identified by their ISO 3166 code. For example, to only allow traffic from Japan, your service request should contain the following tag:
Allow Countries <JP>
You can also block access from certain countries. For example, to block traffic from Australia and New Zealand, your service request should contain the following tag:
Block Countries <AU, NZ>
You can combine these configurations to create more specific access rules. For example, to restrict CIDR blocks 208.128.0.0/10 and 209.128.0.0/10 while simultaneously allowing access from the USA, Canada, and Mexico, add the following strings to your service request:
Block CIDR <208.128.0.0/10, 209.128.0.0/10>
Allow Countries <US, CA, MX>
WAF for Fusion and SaaS also supports differentiated restrictions for specific parts of Oracle Fusion Cloud. For example, while the Oracle Cloud Fusion Cloud might be accessible from designated countries or CIDR blocks, you can make specific parts, like the Oracle Recruitment Cloud portal, accessible to more countries.
Allow CIDR <208.128.0.0/10, 209.128.0.0/10>
Qualified Target <Oracle Recruitment Cloud Portal> Allow Countries <US, CA, MX>
If you try to access the environment from a blocked IP or country, a screen stating, “…Blocked By WAF GEO IP Filters WAF4SaaS…” appears, instructing users to contact Oracle Support. This immediate notification helps ensure that unauthorized users are promptly informed of their restricted access, enhancing the security measures.
WAF IP filtering serves as a powerful tool within the SaaS load balancer, managing system access by blocking traffic before it reaches the application. To implement a WAF policy-based IP Filter, you must disable your network ACL. The implementation of this method requires a lead time of five business days after the service request is created. Plan accordingly to accommodate this setup phase without disrupting your operations. For more information, see the My Oracle Support articles, How To Request for WAF for SaaS IP Based Access Control? (Doc ID 2969290.1) and How to Submit a Technical Service Request for WAF for SaaS? (Doc ID 2969373.1).
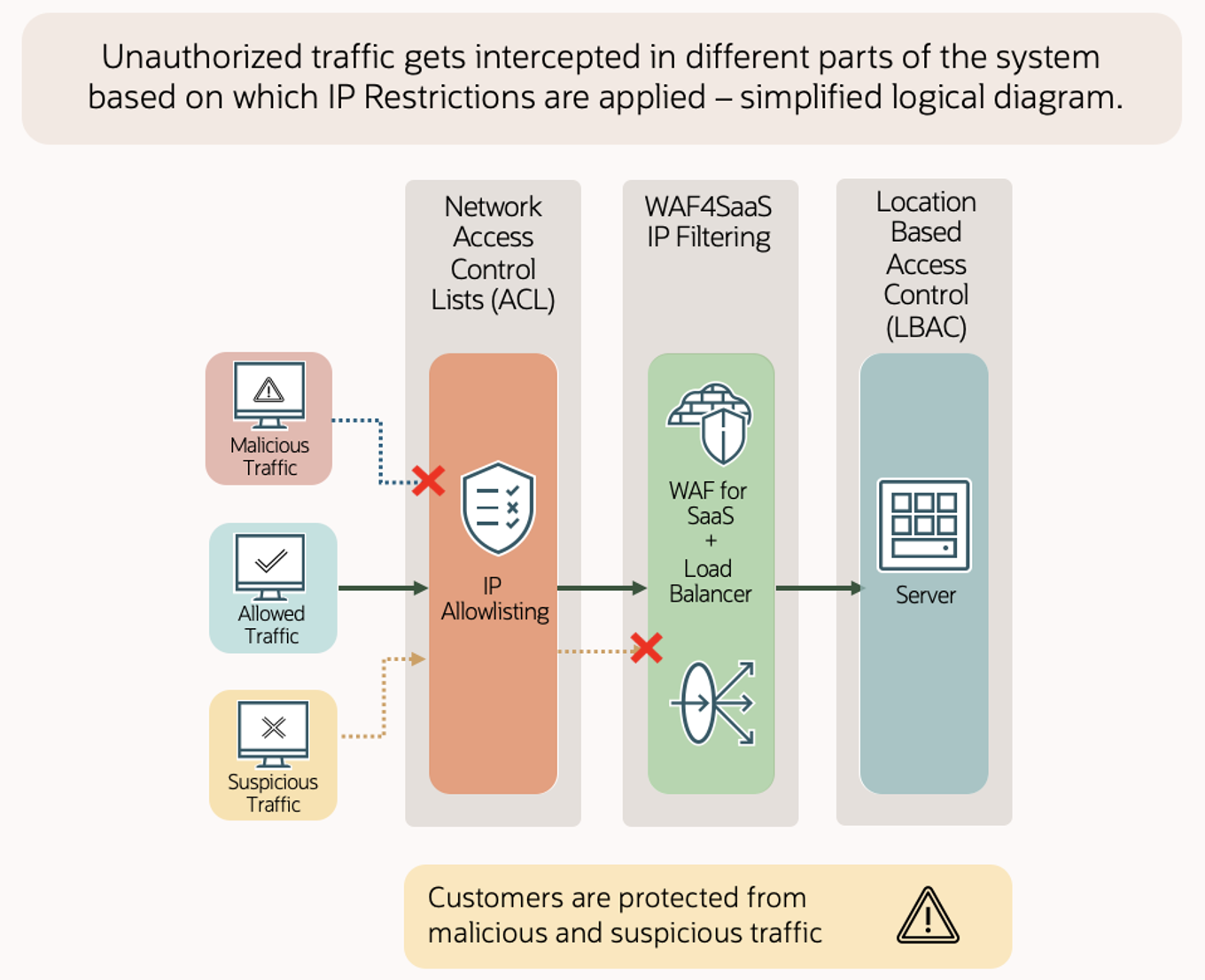
Location-based access control (LBAC): Tailoring Access by Role and Region
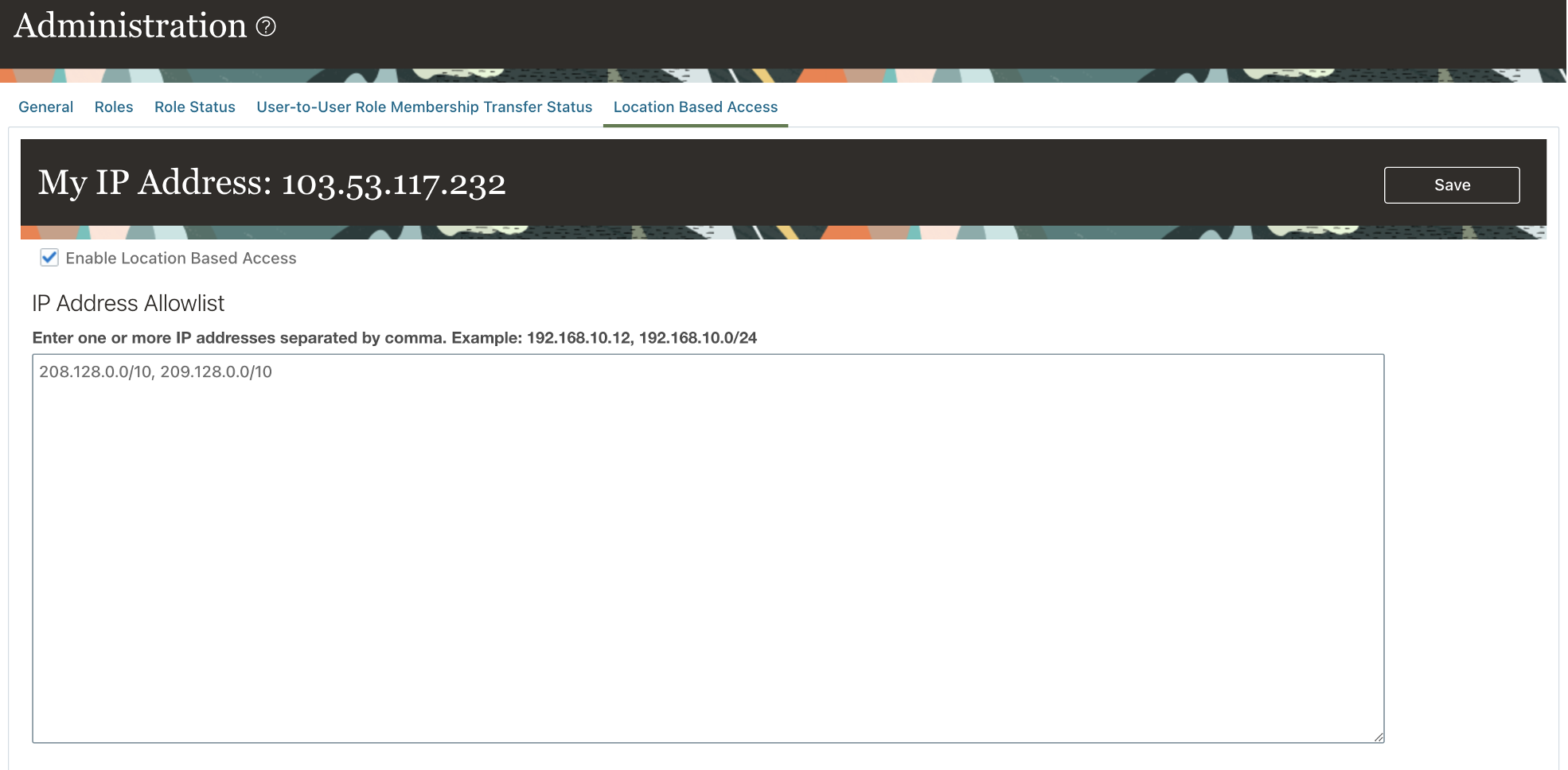
If your security needs to filter both IP address and user role, LBAC is the best tool. LBAC is the only IP-based restriction option that integrates user roles into its filtering criteria, setting it apart from the previous methods of network ACLs and WAF-based filtering. With LBAC, you can set an IP address allowlist, containing both CIDR blocks and individual IPs. Access from any IP on the allowlist faces no functional restrictions for seamless operations.
Implement LBAC in every environment where feasible to enhance security. You can effectively combined this method with either network ACLs or the WAF for Fusion and SaaS, which is particularly useful in environments where access must be finely tuned, based on both location and user permissions.
You can enable this method with self service in the security console. To avoid accidental lockout, ensure that you include the IP of the host you currently use to access the environment.
If you access the system from an IP not on the list, you can still log in but are limited to accessing only those parts of the system where the required role is marked as “available from all IP addresses.” This feature is useful for allowing employees to perform certain tasks from home computers or mobile phones without predefined IPs. For example, you can perform tasks like submitting expenses remotely, while more sensitive tasks like performance reviews can remain restricted to known IPs within your company’s network.
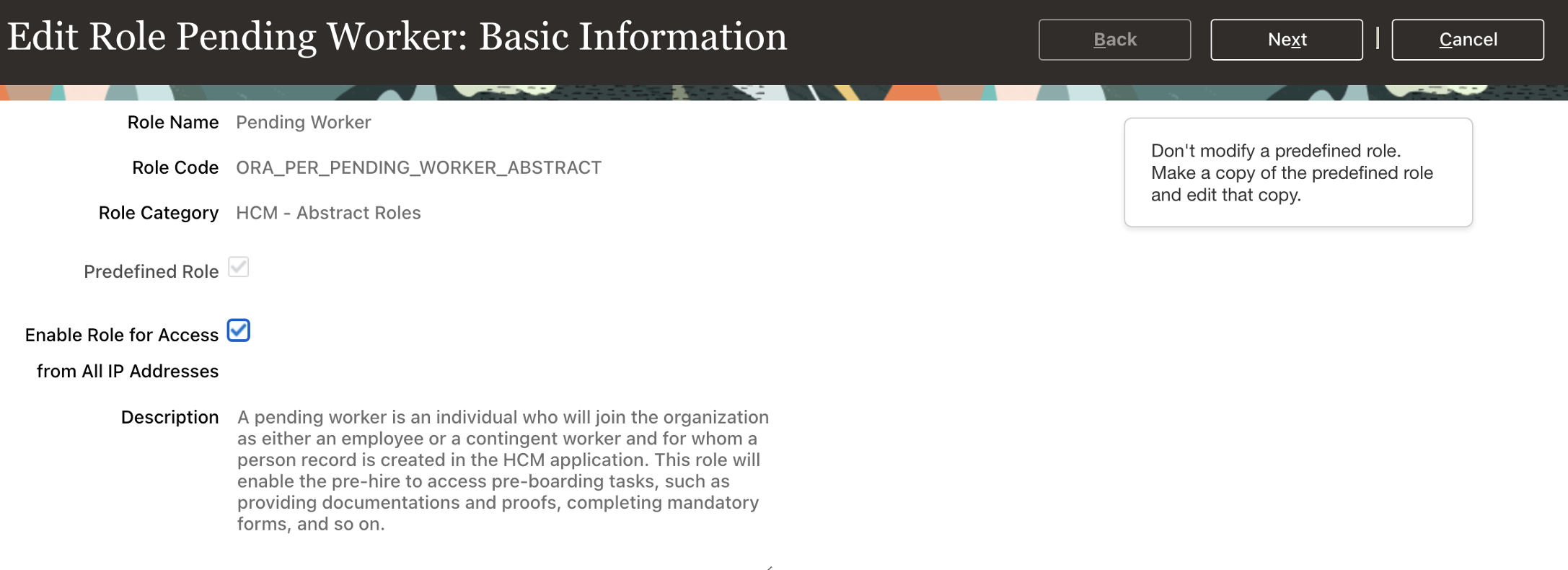
For example, as pending workers, newly hired employees can fill out necessary documents before officially joining the company if the role “ORA_PER_PENDING_WORKER_ABSTRACT” is marked as public. This role allows them to complete onboarding tasks without accessing a company IP. Roles are made available from all IP addresses through Security in the Oracle Cloud Console.
LBAC applies to access through both browser and APIs, helping ensure a comprehensive security model that’s consistent across all access points.
For more information, refer to the resources, Overview of Location-Based Access and Securing Oracle Fusion Applications REST APIs with Location Based Access Control (LBAC).
Conclusion
This two-part series on IP-based filtering culminates by linking the foundational network ACLs, discussed in part 1, with the advanced functionalities of WAF and LBAC explored in this part 2. Together, these methods enhance Oracle Fusion Cloud’s security, offering robust protection by controlling access based on IP addresses and geographical locations. For a comprehensive defense, we recommend employing either network ACLs and LBAC or WAF and LBAC to helps ensure that your cloud environment is safeguarded against sophisticated threats.
If your system’s access isn’t currently restricted to essential IPs, we recommend prioritizing the setup of these advanced options to strengthen your overall security posture.
Dive deeper by revisiting part 1 for a thorough review of network ACLs and check out all the linked resources in our blog to fully arm your cloud security controls. For more information on the concepts in these posts, see the following resources:


