Effective identity security requires holistic visibility into access profile
Enterprises grapple with managing data and policy silos that contain profile and access information about identities. These challenges are further amplified by the distributed nature of IT infrastructure, spanning on-premises environments, sensitive demilitarized zone (DMZ) setups, software-as-a-service (SaaS) applications, multicloud environments, and internet of things (IoT) ecosystems. As access privileges accumulate, the risk of misuse of user accounts increases.
Business owners, managers, and auditors face the following difficulties:
- Business owners: They lack in-depth and consolidated visibility into who has access to specific resource and their access patterns. Ensuring the right level of access becomes a challenge.
- Managers: Identifying access anomalies or reviewing unauthorized accesses by team members is a daunting task.
- Auditors: Demonstrating adherence to security standards and regulatory compliance without detailed access reports poses difficulties.
- Employees: They often lack information about their own access privileges or how to remove unnecessary permissions.
Oracle Access Governance
Oracle Access Governance is a modern identity governance and administration (IGA) solution, offering a specialized set of features tailored to the evolving governance needs of businesses. It seamlessly integrates across diverse applications, systems, and platforms, continuously discovering identities and their assigned accesses. The system consolidates this information into access profiles for each identity. It also provides roles, attributes, policy-based access control, and codeless business workflows to manage access controls effectively, helping ensure appropriate access based on roles and responsibilities.
Next-gen access dashboard
Oracle Access Governance offers a next-gen access dashboard, a powerful and crucial feature designed to empower organizations in maintaining control over identity access and safeguarding sensitive data and systems. The dashboard offers real-time visibility into access profiles of identities across the enterprise. The analytics-driven intelligence further enables business owners, and managers to detect and prevent unauthorized or suspicious activities. It helps auditors to demonstrate adherence to security standards and demonstrate compliance effectively.
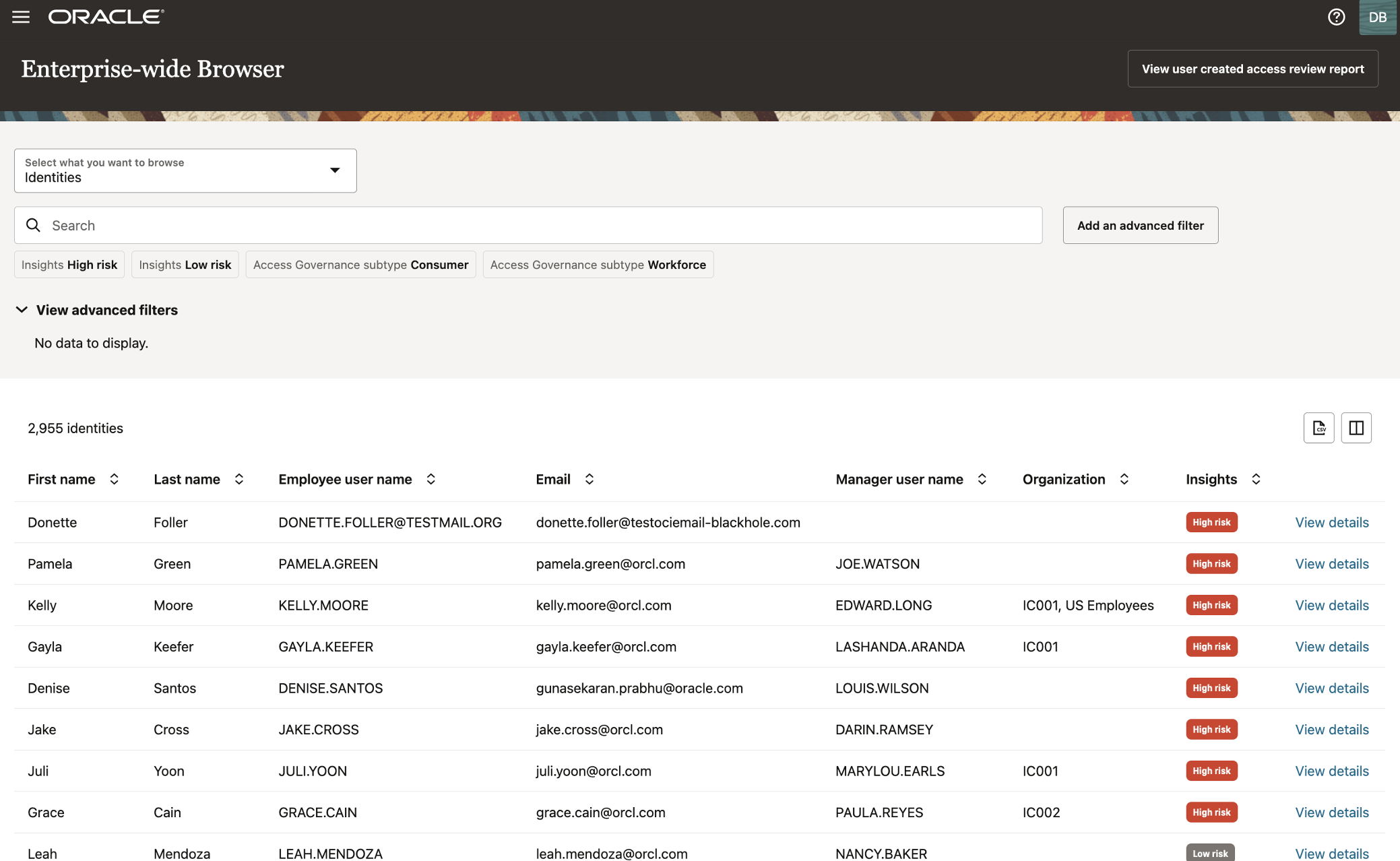
This functionality has the following key aspects:
- Comprehensive and analytics-driven dashboard:
- The dashboard offers an analytics-driven view of access details, connecting identity collections, roles, policies, and applications.
- It empowers business owners, managers, and end users to manage their access effectively by providing a holistic understanding of access patterns.
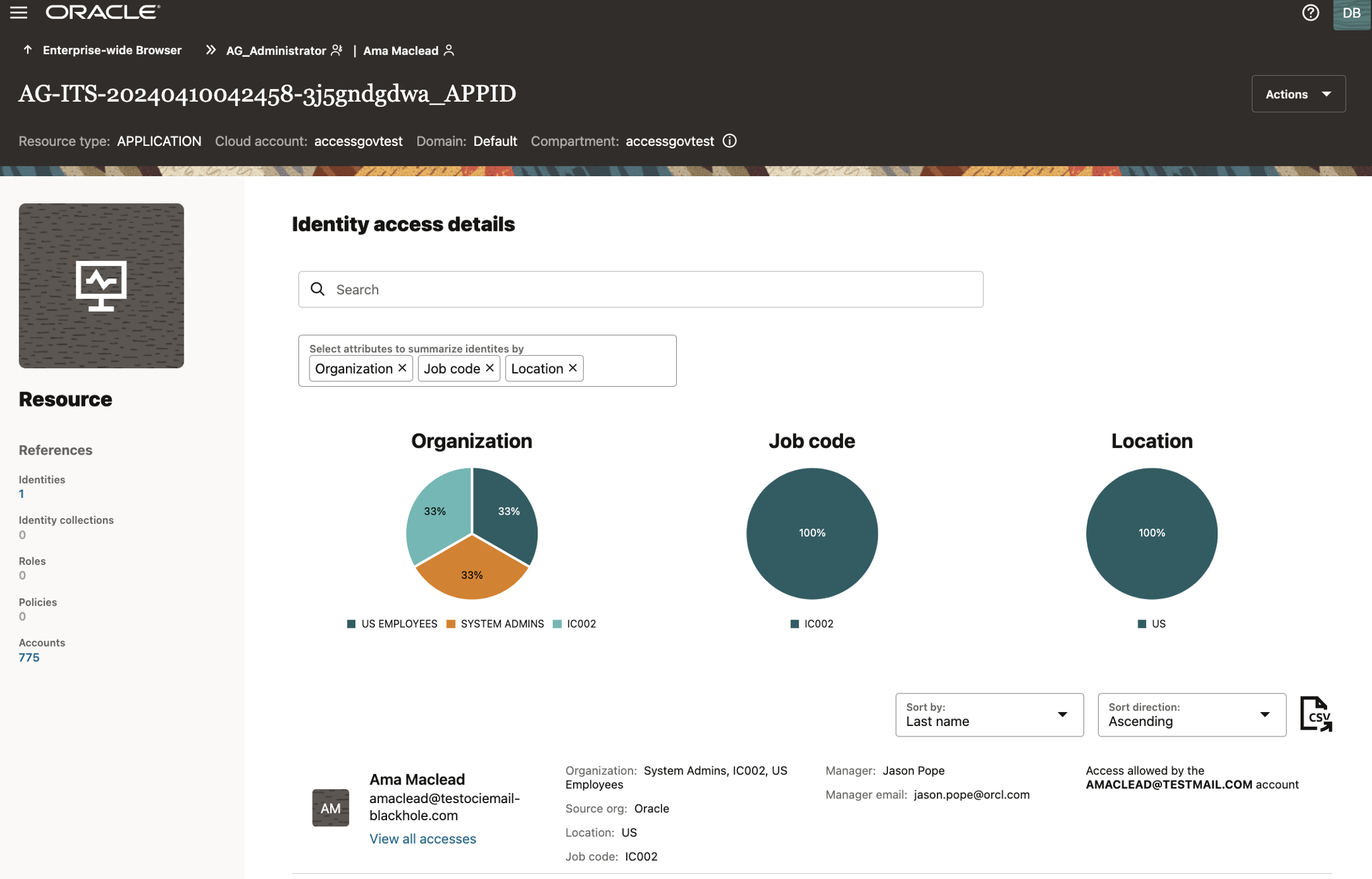
- The access is presented across multiple anchoring points:
- Identities: Understand who has access to what.
- Identity collections: Group identities logically.
- Organizations: View access within specific organizational units.
- Roles: Explore role-based access.
- Policies: Understand access policies.
- Permissions: View details of specific permissions.
- Applications and resources: Identify which applications and resources are accessed.
- Access dashboard for business owners:
- It empowers business owners by offering them deep visibility and control over access. They can anchor their decisions in data-driven insights.
- The dashboard streamlines access governance and strengthens the compliance efforts.
- Access dashboard for managers: Team Managers gain a proxy view to view individual team members’ access. It enables them to identify who has access to critical resources, and spot anomalous or unauthorized access quickly.
- Access dashboard for workforce users: Oracle Access Governance offers a user-centric approach. Employees or workforce users can understand their own access and collaborate securely, and easily find relevant applications and resources. Workforce users benefit from grouping features, such as the following examples:
- Permissions: Understand their own permissions.
- Resources: See which resources and applications they can access.
- Roles: Know their assigned roles.
- Cloud resources: Explore cloud-based resources.
- Identity collections: Understand group memberships.
- Policies: Be aware of access policies.

- On-the-go access reviews: Business owners can perform access reviews directly from the dashboard. This feature ensures timely reviews, reducing the risk of unauthorized access.
- Extensive access reports for auditors: The dashboard provides a rich set of access reports ready to go. These reports cater to regulatory requirements and strengthen overall security posture.
Conclusion
The game-changing next-gen dashboard empowers stakeholders to manage access effectively through a holistic understanding of access patterns. Oracle Access Governance provides purpose-built features that bolster identity security and help safeguard sensitive data within organizations. Overall, it empowers organizations to modernize legacy identity management solutions, offering an intelligent IGA solution enriched with insights and predictive analytics.
For more information, see the following resources:
- What’s new for Oracle Access Governance
- Oracle Access Governance Product Tour
- Oracle Access Governance Datasheet
- Blog Post: Oracle Access Governance introduces next-gen access dashboard and more integrations
- Blog Post: Oracle Access Governance optimizes identity orchestration and enables unlimited integrations with generic connectors
- Blog Post: Oracle Access Governance adds identity lifecycle management and expanded targets
- Oracle Access Governance Documentation
- Oracle Access Governance Tutorials
- Oracle Access Governance Hands-on LiveLabs
- Limited-time free self-paced course: Introduction to Oracle Access Governance

