The Oracle Microsoft partnership is a cloud interoperability alliance that enables customers to connect their Oracle Cloud Infrastructure and Microsoft Azure resources through a dedicated private connection. They can use single sign-on credentials in the Azure Active Directory (AD) to access Oracle and Microsoft resources. They also receive collaborative technical support from both Oracle and Microsoft. This partnership enables enterprises with many on-premises, mission-critical applications that depend on both Oracle and Microsoft technologies to move to the cloud without compromising on performance or security. Only Oracle and Microsoft offer a connected cloud technical alliance for their mutual cloud services. This connection provides the following benefits:
- Swift migration of on-premises applications
- A broader range of tools
- Both services integrated as a single unified enterprise cloud solution
This post discusses how an enterprise can securely connect an application running on Azure to Oracle Autonomous Database running on Oracle Cloud Infrastructure with low latency and guaranteed network throughput.
Solution Summary
This solution uses Oracle Autonomous Database as a fully managed, preconfigured database environment with two workload types available: Autonomous Transaction Processing and Autonomous Data Warehouse. We used a social media application that runs on an Azure virtual machine (VM) and connects privately to the Autonomous Transaction Processing database running on Oracle Cloud Infrastructure
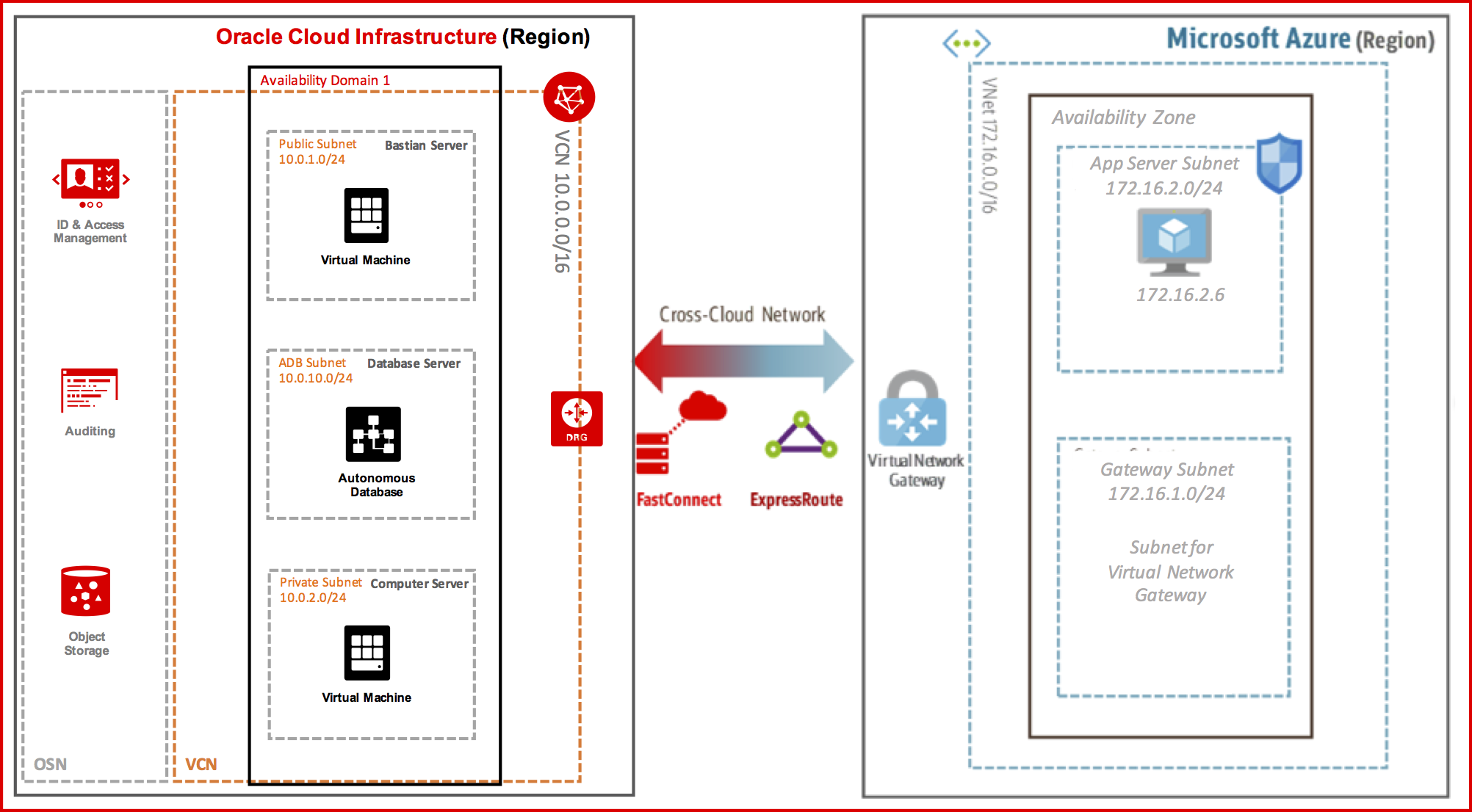
We configured the cloud network and the required network resources on both Oracle Cloud Infrastructure and Azure. The virtual cloud network (VCN) was configured with a private CIDR and subnets on Oracle Cloud, and an Azure Virtual Network (VNet) was configured with a private CIDR and subnets on Azure.
We connected a FastConnect circuit to the dynamic routing gateway (DRG) of the VCN on Oracle Cloud. Similarly, we configured an ExpressRoute circuit on Azure, connecting to the VNet gateway on Azure. The connection between the Azure VNet and the Oracle Cloud VCN uses Border Gateway Protocol (BGP) dynamic routing.
The following diagram illustrates the architecture of the solution
Before you connect to Autonomous Database from the application tier that runs on Azure using a private IP address endpoint, perform the following tasks:
- Create an Oracle Cloud Infrastructure VCN or reuse an existing VCN to configure the connection between Oracle Cloud and Azure.
- Create an Azure VNet or reuse an existing VNet to configure the connection between Oracle Cloud and Azure.
- Ensure that the Azure VNet CIDR block doesn’t overlap with Oracle Cloud VCN CIDR block.
- Identify the /30 subnet private IP address range that is used for BGP, which is required to configure the interconnect configuration./li>
- The IP address range used for BGP shouldn’t overlap with the Oracle Cloud VCN and Azure VNet CIDR block.
- Configure the Oracle Cloud-Azure interconnection with the steps in this blog post.
Follow these steps to connect applications running on Azure to Autonomous Database running on Oracle Cloud Infrastructure.
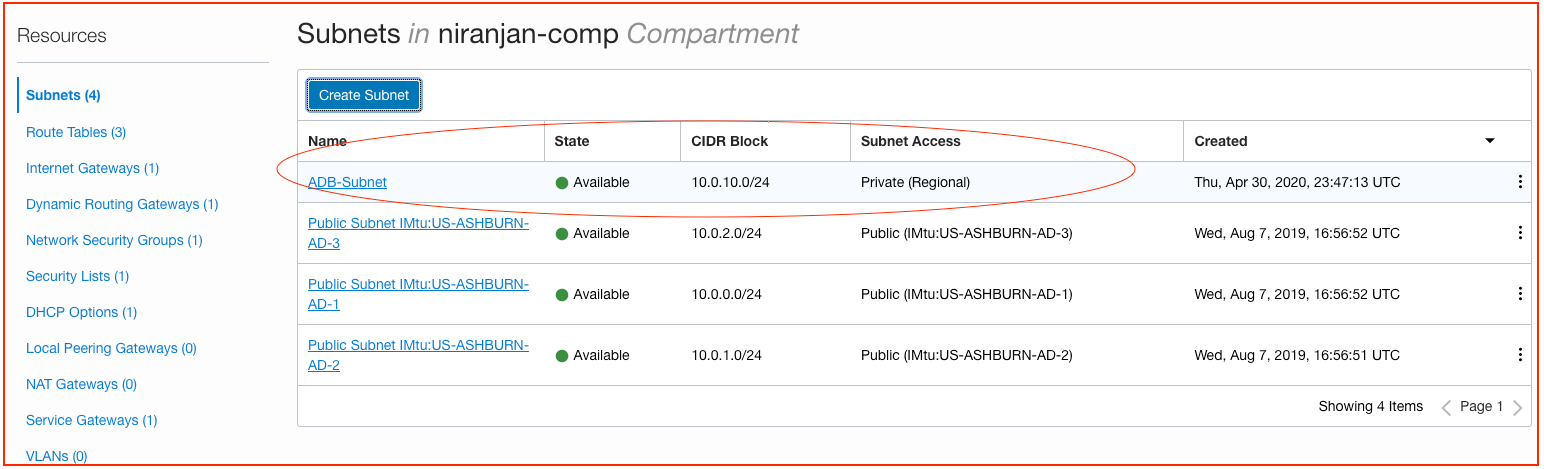
Step 1: Create a Separate Subnet for Autonomous Database
As a best practice, create a separate subnet dedicated for Autonomous Database on the VCN. Use the smaller size of the CIDR for the new subnet from the CIDR block. Choose the private subnet for Autonomous Database private endpoint.
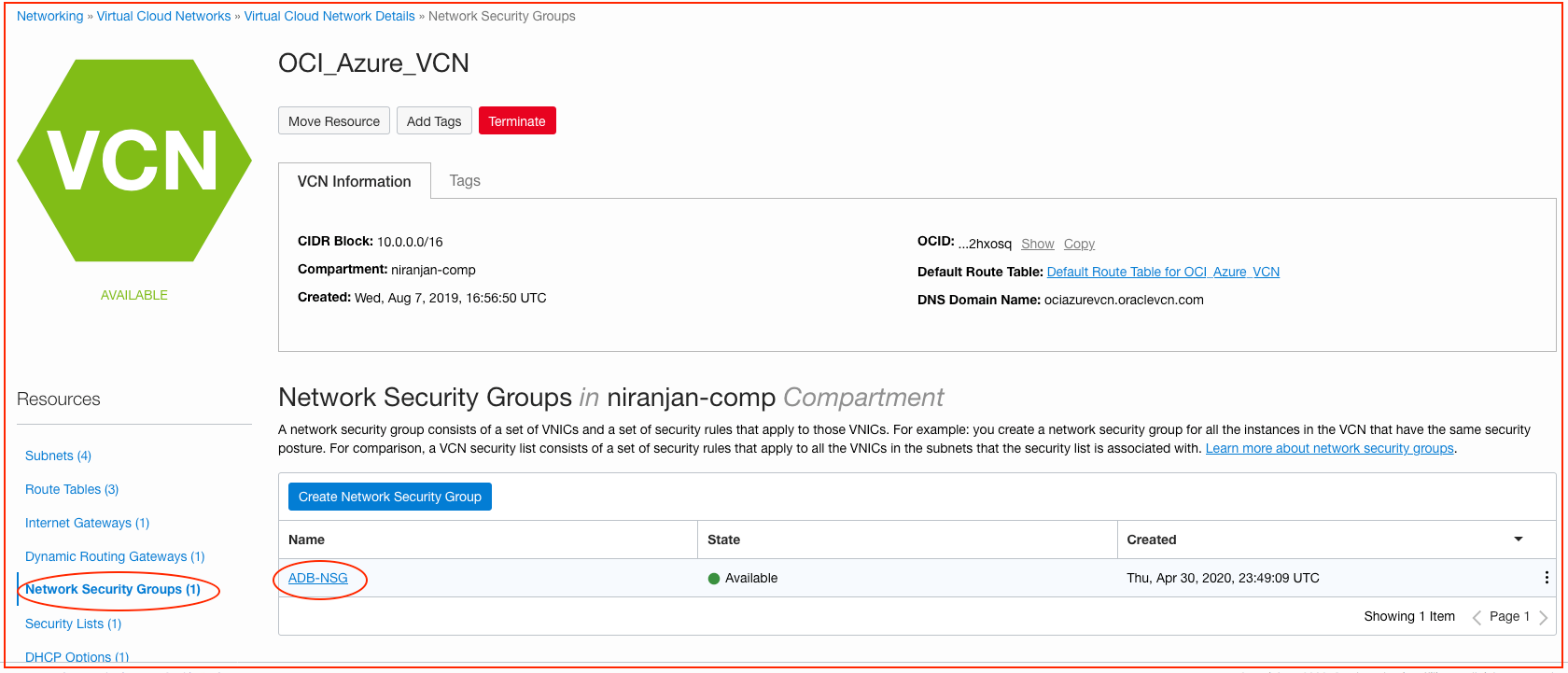
Step 2: Create a Network Security Group (NSG)
A network security group consists of a set of virtual network interface cards (VNICs) and a set of security rules that apply to those VNICs. For example, you create a network security group for all the instances in the VCN that have the same security posture. For comparison, a VCN security list consists of a set of security rules that apply to all the VNICs in the subnets that the security list is associated with. Learn more about network security groups.
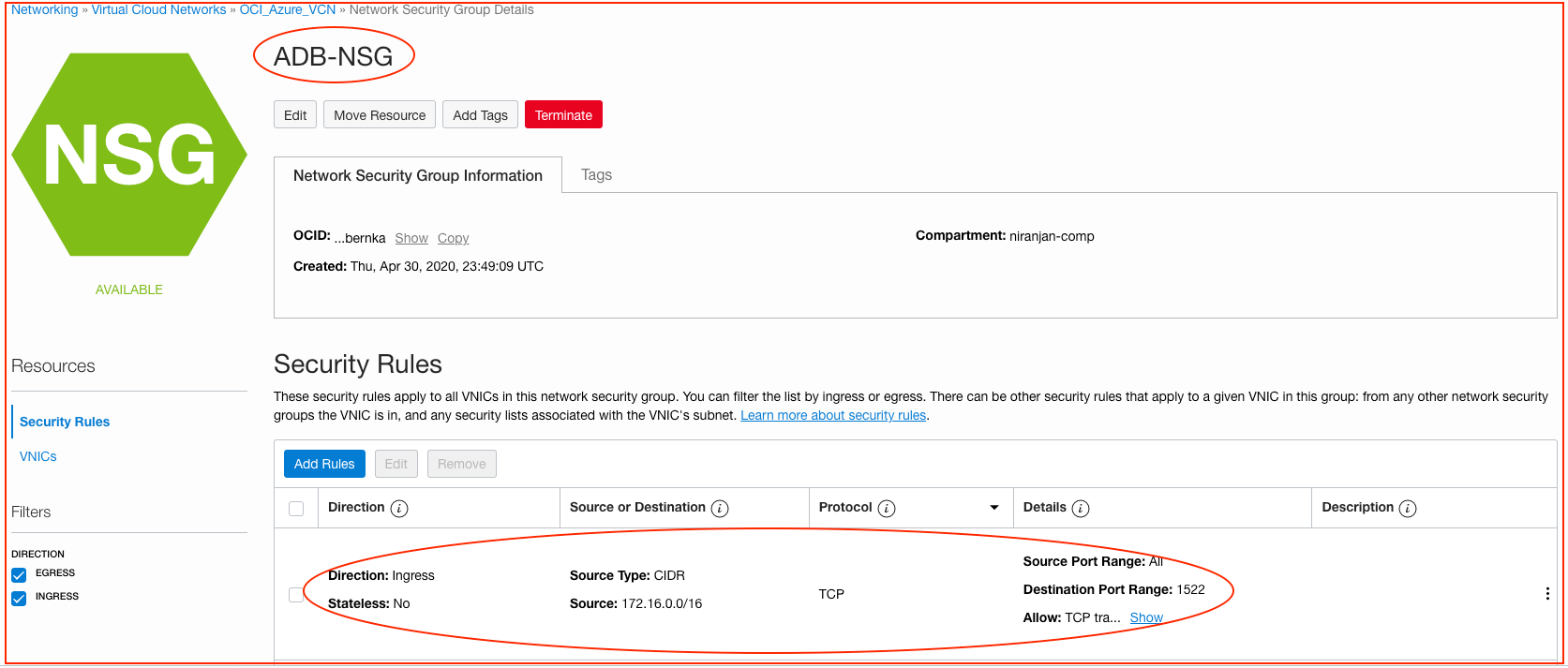
A network security group is required to control the network traffic from the Azure application server or any other application that runs natively on Oracle Cloud Infrastructure and connects to an autonomous database. In this example, we create a network security group and allow the Azure subnet to connect to the autonomous database.
Step 3: Create an Autonomous Database
Create an autonomous database by using the Oracle Cloud Console. Provide the VCN, subnet, and network security groups that you created in previous steps. You can set values for the optional parameters and customizable parameters. In this example, I provided all the parameters required to attach the autonomous database to the VCN.
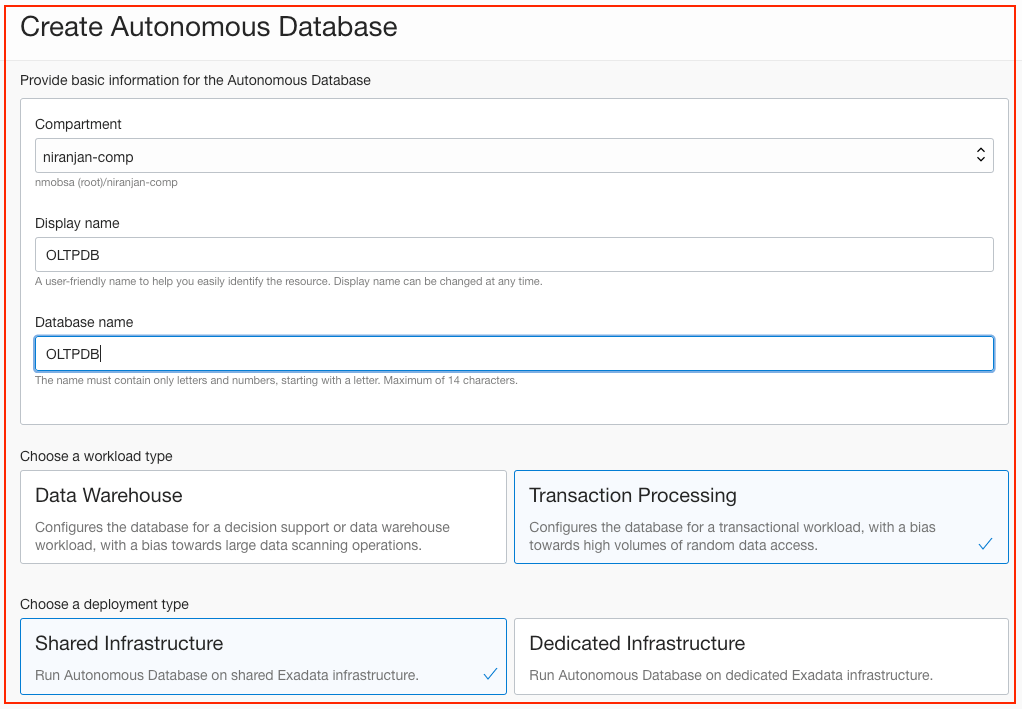
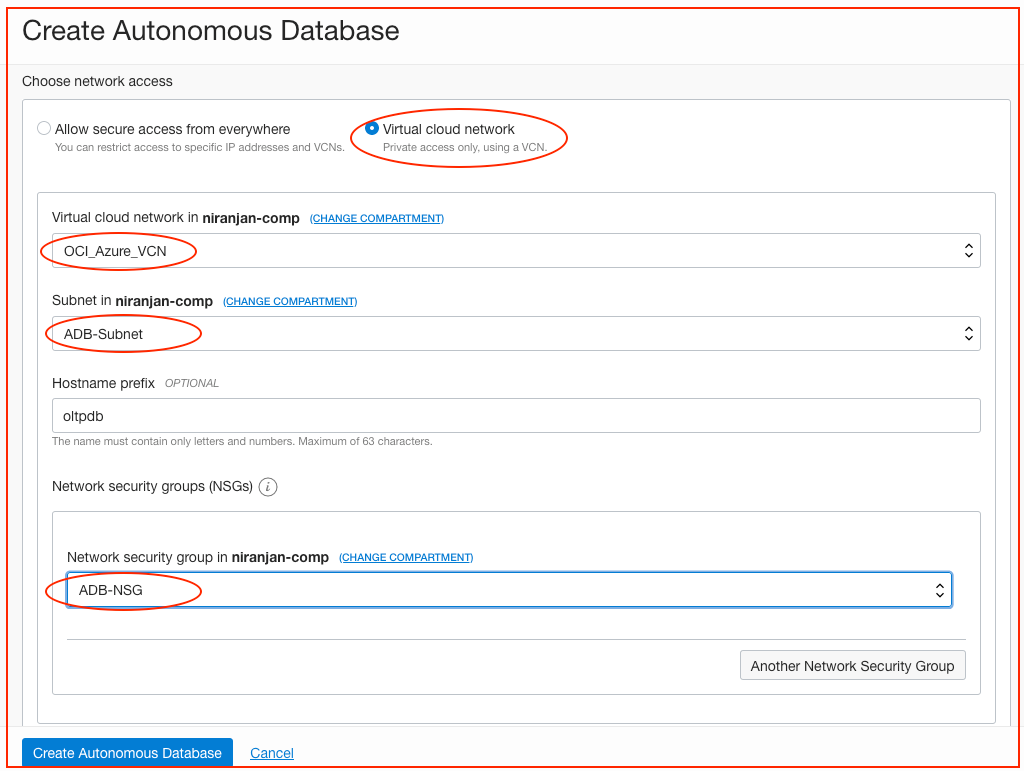
Step 4: Download the Database Connection Wallet
Download the database connection credentials wallet file from the Oracle Cloud Console Autonomous Database details page (by clicking DB Connection). After you extract the database connection wallet file, find the database connect string in the tnsnames.ora file. When connecting, you can use the private IP address or the private FQDN of the autonomous database for the application configuration.
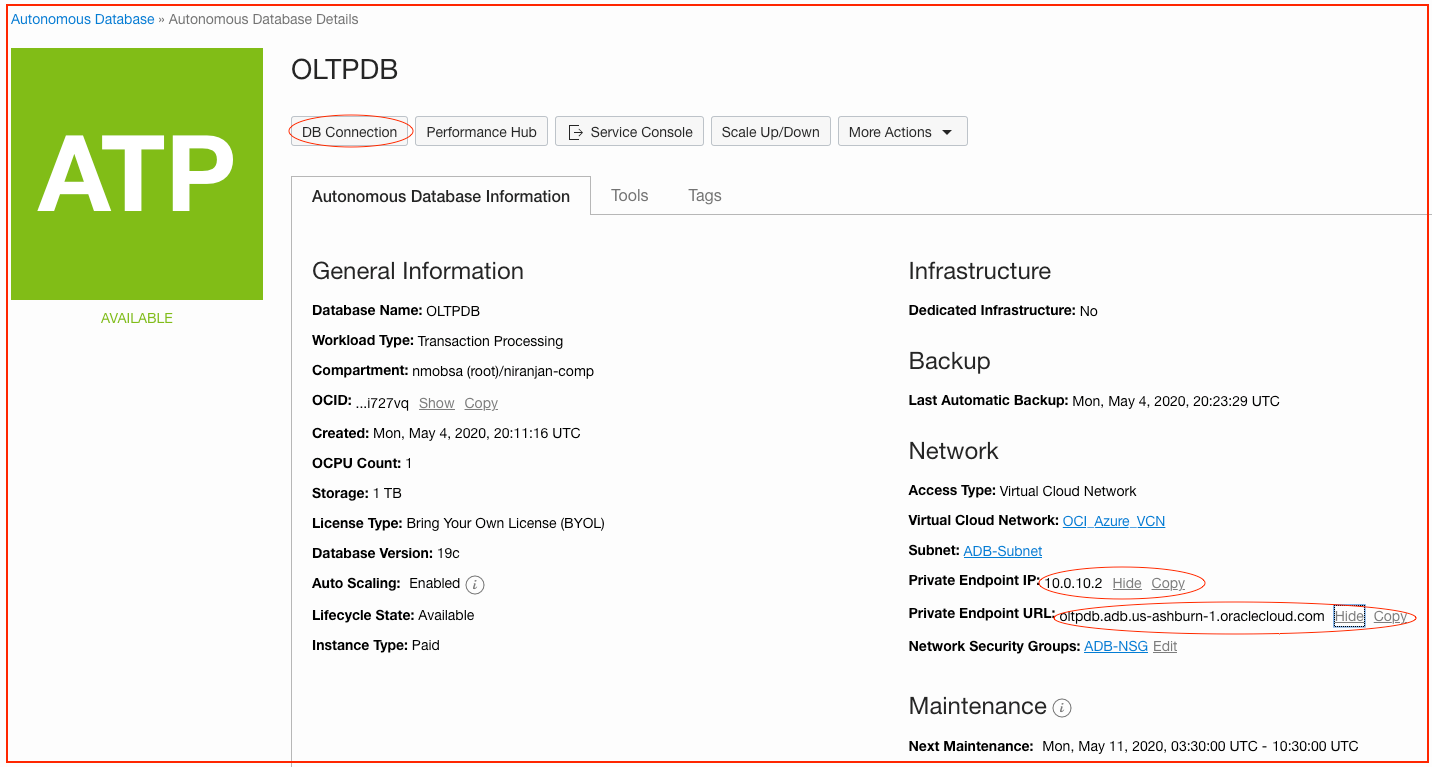
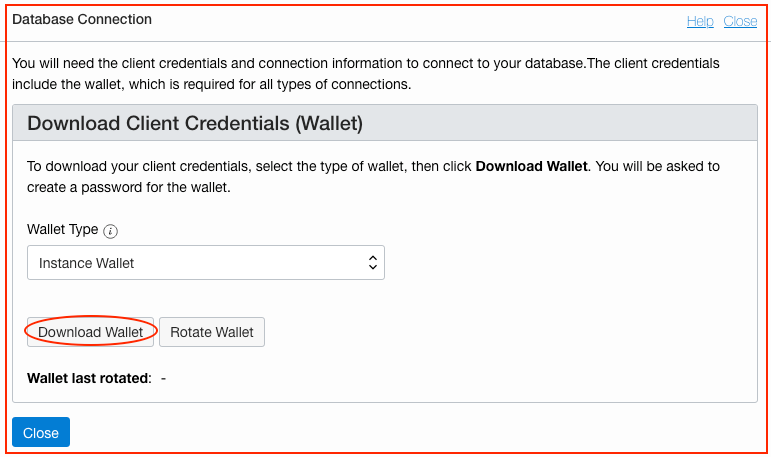
Step 5: Configure the Application with the Autonomous Database Connect String
Update the application server configuration file for the database connection configuration that’s running on Azure. Use the database connect string with the private IP address or private FQDN of the autonomous database.
Now you can connect to the autonomous database running on Oracle Cloud Infrastructure from the Azure application host by using the private IP address. You don’t need a service gateway to use transit routing to connect the Azure application server to the autonomous database.
The following image shows the content of the tnsnames.ora file used on the application server. It’s been updated with the private IP address of the autonomous database.
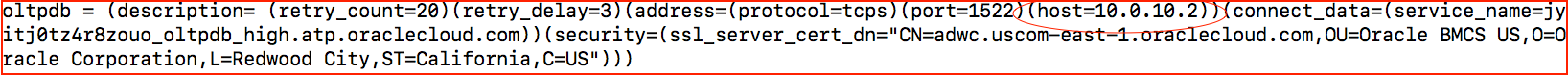
Step 6: Access the Application
As an example, we’ve used a social media application called Avengers Directory running on an Azure host connecting to an Oracle Cloud autonomous database by using a private IP address or private FQDN endpoint. Now we access the application from the Azure host.
Conclusion
You don’t need a service gateway on your VCN to connect an application running on Azure to Autonomous Database running on Oracle Cloud Infrastructure over a private connection. Now you can attach the autonomous database to the VCN and assign a private IP address. You can also configure the application running on the Azure host with the attached private IP address of your autonomous database. The application running on Azure connects directly to the autonomous database using a private IP address.
