This blog was written with contributing guest author Nancy Kramer, senior director in the Oracle Global Information Security organization, a key partner to the SaaS Cloud Security team.
Organizations benefit from incorporating risk management into their strategic planning and decision-making at all levels. By aligning their cloud computing strategy with their business objectives, organizations can make efficient investments and delivery on their goals. Effective risk management helps to anticipate and address future circumstances proactively, adapting as needed to support the organization’s objectives.
What is risk management?
The International Organization for Standardization (ISO) defines risk as “the effect of uncertainty on objectives,” referring to the potential impact of possible future events on the organization’s ability to achieve its goals. An event can be a change or a lack of change. It simply means an unplanned situation. An event can have beneficial or detrimental effects on different objectives. Consider “increase security staff by 5%” as a potential event. This event is beneficial for achieving security objectives but might not necessarily support budgetary objectives for cost control.
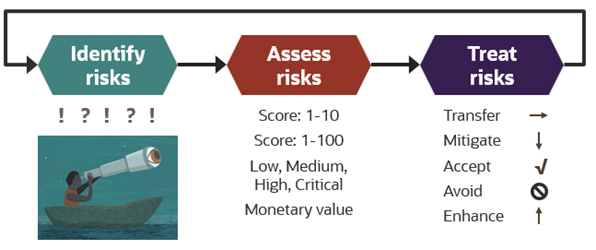
Optimally, risk management is a continuous cycle of activities to monitor the operating environment and direct how an organization identifies, assesses, and responds to risks relevant to the organization’s objectives. The preliminary step to engage in effective risk management is to define or select a risk management methodology. The frameworks differ in activities, but at its most basic level, risk management involves the following activities:
- Identify potential future events by monitoring internal and external environments.
- Assess the likelihood and impact of these potential future events, resulting in risk scores.
- Treat these risks, using the scores to help prioritize and select risk treatment actions.

How to identify risks
Compile a list of the potential events that might impact your organization’s ability to meet its objectives in the short and long term. External events include either stable or changed customer demand, competitive landscape, supplier products and services cost and availability, geopolitical environment, natural disasters, market forces, technology innovation, standards, economics, and regulations. To anticipate external events, monitor legal and industry news for your industry, essential suppliers, and key customers. To anticipate internal events, stay attuned to your staffing, technology, policies, business-critical processes, acquisitions, go-to-market strategies, executive direction, and organizational roles and responsibilities. A common risk for enterprise resource planning (ERP) applications is the lack of management and monitoring of role provisioning, entitlements, privileges, and change controls when roles change.
Assess risks
Evaluate the identified risks to determine their relative importance. Risk is often calculated as a potential event’s likelihood or probability multiplied by the impact if that event occurs. So, you can address the risk associated with potential events by activities that modify the likelihood, impact, or both.
![]()
Using a consistent methodology for scoring risk supports effective risk comparison and treatment planning. While determining likelihood and impact might be somewhat subjective, a defined methodology or framework that includes thresholds and offers examples for various likelihood and impact levels helps align risk assessment decisions. Modify this basic equation as needed, such as adjusting scores by the priority of the associated organizational objective. Options for risk scoring include the following examples:
- Financial: Assign monetary values to likelihood and impact
- Quantitative: Assign numeric values such as a scale of 1–10 or 1–100 to likelihood and impact
- Qualitative: Assign values, such as low, medium, high, and critical, to likelihood and impact
Treat risks
Focus on selecting and completing actions to improve the probability of achieving objectives, considering the impact of future possible events. Respond to risk using the appropriate treatment or response option for treating information security risk using one of the following methods:
- Transfer: Engage a supplier, such as outsourcing a high-risk function or buying insurance.
- Mitigate: Implement controls that reduce the likelihood or impact of possible adverse events, such as tightening access controls.
- Accept: Take no action when risk scores fall within executive risk tolerance guidance.
- Avoid: Prevent adverse events by excluding the source of risk, such as choosing not to offer certain product types, not to operate in particular markets or to use alternative technology
Some potential future events can benefit you in achieving objectives. We recommend that organizations try to implement actions that increase the likelihood of positive impact and events, based on the known risks and available data.
After completing risk treatments, recalculate the risk score using the new likelihood and impact values. The risk level after implementing risk treatments is the residual risk. If the risk is accepted, no recalculation is necessary.
Summary of risk management
Clarify your organization’s objectives. Monitor the internal and external environments to identify potential future events. Assess risk scores by evaluating the likelihood and impact of possible events, adjusting these scores in the context of organizational controls to calculate residual risk levels. Select and implement risk treatments to bring residual risk in line with executive guidance.
We recommend that enterprise risk management programs use a continuous feedback loop. For example, you discover new potential events that require consideration or that an event’s likelihood or impact score needs to change after applying risk treatments. You also learn that organizational controls are stronger or weaker than expected.
Oracle Risk Management and Compliance cloud
Oracle Risk Management and Compliance is a module within Oracle Fusion Cloud Enterprise Resource Planning (ERP), designed to manage risks and help you meet compliance, privacy objectives, and regulatory requirements. Oracle Risk Management can automate analysis, monitoring, and control of Oracle ERP cloud security, configurations, and transactions. Oracle Risk Management uses data science and AI techniques to help design restricted roles, monitor sensitive configurations, and detect suspicious transactions to protect against risks, such as payment fraud and error. To learn more about how to scale security risk management within Fusion applications, watch the Oracle Go webinar to see how the Fusion Risk Management service can provide a machine learning-enabled solution.
Risk management resources
Learn how Oracle’s security controls, privacy policies, and compliance attestations can support your organization’s security risk management and compliance needs by visiting the Oracle Trust Center. The following industry and standard body resources can also help you in your planning and assessments:
- EU ENISA Compendium of Risk Management Frameworks
- US NIST Risk Management Framework (RMF)
- US NIST IR 8286 Integrating Cybersecurity and Enterprise Risk Management (ERM) guidance
- US NIST Special Publication 800-39 Managing Information Security Risk
- ISO 31000:2018 series of international standards provides risk management guidelines
- Enterprise Risk Management Resource Center, including an overview

