From all-or-nothing to just-what-you-need: introducing OCI Private Service Access
As organizations expand their cloud adoption, protecting sensitive data while maintaining operational agility has become a top priority. In Oracle Cloud Infrastructure (OCI), the Service Gateway has long enabled private, on-cloud access to the Oracle Service Network (OSN), keeping service traffic off the public internet and within the Oracle network. However, because it allowed access to all OSN services in a region, customers with strict compliance or security mandates often found themselves needing finer control.
They wanted to restrict connectivity to only the services they trust, enforce precise policies that reflect Zero Trust security principles, and protect against risks like data exfiltration or unauthorized service use. They also needed the ability to use private IPs for service endpoints—ensuring a stronger security posture without complicating operations.
That’s why we recently introduced OCI Private Service Access (PSA).
Stronger data protection through controlled private access
With OCI Private Service Access (PSA), customers now gain the control and assurance they’ve been waiting for—private connectivity that is service-specific, policy-aware, and designed to align with Zero Trust security models.
Quick to Set Up, Easy to Manage
Deploying Private Service Access is quick and simple. You can enable PSA directly from the OCI Console in just a few clicks, and it integrates seamlessly with your VCN.
Use Case: Oracle Linux YUM Service Access
Traditionally, accessing Oracle Linux YUM repositories privately from a VCN required a Service Gateway, which automatically allowed access to all services in the Oracle Services Network (OSN). While this worked well for broad connectivity, many customers in regulated environments wanted something more refined – access only to Oracle Linux YUM, nothing more.
With Private Service Access, this becomes possible.
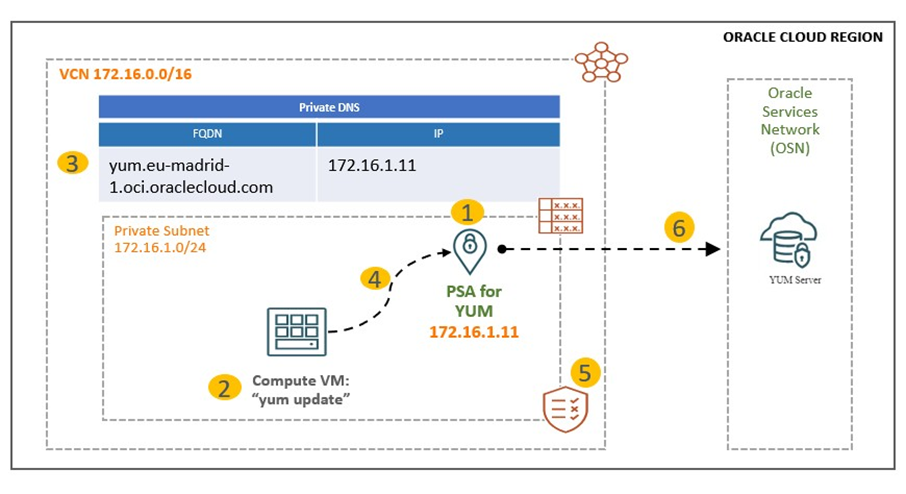
By deploying PSA for the Oracle Linux YUM Service, you can now:
– Privately access YUM repositories over your VCN using private IPs, without the need of using gateways.
– Limit access exclusively to the Oracle Linux YUM Service, rather than the entire OSN.
– Apply targeted ZPR or network policies, aligning with Zero Trust by allowing only the resources that specifically require YUM updates.
– Test and validate in minutes – from creating the PSA endpoint to running a simple “yum update” on an instance to confirm private routing.
How It Works in Practice
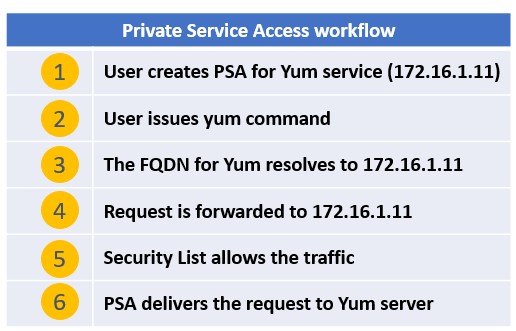
After enabling PSA on your VCN and selecting Oracle Linux YUM Service as the target service, OCI automatically provisions a private endpoint inside your subnet. This endpoint becomes the new destination for all YUM traffic.
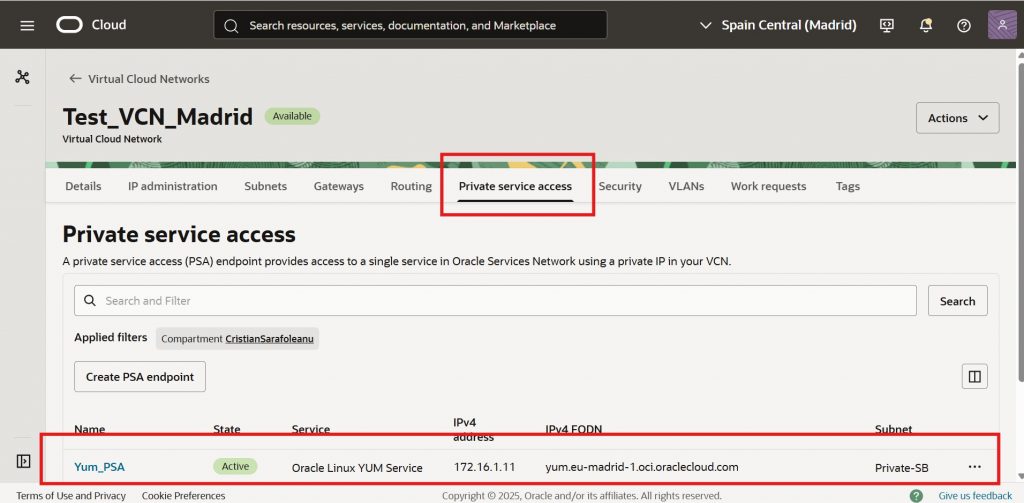
From start to finish, your setup generally includes:
1. PSA Deployment – Select your VCN, subnet, and the specific service (Oracle Linux YUM) in the PSA configuration.
2. ZPR & Network Policies – Allow your resources to use PSA, without opening outbound internet access or Service Gateway routes.
3. Testing the access – On a compute instance inside the subnet, run standard commands like:
sudo yum update
sudo yum install <package>
The traffic stays within Oracle’s private network and is routed strictly to the YUM server.
Your OCI Console screens will clearly show the PSA endpoint, associated private IP, and provide the network visibility through metrics, validating private access traffic — all without relying on the traditional Service Gateway.
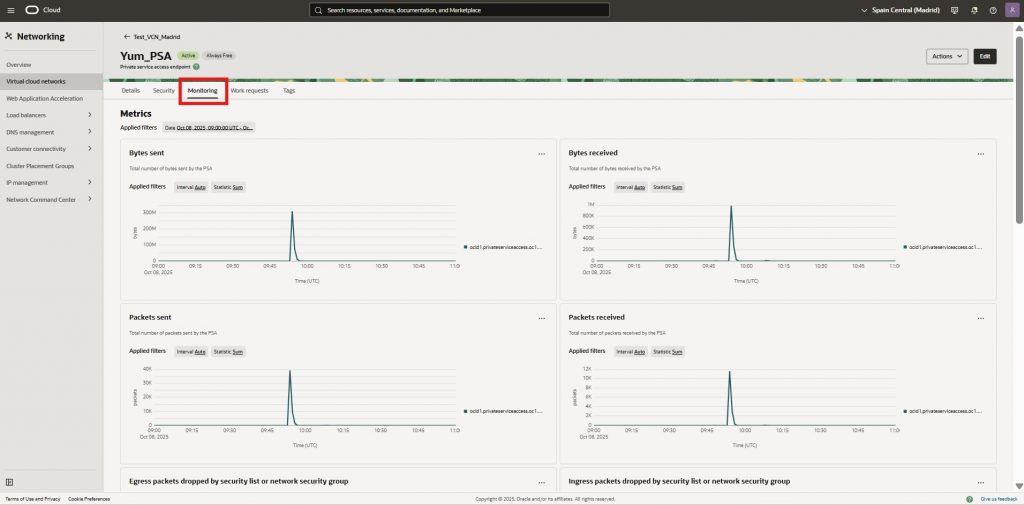
Why This Matters
This use case highlights how PSA modernizes service connectivity in OCI:
Security-first design – Only the YUM service is exposed, minimizing unnecessary access to other Oracle services.
Compliance-ready – Helps address regulatory requirements by keeping patching traffic private and controlled.
Operational simplicity – No need to manage NAT, gateways or public IPs.
Better alignment with enterprise security frameworks like Zero Trust and least-privilege networking.
Closing Thoughts
Private Service Access represents a significant shift in how cloud services are consumed securely within OCI. Instead of granting broad access through a Service Gateway, you can now give your workloads just what they need — nothing more.
The Oracle Linux YUM Service is a perfect example: patch management and OS updates can now be performed entirely over private IPs, with fine-grained control and full visibility. No internet exposure. No excess service permissions. Just secure and efficient operations.
As OCI continues expanding PSA support across more services, organizations can build cloud architectures that are not only scalable—but also inherently secure by design.
Ready to enhance your cloud security and simplify operations? Explore Private Service Access in Oracle Cloud Infrastructure today, and start leveraging its benefits for your workloads. For more information and step-by-step guidance, visit the Oracle Cloud documentation or contact your Oracle representative.
References
- Learn more about Private Service Access
- Read the Blog release announcement here
- Technical links: