We’re excited to announce Zero Trust Packet Routing (ZPR) with cross-VCN policy support, a major step toward unified, intent-based network security across Oracle Cloud Infrastructure (OCI). Modern applications span multiple Virtual Cloud Networks (VCNs) to improve isolation and scalability. But this distributed architecture can create security silos, making it harder to maintain consistent trust boundaries and prevent lateral movement when a single node is compromised. With ZPR cross-VCN policies, you can now define and enforce consistent trust boundaries for your workloads across VCNs through a single, human-readable policy that automatically scales with your environment.
Strengthening East-West Security
ZPR acts as a policy enforcement layer between your workloads, whether traffic flows through a Dynamic Routing Gateway (DRG) or a Local Peering Gateway (LPG). With cross-VCN support, ZPR policies now extend seamlessly across connected VCNs within the same tenancy and region, maintaining consistent segmentation as your applications evolve.
This unified approach:
- Eliminates unauthorized east-west communication
- Blocks lateral movement early in the attack chain
- Reduces the operational burden of managing per-VCN rules
Why this matters
As cloud architectures expand, ensuring consistent network segmentation and trust boundaries becomes both more critical and complex. Traditionally, each VCN required its own set of ingress and egress policies, often managed separately across teams and environments (see Figure 1). This leads to inconsistent enforcement, redundant configurations, and higher operational overhead.
Figure 1: Traditional per-VCN policy model
(Each VCN defines its own ingress/egress rules using Network Security Groups or Security Lists)
For example, the App Tier CIDR(s) are defined in all the peered VCNs. As the App VCN scales, the user is required to update/add App VCN CIDRs in all the peered VCNs.
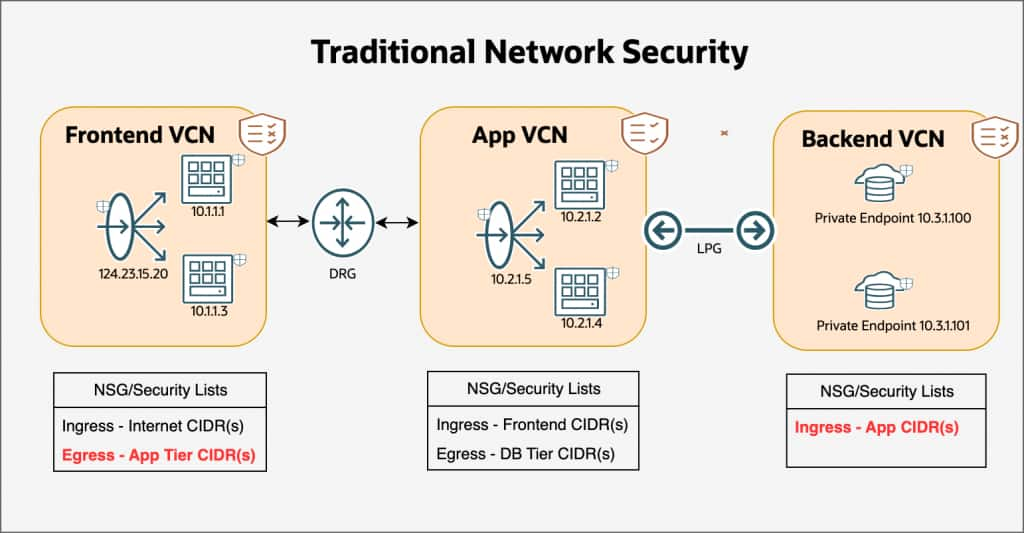
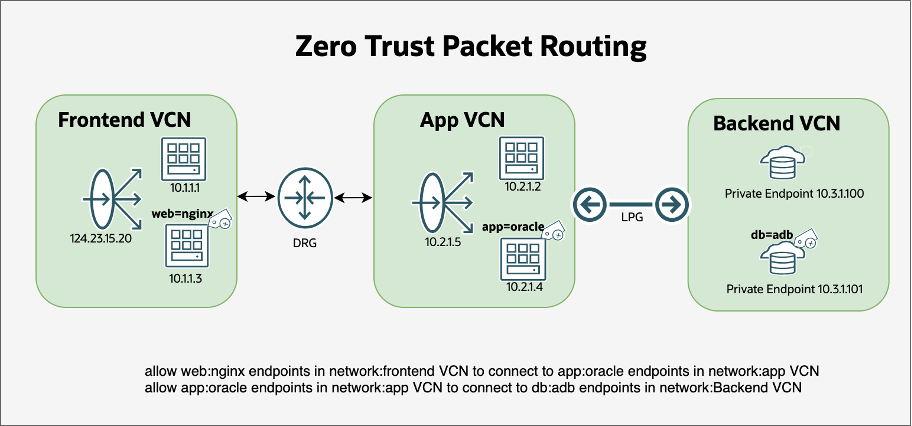
Figure 2: Simplified security with ZPR cross-VCN policies
(A single rule defines allowed communication between OCI resources across VCNs)
With ZPR, cross-VCN policies eliminate this fragmentation by letting you define your security intent once. ZPR takes care of enforcement everywhere as the environment scales.
allow app:oracle endpoints in network:app VCN to connect to db:adb endpoints in network:backend VCN
This single rule ensures that only app workloads with the attribute app:oracle can communicate with backend-tier workloads labeled db:adb. All other connections are blocked by an implicit deny rule – no extra NSG or Security List replication required. When a new instance is added with the appropriate attributes, access is automatically applied, keeping security aligned with business logic, not IP addresses. Defining and assigning these Security Attributes can also be trivially automated as part of deployment workflows, ensuring the right attributes are consistently applied with minimal effort.
Key Benefits
Unified enforcement
Define intent once, and ZPR ensures consistent enforcement across all connected VCNs within the tenancy & region. Policies follow workloads automatically, maintaining trust boundaries as environments scale.
Operational simplicity
Replace duplicative per-VCN rules with a centralized policy model. Gain complete visibility into what can (and cannot) communicate across environments, simplifying audits, reviews, and troubleshooting.
Scalable by design
As your footprint grows, onboard new VCNs (staging, prod, partner), subnets, IP address blocks instantly. Existing ZPR policies automatically extend to them – no manual rule replication required.
Understanding ZPR and Security Attributes
Before diving into Cross-VCN setup, let’s briefly understand the core ZPR concepts.
What is ZPR?
Zero Trust Packet Routing in OCI enforces least-privilege connectivity across workloads. Instead of IP-based rules, ZPR uses security attributes (key-value tags) to define trust relationships between workloads.
What are Security Attributes?
Security attributes (for example, tier=frontend, env=prod) are metadata you assign to OCI resources such as Compute instances or Load Balancers. ZPR uses these attributes to form logical trust groups and enforce access policies between them.
Getting started with Cross-VCN ZPR
Creating cross-VCN ZPR policies is simple and intuitive. The console experience guides you through every step, with built-in UX controls that help you easily craft secure, intent-based policies across VCNs. Whether you are defining policies visually or using templates, ZPR ensures a consistent and streamlined workflow.
You can create cross-VCN ZPR policies in a few simple steps.
Figure 3:
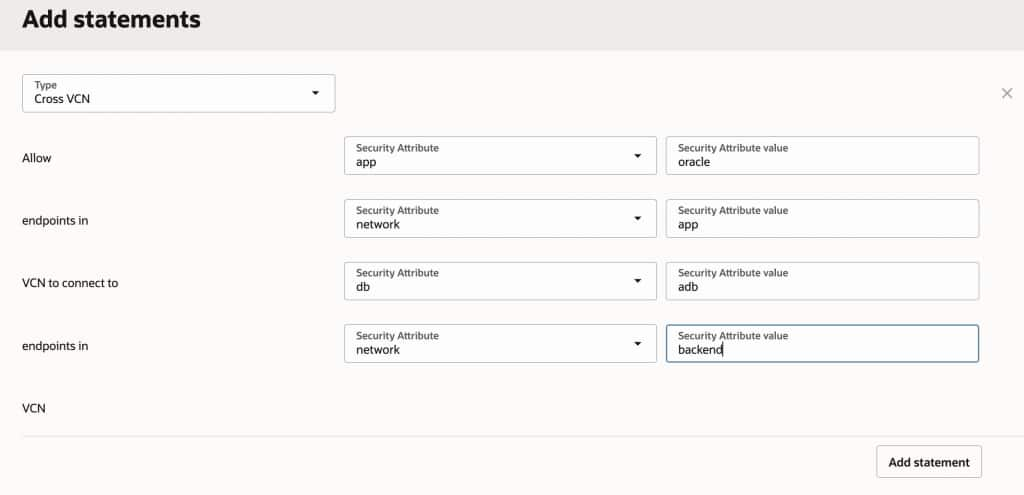
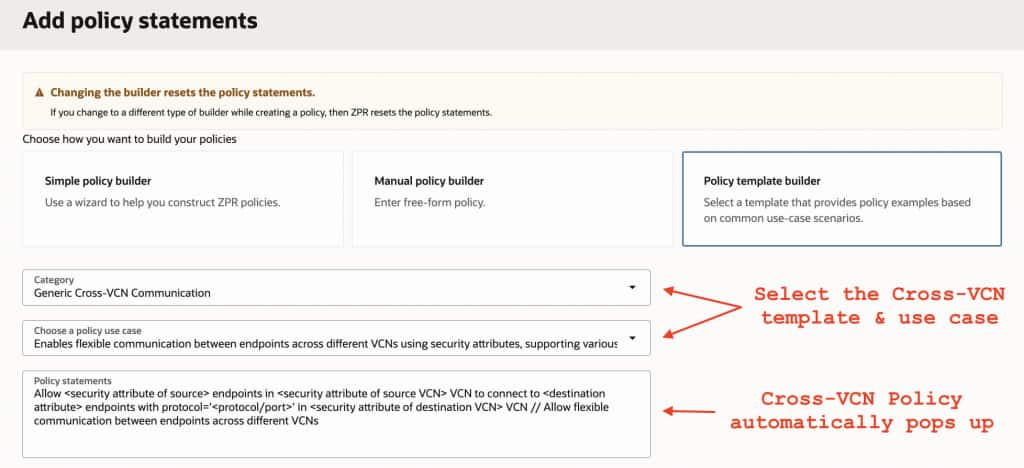
Figure 4:
You can create cross-VCN policies with the following steps:
- Navigate to ZPR: In the Oracle Cloud Console, under the Identity & Security section, go to Zero Trust Packet Routing.
- Create or select a namespace: You could use any existing or the default (oracle-zpr) security attribute namespace. Optionally, you could create a new namespace by clicking on the “Create Security Attribute Namespace” button and adding security attributes.
- Build Policies:
- Next, add ZPR Cross VCN policies by clicking on “Create Policies”. Choose between:
- Simple Policy Builder -now supports “Single VCN” or “Cross VCN” options (Figure 3).
- Policy Template builder – includes ready-to-use cross-VCN templates (Figure 4).
- Manual Policy Builder – For direct rule input
- Apply security attributes: Assign attributes to resources across VCNs. ZPR automatically applies the right policies.
- Validate connectivity: Confirm intended communication between resources across VCNs works as expected.
Next steps
To learn more and explore examples, check out the ZPR Cross VCN documentation and our recent ZPR release announcement. Experience ZPR’s unified security capabilities firsthand – try Oracle Cloud Infrastructure with a US$300 free credit and start building Zero Trust architecture today.
