The Oracle Government Cloud for Department of Defense (DoD) regions are accredited to DISA Impact Level 5 (IL5) for infrastructure and platform as a service (IaaS and PaaS). In my previous posts, I discussed designing a reference architecture for DoD IL2 and a reference architecture for DoD IL4 workloads on Oracle Cloud for Government.
This post examines a reference architecture for DoD IL5 workloads on Oracle Government Cloud for DoD. Oracle Cloud for Government supports five regions, purposefully built for the U.S. Government. Of the five regions, three are accredited for up to IL5 and dedicated to DoD mission and customers. The following table describes the regions, accredited impact levels, and the boundary cloud access point (BCAP) connections.
| Oracle Cloud region |
Information impact level |
Connects to BCAP |
| U.S. DoD East (Ashburn, VA) |
up to IL5 |
Yes |
| U.S. DoD North (Chicago, IL) |
up to IL5 | Yes |
| U.S. DoD West (Phoenix, AZ) |
up to IL5 | Yes |
The data processed at IL5 accommodates nonpublic, unclassified National Security System (NSS) system data, such as U-NSI, or nonpublic unclassified data where the unauthorized disclosure of information is expected to have an adverse effect on organizational operations, organizational assets, or individuals. For IL5, all DoD traffic from NIPRNet to and from off-premises content security policy (CSP) infrastructure, the mission’s virtual networks must traverse one or more NIPRNet BCAPs. No direct IL5 traffic is permitted to or from the internet except through the NIPRNet IAPs and demilitarized zone (DMZ) capabilities provided by the mission owner, a DoD component, or DISA.
How does Oracle Government Cloud for DoD satisfy location and separation requirements?
To satisfy location and separation requirements for IL5, Oracle’s strategy is to have community clouds. Oracle has built separate regions for our DoD customers only or customers with a specific mission supporting the DoD. These regions have complete separation from non-DoD and non-federal government tenants. For non-DoD and non-federal government, tenants can choose to consume our Oracle Cloud for Government regions.
How does Oracle Government Cloud for DoD provide strong virtual separation for IL5?
For IL5, the CSP must provide evidence of solid virtual separation controls and monitoring. Oracle Cloud Infrastructure (OCI) offers various isolation and virtual separation levels through isolated network virtualization with a custom-designed SmartNIC. The SmartNIC is isolated from the host by hardware and software, preventing a compromised instance from compromising the network.
Compute isolation is created when your tenancy is provisioned, and you start to deploy systems by creating your virtual cloud network (VCN). If you require further isolation, you can choose to use OCI bare metal or dedicated virtual machine host options. These options provide a dedicated physical server for more robust isolation. You don’t need to have dedicated compute to have strong isolation. Your Compute instances are already isolated to your VCN, providing extra isolation with dedicated compute options.
OCI reduces risk by decoupling network virtualization from the hypervisor. Oracle has implemented network virtualization as a highly customized hardware and software layer that moves cloud control away from the hypervisor and host and puts it on its network. This hardened and monitored layer of control enables isolated network virtualization. Isolated network virtualization is implemented in every data center in every region, which means that all OCI tenants benefit from this reduced risk.
What are my off-premises connectivity options with OCI for IL5?
For an IL5 system, network traffic must traverse the NIPRNet through a CAP. Select OCI regions to allow for connectivity through a BCAP. For more information on how Oracle connects to the NIPRNet, see the following articles:
-
Connecting to the NIPRNet for Impact Level 4 and 5 workloads in Oracle Cloud Infrastructure
-
Oracle Cloud Infrastructure US Federal Cloud with DISA Impact Level 5 Authorization
Sample DoD IL5 reference architecture workload
Now that we’ve covered how OCI satisfies physical location and separation, virtual separation, off-premises connectivity, we can discuss the integration of your workloads.
As an application owner, you inherit the controls and authorizations that OCI has put in place. However, according to the DoD cloud computing security requirements guide (SRG), applications owners are still responsible for applying other controls.
A DoD IL5 reference architecture differs from an IL2 system, based on external network access and other security controls. In addition, an IL5 workload is different from an IL4 workload because the IL5 workload must reside in a physically separated environment, separated from non-DoD and non-Federal government tenants.
The reference architecture is like an IL4 architecture, only you host your workload in one of the Oracle Government Cloud for DoD regions in Ashburn, Chicago, or Phoenix. The following graphic shows a sample reference architecture of how to host an IL5 system in an Oracle Government Cloud for DoD region:
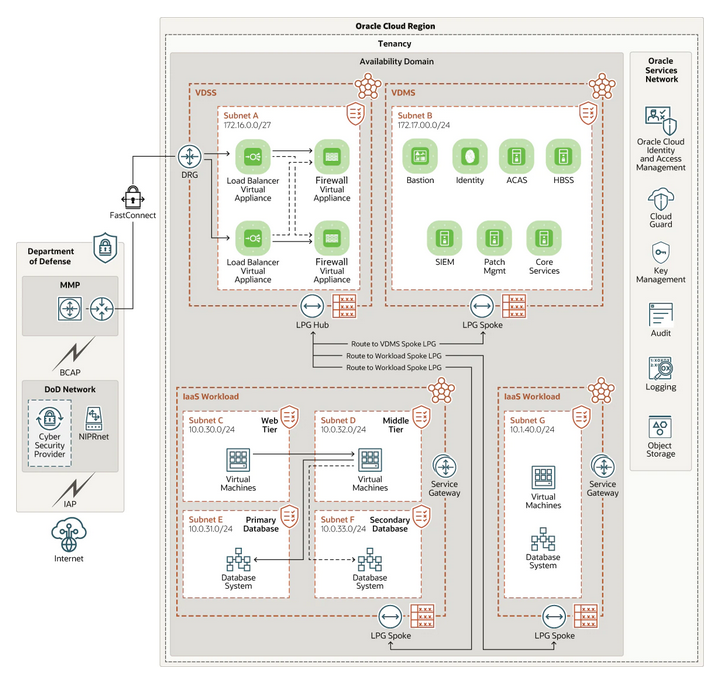
This architecture has the following design considerations:
-
Ensure that you request a tenancy in one of the Oracle Government Cloud for DoD regions accredited for IL5 in Ashburn, Chicago, or Phoenix.
-
By default, OCI uses a zero-trust security model. With zero-trust security, no one is trusted by default from inside or outside the network.
-
All public internet traffic must now enter the DoD information networks (DODIN) before entering the VCN of the OCI tenancy.
-
We introduce the following requirements according to the Cloud Computing—Security Requirements Guide (CC-SRG):
-
Virtual data center security stack (VDSS): Traffic into the VCN flows into subnet A, the VDSS. The core services of the VDSS contain a web application firewall for network traffic inspection, a next-generation firewall for intrusion prevention and intrusion detection, and load balancers.
-
Virtual data center management service (VDMS): For subnet B, a VDMS provides security systems to manage the security posture, such as Bastion, Identity and Access Management (IAM), assured compliance assessment solution (ACAS), host-based security system (HBSS), security information, and event management (SIEM), patch management, and core services.
-
-
The rest of the subnets contain your mission owner components (IaaS and PaaS workloads), such as your virtual instances, web servers, middle-tier servers, and your databases. These subnets are separated from your VDSS and VDMS systems and subnets.
For more information, see What is Secure Cloud Computing Architecture (SCCA).
What’s next?
I invite you to give it a try yourself. When you’ve the design laid out, you can get started with Oracle Cloud Free Tier for a 30-day free trial in our commercial regions, which includes US$300 in credits to get you started with a range of services, including compute, storage, and networking. If you want to take a test drive in Oracle Cloud for Government, consult with Oracle sales representative for a proof of concept in the appropriate region.
