The Oracle Cloud Infrastructure (OCI) Government Cloud regions are accredited DISA impact level 5 (IL5) for infrastructure- and platform-as-a-service (PaaS). Recently, I’ve had a few discussions with various customers around designing systems on OCI Government regions to with other DISA Impact Levels. In this post, I focus on a reference architecture for a DISA impact level 2 (IL2) system.
The data processed at IL2 accommodates DoD information that has been approved for public release with low confidentiality and moderate integrity. Typically, this information includes public websites containing non-sensitive information. If you’re a non-US government or Department of Defense (DoD) customer, you can treat this information the same way that you treat your own data.
You might want to consider separating these public facing systems containing public facing data and connected to the internet, from the more sensitive data into different virtual cloud networks (VCNs) to have isolation between the systems. You can also create separate tenancies for public facing systems and non-public facing systems.
There’s no right or wrong answer for these architectures. When you have your design in place, review your designs with your cyber security teams to ensure that you meet your organization’s cyber security requirements. This reference architecture serves as a guide because each system is different.
Sample DoD impact level 2 reference architecture
The following example exhibits our reference architecture for how to host an IL2 system in an OCI Government region:

Use the following design considerations for this architecture:
-
By default, OCI uses a zero-trust security model. With zero-trust security, no one is trusted by default from inside or outside the network.
-
Security lists control network ingress traffic to the VCN, network traffic from within the VCN, and between subnets.
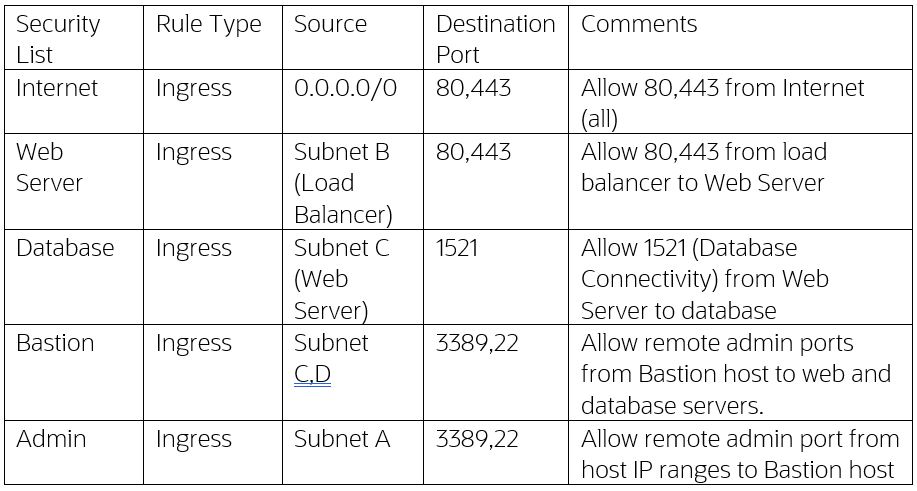
-
A load balancer serves as a reverse proxy to allow you to direct network traffic only to web servers insider your VCN.
-
Oracle uses a service gateway to allow your VCN to privately access specific Oracle services without exposing data to the public internet. In this case, the service gateway is used for accessing OCI Object Storage service.
-
Static web-addressable content can be stored on an object storage bucket that is accessible from the Internet.Static web-addressable content can be stored in an Object Storage bucket accessible from the internet.
-
Backups, images, and log data can be stored in an Object Storage bucket behind the service gateway, making it accessible only on the private network and within the VCN.
What if I need a highly available system for my DoD IL2 system?
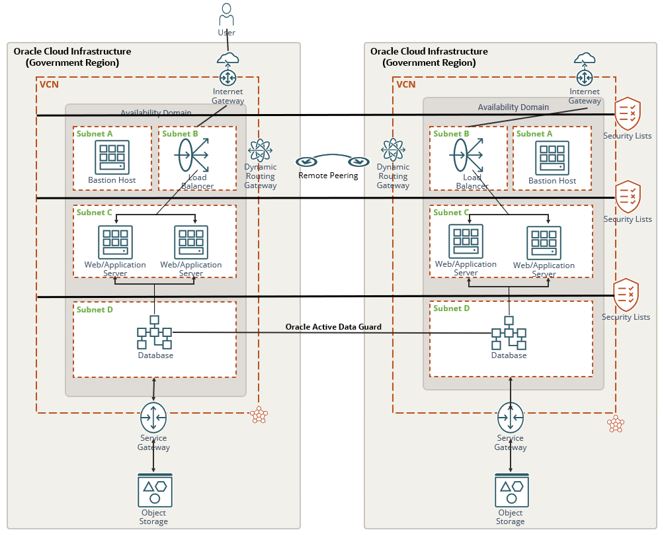
The same design considerations apply to the single region design, but this design has the following considerations in place to allow for a lower recovery time objective (RTO):
-
Create a clone of our environment into another region.
-
Create the same subnets with the same security lists.
-
Deploy dynamic routing gateways (DRGs) and enable remote peering, which allows the VCNs in different regions to communicate with each other.
-
By creating a remote peer, we can now replicate our data across regions, specifically our Oracle Database Data with Oracle Active Data Guard.
-
Other data, such as files storage or application data, can be replicated also over the remote peering connection.
This reference architecture allows you to maintain the same IL2 system but now with higher availability than the previous architecture and a lower RTO.
What’s next?
Wherever applicable, we’re releasing Terraform code that you can easily download, modify, and deploy in your own accounts. The OCI Architecture Center showcases technical content to help you build on Oracle Cloud, and you can find a library of reference architectures to deploy with Resource Manager. Each reference architecture introduces a platform topology, using architectural diagrams, a component overview, and recommendations for best practices, including availability, performance, security, and costs.
I invite you to give it a try yourself. When you have your design laid out, you can get started with Oracle Cloud Free Tier for a 30-day free trial in our commercial regions, which includes US$300 in credits to get you started with a range of services, including compute, storage, and networking. If you want to test-drive in our Oracle Cloud Infrastructure regions dedicated for the government, consult with your Oracle sales representative for a proof of concept in the appropriate region.
