We’re excited to announce the general availability of security scanning for package vulnerabilities in Oracle Cloud Infrastructure (OCI) DevOps service‘s build pipeline in conjunction with the new Application Dependency Management service. Application Dependency Management maintains an expert curated database of vulnerabilities and their relationships to Maven Central dependencies.
Developers today working on any kind of production software have a set of security and compliance best practices to ensure that they don’t release code that’s open to attacks on known vulnerabilities. We all remember scrambling last year to patch software vulnerable to the Log4Shell exploit. This scanning and patching cycle can add manual steps to a software delivery workflow, and we’re excited to make it easier for developers to start to automate compliance in their DevOps service pipelines.
The new vulnerability audit feature enables you to scan for common vulnerabilities and exposures (CVEs) as part of your continuous integration (CI) pipelines. Currently, we’re supporting Maven dependencies based on pom.xml files. Developers can now add a vulnerability audit step for Maven projects within their DevOps service build instructions. Developers can set up the minimum CVSS scores to fail a build and, if a CVE above that threshold in a package is detected in the pipeline, run the build fail to ensure that developers are alerted on the vulnerability and patch it. Integrated vulnerability audits help developers keep known vulnerabilities from making it into production.
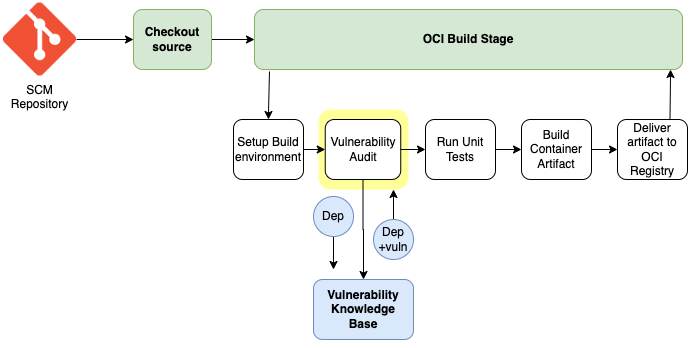
Vulnerability audit build step
The new Vulnerability Audit step can be added to the existing DevOps service build instructions as shown:
...
- type: VulnerabilityAudit
name: "Vulnerability Audit Step"
configuration:
buildType: maven
pomFilePath: ${OCI_PRIMARY_SOURCE_DIR}/pom.xml
packagesToIgnore:
- org.apache.struts
maxPermissibleCvssV2Score: 6.0
maxPermissibleCvssV3Score: 8.1
knowledgeBaseId: ocid1...
vulnerabilityAuditCompartmentId: ocid1...
vulnerabilityAuditName: sample_va
...With this simple configuration, developers can control the configuration of the scan to pass or fail. In the step configuration, developers can ignore certain artifacts or versions paths and control the maximum permissible CVSS scores (the overall score assigned to a vulnerability) that they allow within their project. For example, you can specify that you have tolerance for certain medium or low severity CVEs or for specific package names like struts.
Next, developers can view the results of their vulnerability audit in the build instructions output and details of the build run.
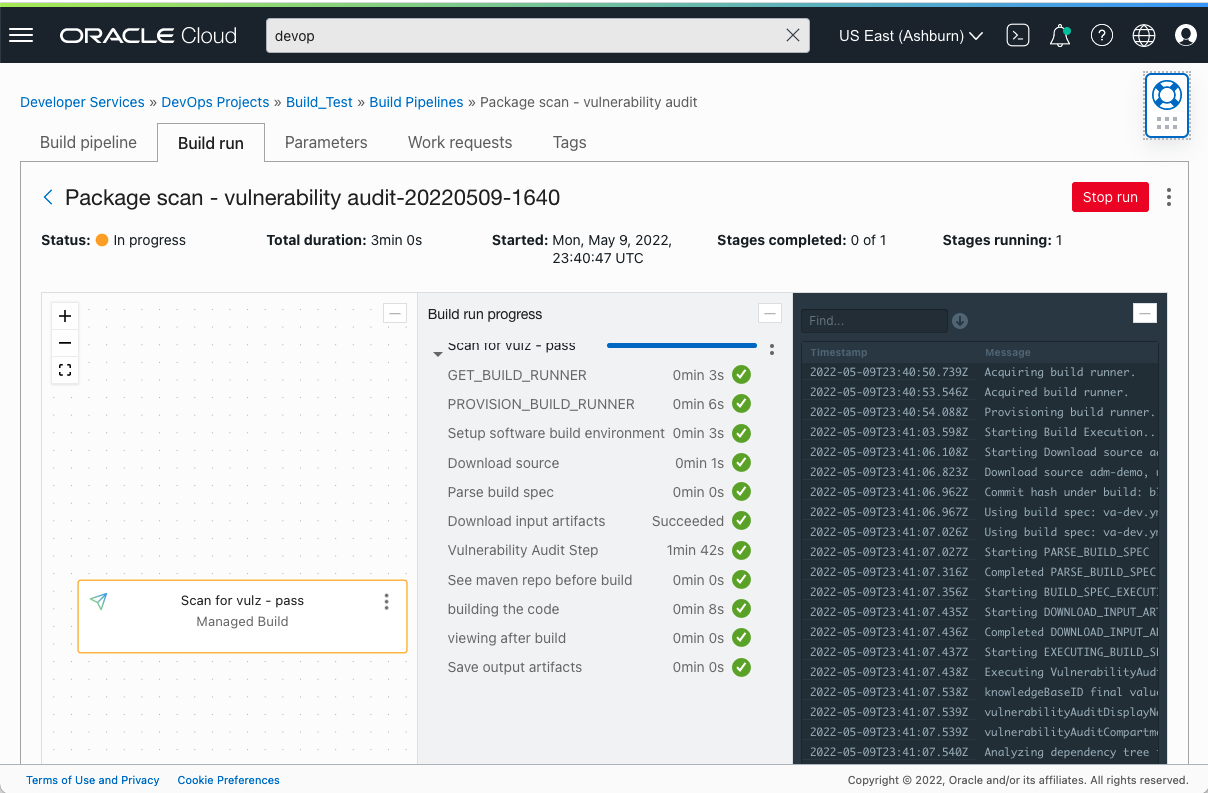
Vulnerability audit
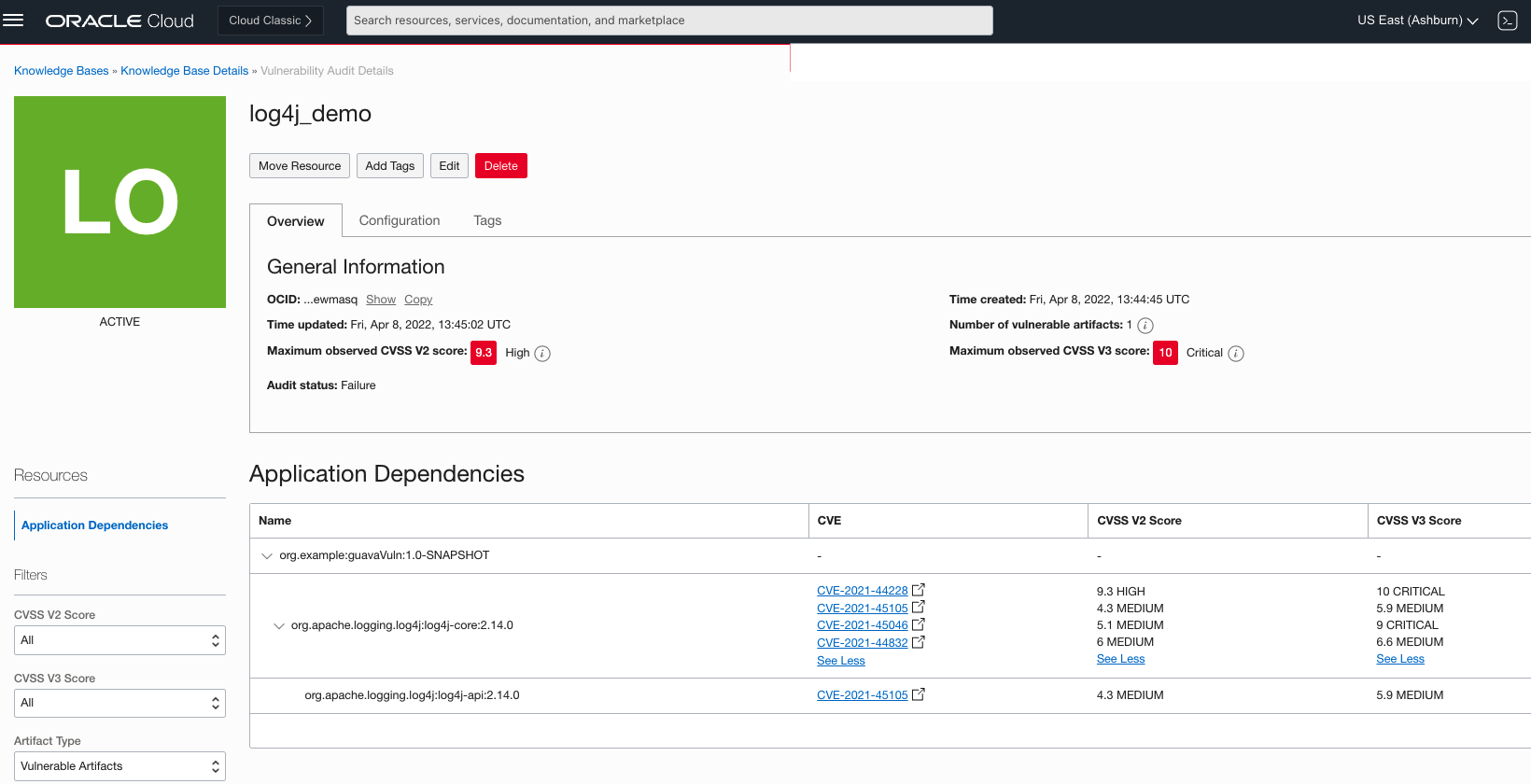
If the DevOps build pipeline fails because of found vulnerabilities, developers can view the vulnerability audit result to see the full tree of dependencies along with the associated CVEs. The developer can inspect CVE scores to understand the issue and then make the necessary changes, such as patching some of the dependencies to versions that don’t include the vulnerabilities.
Get started today
Security vulnerability scanning for Maven builds is a new capability part of Oracle Cloud Infrastructure DevOps CI pipeline service. To use OCI DevOps and create your CI build, simply sign up for a free account and follow the vulnerability audit documentation.

