Oracle Cloud Guard has been helping customers improve the security posture of their Oracle Cloud Infrastructure (OCI) environments since 2020, and now we are introducing Cloud Guard Threat Detector to help identify malicious activities and rescue security operators from drowning in a sea of alerts. We anchored Threat Detector in the MITRE ATT&CK framework, and leverage Oracle’s threat intelligence and data science capabilities to surface sightings of nefarious behaviors that really deserve your attention. You can avoid the trap of investigating every anomaly!
What is Oracle Cloud Guard Threat Detector?
Threat Detector is a new Oracle Cloud Guard detector recipe that continuously monitors OCI audit events looking for malicious activity. It uses a data platform capable of running machine learning (ML)-based behavioral attack models over long periods of time. Models are aligned with MITRE ATT&CK techniques so they are narrow enough to carry clear intent, yet broad enough to be durable as procedures evolve.
Threat Detector maintains user profiles that include the sequence of attack sightings and associated risk score. The risk score is formulated to track attack progression by considering factors such as severity and confidence of individual sightings, tactics and techniques involved, and their timing.
For example, here is the profile for a user called Anakin:
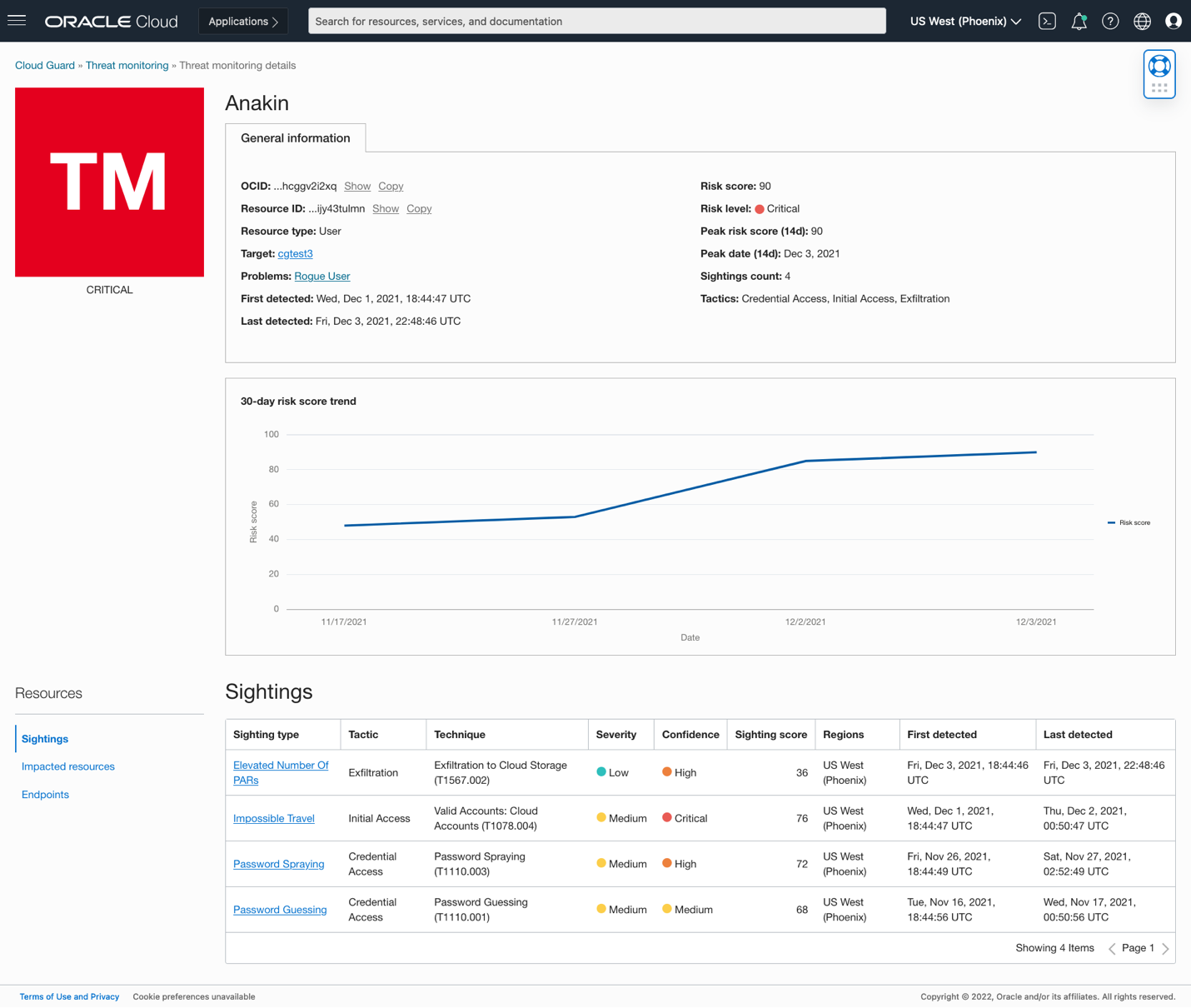
It all started with some brute-force sightings: password guessing early on, followed by password spraying a week later. Anakin’s privileges in this environment seem low enough that these sightings only warrant a medium severity and a middle-of-the-road risk score.
A few days later, Threat Detector observes Anakin in locations too distant to have traveled between them, which could be evidence of success for the preceding brute-force attempts. This increases the risk score significantly, which climbs again once the service detects an elevated number of pre-authenticated object storage requests. The attack seems to be reaching an exfiltration phase!
Tracking each sighting independently would be impractical, and they are minor enough that these sightings could fly under the radar easily. However, putting them together, these sightings paint a grim picture. Therefore, the overall risk score increases to reflect their combined urgency given the attack progression.
As the risk score was rising it exceeded the problem threshold, so a Cloud Guard problem was generated as seen on the following image.
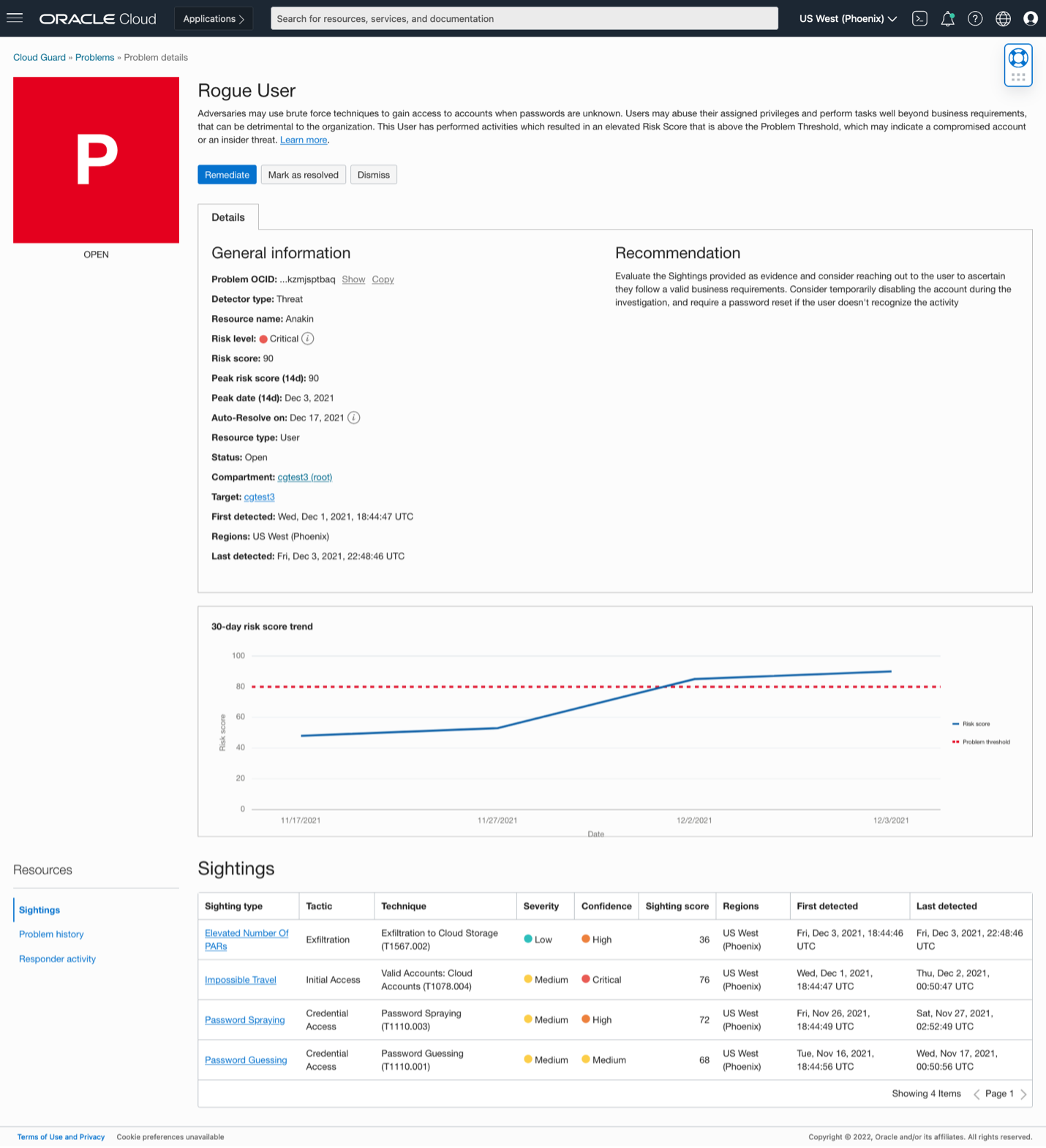
Cloud Guard problems are used to alert security operators that their attention is needed, keep track of the event, and possibly trigger automated remediation workflows and downstream integrations.
Do I really need more alerts?
Imagine you are tasked with protecting your new cloud environment. You may already be suffering from alert fatigue and fear of missing incidents – a dangerous burnout recipe for you and your organization – as the number of daily alerts keeps increasing and you don’t get to investigate many of them.
Sound familiar? According to Cisco’s 2020 CISO Benchmark Report many organizations have gone from 56% of alerts investigated in 2017 to less that 48% in 2020. Evidently you are not alone, but that doesn’t mean you get a pass at protecting your environment. So somewhere in the back of your mind is the nagging concern of an insider threat – somebody in your organization abusing your infrastructure – or maybe a compromised account.
Threat Detector calls this a “rogue user”, and it provides a simple detector rule that combines sightings of multiple malicious behaviors into a single alert. Keeping the volume and noise levels of alerts down to avoid upsetting your already-crazy day.
We launched Threat Detector with support for OCI audit logs and integration with the Oracle Threat Intelligence Service that was also announced announced recently, with multiple models aimed at identifying rogue users. Best of all, Threat Detector for Audit logs is free of charge for paid tenancies, just like Cloud Guard!
We look forward to introducing more models and data sources in the future.
Turning on Threat Detector
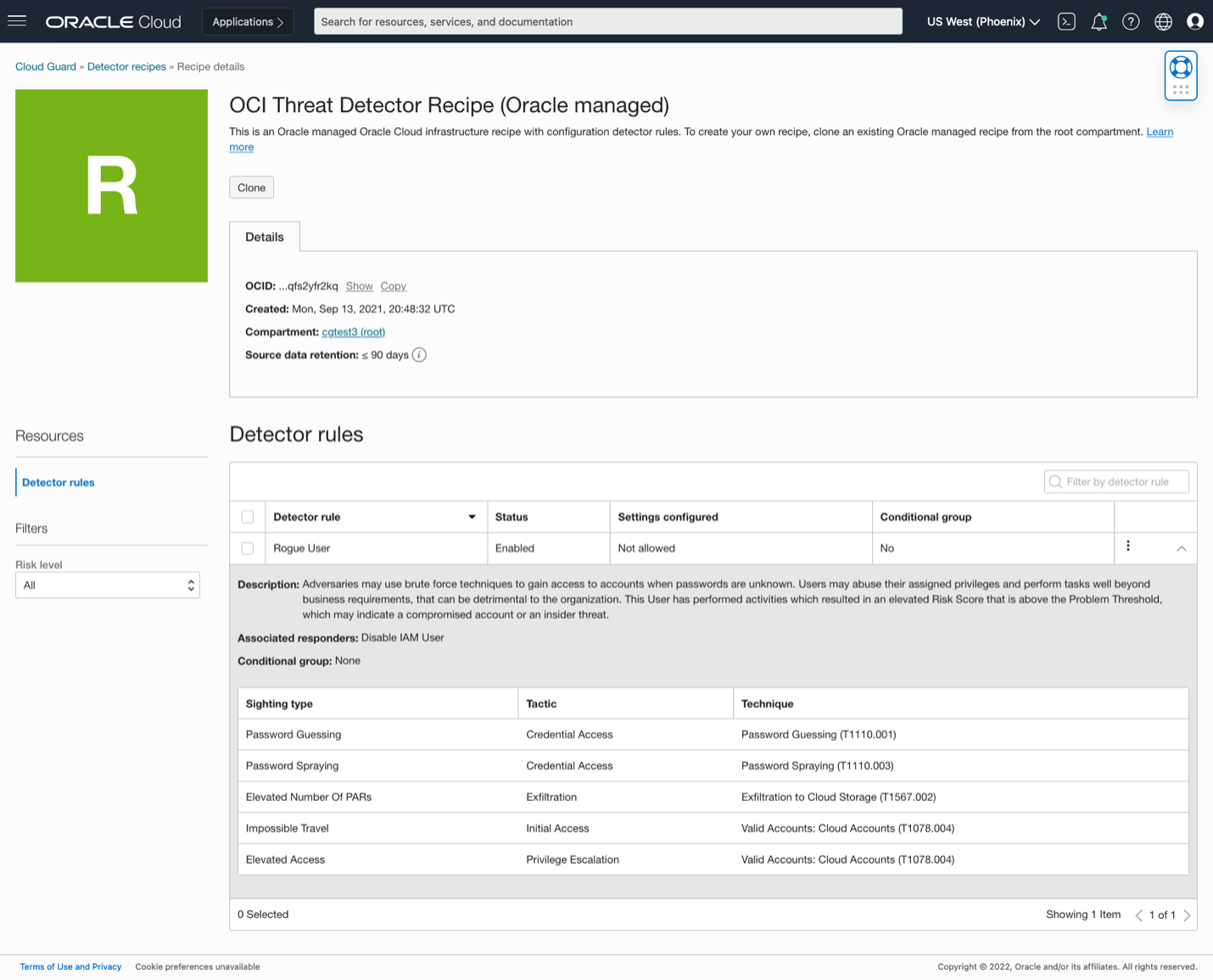
Following Cloud Guard’s approach to making security simple to use, enabling Threat Detector takes just a moment. If you are already using Cloud Guard – and there’s no good reason not to – just add the “OCI Threat Detector Recipe (Oracle managed)” recipe (shown below) to your root compartment’s target and the service is enabled!
Want to learn more about how Cloud Guard Threat Detector can help expand your security coverage without getting buried in alerts? Come and evaluate for yourself. Configure Cloud Guard Threat Detector today!
