Original Publish Date : 9/6/2019
Oracle Identity Cloud Integrator provider has to be configured in JCS Admin console if you have a requirement to login to your application OR Weblogic console using IDCS Users.
As a pre-requisite, we need to create an OAuth client in IDCS:
Step 1:
Login to IDCS console -> Applications -> Add Application -> Confidential Application:
Name:<Any_name> -> Next
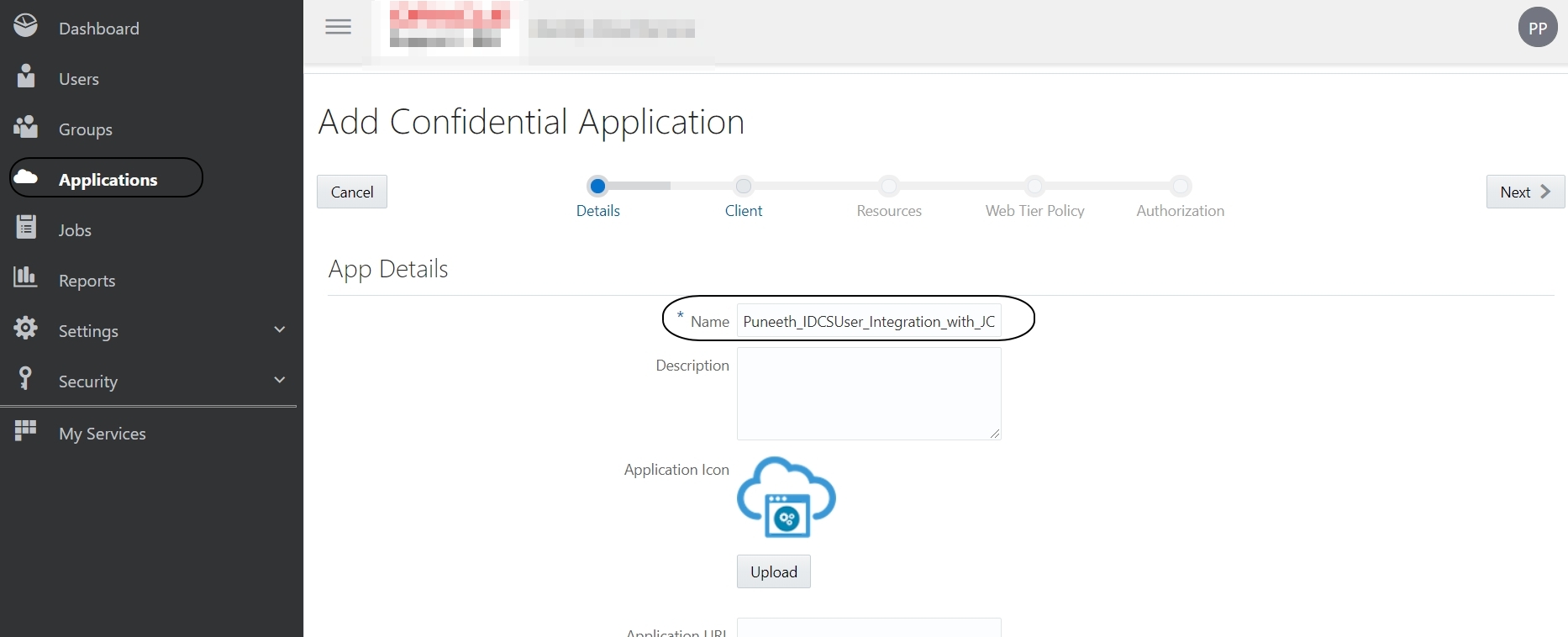
Select “Configure this application as a client now”
Allowed Grant Types: Client Credentials
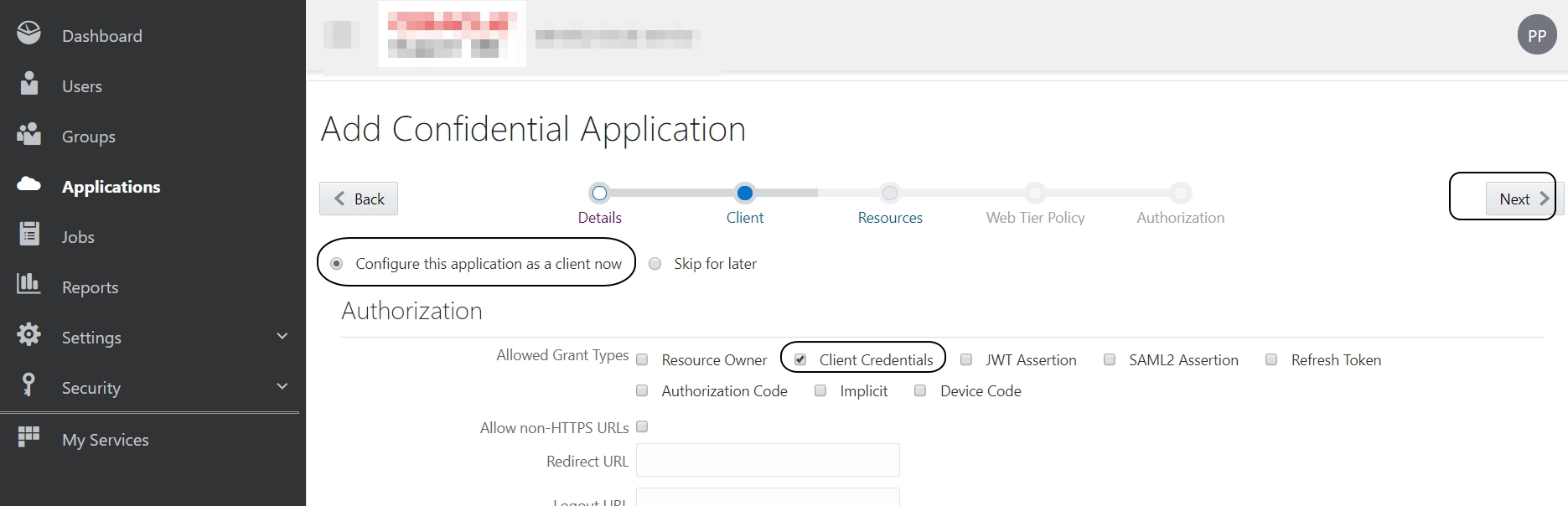
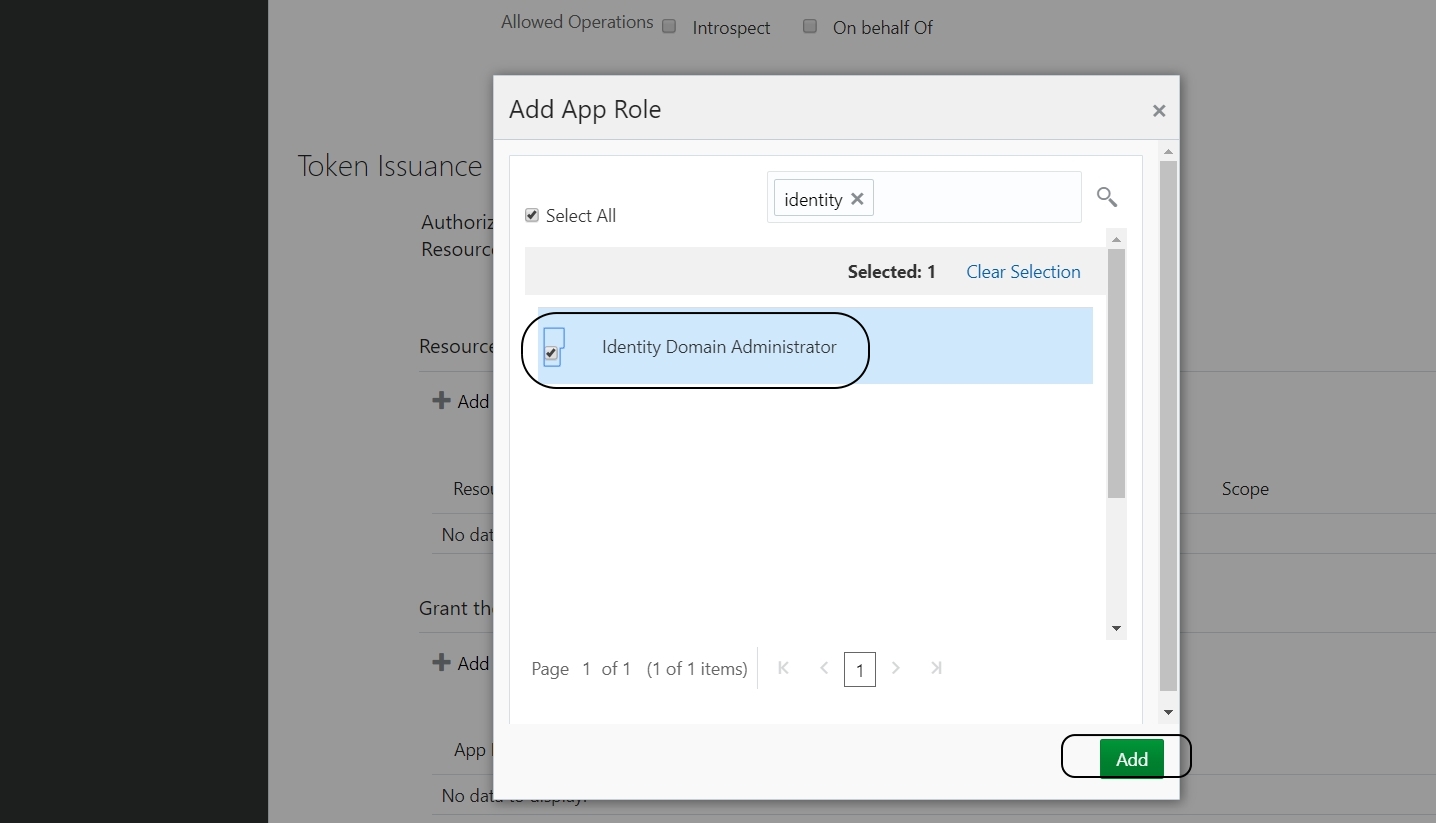
Scroll down and click on +Add icon below “Grant the client access to Identity Cloud Service Admin APIs” :
Choose “Identity Domain Administrator” from the list and click on Add:
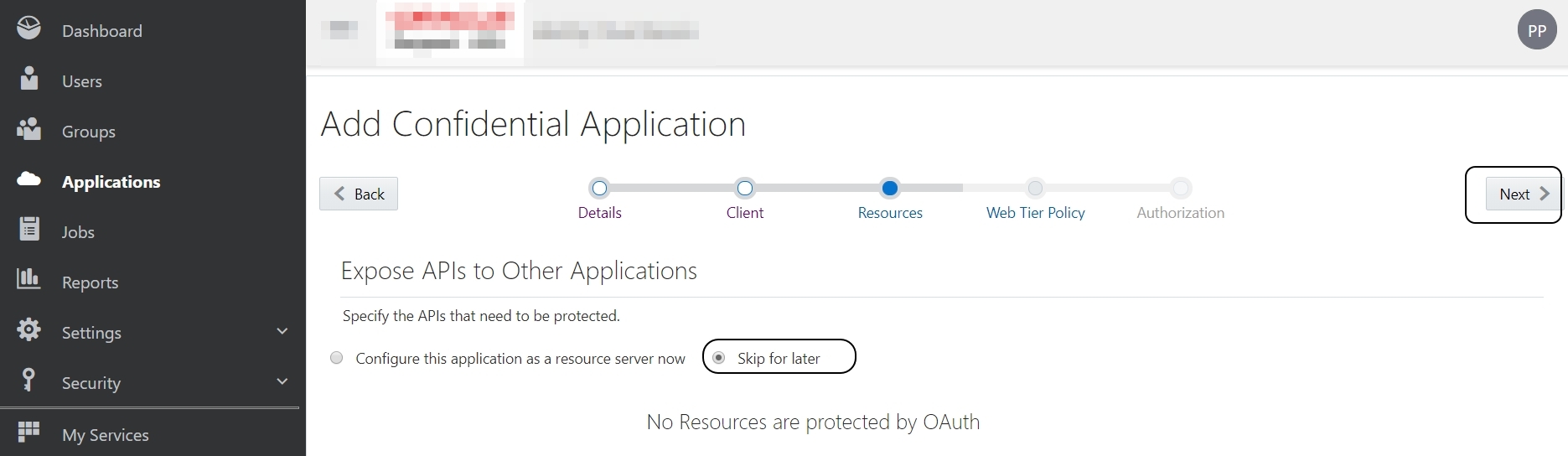
Skip the next section (Expose APIs to Other Applications):
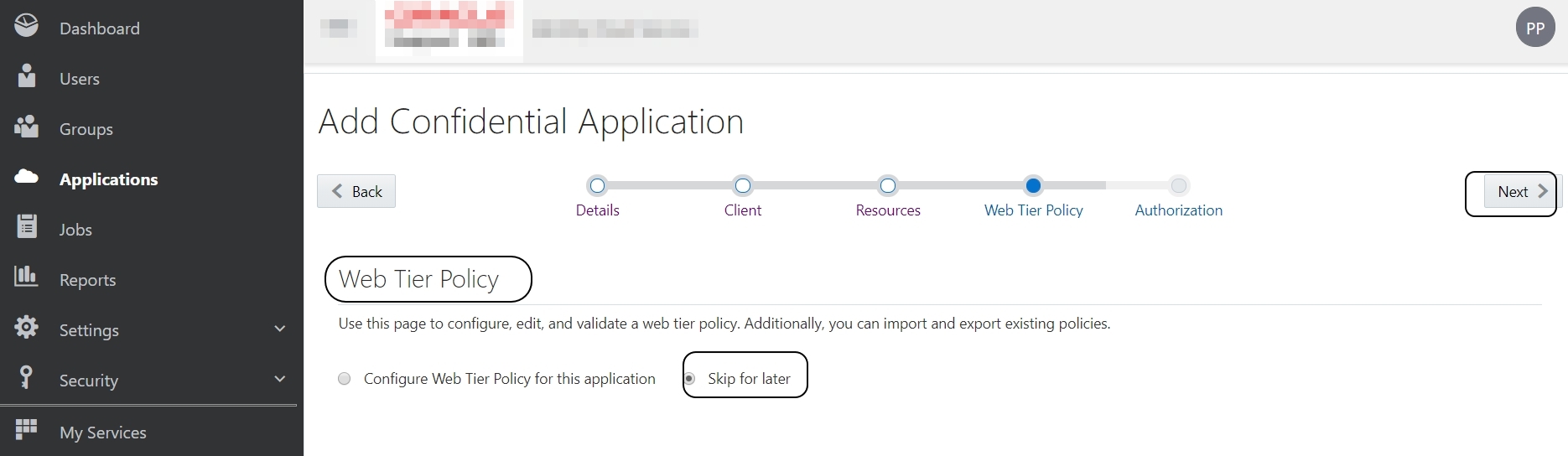
Skip the next section (Web Tier Policy):
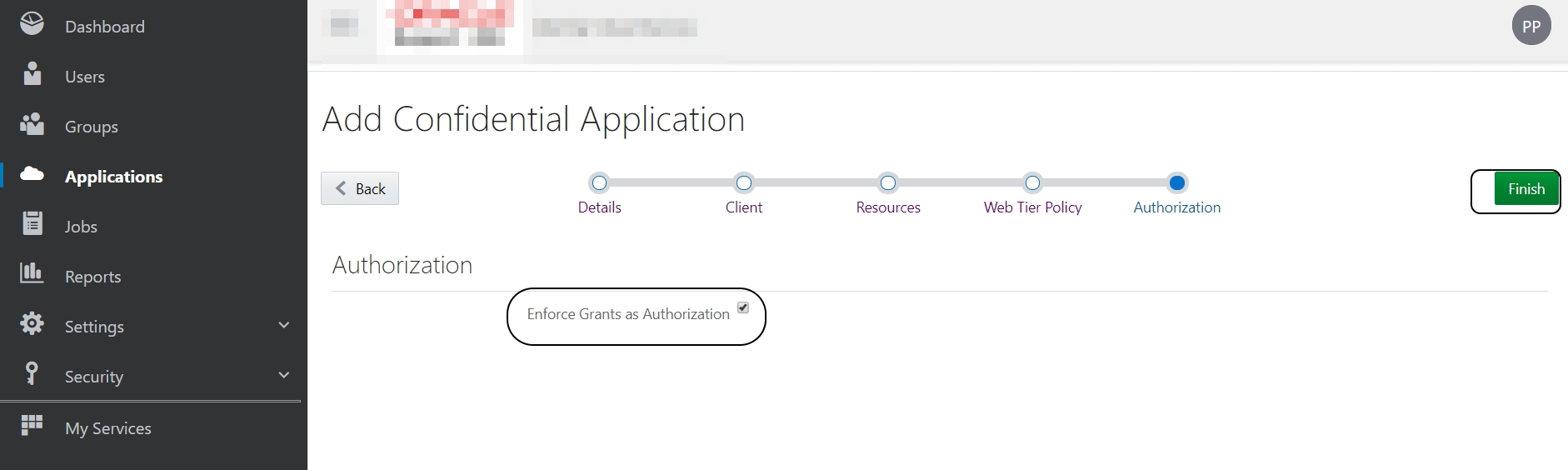
Select “Enforce Grants as Authorization” in the next section and Finish.
Make a NOTE of the “Client ID” and “Client Secret” from the pop window:
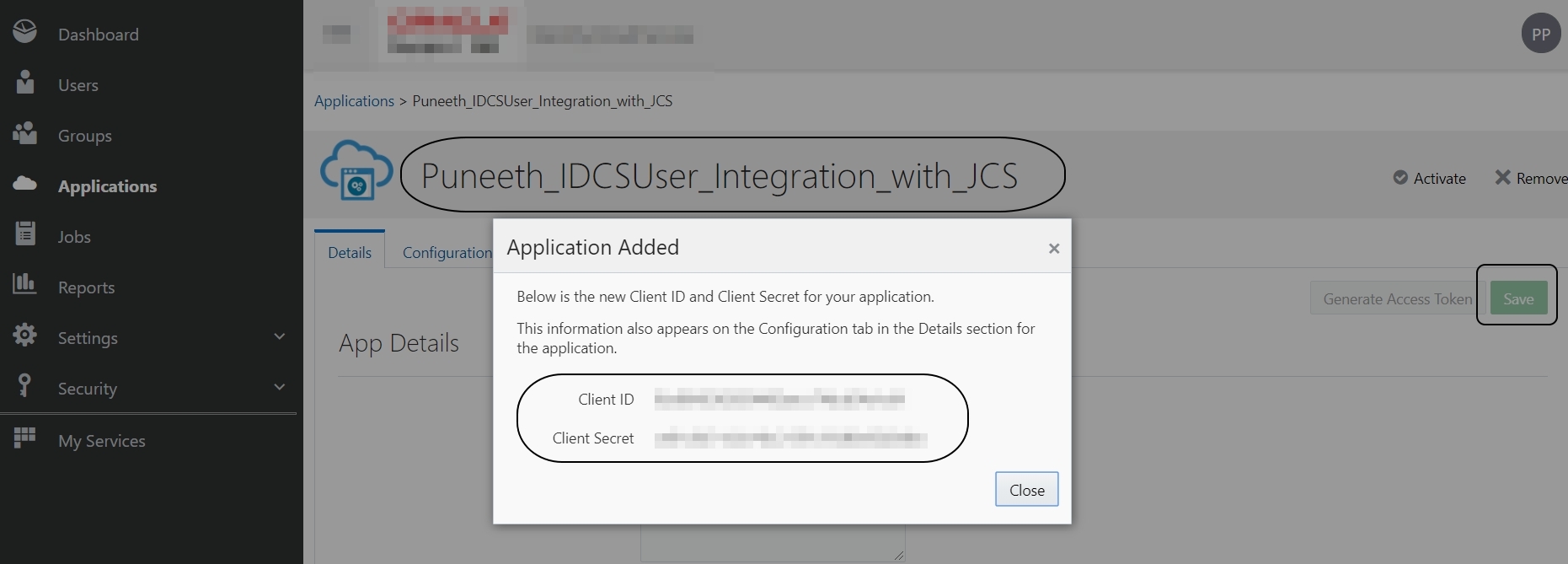
Close the pop-up window -> Save
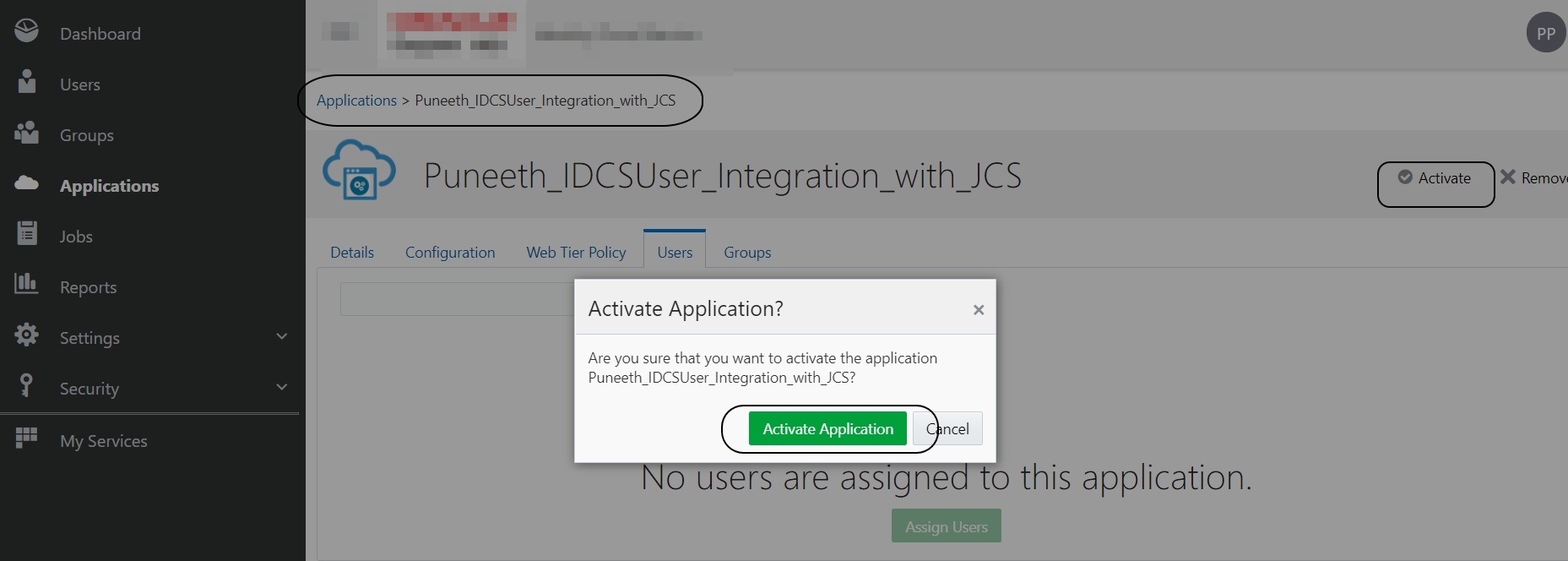
Activate -> Activate application:
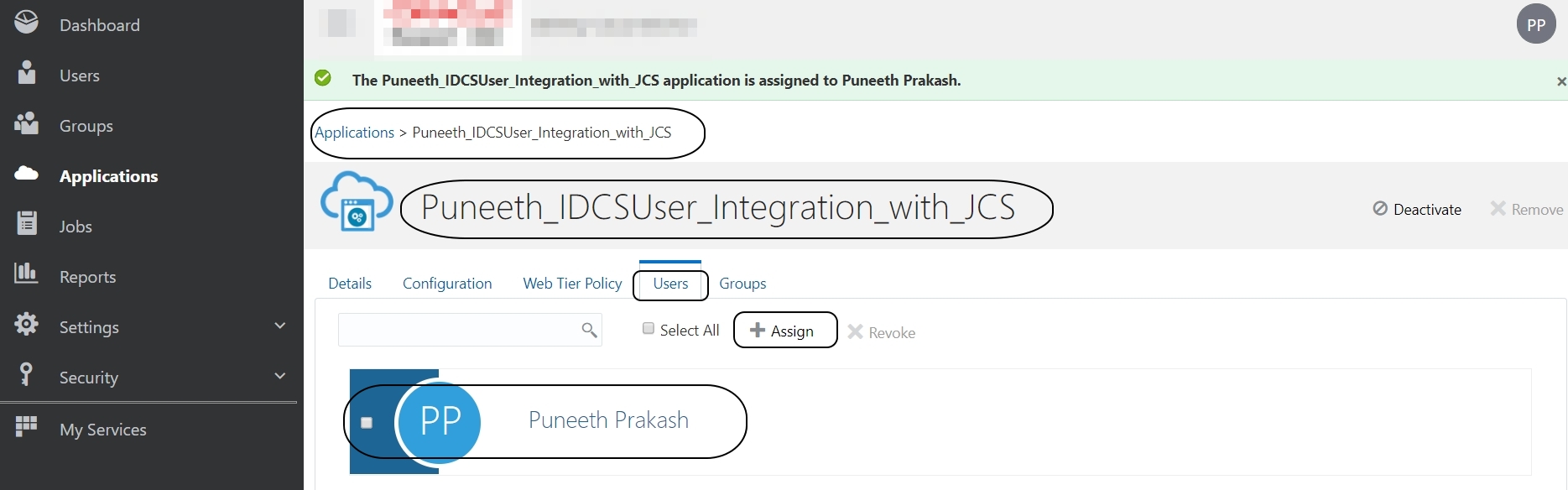
Go to Users tab and add users to this application:
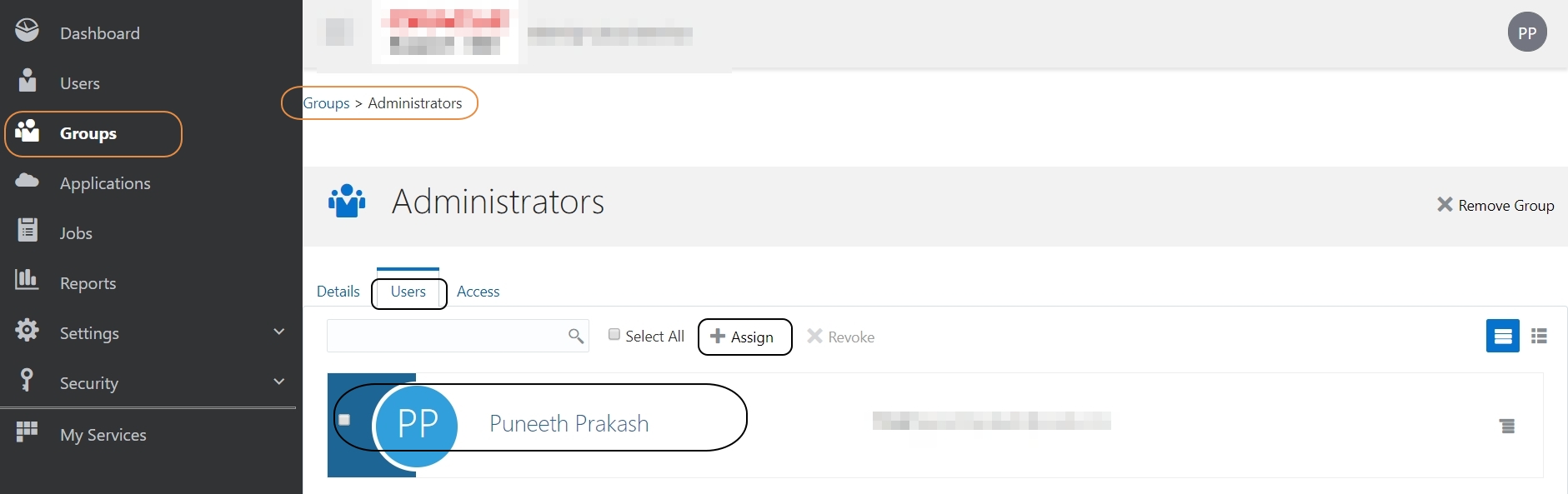
If you have a requirement to log in to Weblogic Admin console using IDCS Users, then you need to create a group in IDCS called “Administrators” and assign this user to that group:
Step 2:
Let’s configure “Oracle Identity Cloud Integrator provider” in Weblogic Admin console:
Login to Weblogic console -> Security Realms -> myrealm -> Providers -> OracleIdentityCloudIntegrator:
Make sure that the ControlFlag for DefaultAuthenticator is set to either “Sufficient” OR “Optional”
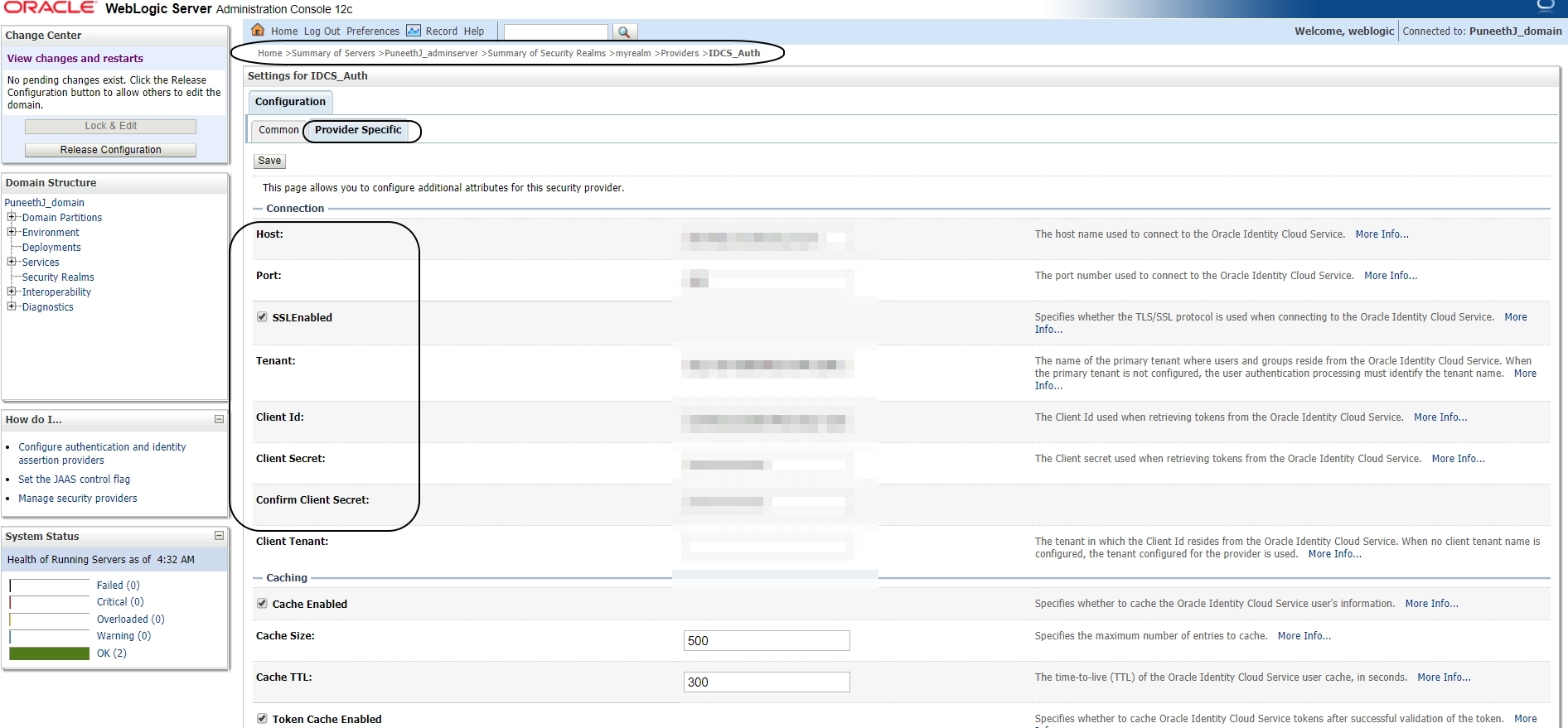
Click on the newly created IDCS provider -> ProviderSpecific tab and update the following:
Host:
Port:
SSL Enabled: Check
Tenant:
Client Id:
Client Secret:
Confirm Client Secret:
Login to IDCS console -> About page to get the above information:
Cloud Account name is of the format: https://xxx.identity.oraclecloud.com:443
Update the Info in IDCS provider accordingly:
Host: identity.oraclecloud.com
Port: 443
Instance GUID is: idcs-xxxx
Update this info in IDCS provider:
Tenant: idcs-xxxx
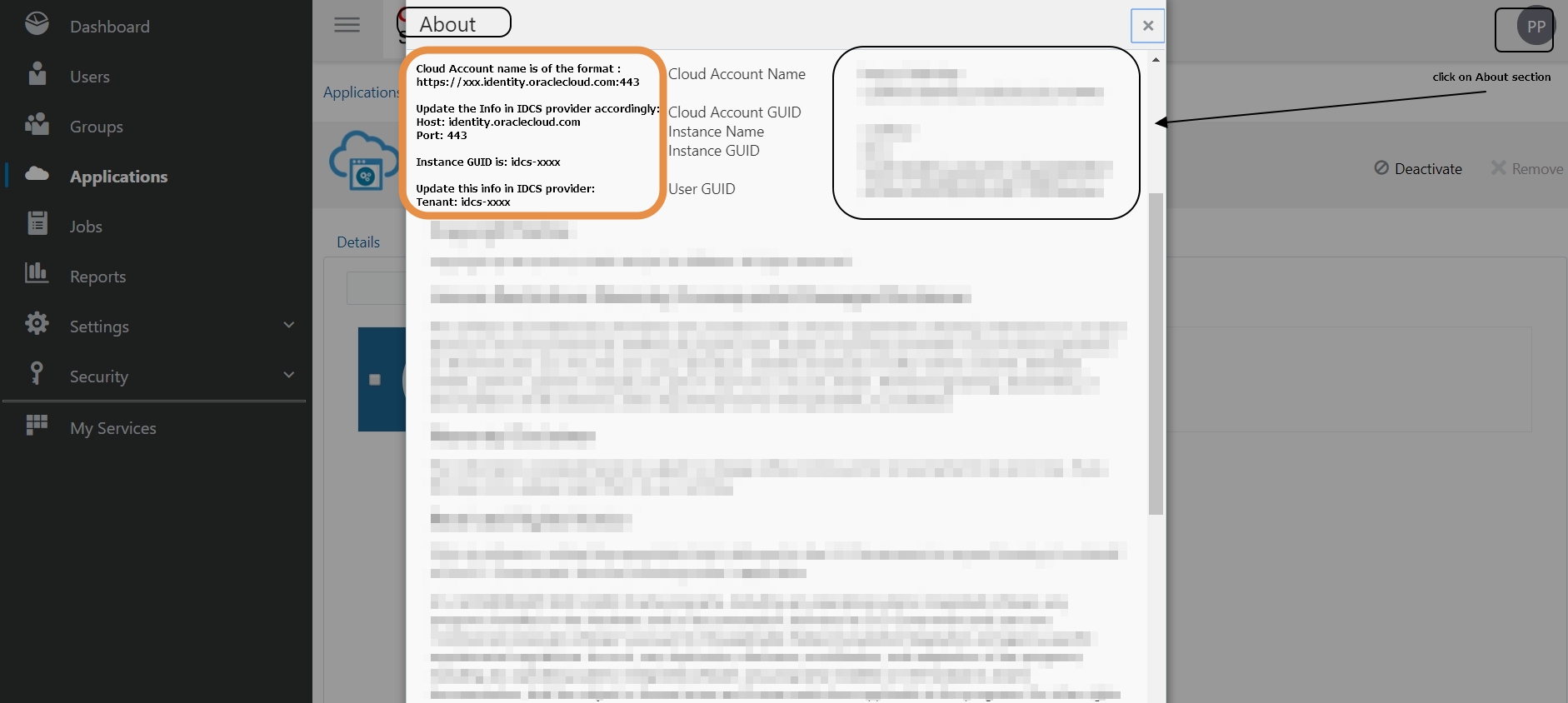
You can get the ClientId and ClientSecret from the application that you created in IDCS
Save the changes.
Restart JCS Instance.
Now login to Weblogic Admin console using IDCS user.
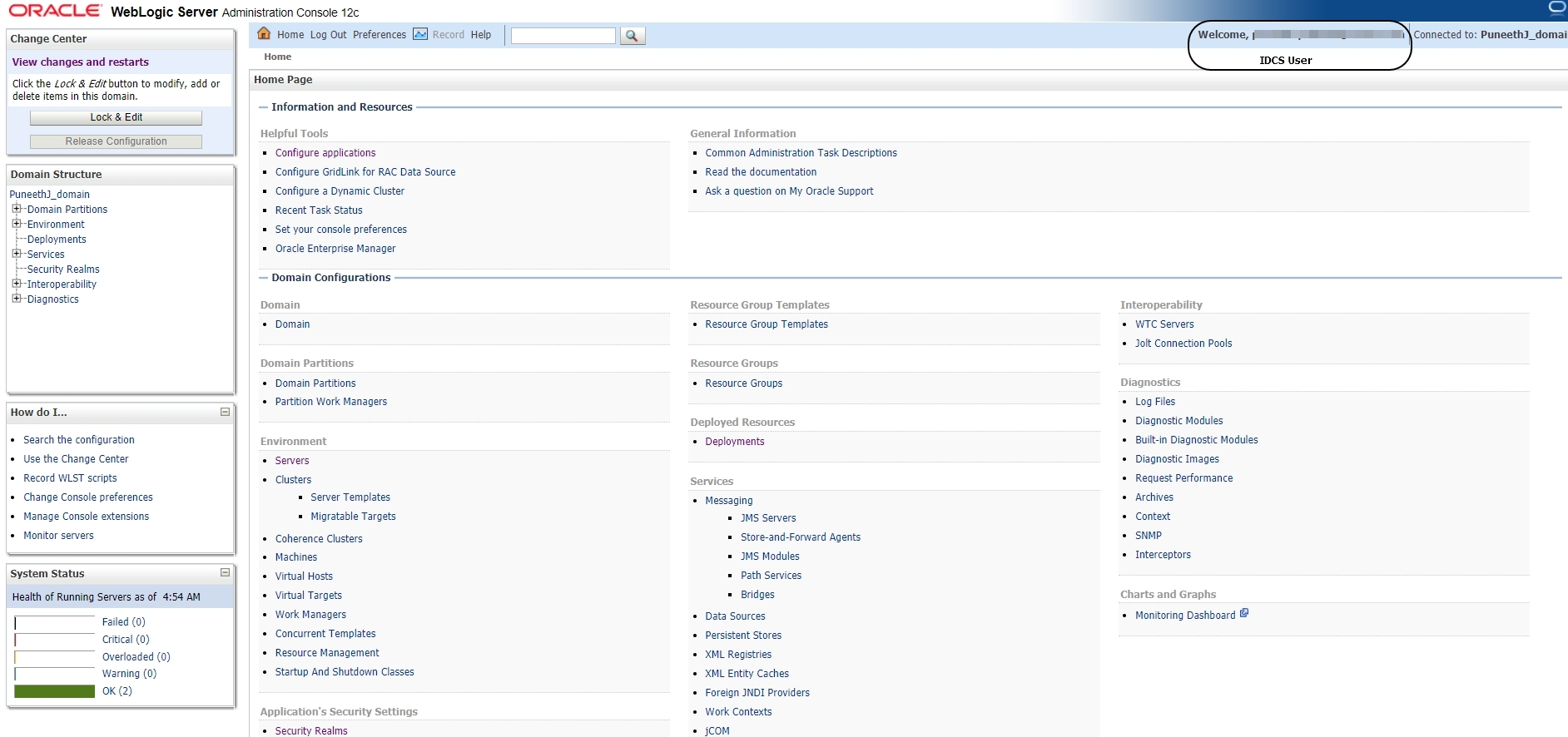
NOTE: Unlike other external LDAP configurations you will not be able to see the list of IDCS Users in the Security Realms -> myrealm -> Users and Groups tab.
—
<Additional Info>
Consider a scenario where-in you have WebLogic installed on an OCI instance and are trying to connect to IDCS using Oracle Identity Cloud Integrator provider.
In this case Weblogic default truststore will not have the root and intermediate certificates of IDCS and you may encounter the following error :
<May 5, 2021 7:19:05,639 AM GMT> <Debug> <SecurityAtn> <BEA-000000> <IDCS verify user request URL: null>
<May 5, 2021 7:19:05,640 AM GMT> <Debug> <SecurityAtn> <BEA-000000> <Failed to authenticate user: java.io.IOException: The endpoint URI was not obtained!
java.io.IOException: The endpoint URI was not obtained!
at weblogic.security.providers.authentication.IDCSUserAsserter.verifyUser(IDCSUserAsserter.java:327)
at weblogic.security.providers.authentication.IDCSUserAsserter.authenticateUser(IDCSUserAsserter.java:187)
at weblogic.security.providers.authentication.IDCSAtnDelegateImpl.authenticateUser(IDCSAtnDelegateImpl.java:123)
at weblogic.security.providers.authentication.IDCSAtnLoginModuleImpl.login(IDCSAtnLoginModuleImpl.java:366)
at com.bea.common.security.internal.service.LoginModuleWrapper$1.run(LoginModuleWrapper.java:117)
Download the root and intermediate certificates of IDCS from browser and import it to WLS trust store.
Also make sure that you have the hostname verification in WLS set to NONE or WildCard hostname verifier.
