Original Publish Date : 8/31/2015
In this post we will see how to configure OCSP based certificate revocation check in Weblogic Server :
– First we need to create a self-signed certificate and get it signed from an internal CA (created using openssl)
– Then create another self-signed certificate and get it signed from the same CA. Now lets revoke this certificate.
– Establish a two-way SSL communication between browser and WLS.
– Configure WLS to enable OCSP (Online Certificate Status Protocol) check.
– Connect to WLS using valid and revoked certificate and see the difference.
Step 1 :
– Install OpenSSL and modify the openssl.cfg file as follows :
authorityInfoAccess = OCSP;URI: http://host:port
Download sample openssl.cfg file HERE..!!
NOTE : Right Click on the above hyperlink and click on “Save Link As” – Now download the file and rename its extension to .zip.
Setup your shell/cmd prompt to use the openssl.cfg file :
Command :
Step 2 :
Create an Internal CA
Command :
./openssl req -nodes -new -x509 -keyout cakey.pem -out cacert.pem -days 3650

Step 3 :
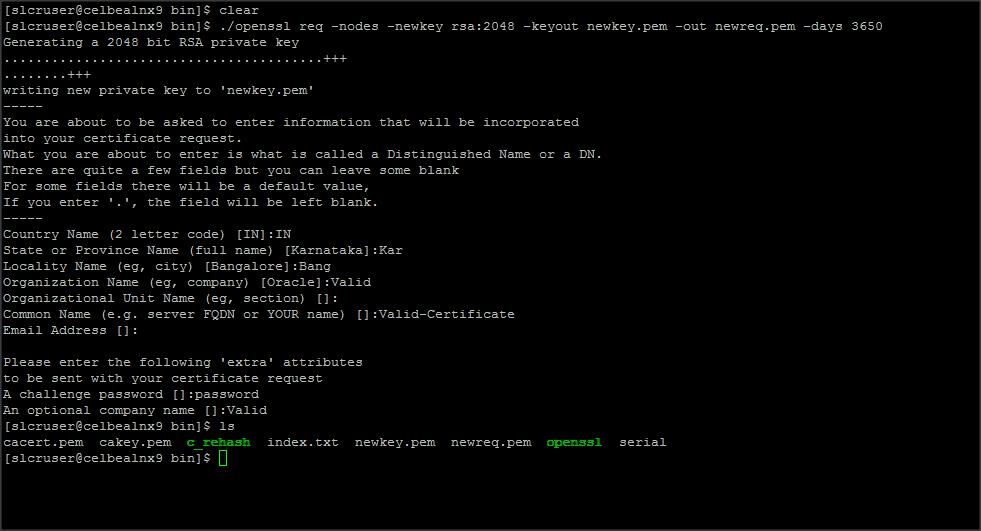
Create a certificate and get it signed by internal CA. (say Valid certificate)
Command :
./openssl req -nodes -newkey rsa:2048 -keyout newkey.pem -out newreq.pem -days 3650
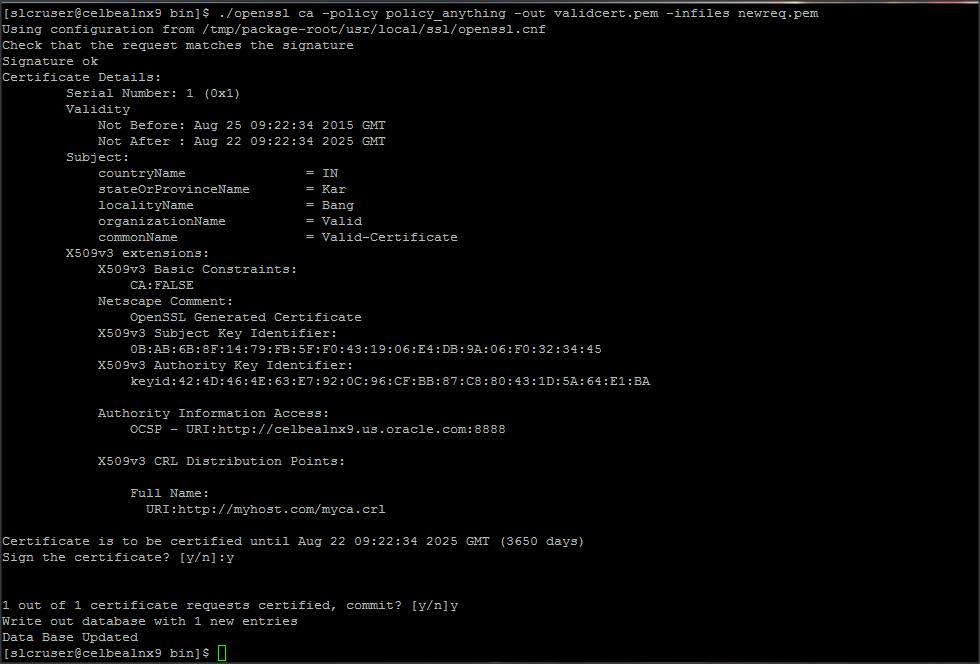
./openssl ca -policy policy_anything -out validcert.pem -infiles newreq.pem
Step 4 :
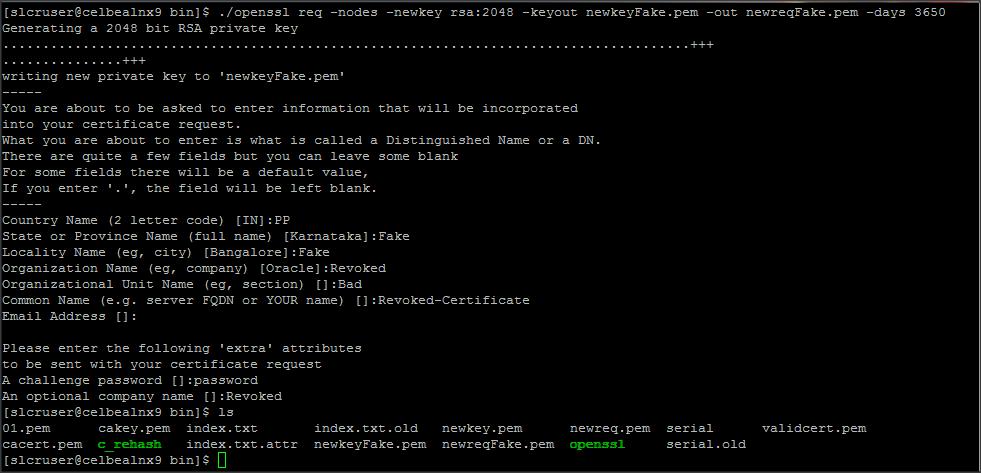
Create a certificate and get it signed by internal CA (say Revoked certificate).
Command :
./openssl req -nodes -newkey rsa:2048 -keyout newkeyFake.pem -out newreqFake.pem -days 3650
./openssl ca -policy policy_anything -out revokecert.pem -infiles newreqFake.pem
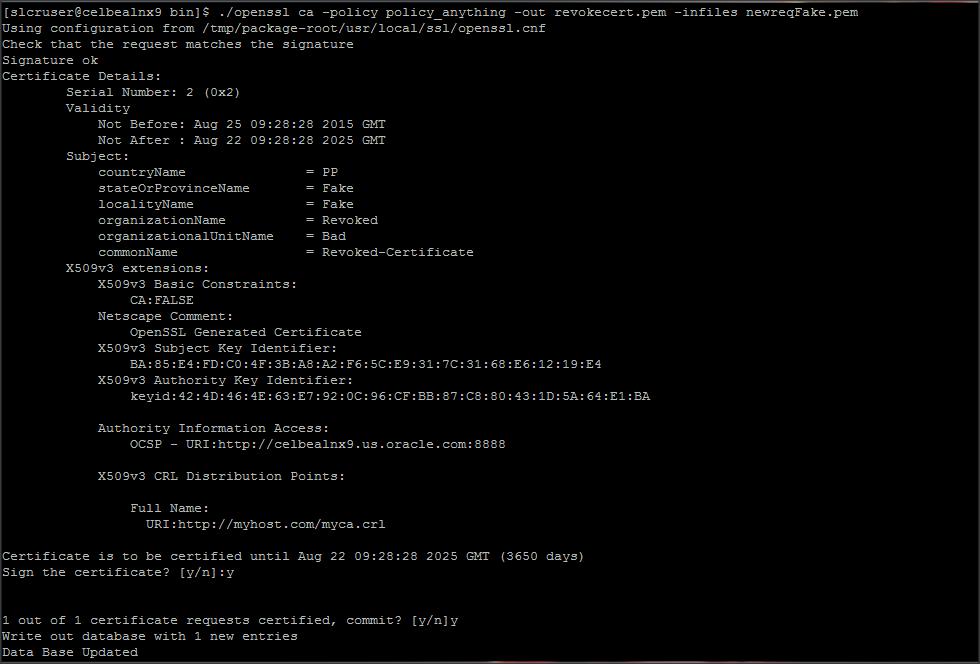
Lets revoke this certificate now :
Command :
./openssl ca -revoke revokecert.pem
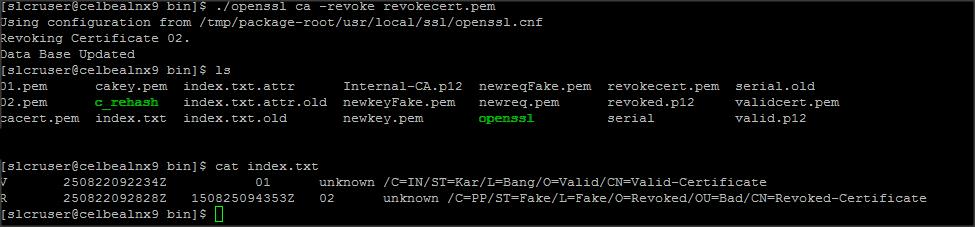
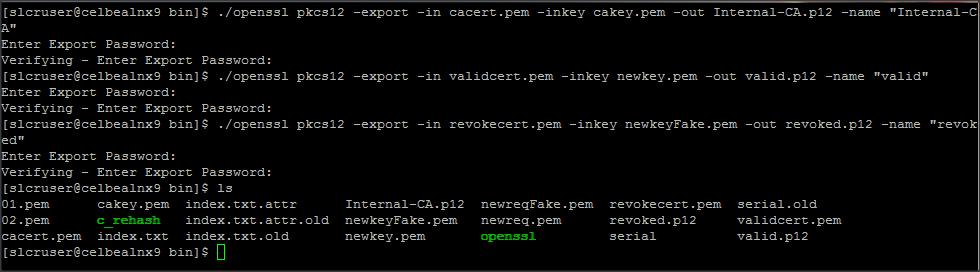
Create two .p12 keystore (valid keystore and revoked keystore) using the following command, this file will be used to configure certificates/keystore on the browser :
Command :
./openssl pkcs12 -export -in validcert.pem -inkey newkey.pem -out valid.p12 -name “valid”
./openssl pkcs12 -export -in revokecert.pem -inkey newkeyFake.pem -out revoked.p12 -name “revoked”
Step 5:
Start your OCSP server.
Command :
./openssl ocsp -index index.txt -CA cacert.pem -rsigner cacert.pem -rkey cakey.pem -port 8888
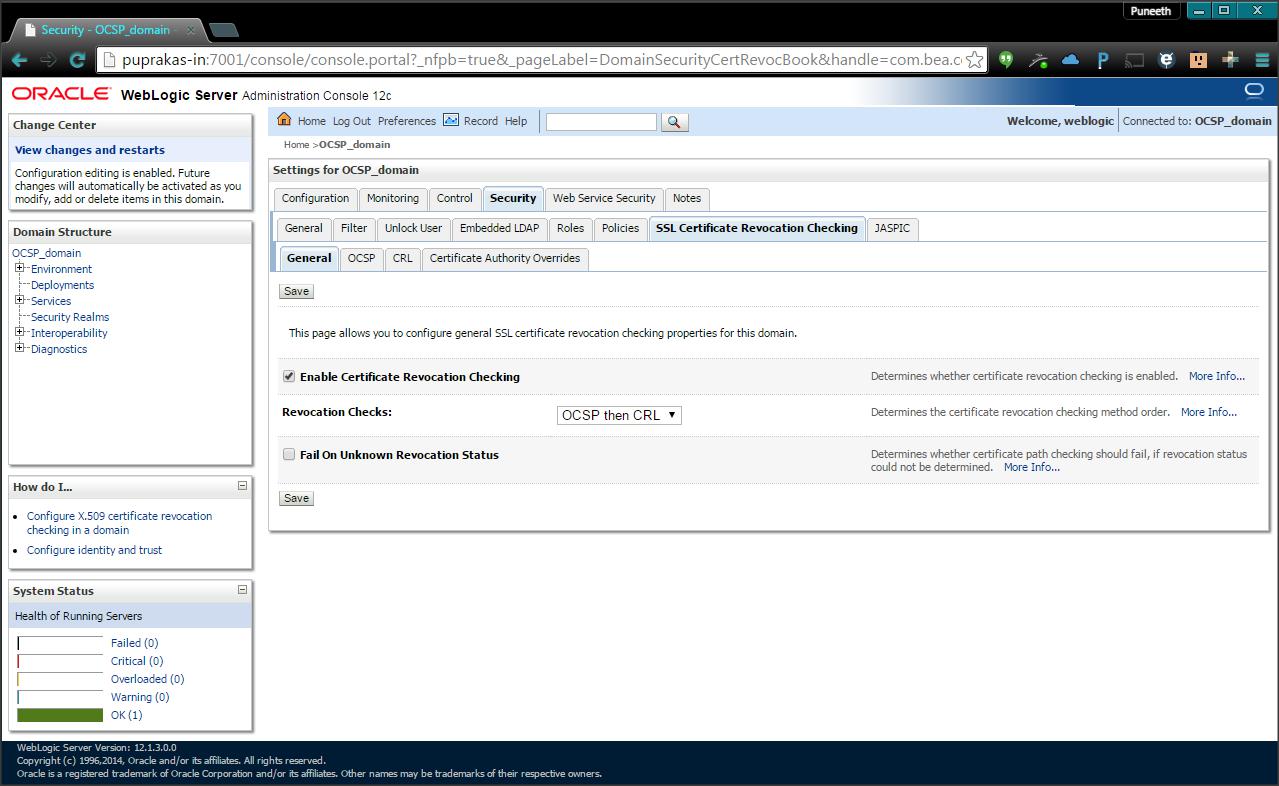
Step 6:
Configure Weblogic to enable OCSP based certificate Revocation Check.
Step 7 :
– Enable SSL (Demo Identity and Demo Trust will be configured by default) on Weblogic and enable Two-WAY SSL (client-cert requested and enforced)
Login to console -> +Environment -> Servers -> AdminServer -> General -> SSL Listen port Enabled (check)
Login to console -> +Environment -> Servers -> AdminServer -> SSL -> +Advanced -> Two Way Client Cert Behavior -> select “Client Certs Requested and Enforced ” from the drop down menu.
– Enable Certificate Revocation Debugs :
Login to console -> +Environment -> Servers -> AdminServer ->Debug -> +weblogic -> +security -> certrevocationchecking (enable)
– Make sure you increase the logging severity to DEBUG :
Login to console -> +Environment -> Servers -> AdminServer ->Logging -> +Advanced ->
Log file : Severity level : Debug
Standard out : Severity level : Debug
Step 8 :
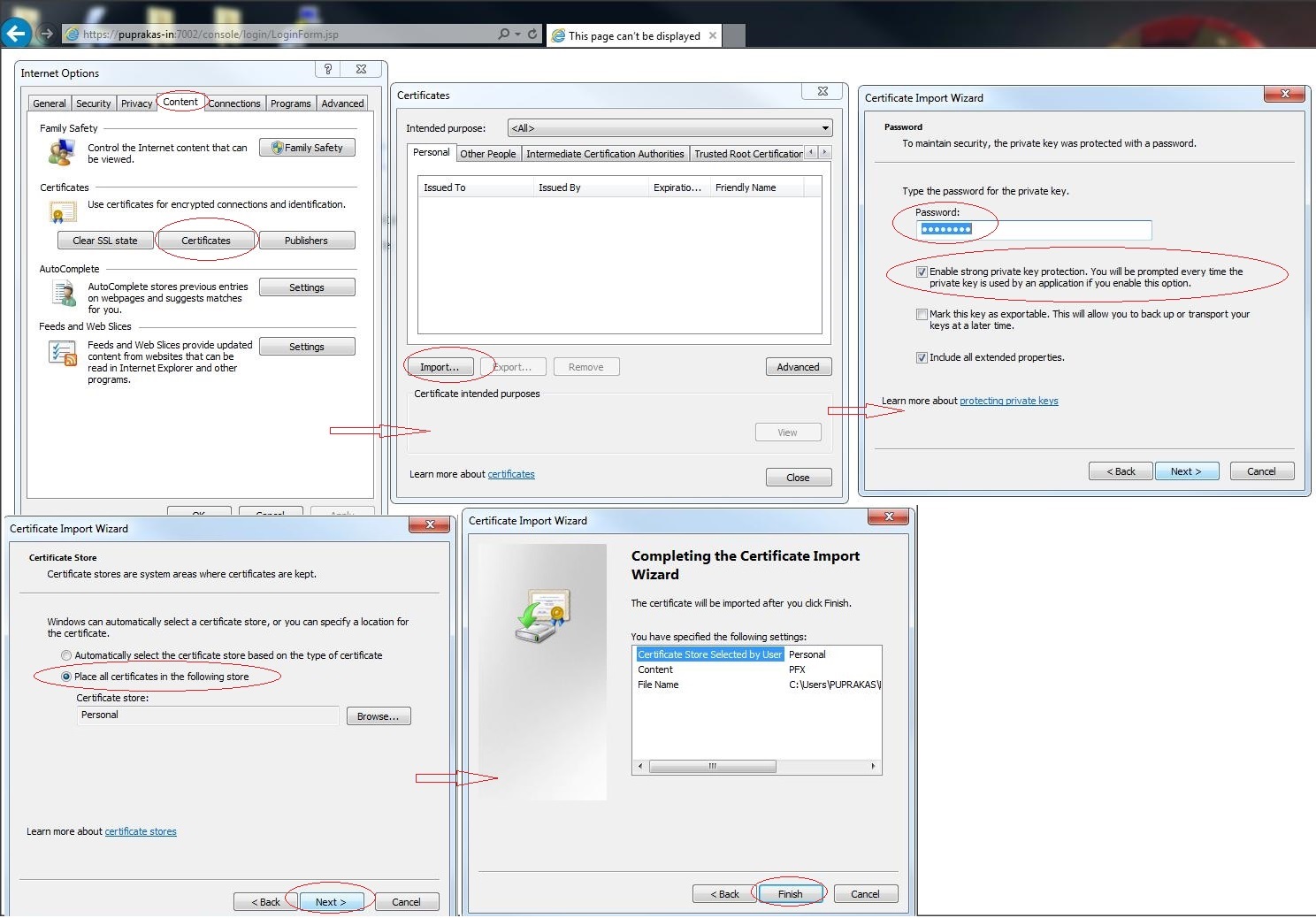
Configure a certificate signed by internal CA on your browser and access Weblogic console.
1) First configure the valid .p12 keystore –> access the console over SSL and check the Weblogic logs
2) Now delete the valid certificate.keystore from IE and configure Revoked .p12 keystore –> access the console over SSL and check the Weblogic logs
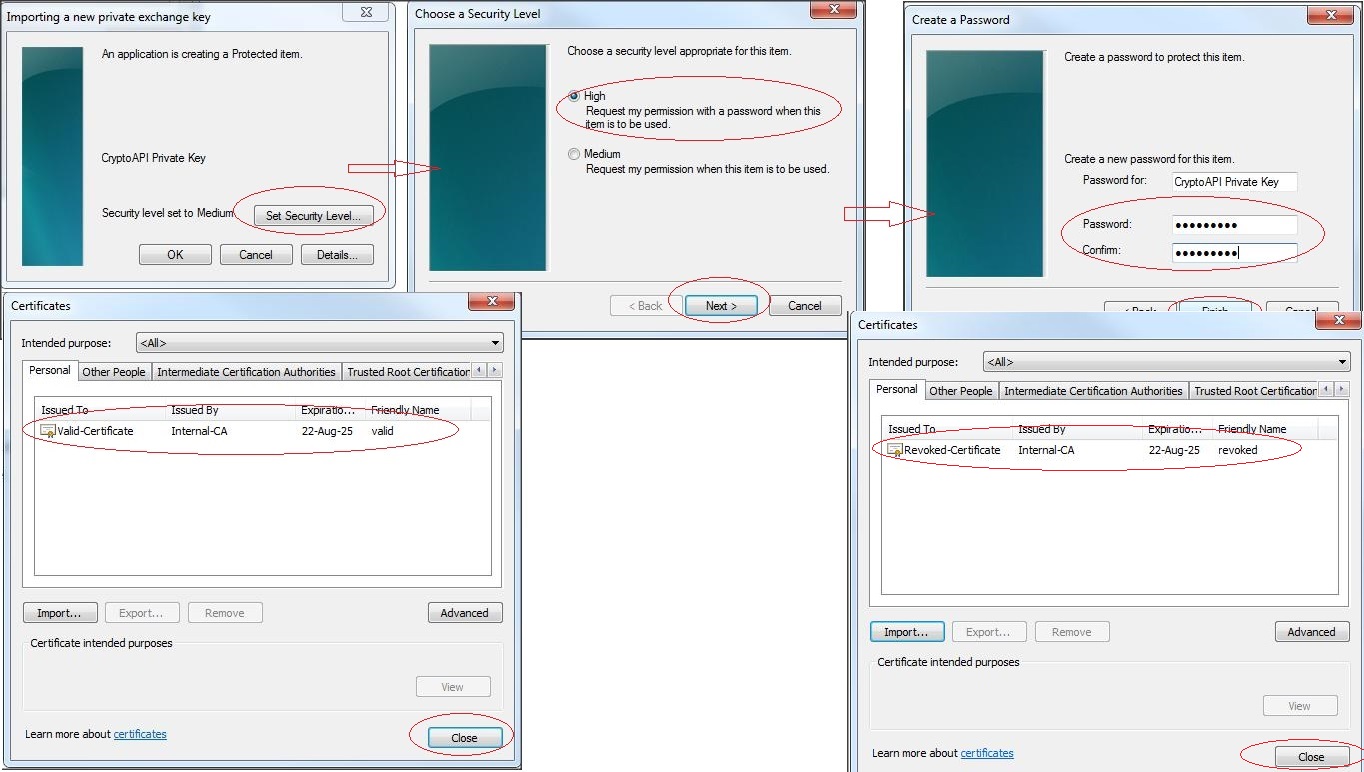
NOTE :
– After successfully configuring Two-Way SSL on Weblogic Admin Server and browser (IE) –> Access WLS console over https. You should see the following :
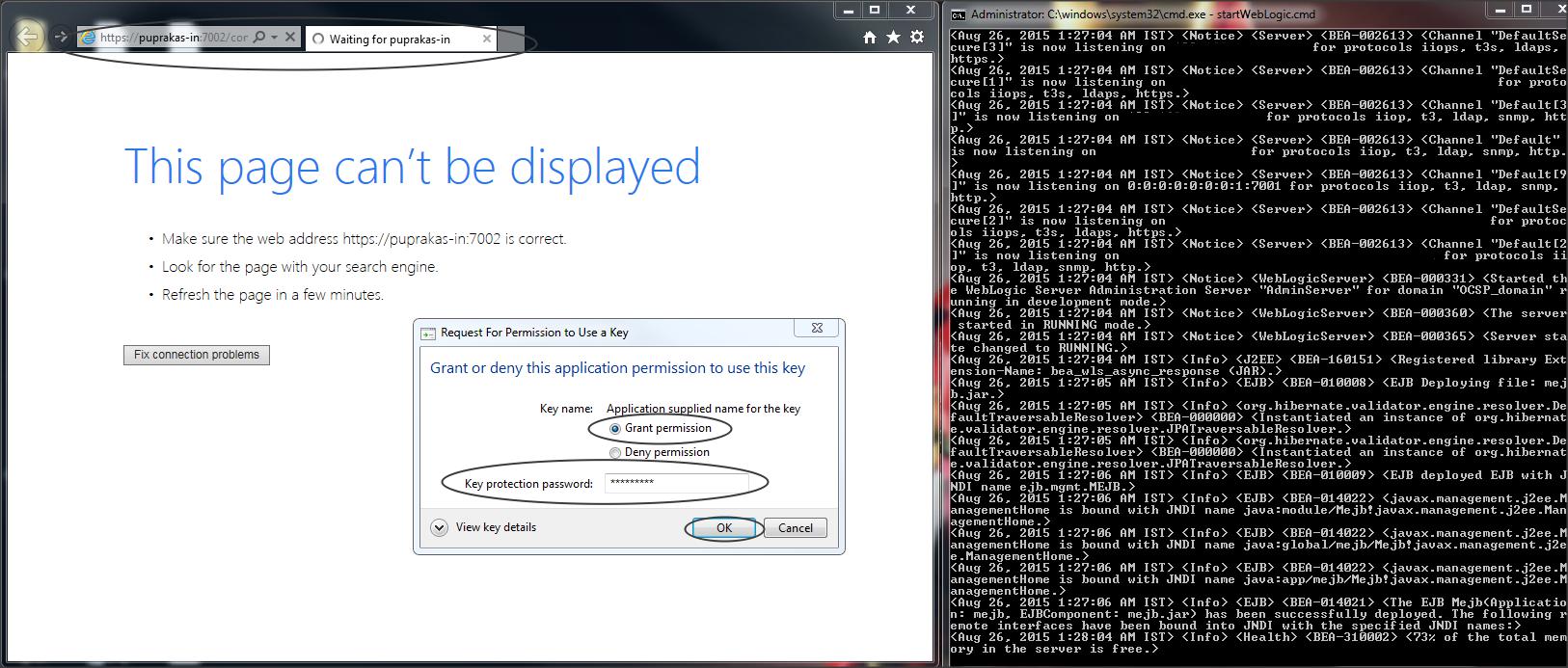
NOTE :
– Configure a valid .p12 keystore on IE and access the Weblogic console on Https, you will see the following logging in out file :
Status=NOT REVOKED
Source=OCSP
Subject=”CN=Valid-Certificate,O=Valid,L=Bang,ST=Kar,C=IN”
Issuer=”CN=Internal-CA,OU=Weblogic,O=Oracle,L=Bangalore,ST=Karnataka,C=IN”
SerialNumber=1
StatusValid=Tue 25 Aug 2015 16:08:39.000 +0530
StatusExpires=null
NonceIgnored=false
RevocationTime=null
ReasonCode=null
Flags=0
ProducedAt=Tue 25 Aug 2015 16:08:39.000 +0530
.>
<Aug 26, 2015 1:36:50 AM IST> <Info> <Security> <BEA-090914> <Certificate revoca
tion status:
Status=NOT REVOKED
Source=OCSP
Subject=”CN=Valid-Certificate,O=Valid,L=Bang,ST=Kar,C=IN”
Issuer=”CN=Internal-CA,OU=Weblogic,O=Oracle,L=Bangalore,ST=Karnataka,C=IN”
SerialNumber=1
StatusValid=Tue 25 Aug 2015 16:08:39.000 +0530
StatusExpires=null
NonceIgnored=false
RevocationTime=null
ReasonCode=null
Flags=0
ProducedAt=Tue 25 Aug 2015 16:08:39.000 +0530
>
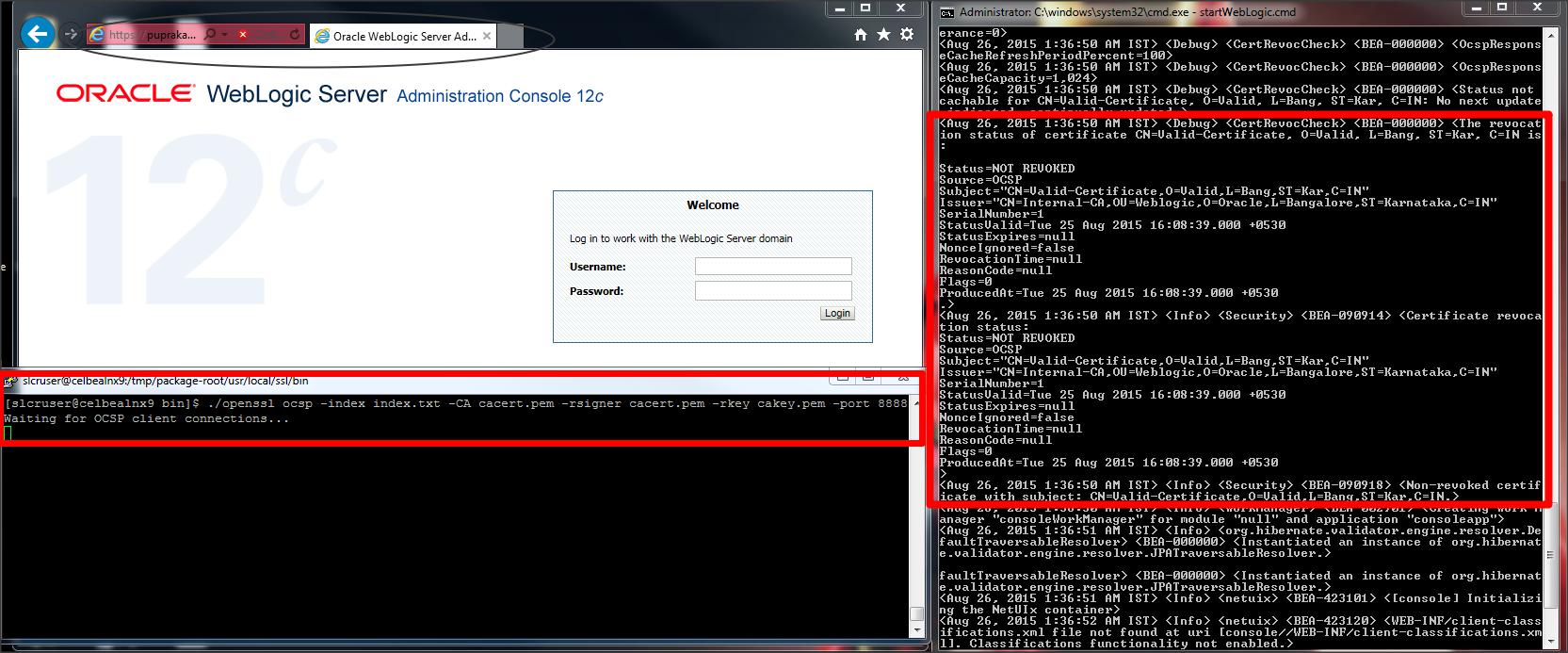
NOTE :
– Configure a revoked .p12 keystore on IE and access the Weblogic console on Https, you will see the following logging in out file :
Status=REVOKED
Source=OCSP
Subject=”CN=Revoked-Certificate,OU=Bad,O=Revoked,L=Fake,ST=Fake,C=PP”
Issuer=”CN=Internal-CA,OU=Weblogic,O=Oracle,L=Bangalore,ST=Karnataka,C=IN”
SerialNumber=2
StatusValid=Tue 25 Aug 2015 16:03:41.000 +0530
StatusExpires=null
NonceIgnored=false
RevocationTime=Tue 25 Aug 2015 15:13:53.000 +0530
ReasonCode=-1
Flags=0
ProducedAt=Tue 25 Aug 2015 16:03:41.000 +0530
.>
<Aug 26, 2015 1:31:51 AM IST> <Info> <Security> <BEA-090914> <Certificate revoca
tion status:
Status=REVOKED
Source=OCSP
Subject=”CN=Revoked-Certificate,OU=Bad,O=Revoked,L=Fake,ST=Fake,C=PP”
Issuer=”CN=Internal-CA,OU=Weblogic,O=Oracle,L=Bangalore,ST=Karnataka,C=IN”
SerialNumber=2
StatusValid=Tue 25 Aug 2015 16:03:41.000 +0530
StatusExpires=null
NonceIgnored=false
RevocationTime=Tue 25 Aug 2015 15:13:53.000 +0530
ReasonCode=-1
Flags=0
ProducedAt=Tue 25 Aug 2015 16:03:41.000 +0530
>
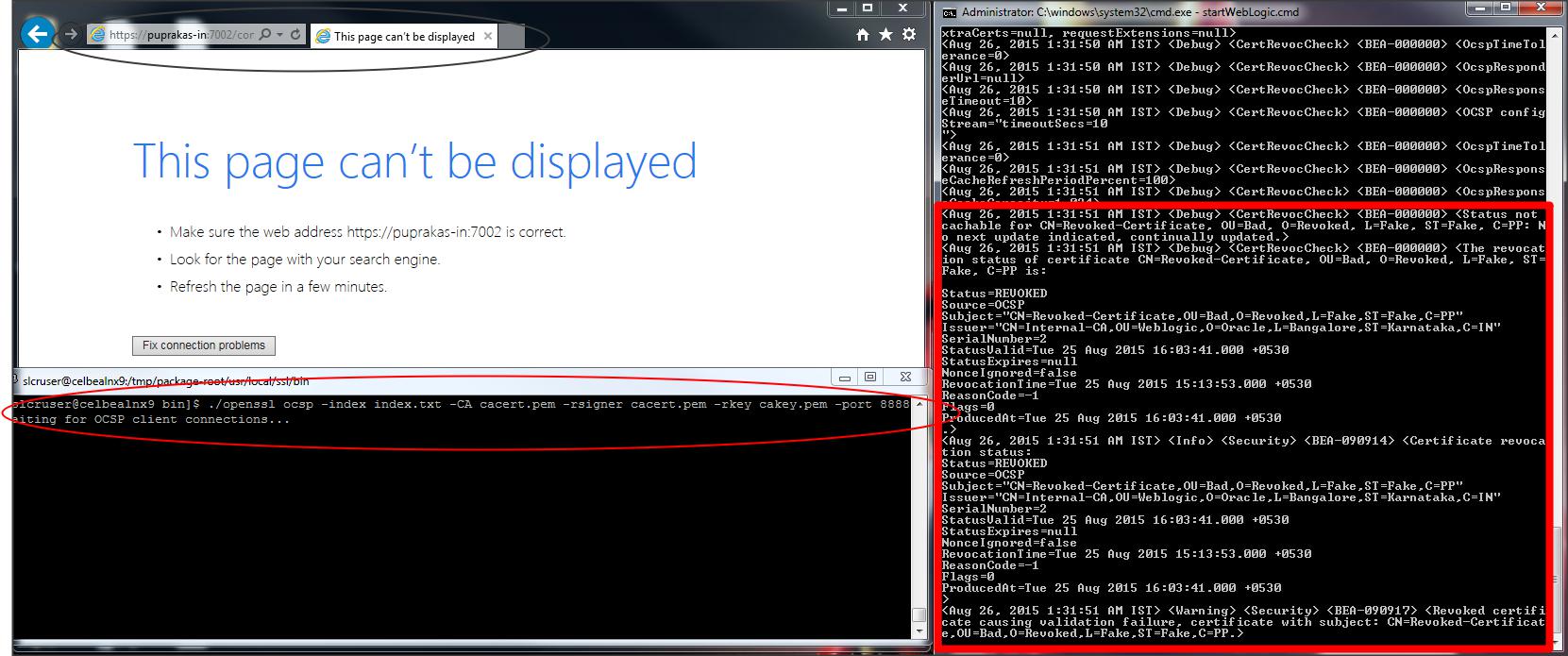
NOTE :
When your ocsp server is down you will see the following in Weblogic Server logs and both valid and revoked keystore will be accepted by Weblogic.
<Aug 26, 2015 1:40:19 AM IST> <Debug> <CertRevocCheck> <BEA-000000> <Exception while checking revocation status using OCSP.
com.rsa.certj.spi.revocation.CertStatusException: com.rsa.certj.spi.pki.PKIException: OCSP.SendOCSPRequest: Tried all: ‘1’ addresses, but could not connect over
HTTP to server: ‘celbealnx9.us.oracle.com’, port: ‘8888’
at com.rsa.certj.provider.revocation.ocsp.OCSP$Implementation.checkCertRevocations(OCSP.java:705)
at com.rsa.certj.provider.revocation.ocsp.OCSP$Implementation.checkCertRevocation(OCSP.java:592)
at com.rsa.certj.CertJ.checkCertRevocation(CertJ.java:1270)
at weblogic.security.pki.revocation.common.DefaultOcspChecker.checkCertRevocation(DefaultOcspChecker.java:737)
at weblogic.security.pki.revocation.common.DefaultOcspChecker.getRemoteStatus(DefaultOcspChecker.java:133)
at weblogic.security.pki.revocation.common.OcspChecker.getCertRevocStatus(OcspChecker.java:93)
at weblogic.security.pki.revocation.common.RevocationCertPathChecker.runThruMethods(RevocationCertPathChecker.java:279)
at weblogic.security.pki.revocation.common.RevocationCertPathChecker.check(RevocationCertPathChecker.java:185)
NOTE :
– In the above example I am using browser as SSL client to demonstrate OCSP feature in WLS.
– But you can use any Java standalone client to connect to Weblogic and initiate a two-way SSL to demonstrate the above behavior
Example :
java -Djavax.net.ssl.keyStoreType=jks -Djavax.net.ssl.trustStoreType=jks -Djavax.net.ssl.keyStore=valid.jks -Djavax.net.ssl.trustStore=trust.jks -Djavax.net.debug=ssl -Djavax.net.ssl.keyStorePassword=password -Djavax.net.ssl.trustStorePassword=password -cp . TwoWaySSLClient
