CertGenCAB was the Certificate Authority that signed the Demo Certificates used by WLS.
This CA certificate expired on Oct 25 2022 and hence all Demo keystores are no longer valid.
This blog has more information on how to overcome this issue.
Background:
- Before 10.3.3 (11g), Certicom SSL was the only SSL implementation.
- In 10.3.3 thru 10.3.6 (11g), Certicom SSL is the default SSL implementation, with JSSE available by enabling a property switch.
- In 12.1.1 and up (12c), JSSE is the default SSL implementation and Certicom was removed.
- Weblogic Server versions 10.3.6 and 12.1.1 and later are certified with JDK 7
- TLS 1.1 and 1.2 is only supported with a combination of JDK 7 Update 1 (or later) and JSSE enabled
- With JSSE and JDK 7, higher security defaults are available (e.g updated ciphers)
NOTE:
DO NOT use the demonstration keystores in a Production Environment.
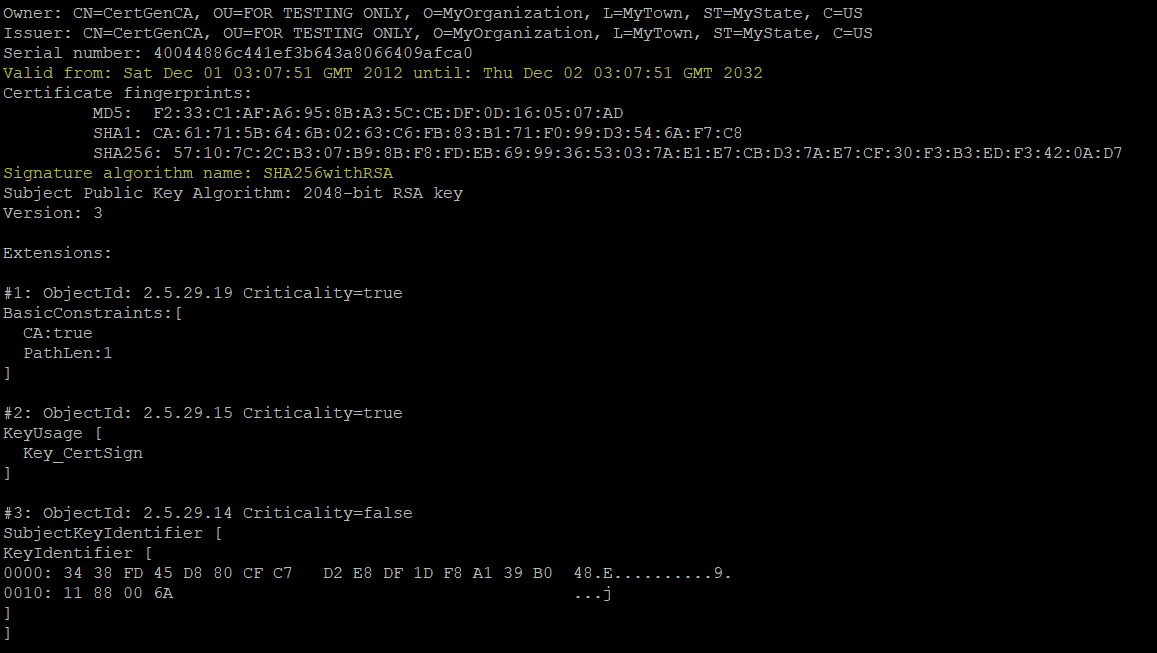
Oracle released Patch 13964737 that updates Signing Authority from CertGenCAB to CertGenCA.
- Patch 13964737 is available for WLS 10.3.6 and 12.1.1
- This patch is not required for WLS 12.1.3 and above. You can directly create new DemoIdentity and DemoTrust keystores.
Old CA :
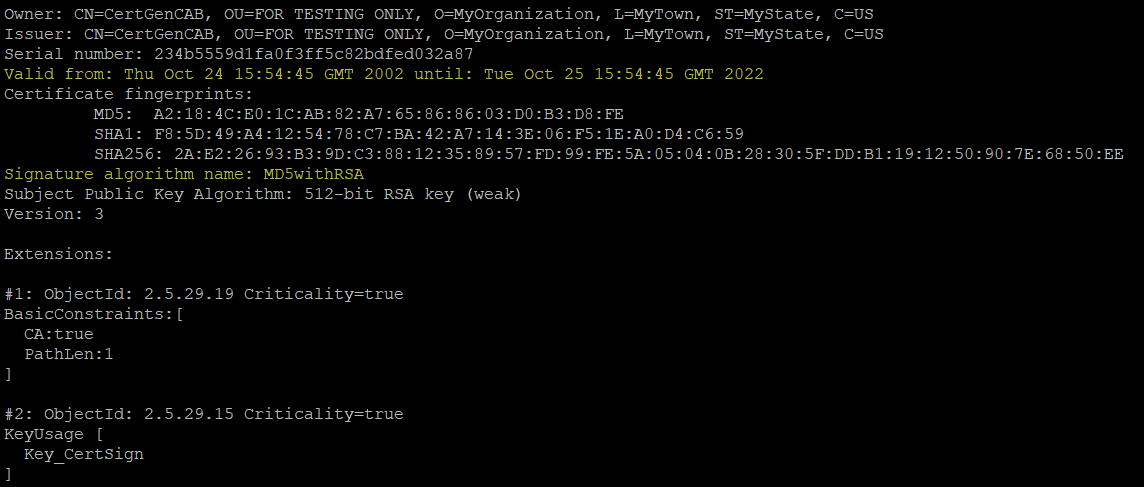
New CA :
Below are the steps to be performed on different WebLogic versions to overcome the issue of expiring Demonstration Certificate Authorities :
| WLS Version | JDK Version | SSL Implementation | Apply Patch | Suggested Action Plan |
| WLS 8.x | Any supported JDK | Certicom (Default) | NA | OPTION 1: Create Self Signed Certificates and configure Custom Identity and Custom Trust OPTION 2: Disable SSL on WebLogic Server. NOTE:There is no way to disable SSL on nodemanager for WLS 8.x |
| WLS 9.x | Any supported JDK | Certicom (Default) | NA | OPTION 1: Create Self Signed Certificates and configure Custom Identity and Custom Trust OPTION 2: Disable SSL on WebLogic Server. |
| WLS 10.3.6 | JDK 1.6 / JDK 1.7 | Certicom (Default) | Do Not apply patch. |
OPTION 1: Create Self-Signd Certificates and configure Custom Identity and Custom Trust OPTION 2: Disable SSL on Nodemanager and WebLogic Server |
| WLS 10.3.6 | JDK 1.7 | JSSE | Apply patch 13964737 | OPTION 1: Recreate DemoIdentity and DemoTrust :- Apply patch 13964737 and regenerate DemoIdentity.jks as mentioned in KM 1392455.1 OPTION 2: Create new SelfSigned Certificates (You could also use CA signed certificates) and configure Custom Identity and Custom Trust OPTION 3: Disable SSL on NodeManager and WebLogic Server |
| WLS 12.1.1 | Any supported JDK | JSSE (Default) | Apply Patch 13964737 | OPTION 1: Recreate DemoIdentity and DemoTrust :- Apply patch 13964737 and regenerate DemoIdentity.jks as mentioned in KM 1392455.1 OPTION 2: Create new SelfSigned Certificates (You could also use CA signed certificates) and configure Custom Identity and Custom Trust OPTION 3: Disable SSL on NodeManager and WebLogic Server |
| 12.1.3 and above | Any supported JDK | JSSE (Default) | NA | OPTION 1: Recreate DemoIdentity and DemoTrust :- Regenerate DemoIdentity.jks as mentioned in KM 1392455.1 OPTION 2: Create new SelfSigned Certificates (You could also use CA signed certificates) and configure Custom Identity and Custom Trust OPTION 3: Disable SSL on NodeManager and WebLogic Server |
For WLS 8.1 :
OPTION 1: Create Self Signed Certificates and configure Custom Identity and Custom Trust
Step 1:
Go to <WL_HOME>/server/bin/
Run
Linux : . ./setWLSEnv.sh
Windows : setWLSEnv.cmd
Then run “java -version” and make sure it is the same java being used by your WebLogic Server.
Example :
Step 2:
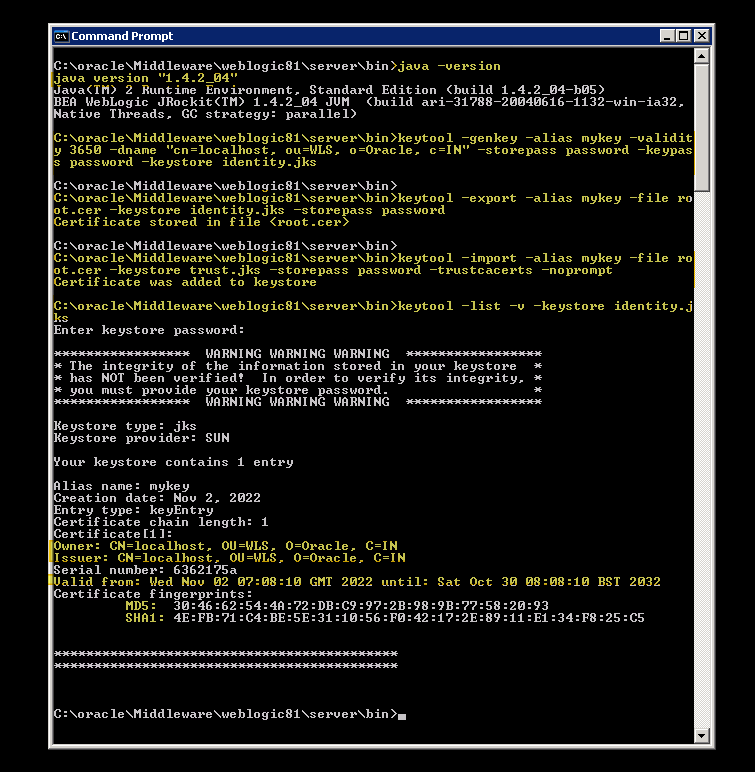
Create a Self-Signed certificate using the following command :
keytool -genkey -alias mykey -validity 3650 -dname “cn=localhost, ou=WLS, o=Oracle, c=IN” -storepass password -keypass password -keystore identity.jks
keytool -export -alias mykey -file root.cer -keystore identity.jks -storepass password
keytool -import -alias mykey -file root.cer -keystore trust.jks -storepass password -trustcacerts -noprompt
NOTE:
– Replace the cn in the above command to your servers hostname. (Specified in console -> server listen_address field).
– You also change the storepass and keypass values in the above commands.
– The above commands will generate identity.jks and trust.jks which can be used to configure SSL on your nodemanager and WebLogic servers.
– The certificate generated should have a signature algorithm as MD5withSHA1
Step 3:
Now configure the NodeManager and WebLogic servers to use this newly created identity.jks and trust.jks
OPTION 2: Disable SSL on WebLogic Server. There is no way to disable SSL on nodemanager for WLS 8.x (Not Recommended)
For WLS 10.3.6 :
The default SSL implementation in Weblogic 10.3.6 is Certicom, but WLS 10.3.6 also supports JSSE SSL Implmentation.
For WLS 1036 domains using JSSE SSL Implemenatations :
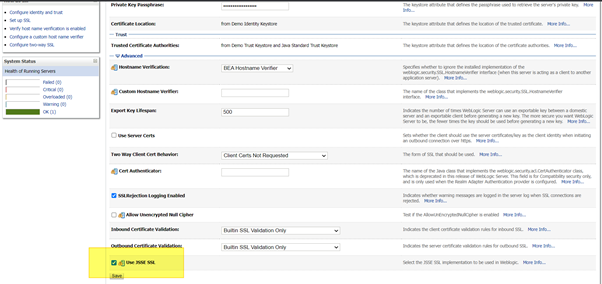
OPTION 1: Recreate DemoIdentity and DemoTrust :
Step 1:
Apply patch 13964737 and regenerate DemoIdentity.jks as mentioned in the below KM articles :
How to Renew Demo Trust Certificate in WLS that Expires on Oct 25 2022 (Doc ID 2901612.1)
Regenerating DemoIdentity.jks and/or DemoTrust.jks (Doc ID 1392455.1)
OPTION 2: Create new SelfSigned Certificates (You could also use CA signed certificates) and configure Custom Identity and Custom Trust :
Step 1:
Create a Self-Signed certificate using the following command :
keytool -genkeypair -alias mykey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -dname “cn=localhost, ou=WLS, o=Oracle, c=IN” -storepass password -keypass password -keystore identity.jks
keytool -export -alias mykey -file root.cer -keystore identity.jks -storepass password
keytool -import -alias mykey -file root.cer -keystore trust.jks -storepass password -trustcacerts -noprompt
NOTE:
– Replace the cn in the above command to your servers hostname. (Specified in console -> server listen_address field).
– You also change the storepass and keypass values in the above commands.
– The above commands will generate identity.jks and trust.jks which can be used to configure SSL on your nodemanager and WebLogic servers.
Step 2:
Configure nodeManager and WebLogic server to use this newly created identity.jks and trust.jks
OPTION 3: Disable SSL on NodeManager and WebLogic Server (Not Recommended)
For WLS 1036 domains using the default Certicom SSL Implementations :
NOTE : Applying patch 13964737 and recreating the DemoIdentity as mentioned in KM 1392455.1 creates SHA256withRSA certificate, which is not supported on Certicom. So there is no point in applying the patch if JSSE is not enabled in your WLS 1036 domain.
OPTION 1: Create Self-Signd Certificates and configure Custom Identity and Custom Trust
Step 1:
Go to <WL_HOME>/server/bin/
Run
Linux : . ./setWLSEnv.sh
Windows : setWLSEnv.cmd
Then run “java -version” and make sure it is the same java being used by your WebLogic Server.
Example :
Step 2:
Create a Self-Signed certificate using the following command :
keytool -genkey -alias mykey -validity 3650 -keyalg RSA -sigalg MD5withRSA -dname “cn=localhost, ou=WLS, o=Oracle, c=IN” -storepass password -keypass password -keystore identity.jks
keytool -export -alias mykey -file root.cer -keystore identity.jks -storepass password
keytool -import -alias mykey -file root.cer -keystore trust.jks -storepass password -trustcacerts -noprompt
NOTE:
– Replace the cn in the above command to your servers hostname. (Specified in console -> server listen_address field).
– You also change the storepass and keypass values in the above commands.
– The above commands will generate identity.jks and trust.jks which can be used to configure SSL on your nodemanager and WebLogic servers.
– The certificate generated should have a signature algorithm as MD5withRSA. (if you are using an older JDK 1.6 version)
OPTION 2: Disable SSL on Nodemanager and WebLogic Server (Not Recommended)
For WLS 12.1.3 and above :
The default SSL implementation is JSSE.
OPTION 1 : Recreate DemoIdentity and DemoTrust :
Step 1:
How to Renew Demo Trust Certificate in WLS that Expires on Oct 25 2022 (Doc ID 2901612.1)
Regenerating DemoIdentity.jks and/or DemoTrust.jks (Doc ID 1392455.1)
OPTION 2: Create new SelfSigned Certificates (You could also use CA Signed certificates) and configure Custom Identity and Custom Trust:
Step 1:
Create a Self-Signed certificate using the following command :
keytool -genkeypair -alias mykey -keyalg RSA -sigalg SHA256withRSA -keysize 2048 -validity 3650 -dname “cn=localhost, ou=WLS, o=Oracle, c=IN” -storepass password -keypass password -keystore identity.jks
keytool -export -alias mykey -file root.cer -keystore identity.jks -storepass password
keytool -import -alias mykey -file root.cer -keystore trust.jks -storepass password -trustcacerts -noprompt
NOTE:
– Replace the cn in the above command to your servers hostname. (Specified in console -> server listen_address field).
– You also change the storepass and keypass values in the above commands.
– The above commands will generate identity.jks and trust.jks which can be used to configure SSL on your nodemanager and WebLogic servers.
Step 2:
Configure nodeManager and WebLogic server to use this newly created identity.jks and trust.jks
OPTION 3: Disable SSL on NodeManager and WebLogic server. (Not Recommended)
<Additional Info>
Steps to create self signed certificates and configure Custom Identity and Custom trust in WebLogic
Create an Internal Certification Authority (CA) using Keytool and sign your Server Certificate
Steps to configure Custom keystore with NodeManager (per domain NodeManager)
