This blog was originally published on Jan 13, 2012.
In addition to blocking Oracle Autonomous Database (ADB) Vanity URL access to APEX tools, you optionally can block developer and administrator tools exposed by Oracle REST Data Services (ORDS). These tools include Database Actions, REST-Enabled SQL, the API of ORDS itself, Simple Oracle Document Access (SODA) for REST, and more. An Oracle Cloud Infrastructure (OCI) Load Balancer sitting in front of ADB can block these tools at the Vanity URL while continuing to provide user access to runtime APEX apps and custom REST endpoints.
Prerequisites
You must have a few things in place before proceeding. If you have not already done so, configure a Vanity URL on ADB using OCI Load Balancer and block Vanity URL access to APEX tools as described here and here. The following blog post builds on this prior configuration by adding new URL Redirect Rules to the Load Balancer Listener.
Step 1 – Review Current Blocking Rules
With a Load Balancer Listener and Rule Set already deployed, it is easy to add new URL Redirect Rules to block Vanity URL access to ORDS-provided tools. Such rules operate on the server side within the Load Balancer. They redirect selected Source Paths in the URL to new Paths of your choosing. We can leverage this capability to block access to developer and administrator tools provided by ORDS.
Start by signing into OCI Console, then navigate to your Load Balancer Details page, and drill into the existing Rule Set. Click Edit to open it.
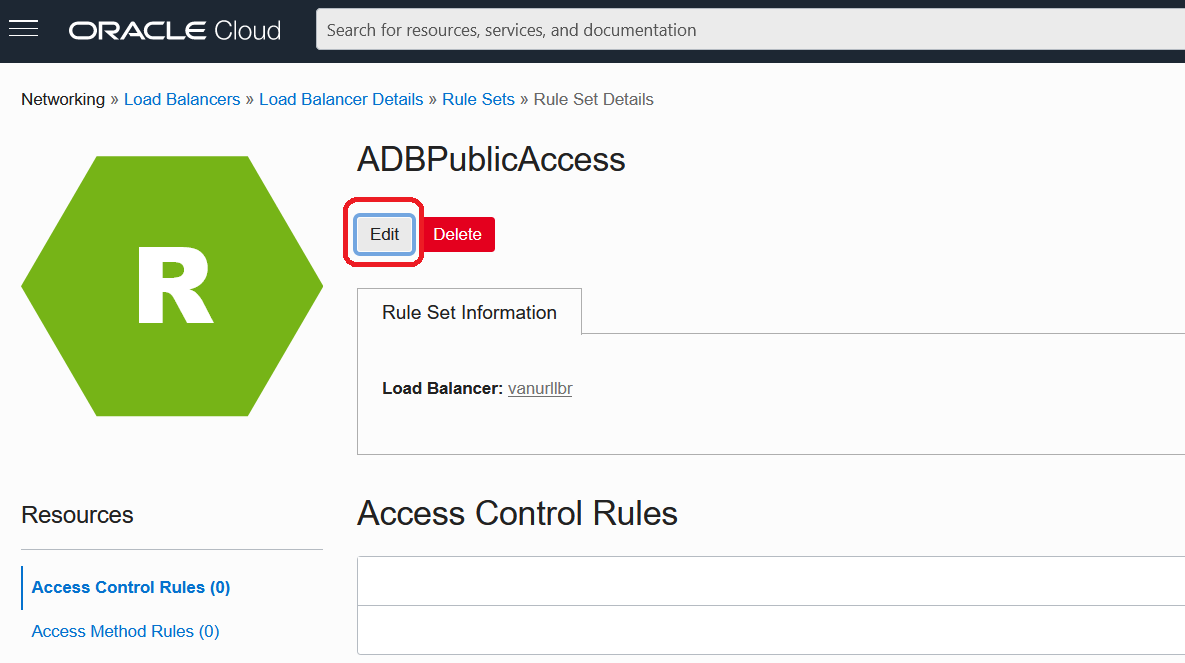
Scroll down to the URL Redirect Rules section and review your existing rule. Recall that it assigns an APEX app to be your Vanity URL landing page. In an upcoming step, we will add further rules to this list.
Step 2 – Determine New Blocking Rules
Next, review suggested rules in Table 1 below for blocking Vanity URL access to the ORDS-provided tools. These rules cover a range of functionality included and pre-configured in ADB such as Database Actions, REST-Enabled SQL, the API of ORDS itself, and SODA for REST. Read the full description for each table entry, then determine the minimal set of blocking rules that you need. For example, if you wish to block Vanity URL access only to SODA for REST, then you will only create a rule covering this component.
| Source Paths to Block | Matching Rule | ADB Feature | Comments |
|---|---|---|---|
| /sql-developer | Suffix Match | A shortcut to get to the ORDS and Database Actions sign-in page. Prompts first for user name. | Can optionally block if intending to shut off at the Vanity URL interactive user access to Database Actions. |
| /sign-in/ |
Suffix Match | The sign-in and signed-out pages used when authenticating to ORDS (including Database Actions). | Can optionally block if intending to shut off at the Vanity URL all interactive user logins. CAUTION: Do not block if legitimate runtime access at the Vanity URL to custom REST endpoints that you configure is needed and this access will require interactive user logins (e.g. the custom REST endpoint requires interactive authentication using HTTP Basic Auth or OAuth). |
| /sign-in/session | Suffix Match | Information about the signed-in ORDS user session. | Can optionally block if intending to shut off at the Vanity URL access to information about the singed-in ORDS user session. |
| /_/sql | Suffix Match | Access to REST-Enabled SQL. | Can optionally block if intending to shut off at the Vanity URL access to REST-Enabled SQL. |
| /ords/<schema-name>/_sdw/ | Prefax Match | Access to Database Actions (including SQL Developer Web). | Can optionally block if intending to shut off at the Vanity URL access to Database Actions and SQL Developer Web. NOTE: The path to match must be narrowed to <schema-name> of specific web-enabled users. |
| /ords/_/db-api/ | Prefax Match | Base access to the APIs of ORDS itself. | Can optionally block if intending to shut off at the Vanity URL access to the APIs of ORDS itself. |
| /ords/<schema-name>/_/db-api/ | Prefax Match | User-specific access to the APIs of ORDS itself. These APIs support operations like DataPump Import, Data Guard standby management, get Data Dictionary information, provision a database instance, monitor a database, and so forth. | Can optionally block if intending to shut off at the Vanity URL access to the APIs of ORDS itself. NOTE: The path to match must be narrowed to <schema-name> of specific web-enabled users. Also, APIs that perform changes will require authenticating by supplying credentials of a web-enabled database user account, and they will not execute successfully in the first place until such users have been created. |
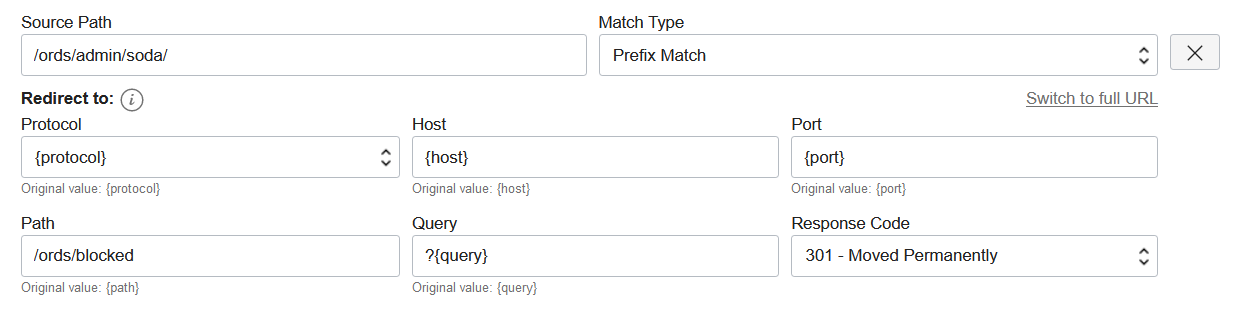
| /ords/<schema-name>/soda/ | Prefax Match | Access to the SODA for REST APIs. These APIs provide JSON document access to data. | Can optionally bock if intending to shut off at the Vanity URL access to the SODA for REST APIs. NOTE: The path to match must be narrowed to <schema-name> of specific web-enabled users. Also, this API requires pre-configuring HTTP Basic Auth or OAuth for authenticated user access. |
| /_/public-properties/ | Suffix Match | Miscellaneous property information exposed by ORDS. | Can optionally block if intending to shut off access at the Vanity URL to this miscellaneous property information. |
| /ords/<schema-name>/_adp | Prefix Match | Access to the Data Tools components of Database Actions (aka Autonomous Data Platform). This includes data load, data insights, and so forth. | Can optionally block if intending to shut off access at the Vanity URL to Data Tools. NOTE: The path to match must be narrowed to <schema-name> of specific web-enabled users. |
IMPORTANT NOTES:
- Immediately after a new ADB instance is provisioned, the
adminuser is the only <schema-name> in existence that can sign into ORDS-provided developer and administrator tools. In other words, initially you only need to create Prefix Match blocking rules for <schema-name> =admin. Later, as you create and web-enable additional database schemas, you must create Prefix Match rules for each new schema. - If you are planning to create custom REST endpoints at URLs that contain legitimate usage of strings shown in the first column of Table 1 (e.g. “…adp…”), then make sure to construct your rules to block the default REST endpoint exposed by ORDS and *not* your legitimate usage. It may be necessary to switch certain rules from Suffix Match to Prefix Match to avoid intercepting your custom REST endpoint.
Step 3 – Create and Deploy New Rules
Follow a process similar to what is described here to create each new URL Redirect Rule. Note that new rules you create should set Path to a fictitious value such as /ords/blocked. This ensures an HTTP 404 error will be returned to the caller, and it signals that access was intentionally blocked. Below is an example of a new rule that blocks access to SODA for REST for the admin user.
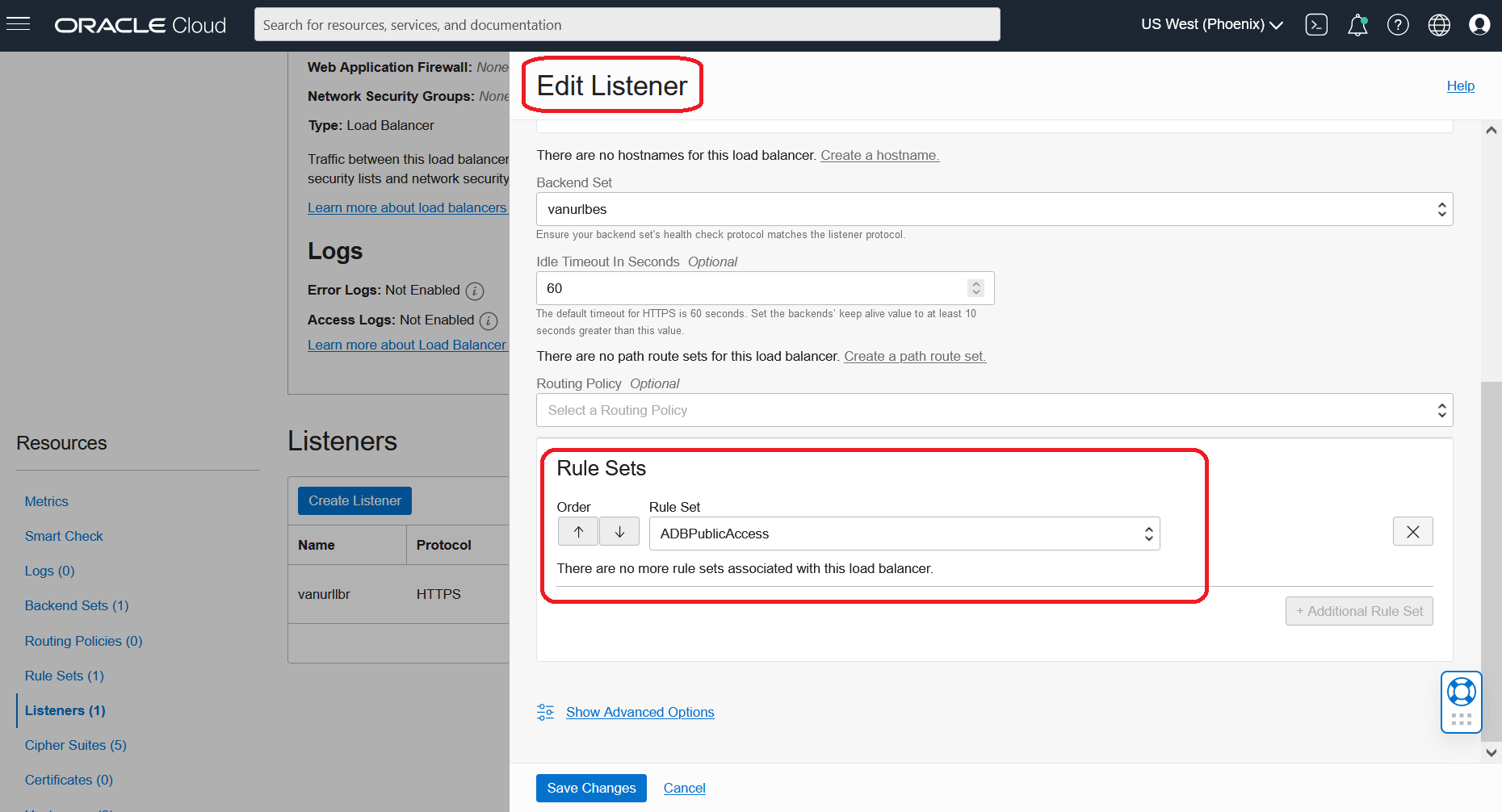
If your Rule Set already is added to the Load Balancer Listener, then new rules will be enforced after the Work Request containing your changes is completed. If your Rules Set is not added to the Listener, then you will need to add it to begin enforcing changes.
Conclusion
Blocking Vanity URL access to ORDS-provided developer and administrator tools is an important optional extension to the Oracle Autonomous Database Vanity URL architecture. It is now possible to do this using Load Balancer Rule Sets. Once you have created appropriate URL Redirect Rules, such tools are blocked at your Vanity URL while runtime apps and custom REST endpoints remain accessible.
Although this blog post focuses on one possible ADB Vanity URL extension, there are many ways that your Vanity URL configuration can be extended and adapted. For example, you can optionally configure a single ADB to support multiple Vanity URLs. To learn more about that, proceed to the next article in this blog series here.
* * * * * * * * * * * * *
For a live demonstration of blocking Vanity URL access to ORDS-provided tools, see the end of this APEX Office Hours recording on YouTube:
Navigation Links for This Blog Series
Introducing Vanity URLs for APEX and ORDS on Oracle Autonomous Database
ADB Vanity URLs Part 2: Blocking APEX Developer and Administrator Tools
ADB Vanity URLs Part 3: Blocking ORDS-Provided Developer and Administrator Tools
ADB Vanity URLs Part 4: Multiple Domain Names
