
Introduction
Oracle Data Intelligence Platform in Oracle Cloud Infrastructure (OCI) provides a set of data services that help organizations manage, process, and integrate vast amounts of data efficiently. These services, tailored for cloud environments, span data discovery, big data processing, integration, and governance.
- Data lake services: Oracle Big Data Service (BDS), OCI Data Flow (DFS), OCI Data Catalog, Oracle Intelligent Data Lake* (IDL)
- Data motion and integration services: OCI Data Integration (DIS)
* Oracle Intelligent Data Lake (IDL) is a new data lake service in the Oracle Data Intelligence Platform. For a deeper understanding, check the article, Oracle’s Unique 360-degree vision for Data Intelligence.
This post describes how to secure an OCI Data Flow (DFS) SQL Endpoint using Zero Trust Packet Routing (ZPR). The post is part of the Securing Oracle Data Intelligence Platform using Zero Trust Packet Routing series and a companion post to Secure Oracle Big Data Service using Zero Trust Packet Routing. It includes architectural diagrams, component descriptions, deployment scenarios, and links to other references.
This post uses an existing scenario, where data stored in a data lake or OCI Object Storage is accessed through a Data Flow SQL Endpoint without transforming or moving the data. An OCI Data Catalog is created for the metadata of the data stored in OCI Object Storage. Oracle Analytics Cloud (OAC) uses the Data Flow SQL Endpoint to connect to the data, creates a dataset from the data, and uses the dataset to create data visualizations and generate insights. Refer to this article to understand more about the scenario, Integrating Oracle Cloud Infrastructure Data Flow SQL Endpoint with Oracle Analytics Cloud.
This ZPR configuration described here uses the resources involved in the scenario, where Oracle Analytics Cloud connects to the OCI Data Flow SQL Endpoint, creates a dataset, and uses the dataset to create data visualization workbooks.
PrerequisitesTo follow this article you need:
- An existing OCI tenancy.
- An OCI administrator with the privileges to:
- Manage resources in compartments
- Manage ZPR policies in the tenancy
- ZPR components (introduced in the post Prepare Zero Trust Packet Routing Components for Securing Oracle Data Intelligence Platform Services):
- An OCI compartment for ZPR
- OCI policies that allow you to manage resources in the OCI compartment
- ZPR namespace
- ZPR attributes
- An understanding of ZPR policy statements
- A VCN (Virtual Cloud Network).
- VNIC’s of the OCI Data Flow SQL Endpoint in the private subnet of the VCN.
- Oracle Analytics Cloud (OAC) instance with a private endpoint. A private access channel (PAC) must be enabled.
- Bastion or Windows VM from the public subnet of the same VCN where DBeaver is installed.
- Security lists and route tables configured to allow ingress from users to OAC and egress to the OCI Data Flow SQL Endpoint.
- Connections in OAC that connect to the data in OCI Object Storage through the OCI Data Flow SQL Endpoint before ZPR is configured.
About Zero Trust Packet Routing – A Summary
The OCI Zero Trust Packet Routing documentation provides an excellent introduction and a short video.
ZPR helps prevent unauthorized access to data by decoupling network security policies from the underlying network architecture. Using an easily understood, intent-based policy language, functional security administrators can define specific access pathways for data that build upon the foundation of network firewalls, route tables, and security lists managed by network administrators.
ZPR policies require that the network administration components exist but take precedence over them. For example, security lists and route tables in a VCN (Virtual Cloud Network), DFS, and OAC resources. ZPR policies restrict access to only the resources explicitly assigned to ZPR security attributes referenced in a ZPR policy.
ZPR is VCN-centric. Components secured with ZPR security attributes must reside in the same VCN.
Topics

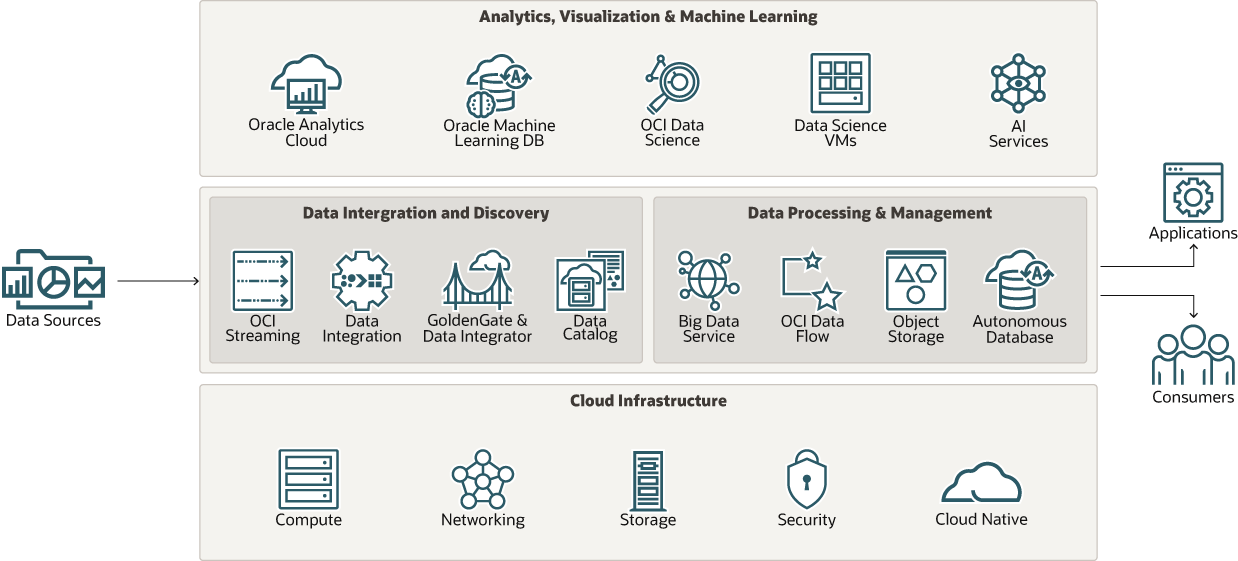
This diagram shows a VCN in an OCI region that contains an OCI Data Flow SQL Endpoint, OAC private endpoint, and public Windows VM.
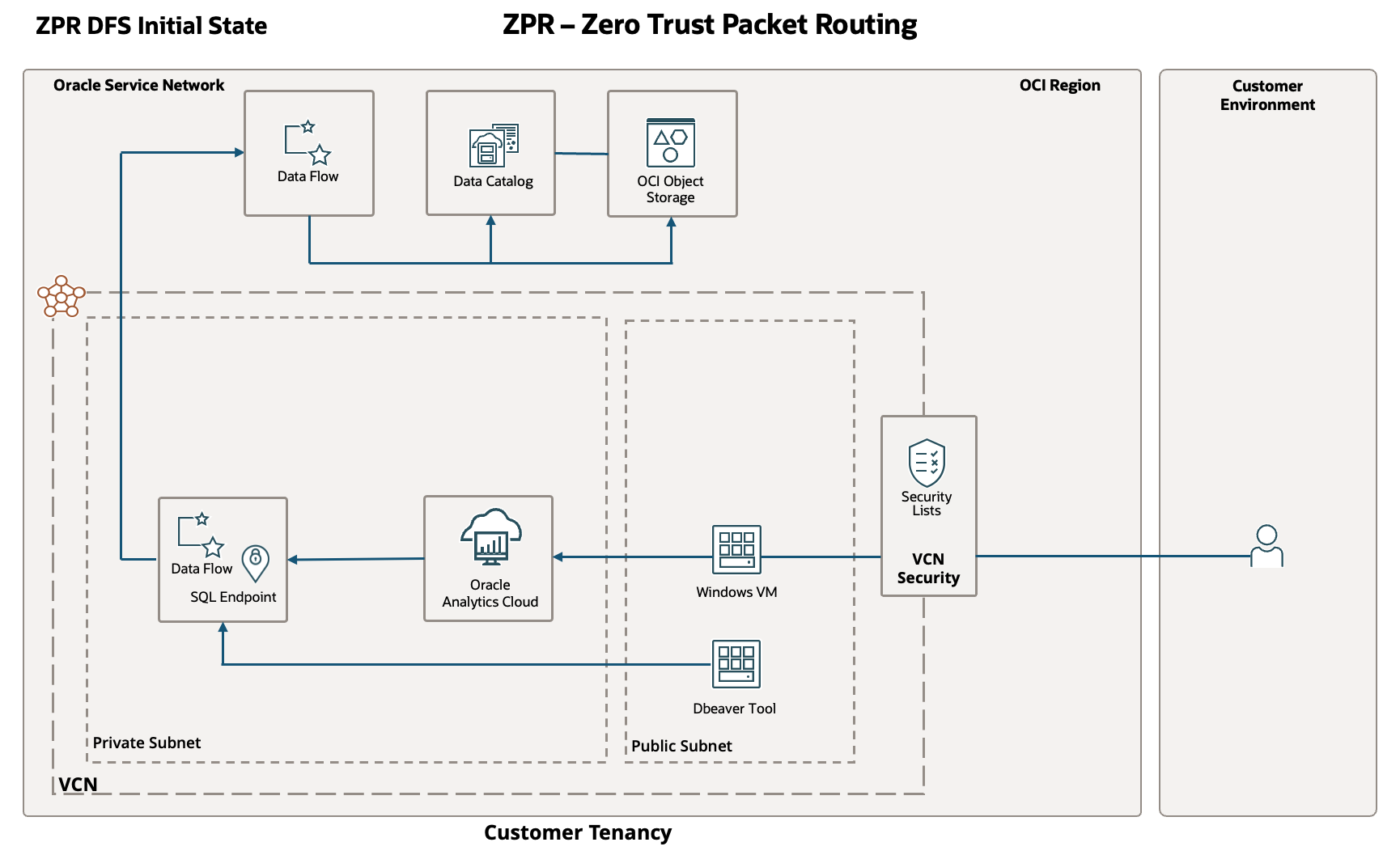
Secured State
This diagram shows the ZPR components required to secure the Windows VM, OAC services, and the OCI Data Flow SQL Endpoint.
![]()
ZPR configuration requires that you configure the following:
- ZPR IAM policies
- ZPR enablement
- ZPR compartment
- ZPR namespace
- ZPR attributes
The secured architecture includes the following components:
- ZPR attribute values
- ZPR policy statements
- ZPR resource assignments
User Device Connect to the OAC instance from the Bastion or Windows VM in the public subnet of the same VCN as the OCI Data Flow SQL Endpoint and OAC.
ZPR IAM Policies
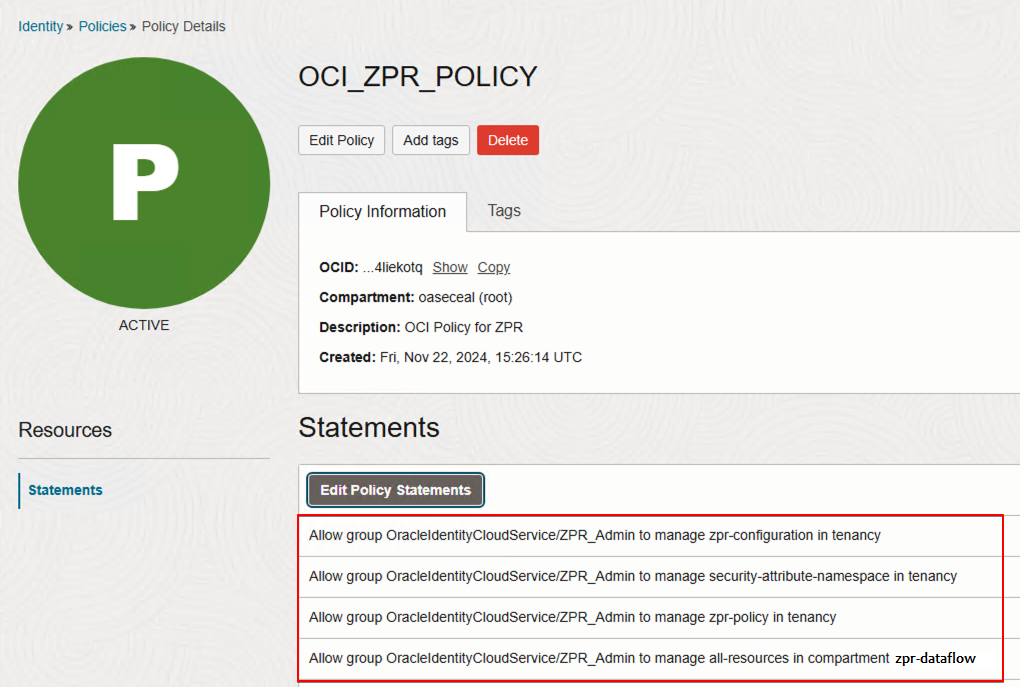
Use Oracle Cloud Infrastructure Identity and Access Management (IAM) to create policies to control access to the Zero Trust Packet Routing (ZPR) service.
- Allow group OracleIdentityCloudService/ZPR_Admin to manage zpr-configuration in tenancy
- Allow group OracleIdentityCloudService/ZPR_Admin to manage security-attribute-namespace in tenancy
- Allow group OracleIdentityCloudService/ZPR_Admin to manage zpr-policy in tenancy
- Allow group OracleIdentityCloudService/ZPR_Admin to manage all-resources in compartment zpr-dataflow
ZPR Enablement
ZPR is disabled by default. When you enable ZPR in your tenancy, a default Oracle-ZPR security attribute namespace is created that you can use.

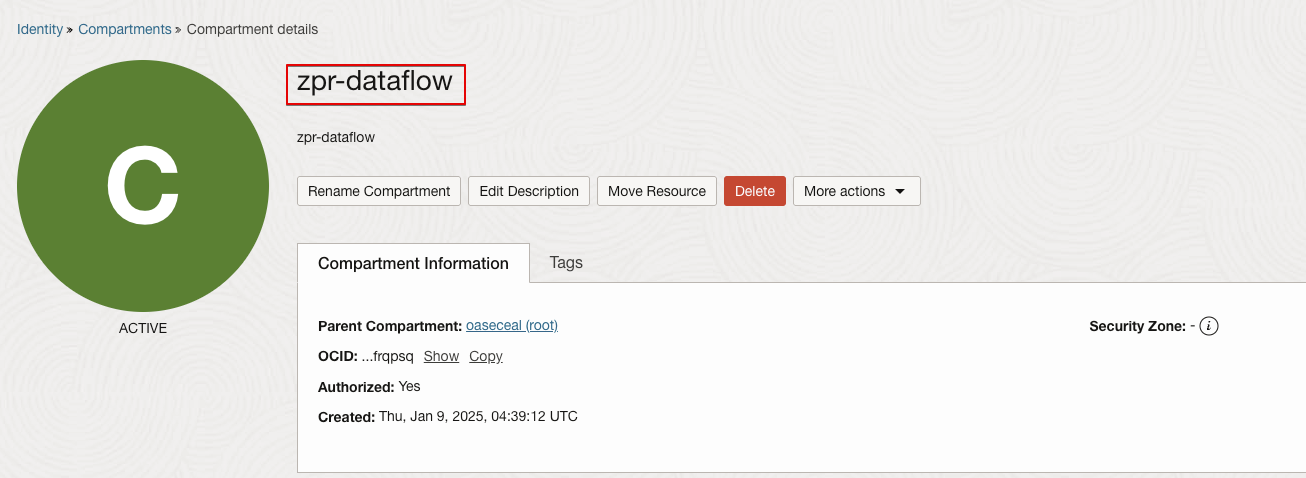
ZPR Compartment
Oracle recommends separate compartments for ZPR namespaces to separate duties. For example, a Human Resources ZPR security administrator may not be a Financials ZPR security administrator.
Create a ZPR compartment for each planned ZPR functional area. For example, HR, ERP, and so on.
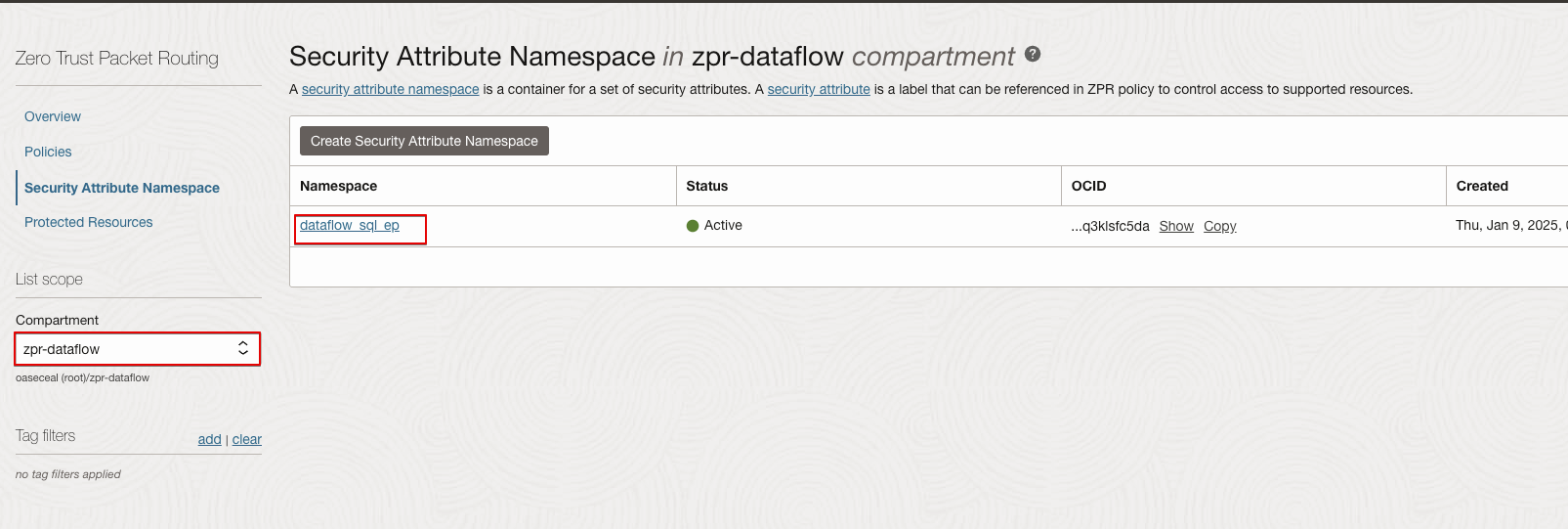
ZPR Namespace
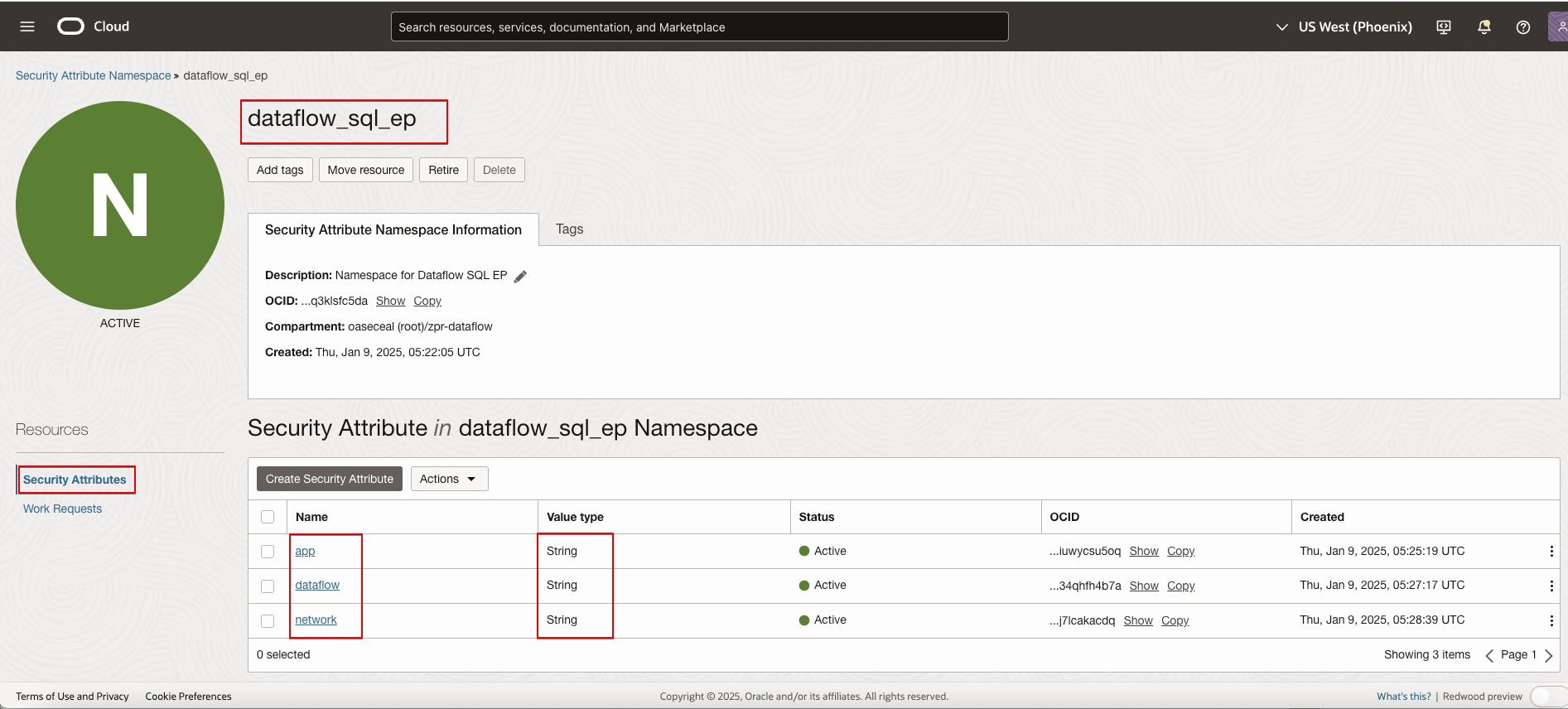
ZPR namespaces are containers for ZPR security attributes. In this example, the ZPR namespace is dataflow_sql_ep.
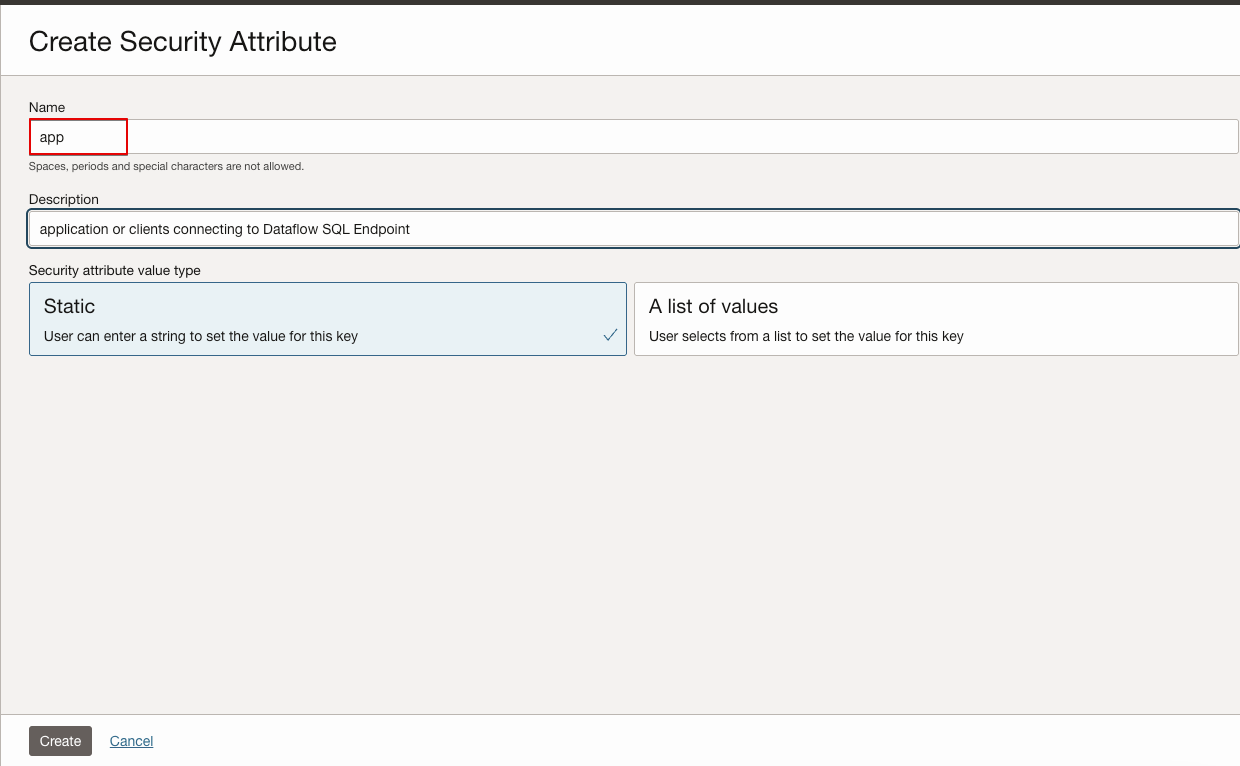
ZPR Attributes
ZPR security attributes are labels that you can reference in ZPR policies to control access to supported resources. Attributes are used in conjunction with attribute values when creating ZPR policies. The documentation uses application, network, and database/dataflow as example attributes.
- app (application)
Zero Trust Packet Routing – Create Security Attribute - dataflow
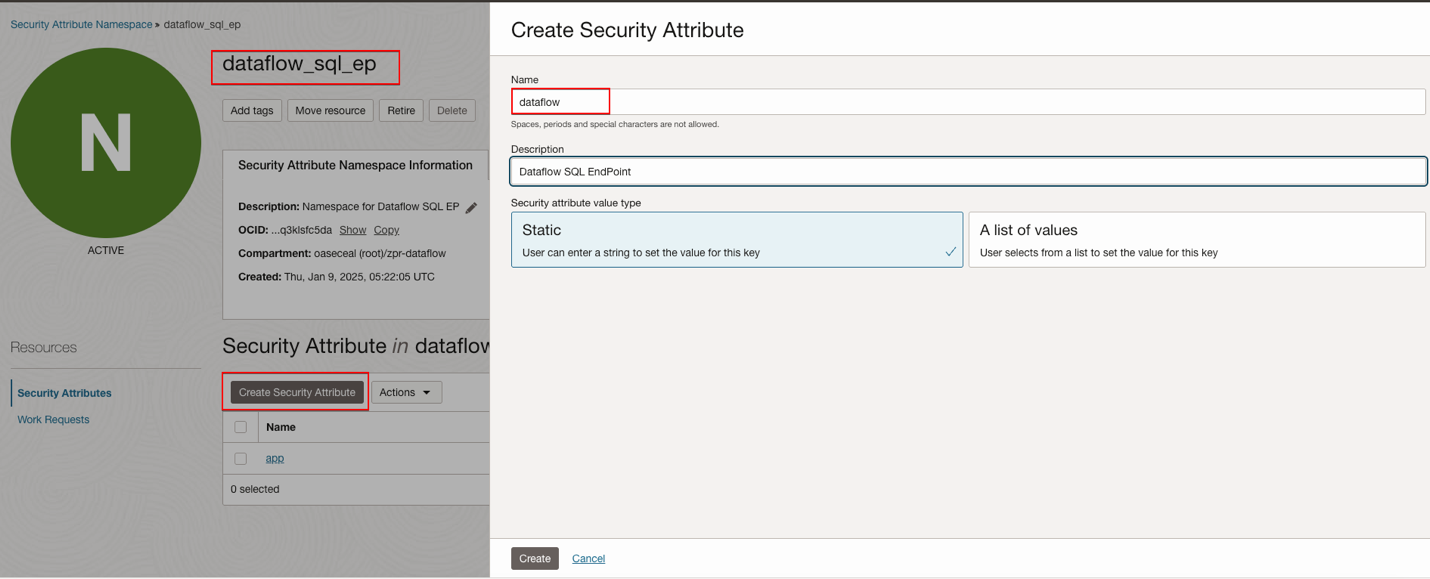
Zero Trust Packet Routing – Create Security Attribute - network
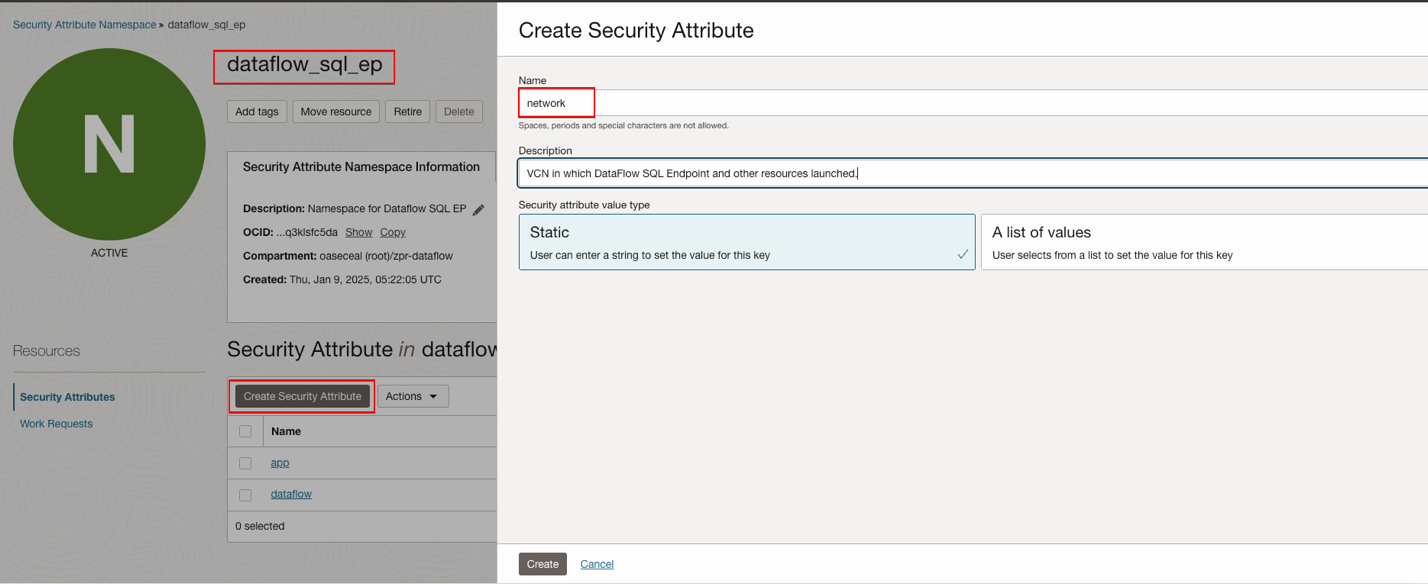
Zero Trust Packet Routing – Create Security Attribute
ZPR Attribute Values
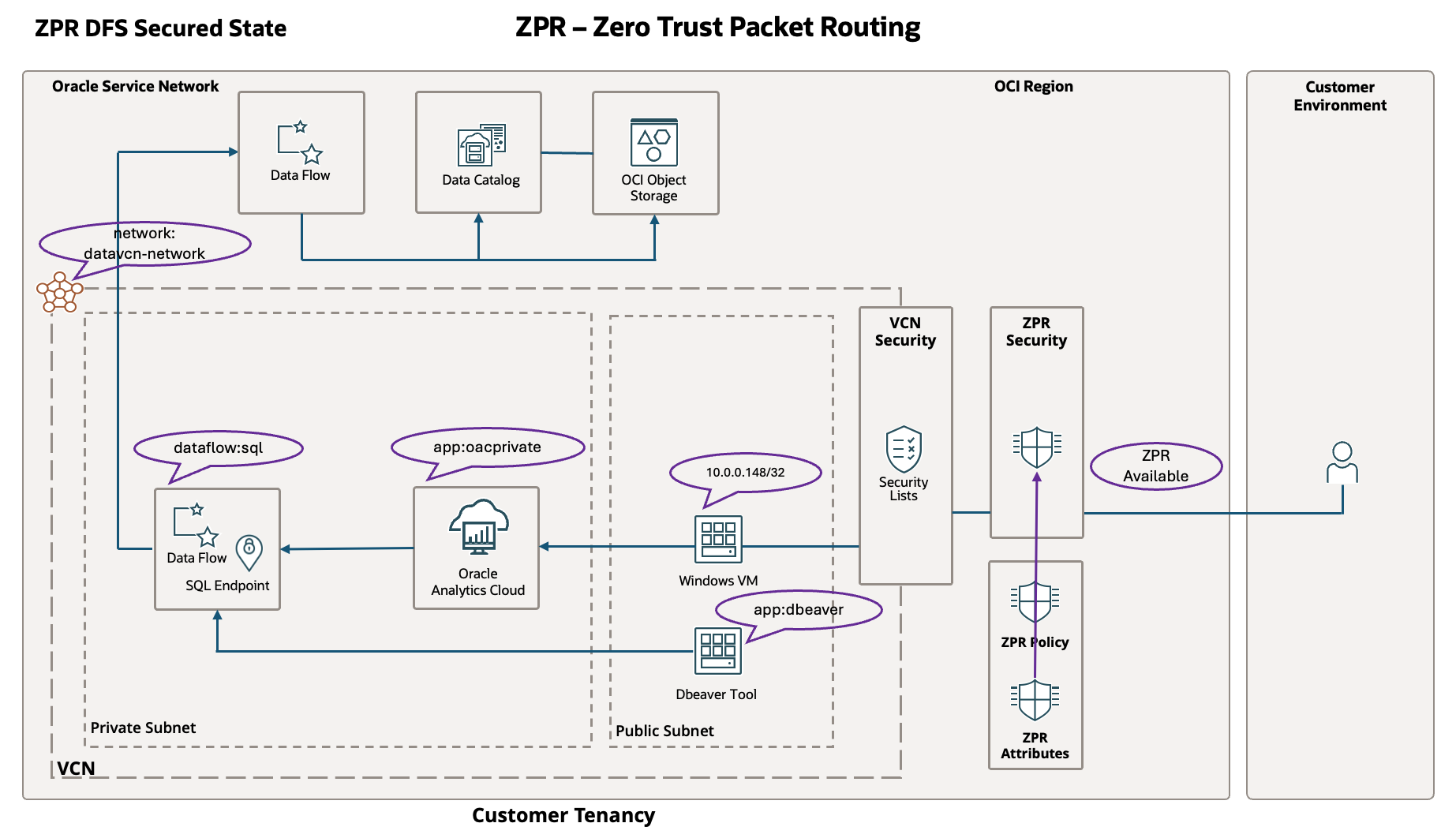
You reference ZPR security attribute values in ZPR policies to control access to supported resources. This post uses the following values:
- network:datavcn-network
- dataflow:sql
- app:oacprivate
- app:dbeaver
Use a Windows VM in the public subnet of the same VCN as the OCI Data Flow SQL Endpoint and OAC to access the private OAC instance. You must use the Windows VM private IP CIDR block to create the ZPR policy to allow access from the public Windows VM to the private OAC instance.
- 10.0.0.148/32 for the Public Windows VM
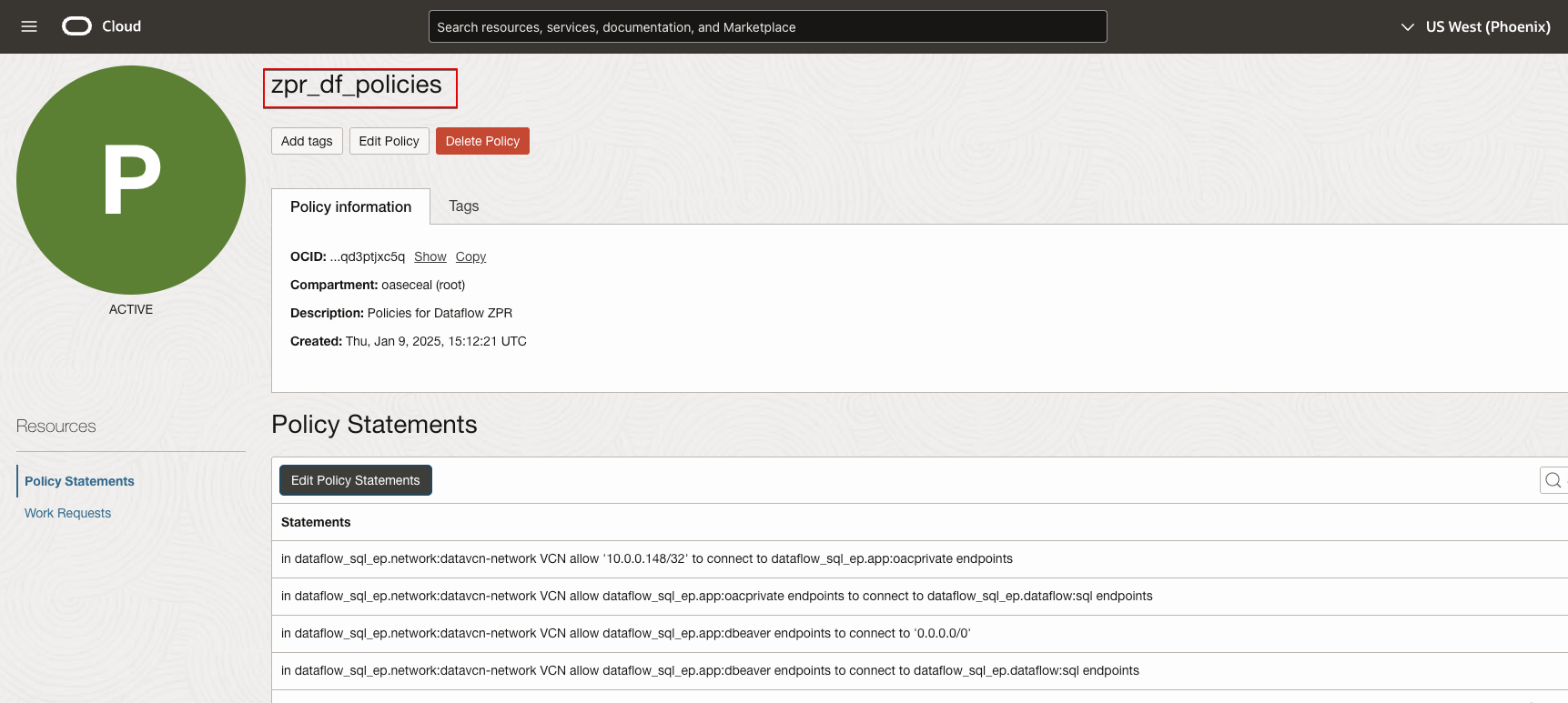
ZPR Policy Statements
A ZPR policy is a rule that governs the communication between specific endpoints identified by their security attributes. Refer to Policy Syntax.
In OCI Console, navigate to Identity & Security. Under Zero Trust Packet Routing, click Policies, then Create Policy.
- in dataflow_sql_ep.network:datavcn-network VCN allow ‘10.0.0.148/32’ to connect to dataflow_sql_ep.app:oacprivate endpoints
- in dataflow_sql_ep.network:datavcn-network VCN allow dataflow_sql_ep.app:oacprivate endpoints to connect to dataflow_sql_ep.dataflow:sql endpoints
- in dataflow_sql_ep.network:datavcn-network VCN allow dataflow_sql_ep.app:dbeaver endpoints to connect to ‘0.0.0.0/0’
- in dataflow_sql_ep.network:datavcn-network VCN allow dataflow_sql_ep.app:dbeaver endpoints to connect to dataflow_sql_ep.dataflow:sql endpoints
ZPR Resource Assignments Listing Protected Resources
app:oacprivate
Get the details of the private OAC instance. To list the OAC in ZPR Protected Resources, use the VNIC of the OAC Instance.
In this article, the goal is to protect access from OAC (or any client tools) to the OCI Data Flow SQL Endpoint.
This article doesn’t describe how to protect OAC using ZPR. This is described in the article, Secure Oracle Analytics Cloud using Zero Trust Packet Routing.
app:dbeaver
Get the details of the Dbeaver host Windows instance. To list the host Windows instance in ZPR Protected Resources, use the VNIC of the Windows instance.

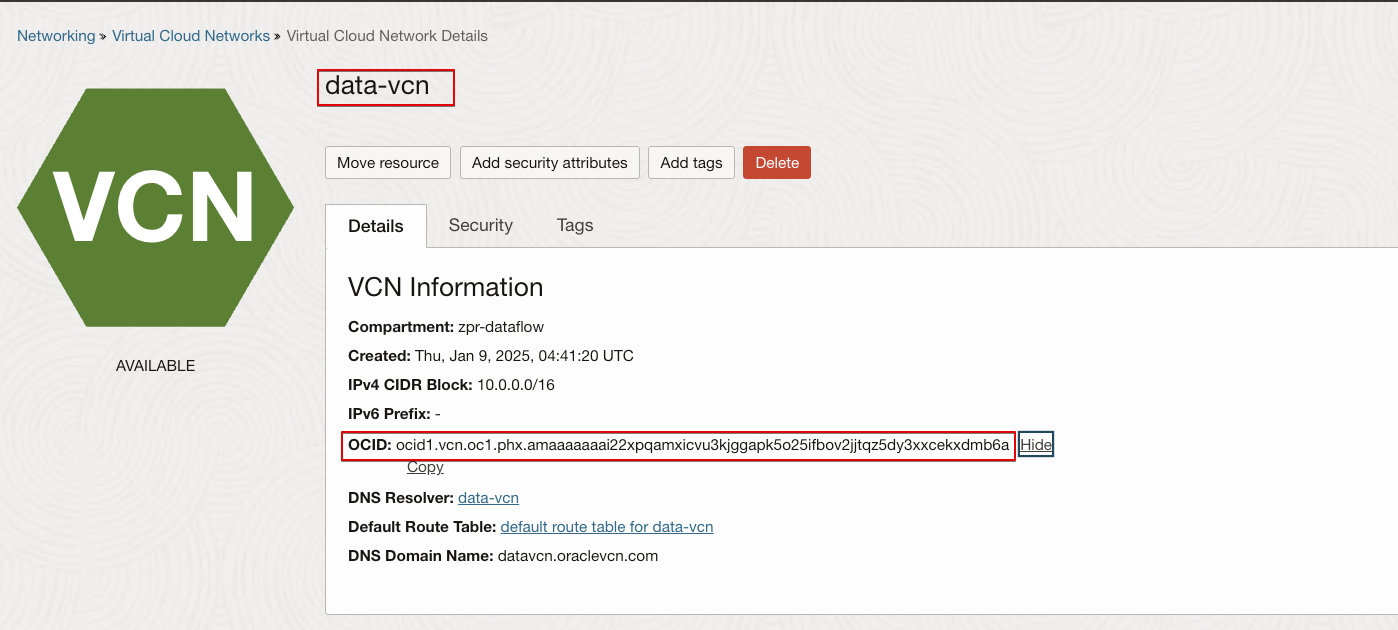
network:datavcn-network
Get the details of the VCN where the OCI Data Flow SQL Endpoint, private OAC instance, and public Windows VM exist.
In the OCI Console, navigate to Networking à Virtual Cloud Networks. Select the compartment, select the VCN, and get the OCID of the VCN.
The VCN name in this example is: dsvcn
dataflow:sql
Get the details of the OCI Data Flow SQL Endpoint and nodes that are involved in this scenario for the ZPR security configuration. Get the OCID values of the Node and the VNIC.
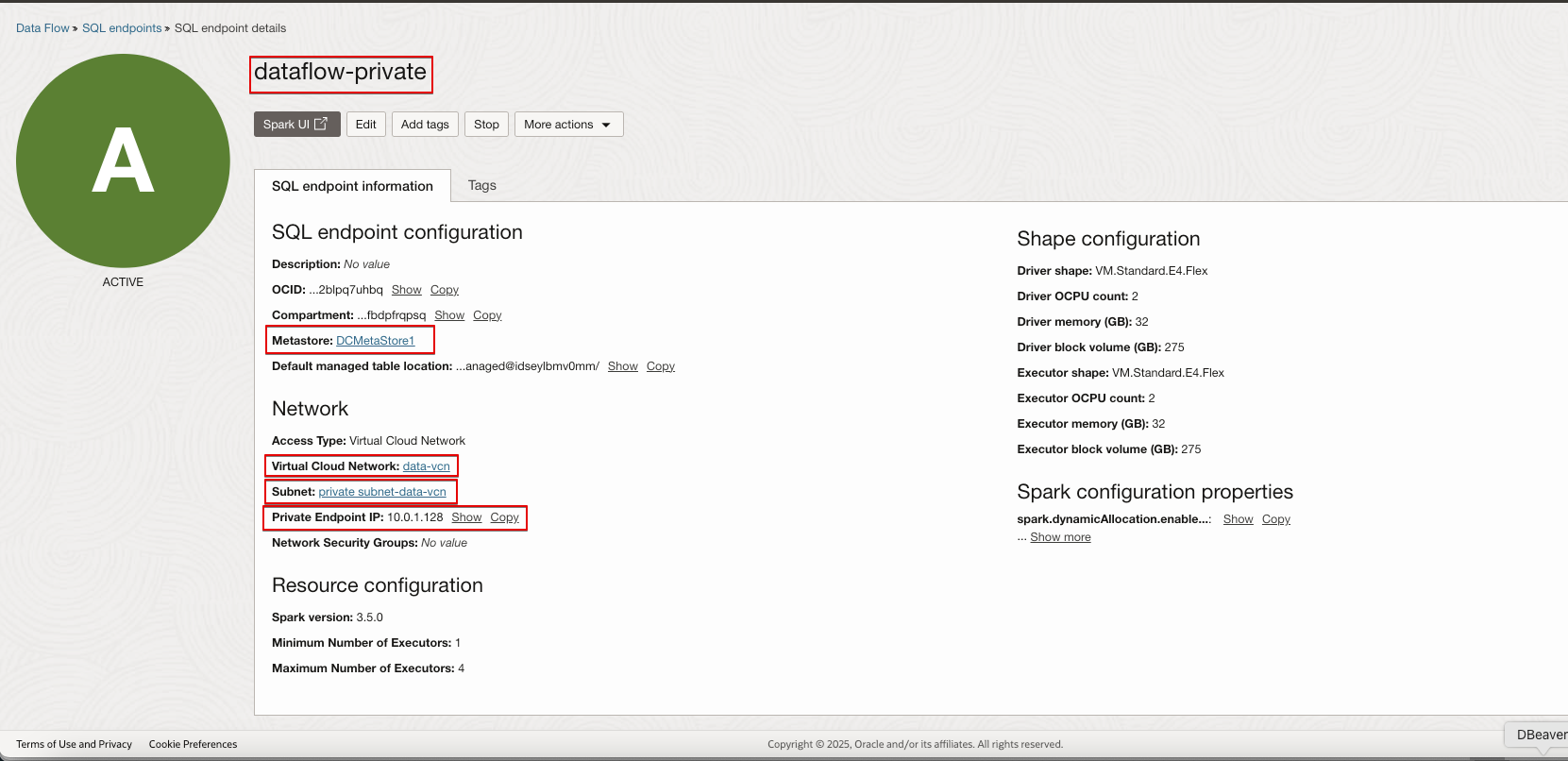
Get the OCID of the SQL Endpoint. For example: ocid1.dataflowsqlendpoint.oc1.phx.anyhq********************************************q7uhb
Add Resources to ZPR
In OCI Console navigate to Identity & Security. Under Zero Trust Packet Routing, click Protected Resources, and select the compartment where the OCI Data Flow, OAC instance, and other resources exists. Select the ZPR Security attribute namespace, and click Add security attribute to resources.
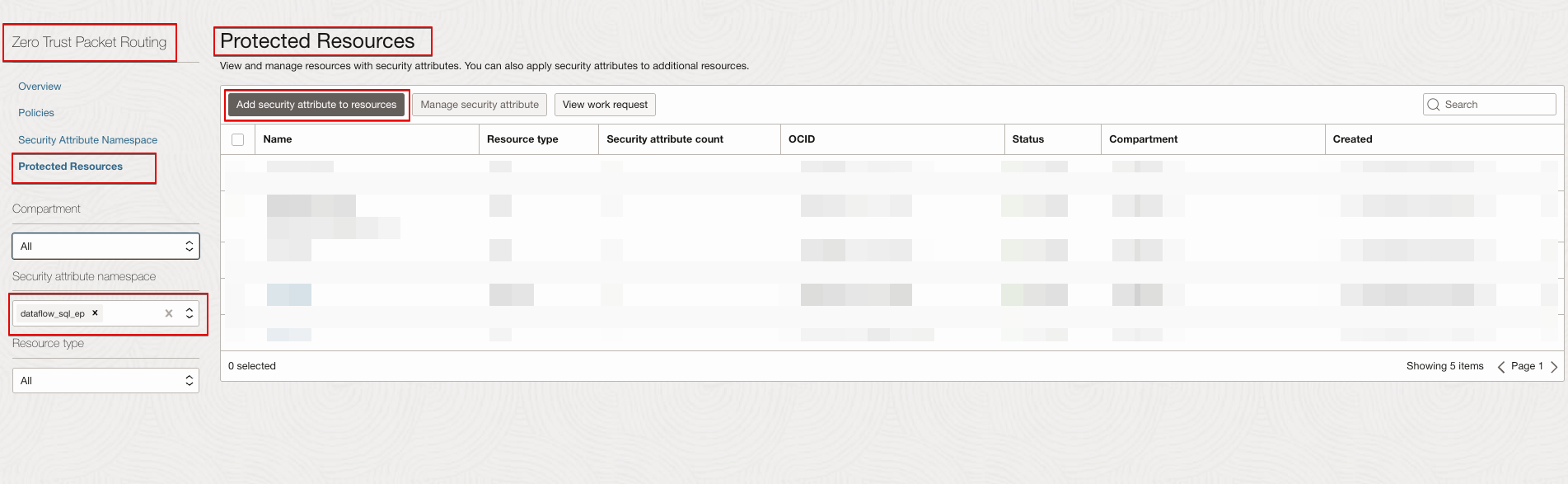
VCN
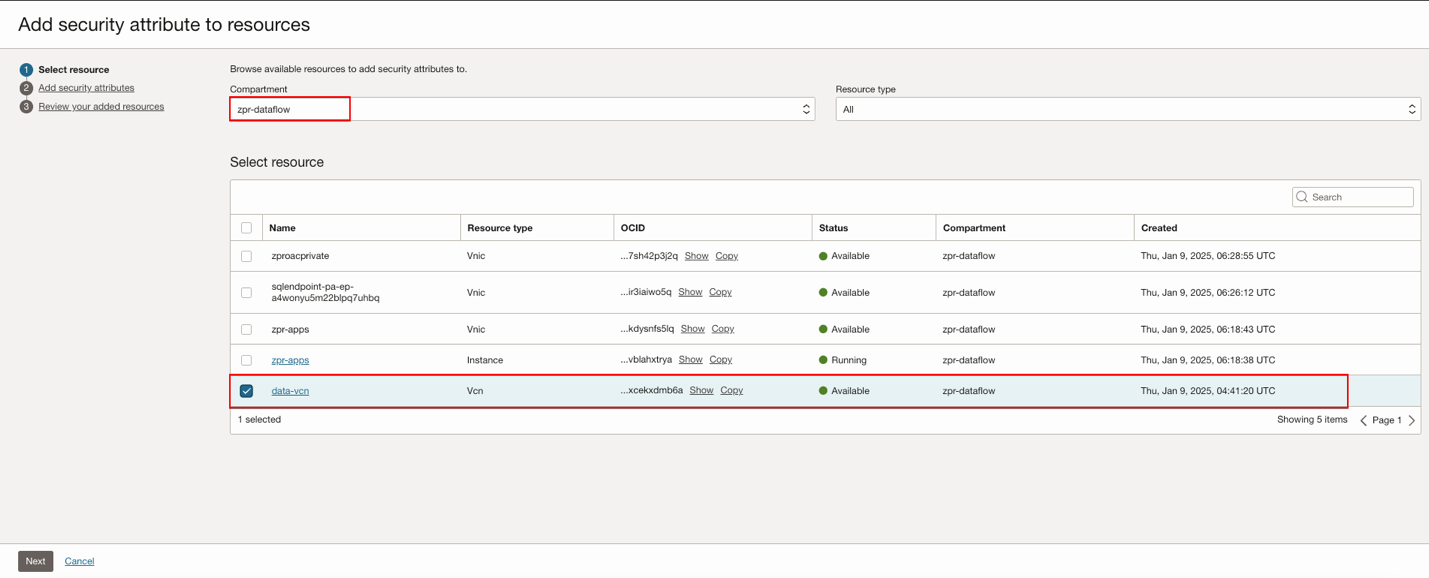
Select the resource you need, click Next, then Add security attributes to the resources.
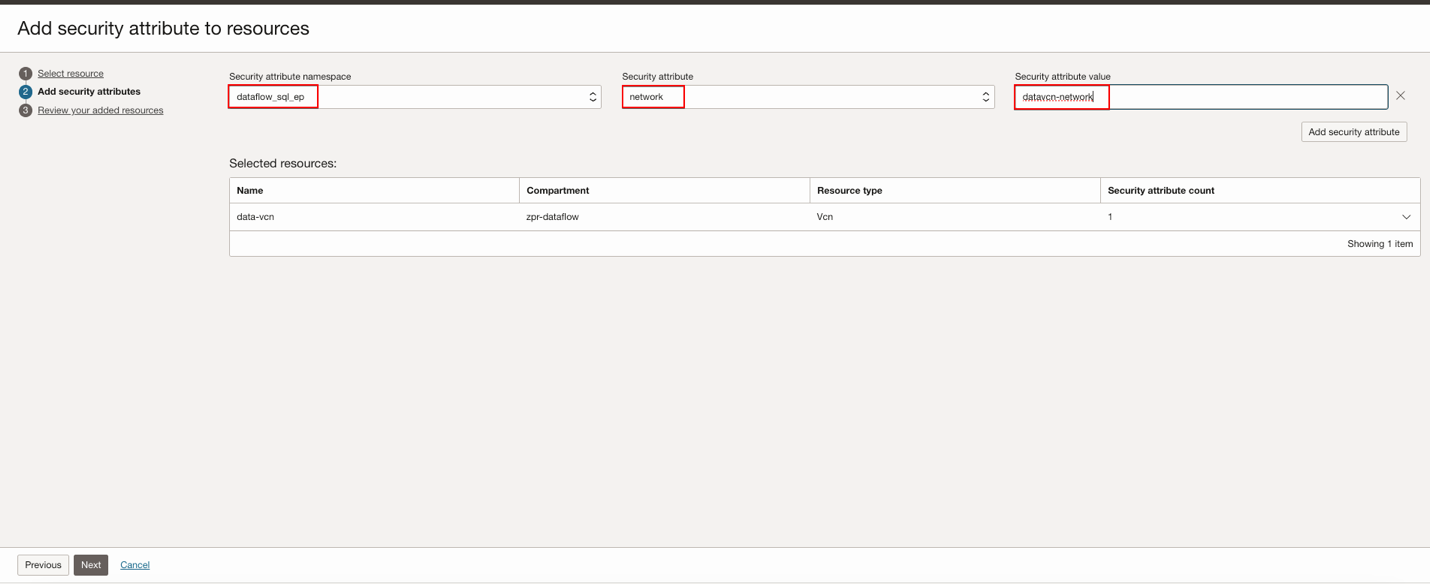
Click Next, then Submit after a review.
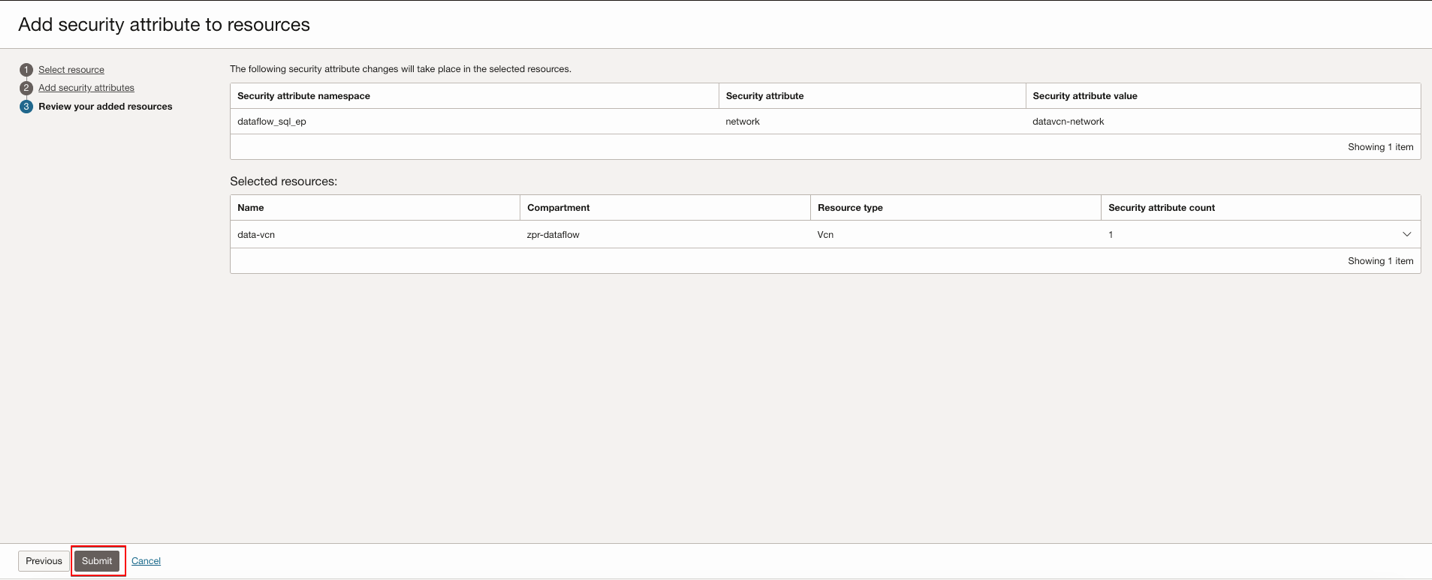
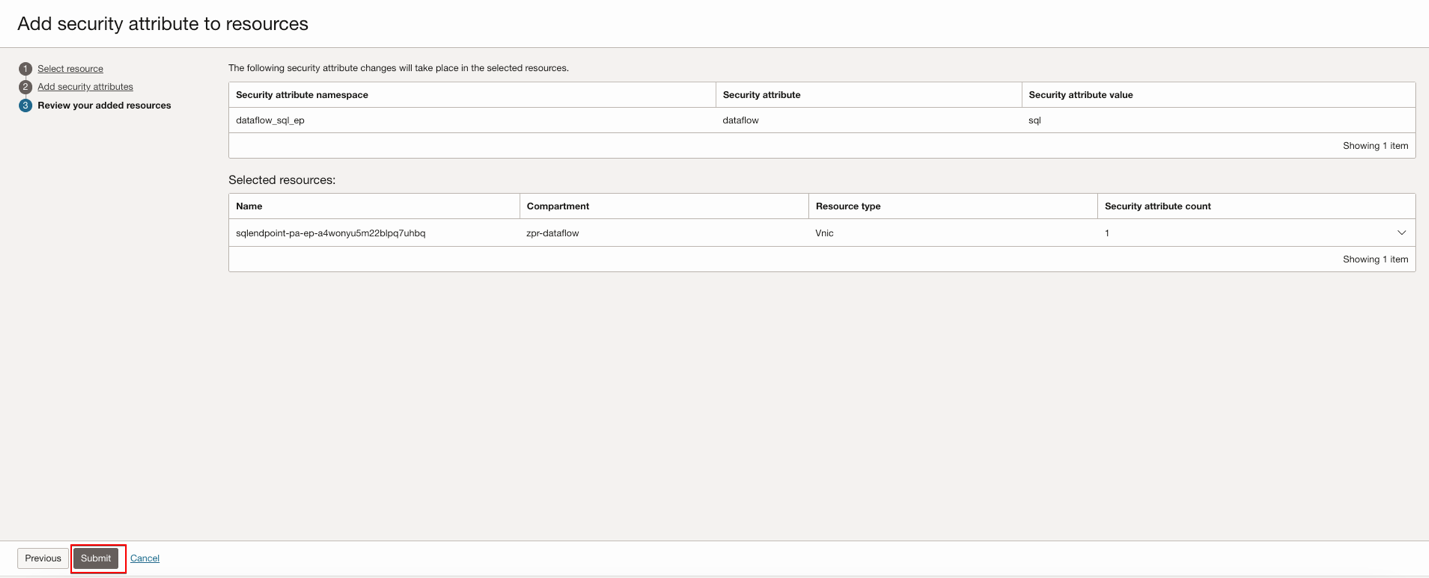
VNIC of the Data Flow SQL Endpoint
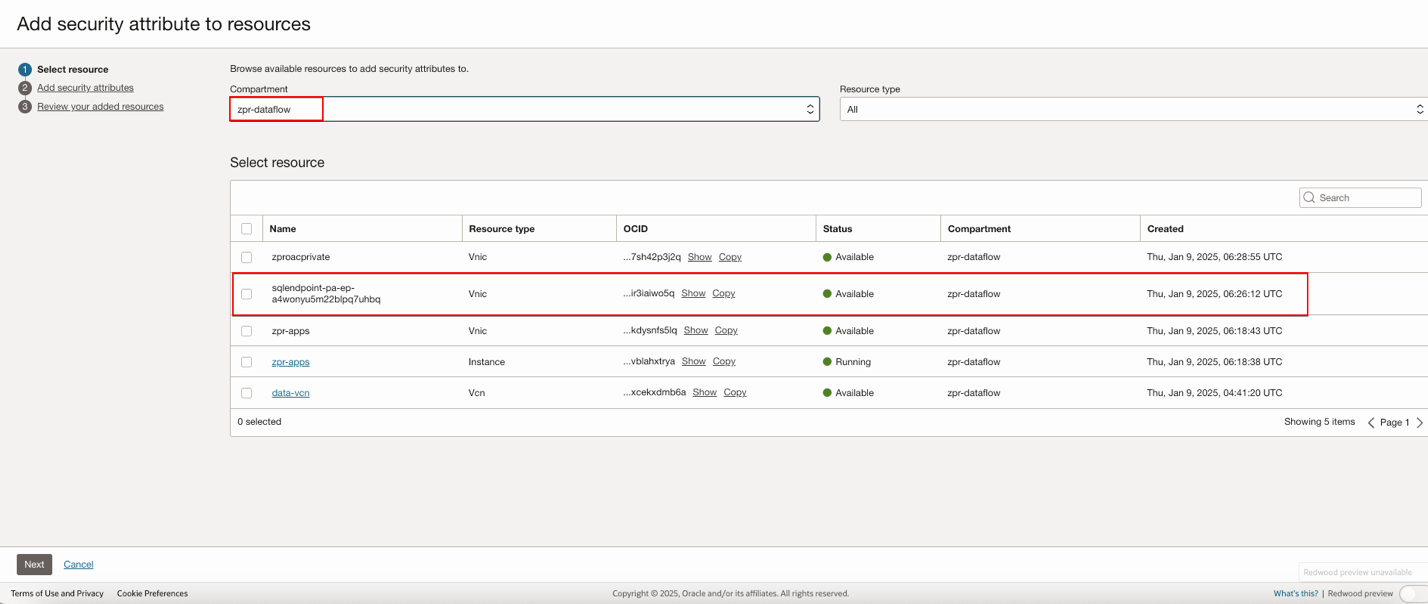
Select the resource you need, click Next, then Add security attributes to the resources.
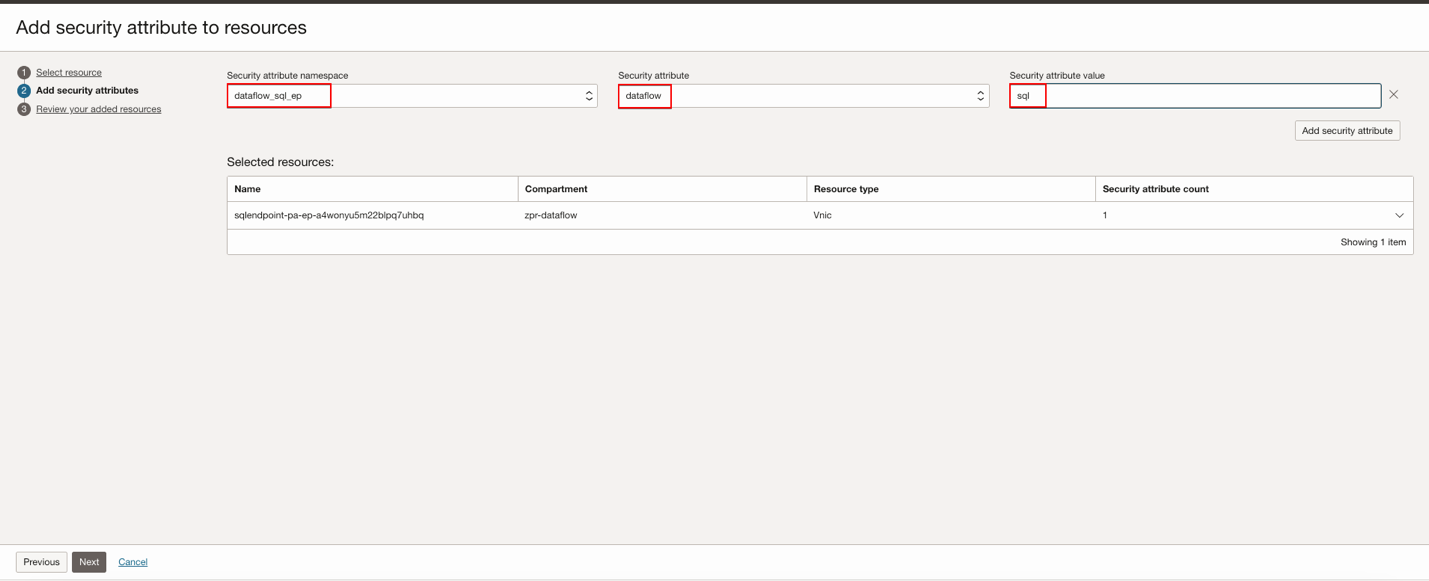
Click Next, then click Submit after a review.
VNIC of the OAC instance:
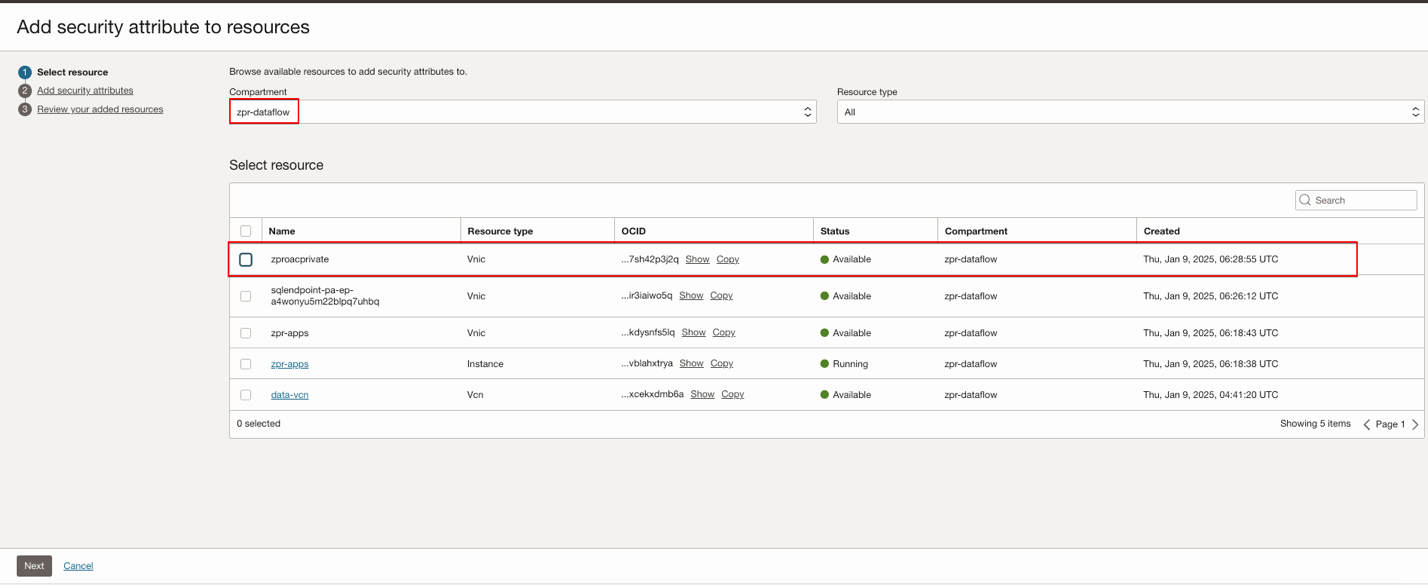
Select the resource you need, click Next, then Add security attributes to the resources.
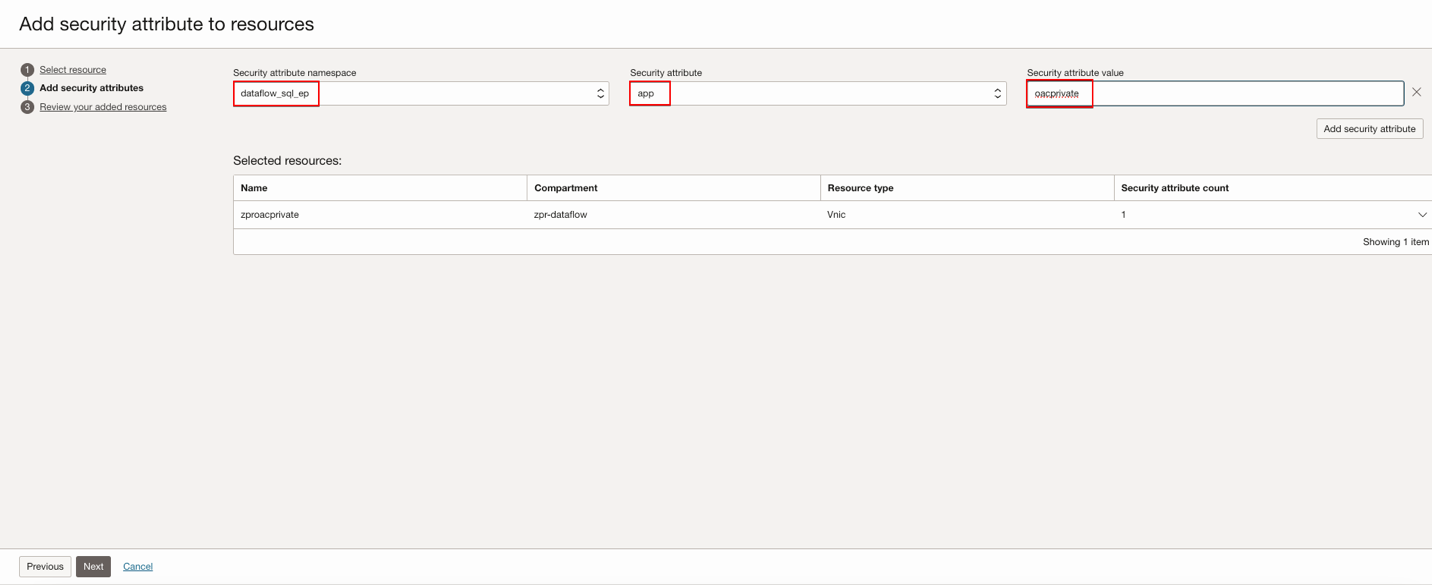
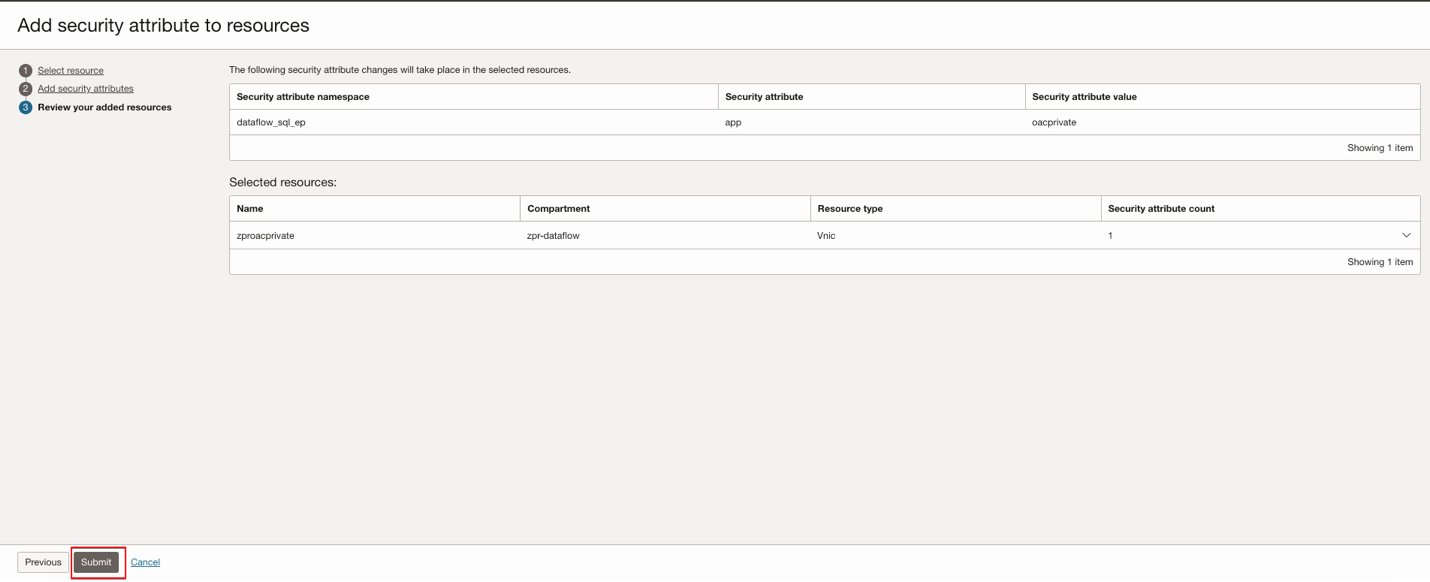
Click Next, and then click Submit after a review.
VNIC of the DBeaver Host Instance:
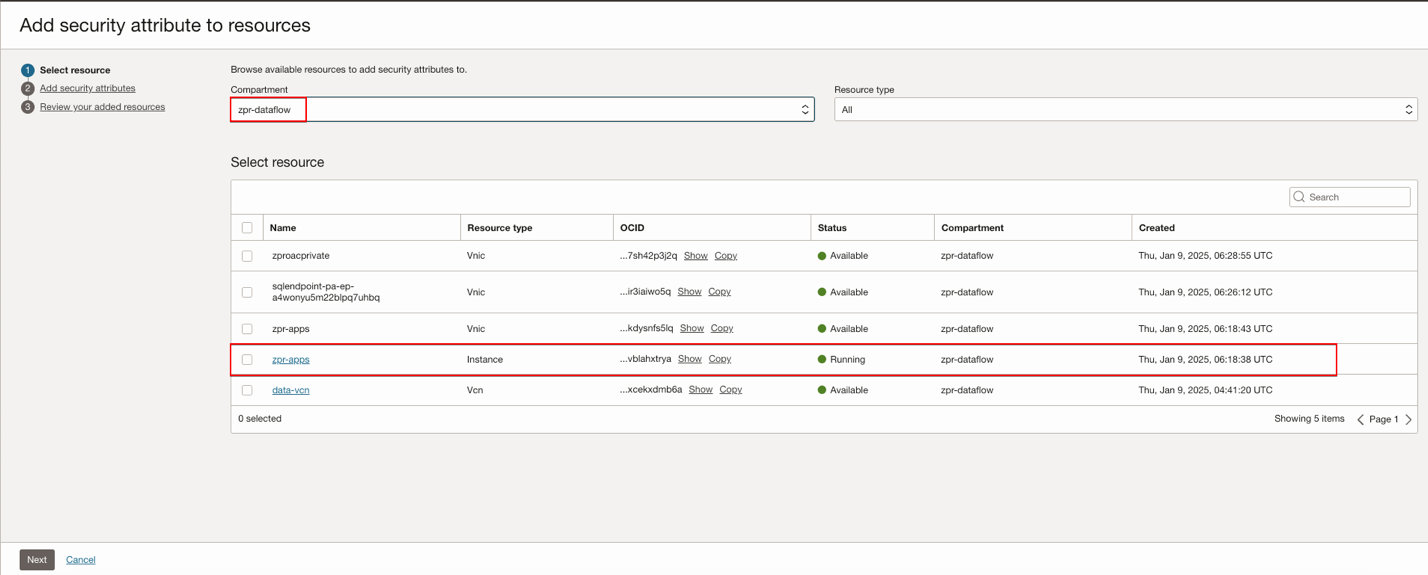
Select the resource you need, click Next, then Add security attributes to the resources.
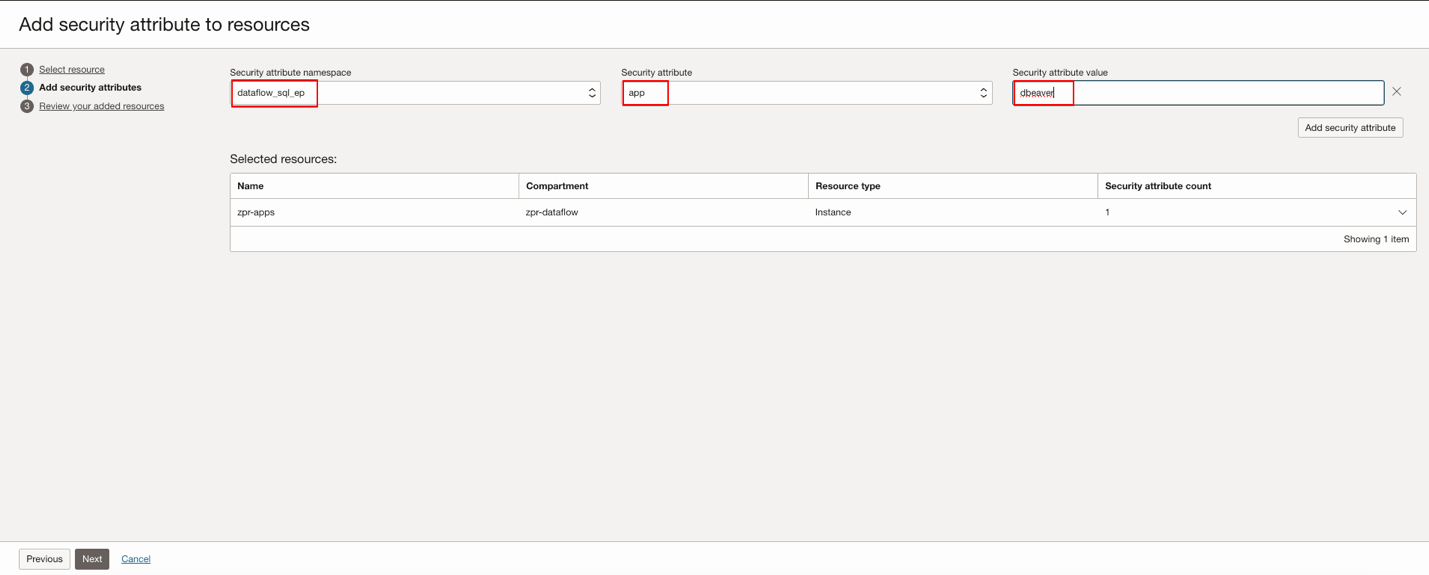
Click Next, and then click Submit after a review.
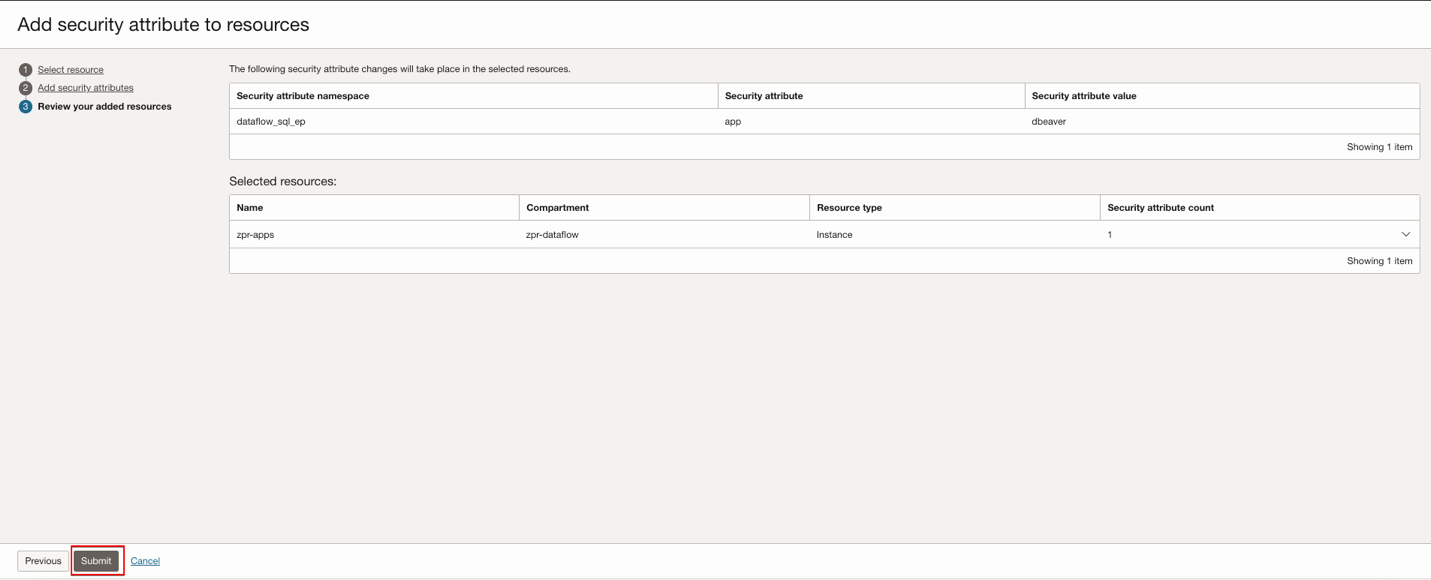
Currently ZPR security attributes supports only few resources such as Compute, Database, Networking and Network Load Balancer.
The next step, you use the VNIC of the private endpoint of the OCI Object Storage, add the Object Storage as a ZPR protected resource, and test the ZPR security.
![]()
Access Data Flow SQL Endpoint from OAC
Accessing OAC in a private subnet and OCI Data Flow SQL Endpoint in a private subnet isn’t covered in this article. For more detail, refer to the article, Integrating Oracle Cloud Infrastructure Data Flow SQL Endpoint with Oracle Analytics Cloud.
Validate OAC access from the public Windows server which is in the same data-vcn VCN.
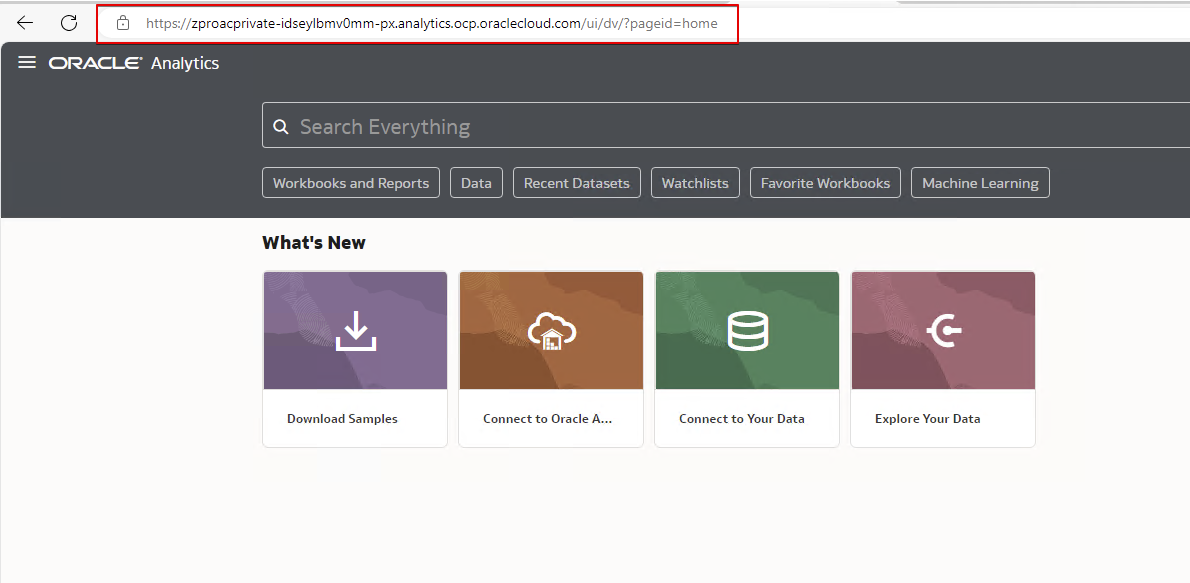
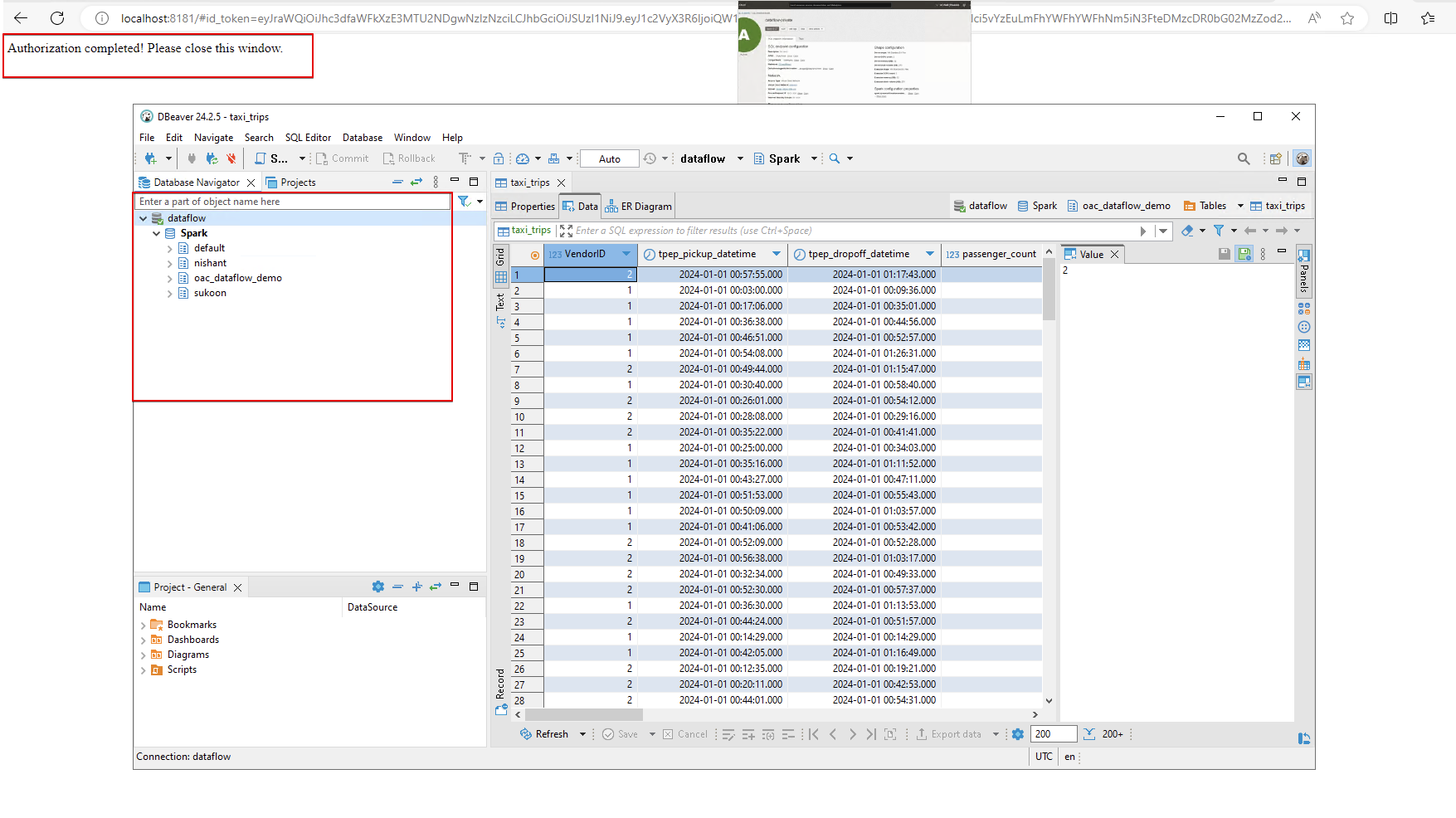
Either create a new connection or use an existing connection to the Data Flow SQL Endpoint and create a new dataset from the data.
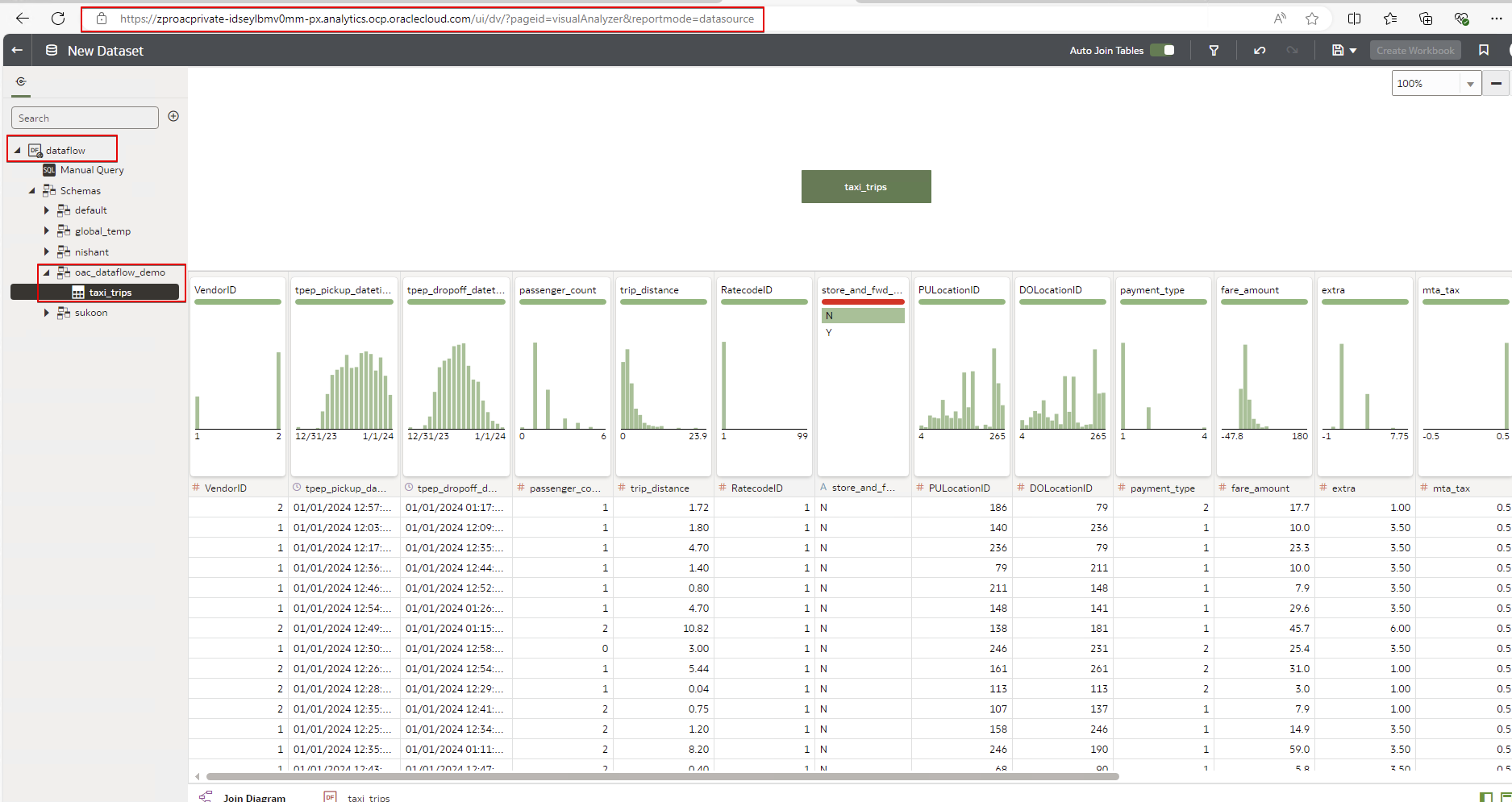
Access Data Flow SQL Endpoint with DBeaver
Without the ZPR access to DBeaver, you see the error shown here.
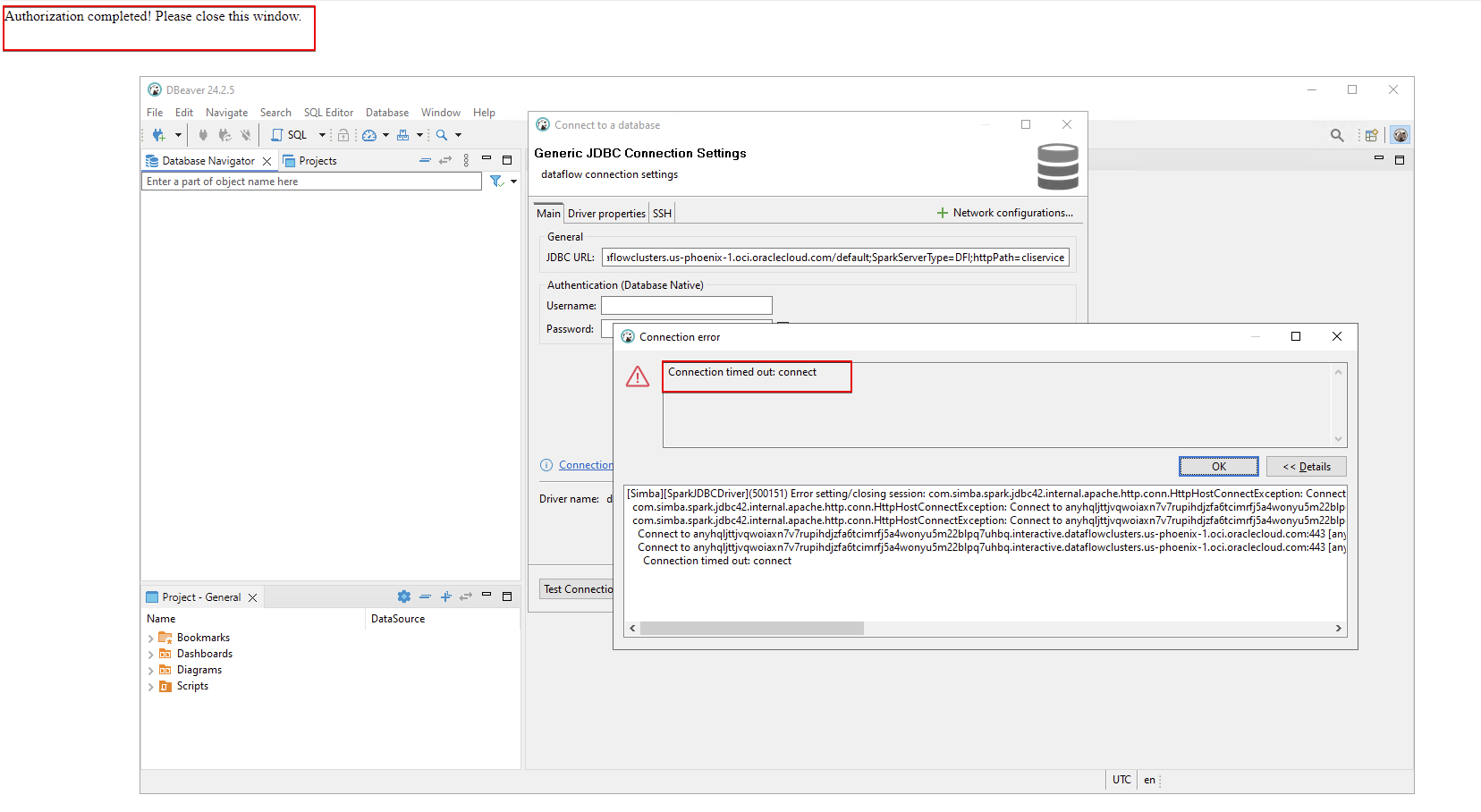
This proves that the OCI Data Flow SQL Endpoint is protected by Zero Trust Packet Routing (ZPR).
![]()
Read more about ZPR:
Zero Trust Packet Routing IAM Policies
Enabling Zero Trust Packet Routing
Managing Security Attribute Namespaces
Managing Security Attributes
ZPR policy basics
Managing Zero Trust Packet Routing Policies
ZPR Policy Syntax
ZPR Protected Resources
Read more about securing services on Oracle Intelligence Data Platform with ZPR:
Series Overview for Securing Oracle Data Intelligence Platform Services with Zero Trust Packet Routing
Prepare Zero Trust Packet Routing Components for Securing Oracle Data Intelligence Platform Services
Secure Oracle Big Data Service using Zero Trust Packet Routing
![]()

