
Published Version 1 on July 24th, 2024.
Oracle Fusion Analytics (Fusion Analytics) is a component of the Oracle Fusion Data Intelligence (FDI) platform designed to deliver personalized insights for Oracle Fusion Cloud Applications (Fusion Cloud Applications). It combines business data, ready-to-use analytics, and prebuilt AI and machine learning (ML) models to deliver deep insights and actionable results.
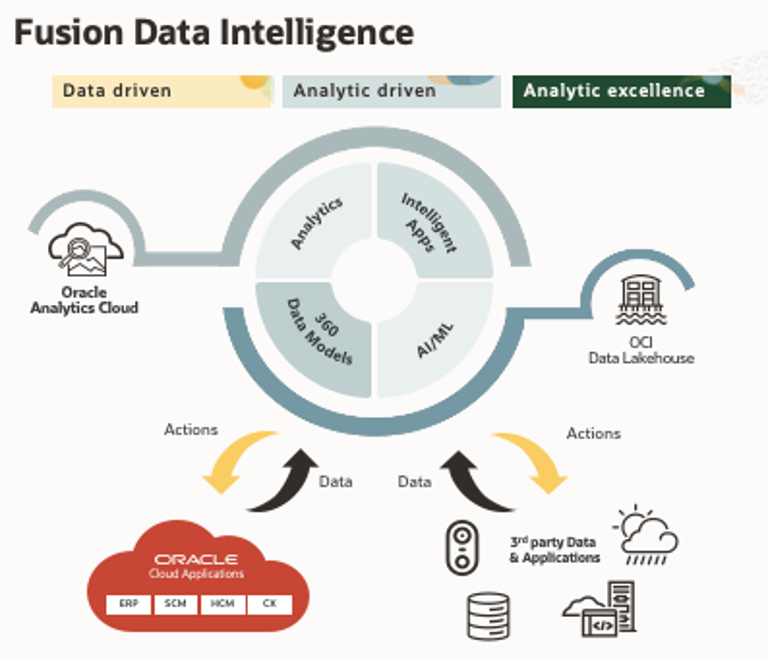
This post builds upon the foundation described in Use Custom Hostnames for Oracle Fusion Analytics.
It guides setting up the OCI (Oracle Cloud Infrastructure) network components required to use custom hostnames to access Fusion Analytics services via the Internet. Architectural diagrams, component descriptions, access flows, and links for additional references are included.
Note: This post describes using a custom hostname for two FDI web services, one of which is OAC (Oracle Analytics Cloud). It does not cover using a custom hostname for the FDI ADW (Autonomous Data Warehouse). The Call to Action includes links to relevant ADW documentation.
Note: The Vanity URL feature available in standalone instances of OAC offers more functionality than the method described in this post. However, it is unavailable in the current release of Fusion Analytics. The method described in this post may also be used for standalone instances of OAC if desired.
Use Case
Custom hostnames enable customers to use their registered domains for Fusion Analytics services and a single hostname for multiple web services.
The following shows the Fusion Analytics prebuilt hostnames format as of the current release.
- Fusion Analytics Console
- <instance name>-<tenancy name>-prod.data.analyticsapps.<region name>.ocs.oraclecloud.com
- Oracle Analytics Cloud
- oax<instance name>-<tenancy object storage namespace>-to.analytics.ocp.oraclecloud.com
The following shows an example format of a custom hostname used by Myorg, inc., whose registered domain is myorg.com.
- For all Fusion Analytics services
- analytics.<environment>.myorg.com
Prerequisites
Following the guidance in this post requires:
- Fusion Analytics Components
- An accessible Fusion Analytics environment using default Fusion Analytics hostnames.
- Custom hostname components described in Use Custom Hostnames for Oracle Fusion Analytics:
- The custom hostname designated for the Fusion Analytics environment.
- The certificate for the hostname signed by a CA (Certificate Authority).
- Privileges to
- Manage load-balancers, certificate-authority-family, and virtual-network-family in the compartment hosting the Fusion Analytics environment.
- Create, register, and publish DNS entries for the custom hostnames.

The architecture diagrams depict the initial and prepared states.
Initial State
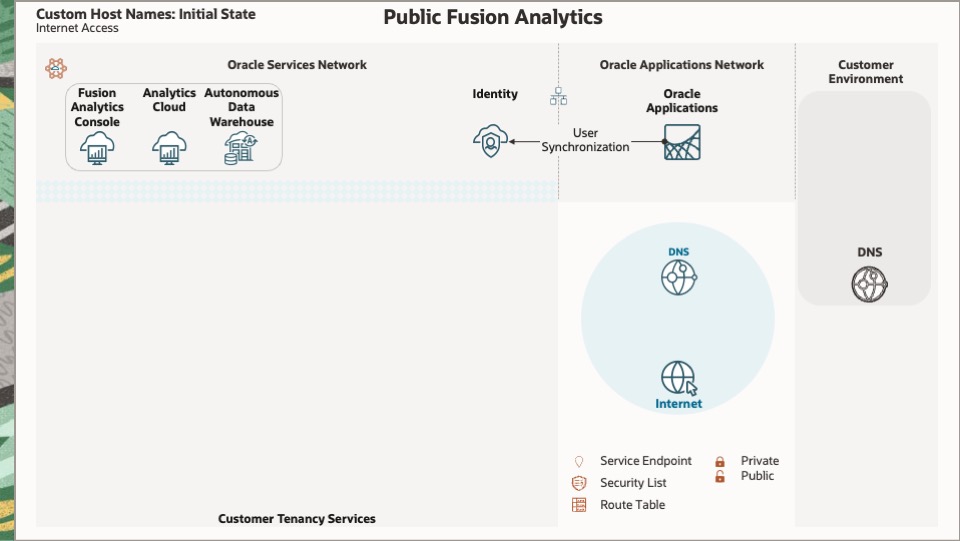
This diagram depicts the initial state of a public Fusion Analytics instance.
Prepared State
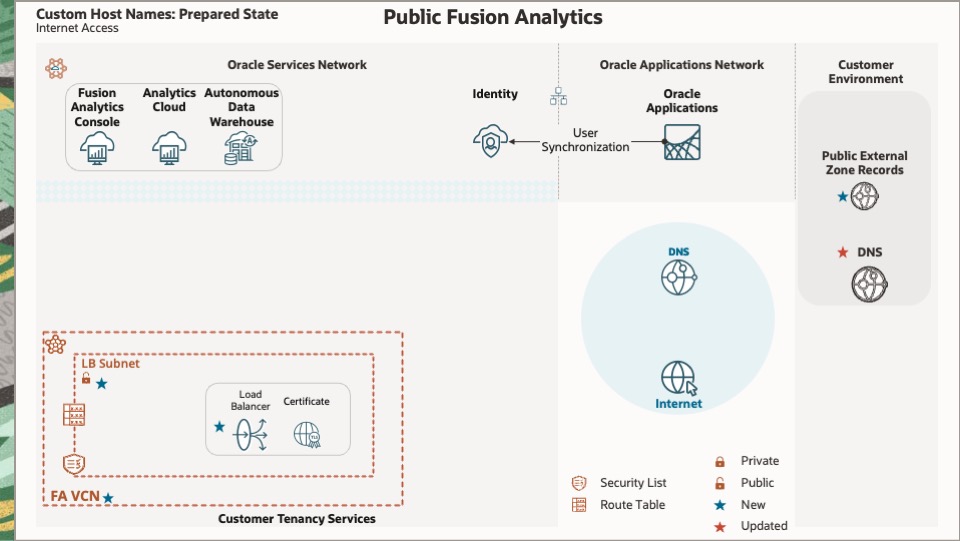
This diagram depicts the prepared state of a public Fusion Analytics instance using custom hostnames.

This section describes the additional and updated components in the prepared-state architecture diagram.
Accessing Fusion Analytics services via the Internet is the only scenario in this series where a VCN (Virtual Cloud Network) is not a required initial component. An existing VCN and public subnet may be used if available.
A VCN provides a customizable and private cloud network in OCI.
In the prepared diagram, the VCN contains the load balancer, an Internet gateway, a public subnet, a security list, and a route table.
In the prepared diagram, the Internet gateway enables direct connectivity to and from the Internet.
Public Subnet
A subnet is a logical subdivision of a VCN. Each subnet consists of a contiguous range of IP addresses that don’t overlap with other subnets in the VCN.
A public subnet provides public IP addresses to resources that need to reach or be reached from the Internet.
In the prepared diagram, the public subnet hosts the load balancer.
Security List
A security list consists of rules specifying protocols, ports, and allowable source and destination CIDR blocks (IP address ranges) and is assigned to one or more subnets in the VCN.
In the prepared diagram, the security list restricts access to the load balancer.
Route Table
A route table consists of rules specifying targets and destination CIDR blocks and is assigned to one or more subnets in the VCN.
In the prepared diagram, the route table routes return traffic from the load balancer.
OCI Certificates Service
The OCI Certificates Service creates and manages TLS certificates, certificate authorities (CAs), and CA bundles. It provides certificate issuance, storage, revocation, and automatic renewal capabilities.
In the prepared environment, the Certificates service stores the certificate associated with the custom hostname.
Public Load Balancer
A load balancer provides automated traffic distribution and processing from a single entry point.
A public load balancer has a public IP address that is accessible from the Internet and can be associated with a friendly DNS name through any DNS vendor.
In the prepared diagram, a public load balancer receives a Fusion Analytics URL containing a custom hostname and returns the prebuilt Fusion Analytics URL. Its public IP address is associated in DNS with the custom hostname.
A rule set is associated with the load balancer’s listener and comprises rules and actions applied to inbound traffic.
A URL redirect rule specifies the path string and match condition the service uses to evaluate an incoming URL. URL redirect rules in the load balancer’s rule set specify how to redirect incoming URLs to destination URLs. A destination URL and response code are returned to the client.
Load Balancer Backend Set
A backend set is a logical entity associated with the load balancer listener. It is defined by a load balancing policy, a health check policy, and, optionally, a list of backend servers.
In the prepared environment, the default backend set is defined without backend servers, as they are unnecessary for URL redirection.
Load Balancer Listener
A listener is a logical entity that checks for incoming traffic on the load balancer’s IP address. For FDI and OAC URL redirection, it handles HTTPS traffic arriving on port 443.
In the prepared environment, it is configured with the following:
- SSL termination using the custom hostname certificate managed by the Certificates service.
- The rule set defined for URL redirection.
Customer DNS
The customer DNS is modified to add records to a public external zone.
A DNS “A” record is added to a public external zone. It contains the load balancer’s custom hostname and the public IP address of the load balancer.

Several frameworks exist to deploy the components:
The Call to Action includes links to documentation for using the OCI console.
A typical provisioning sequence follows:
- Use an existing VCN or create one. For new VCNs:
- Ensure the VCN CIDR block does not overlap existing CIDRs.
- Use a small CIDR IP address range, as the VCN only needs to host a Load Balancer. For example, 10.22.0.0/26 provides 64 IP addresses.
- If necessary, additional CIDRS can be added later to the VCN.
- Check the Use DNS hostnames in this VCN checkbox.
- Use an existing Internet Gateway in the chosen VCN or create one.
- Add rules to an existing Security List in the chosen VCN or create one.
- For ingress, use the same CIDR ranges specified in FDI ACLs (Access Control Lists).
- For egress, allow all traffic to be returned to the source.
- Add a rule to an existing Route Table in the chosen VCN or create one.
- Route all unrouted traffic to the Internet gateway.
- Use an existing Public Subnet in the chosen VCN or create one.
- Use a CIDR block that is a subset of the VCN CIDR. For example, 10.22.0.0/27 provides 32 IP addresses.
- Associate the Route Table configured above.
- Check the Use DNS hostnames in this Subnet checkbox.
- Associate the Security List configured above.
- Import the custom hostname certificate determined in Use Custom Hostnames for Oracle Fusion Analytics to the OCI Certificates Service.
- Create a public load balancer with a public IP address in a public subnet.
- Accept the defaults for the backend set. Do not add backend servers.
- Configure the listener for the HTTPs protocol and port 443.
- Configure SSL for the listener using the custom hostname certificate.
- Update the load balancer.
- Create and associate a Rule Set to the load balancer listener.
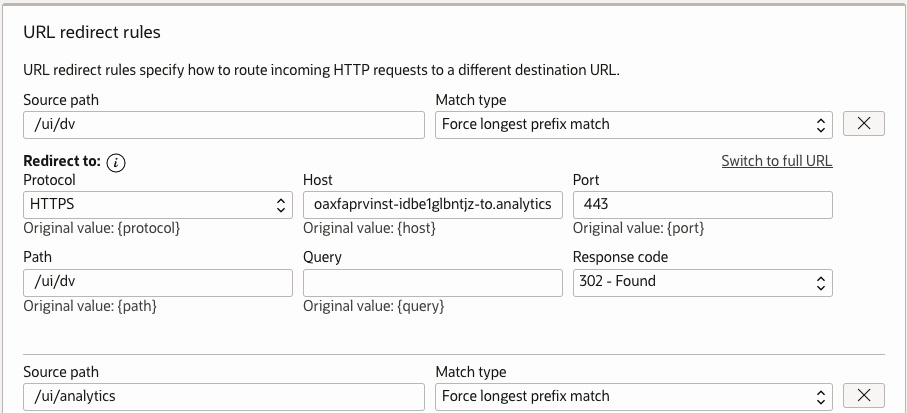
- Add URL redirection rules for these source paths to the rule set.:
- /ui
- /ui/dv
- /analytics
- /ui/analytics
- /ui/oax
- For each rule:
- Use the prebuilt FDI console hostname for the /ui/oax rule.
- Use the prebuilt FDI OAC hostname for all other rules.
- Use the source path as the Path.
- Use Force longest prefix match as the Match type.
- Use https as the Redirect protocol.
- Use 443 as the Redirect port.
- Leave the Redirect query blank.
- Use 301 - Moved Permanently as the Response code.
- Add URL redirection rules for these source paths to the rule set.:
- Create and associate a Rule Set to the load balancer listener.
- Follow your organization’s procedures for adding a DNS record to the private internal zone containing the custom hostname and the load balancer’s private IP address.
An example may look like this:
Domain:
Type:
TTL:
RDATA:
analytics.dev.myorg.com
A
500
129.35.20.68

After the components are deployed, custom hostnames can be used to access Fusion Analytics services.
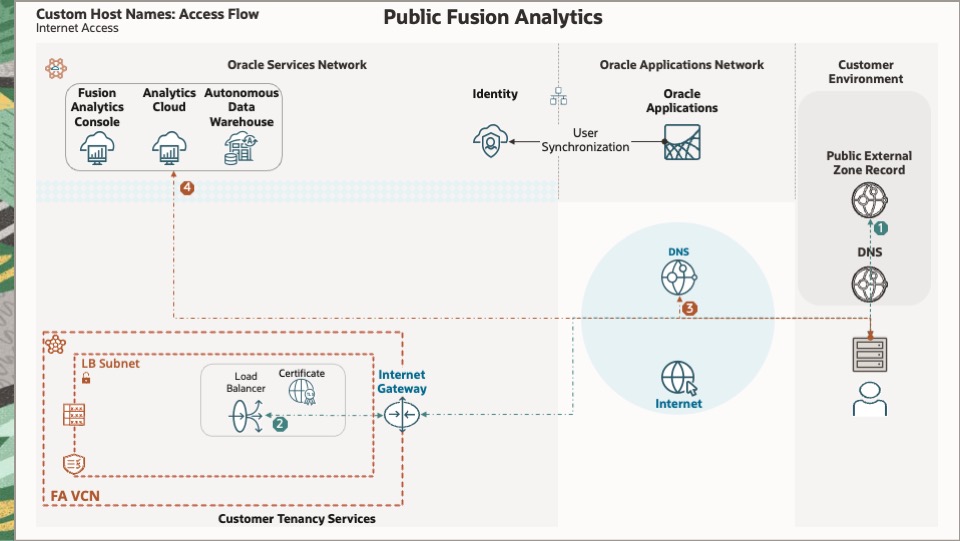
This diagram depicts the access flow for a public Fusion Analytics instance using custom hostnames.
![]()
![]()
![]()
![]()
A client browser sends a DNS query with the Fusion Analytics custom hostname. The query is resolved with the record in the public external zone, and the LB (Load Balancer) IP is returned.
The browser sends an HTTPs request to the LB with the Fusion Analytics custom hostname. The load balancer evaluates the URL path and match rules and returns the Fusion Analytics hostname.
The browser sends a DNS query with the Fusion Analytics hostname. An Internet DNS resolves the query, and the Fusion Analytics service IP is returned.
The browser sends an HTTPs request with the Fusion Analytics hostname to the Fusion Analytics web service.


