
Published Version 7 on July 25th, 2024 using the current FDI release 24.R2
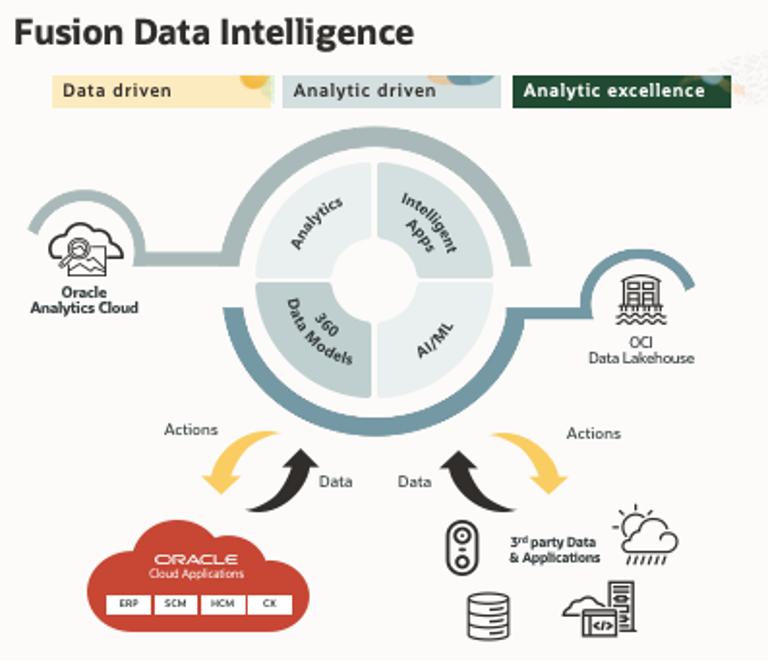
Oracle Fusion Analytics (Fusion Analytics) is a component of the FDI (Oracle Fusion Data Intelligence) platform designed to deliver personalized insights for Oracle Fusion Cloud Applications (Fusion Cloud Applications). It combines business data, ready-to-use analytics, and prebuilt AI (Artificial Intelligence) and ML (Machine Learning) models to deliver deep insights and actionable results.
This post provides an overview and landing page for blog posts describing using custom hostnames in different implementation scenarios. It offers guidance on preparing the components required to use custom hostnames in all scenarios.
Note: This post describes using a custom hostname for two FDI web services, one of which is OAC (Oracle Analytics Cloud). It does not cover using a custom hostname for the FDI ADW (Autonomous Data Warehouse). The Call to Action includes links to relevant ADW documentation.
Note: The Vanity URL feature available in standalone instances of OAC offers more functionality than the method described in this post. However, it is unavailable in the current release of Fusion Analytics. The method described in this post may also be used for standalone instances of OAC if desired.
Use Case
Custom hostnames enable customers to use their registered domains for Fusion Analytics services and a single hostname for multiple web services.
The following shows the Fusion Analytics prebuilt hostnames format as of the current release.
- Fusion Analytics Console
- <instance name>-<tenancy name>-prod.data.analyticsapps.<region name>.ocs.oraclecloud.com
- Oracle Analytics Cloud
- oax<instance name>-<tenancy object storage namespace>-to.analytics.ocp.oraclecloud.com
The following shows an example format of a custom hostname used by Myorg, inc., whose registered domain is myorg.com.
- For all Fusion Analytics services
- analytics.<environment>.myorg.com
Prerequisites
Following the guidance in this post requires:
- An existing Fusion Analytics instance is accessible by users.
- Administrators with the authority to:
- Create and submit a CSR (Certificate Signing Request) to a registered CA (Certificate Authority).
- The OpenSSL toolset for the examples in this post. If your workstation does not have OpenSSL, obtain it using one of the following methods:
- Download and install it from OpenSSL Downloads.
- Create a temporary OCI Linux compute instance.
- Use an Apple Mac, which by default uses LibreSSL.
Run the following command in a Terminal or PowerShell session to determine the existence of OpenSSL and the version used.
openssl version
Topics
- Architecture
- Components
- Deploy
- Implementation Scenarios

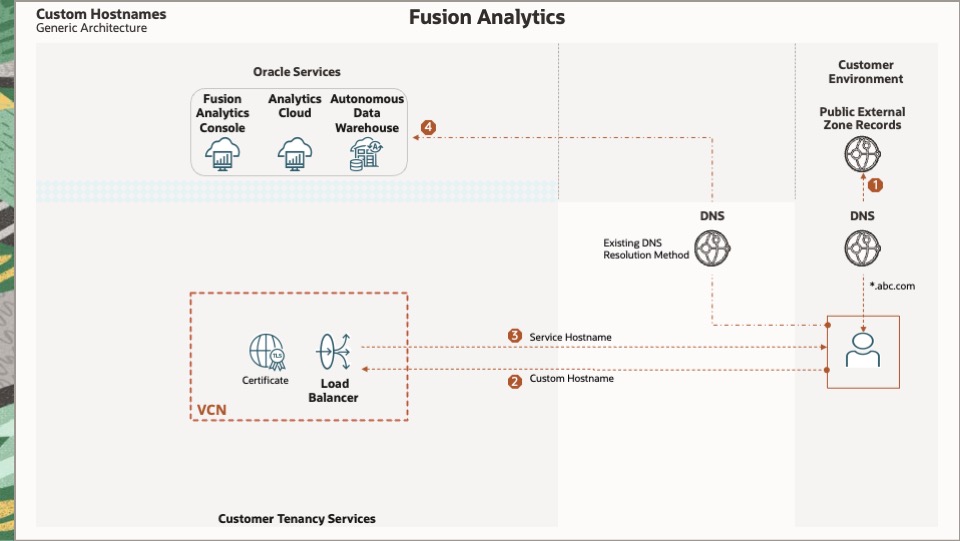
This diagram depicts the logical flow for custom hostnames:
- The user enters a custom URL containing a custom hostname into a browser.
- The browser sends the custom hostname to a DNS server.
- The DNS server returns the IP Address of the load balancer.
- The browser sends the custom URL to the load balancer.
- The load balancer returns the Fusion Analytics URL containing the Fusion Analytics hostname.
- The browser accesses the Fusion Analytics service using the Fusion Analytics URL.
Note: Detailed architectures are provided in the implementation scenario posts.

The following are components used to enable custom hostnames.
A private key creates a CSR, which a CA digitally signs. The key is later used to secure and verify connections to the load balancer.
OCI load balancers accept private keys using the RSA algorithm in PEM format only.
Certificate Signing Request A CSR contains a public key and information, such as the common name, organization, country, and the CA used to create and sign a certificate.
Certificate Authority
A CA issues certificates based on the information in a CSR and signs it with a private key. CAs exist to certify the ownership of a public key in a given certificate.
Certificate
A certificate is a digital document created and signed by a CA that verifies the load balancer’s owner. It is required when using HTTPs and SSL with a load balancer and its resources.
OCI load balancers only accept x.509 type certificates in PEM format.
Load Balancer
The Load Balancer service provides automated traffic distribution and redirection. It offers a choice of a public or private IP address and provisioned bandwidth.
Listeners
A listener is a logical entity that checks for incoming traffic on the load balancer’s IP address for one or more protocols and ports. Based on its configuration, it distributes or redirects incoming traffic.
SSL Certificates for Load Balancers
Custom hostname certificates are uploaded, imported, and attached to a listener. They display important information to clients to verify the load balancer’s owner and the certificate’s issuer.
URL Redirect Rules
URL redirect rules are attached to a listener and specify how to route incoming HTTPs requests to a different destination URL.
DNS
The DNS (Domain Name System) translates human-readable hostnames to machine-readable IP addresses. DNS uses DNS records containing hostnames and their IP addresses to respond with answers to DNS queries.
DNS records are stored in either public/external zones or private/internal zones.
Public External Zone
A public DNS external zone has the DNS record, publicly available on the internet, containing the load balancer’s custom hostname and public IP address.
Private Internal Zone
A private DNS internal zone has the DNS record, available only in the internal network, containing the load balancer’s custom hostname and private IP address.

Nothing needs to be deployed now if you have a signed certificate for the desired custom hostname. If not, follow your organization’s procedures for creating a CSR, submitting it to a CA, and receiving a signed certificate.
For development purposes, the guidance in this section creates the following components for a certificate signed by a self-deployed CA.
- Create a Self-Deployed CA
- Create a Private Key
- Create a CSR
- Create a Certificate
A typical provisioning sequence follows:
Create a CA private key and use it to create a CA certificate.
openssl genrsa -out myRootCA.key 4096; openssl req -x509 -new -nodes -key myRootCA.key \ -subj "/C=US/ST=CA/O=MyCAOrg" -sha256 -days 1024 \ -out myRootCA.crt
Create a Private Key
Create a private key for the custom hostname CSR.
openssl genrsa -out myorg.key 2048
Create a CSR
Create a custom hostname CSR using the private key.
openssl req -new -sha256 -key \ myorg.key -subj '/C=US/ST=CA/O=MyOrg/CN=*.myorg.com' -out myorg.csr
Create a Certificate
Create a custom hostname certificate by signing the CSR with the CA certificate and key.
openssl x509 -req -in myorg.csr \ -CA myRootCA.crt -CAkey myRootCA.key \ -CAcreateserial -out myorg.crt -days 500 -sha256
Note: The blog posts listed in the Implementation Scenarios section below guide with deploying a load balancer, uploading the certificate, and configuring DNS

Depending on the type of Fusion Analytics services and the type of access, follow one of the scenarios to implement custom hostnames.

Explore Fusion Analytics by visiting the community links, blogs, and library.
- Overview of the OCI Certificate Service
- Overview of OCI Load Balancers
- Load Balancer URL Redirection
- SSL Certificates for Load Balancers
- OpenSSL
- Access Oracle REST Data Services, Oracle APEX, and Developer Tools Using a Vanity URL
- Fusion Analytics Community
- Fusion Analytics Blogs
- Fusion Analytics Library


