The Evolving Threat Landscape and the Need for Stronger Authentication
As cyber threats continue to grow, organizations must stay ahead by adopting robust security measures to protect sensitive information and digital resources. Private and public organizations must go beyond traditional password-based security and implementing phishing-resistant multifactor authentication (MFA), adaptive risk-based security, and passwordless access. For public organizations, this need has transitioned from being a best practice to becoming a compliance mandate in many regions from the following directives:
- US government zero trust mandate: The Biden Administration’s Executive Memorandum, “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles” (M-22-09) has mandated federal agencies to implement zero trust architecture, explicitly calling for phishing-resistant MFA. This directive aligns with the broader zero trust goal to ensure secure and verified access across federal networks.
- Australia’s Essential Eight: The Australian Cyber Security Centre (ACSC) includes MFA as a core strategy within the Essential Eight framework. It explicitly recommends adopting phishing-resistant MFA methods to safeguard critical infrastructure and public sector organizations.
- European Union’s Digital Operational Resilience Act (DORA) requires robust security measures like MFA to ensure operational resilience against cyber threats.
With Oracle Advanced Authentication (OAA), Adaptive Risk Management (OARM), and Universal Authenticator (OUA) solutions, organizations can protect their users and data while simplifying the authentication experience.
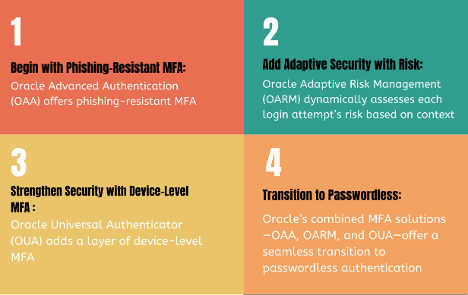
Begin with Phishing-Resistant MFA through OAA
Many organizations rely on password-based security, which is vulnerable to phishing attacks. Phishing attacks are becoming increasingly sophisticated, and traditional MFA, such as email and SMS-based one-time password (OTP), isn’t enough to prevent them.
OAA offers broad range of MFA options, including phishing-resistant MFA factors such as FIDO2-based authentication. These options help ensure that, even if a password is compromised, attackers can’t gain access without more verification. OAA includes the following features and benefits:
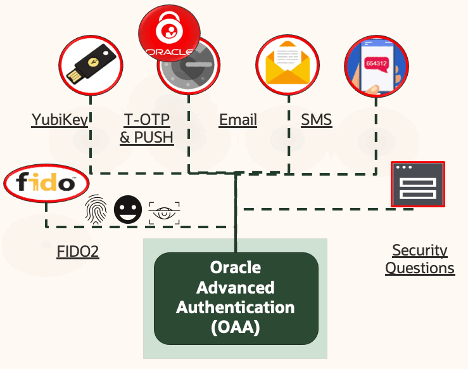
- FIDO2 authentication: FIDO2 is one of the most secure forms of authentication available today. It uses public-private key cryptography to verify a user’s identity without sending passwords over the network. In this setup, the user’s private key is stored securely on a FIDO2 security key, such as a Yubikey or biometric-enabled device, such as Windows Hello and Mac TouchID, which verifies the user’s identity by comparing a public key stored with OAA. This method is resistant to phishing because attackers can’t use fake websites or email-based attacks to intercept the private key because it never leaves the security key or device.
- Push notifications and time-based OTP: OAA also supports push notifications and OTP-based MFA, providing flexibility for various user scenarios. For example, push notifications allow users to authenticate by simply approving a prompt on their mobile device, ensuring that only authorized devices can confirm access.
By adopting OAA, Oracle customers can significantly reduce phishing risks and reinforce their security stance.
Add Adaptive Security with OARM
Users often log in from multiple locations, devices, and networks, which can be difficult to secure without implementing complex security layers. Static authentication doesn’t account for changes in risk. Oracle Adaptive Risk Management (OARM) dynamically assesses each login attempt’s risk based on context, including the user’s device, location, IP address, and behavior history. By integrating OARM with OAA, customers can establish adaptive, context-driven security with the following features:
- Risk-based step-up authentication: If a user’s behavior deviates from their typical pattern, OARM can trigger extra security measures. For example, if an employee typically logs in from the office and then attempts access from an unfamiliar location, OARM prompts them for more MFA verification. This configure helps ensure that only legitimate users can access the system, even under unusual circumstances.
- Behavioral analysis and IP intelligence: OARM continuously evaluates login attempts to detect potentially malicious activities. For example, logging in from high-risk or flagged IP addresses can automatically require the user to reauthenticate or provide more verification.
By integrating OARM, Oracle customers can secure their environments dynamically without disrupting legitimate users.
Strengthen Security with Device-Level MFA through OUA
While MFA can protect against unauthorized access, organizations also need a way to bind specific devices to specific users, ensuring that only trusted devices are allowed access. Oracle Universal Authenticator (OUA) adds a layer of device-level MFA, enabling customers to register trusted devices and secure access to devices, applications, and data even further with the following features:
- Device trust and recognition: OUA enables device-based MFA by registering users’ devices as trusted endpoints. So, users don’t need to repeat web or desktop application login on recognized devices, reducing login friction and increasing security. For example, if a user logs in from their registered Windows machine, they might be prompted to verify their identity using preferred MFA method. After that, they can single-sign-on to OAM protected applications or desktop applications, creating a frictionless experience for trusted devices.
- Seamless access for recognized devices: With device-level authentication, OAM customers can avoid continuous authentication prompts for known devices, while maintaining strict security and compliance requirements. This balance helps ensure that users have a seamless yet secure experience.
OUA helps ensure that only authorized devices and users access sensitive systems, reinforcing security and compliance for the organizations.
Transition to Passwordless Security with OAA, OARM, and OUA
Passwords are one of the weakest links in authentication security. Passwords can be stolen, shared, or reused, making them easy targets for attackers. Organizations increasingly seek passwordless solutions for enhanced security and user convenience.
Oracle’s combined MFA solutions—OAA, OARM, and OUA—offer a seamless transition to passwordless authentication, eliminating the need for traditional passwords while maintaining high security with the following steps:
- Implement phishing-resistant MFA (OAA) using FIDO2 or biometric factors.
- Integrate OARM to add adaptive, risk-based security that dynamically responds to login conditions.
- Extend device trust with OUA and add MFA for device level login, associating users with specific devices for an added layer of protection.
- Reduce reliance on passwords by allowing secure passwordless login options at application and device level, like FIDO2-based biometrics, push notification with Oracle Mobile Authenticator, or OUA-based device MFA.
With this phased approach, organizations can embrace passwordless authentication gradually, minimizing disruption and ensuring users are fully prepared.
Build a Future-Proof Security Ecosystem with Oracle’s MFA and Passwordless Solutions
Oracle customers now have a powerful pathway to enhanced security through Oracle Advanced Authentication, Adaptive Risk Management, and Universal Authenticator. By adopting a phased approach, organizations can gradually strengthen their security, reduce reliance on passwords, and achieve a seamless authentication experience across all devices and applications.
To start your journey towards phishing-resistant MFA and passwordless security today, refer to the following documents and tutorials:
- Oracle Advanced Authentication Solutions
- Installing OAA, OARM, and OUA
- MFA everywhere: Tailored strategies for securing diverse industries (Blog post)
- Oracle Access Management website
