4 Power Tools for Security Leaders
Successful leaders bring people together to achieve common objectives, so that each person’s contributions bring the organization closer to those objectives. For example, security leaders need effective ways to guide personnel, so their activities support the organization’s security goals. Luckily, there are four power tools which enable leaders at all levels to align operations and personnel decisions with the security objectives. These tools are policies, standards, processes, and procedures.
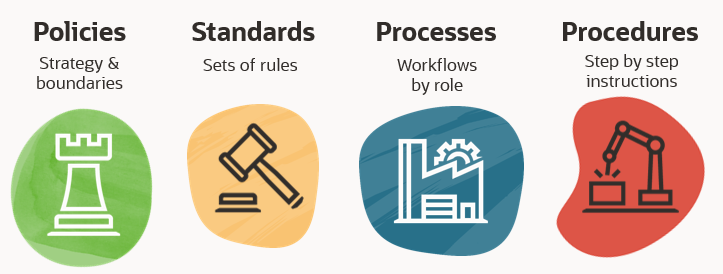
When defined and communicated clearly, these tools support operational excellence by guiding choices and behavior at varying levels of specificity. This post explains how security leaders can deploy each of these 4 tools to guide the decisions and actions of personnel across their organization.
To illustrate how policies, standards, processes, and procedures collectively form a complete system, we’ll use the example of securing a company’s access controls with Oracle Cloud Infrastructure (OCI) services.
Policies define boundaries
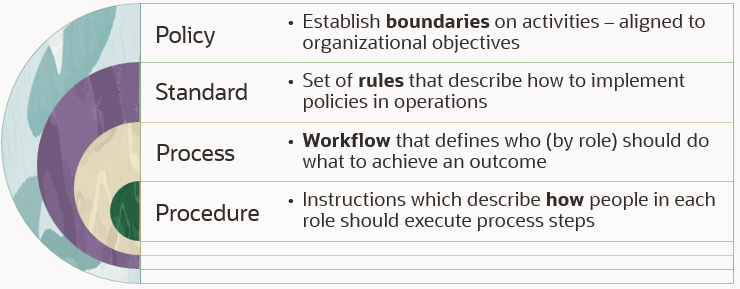
Policies establish limits on activities, with broad guiding principles that reflect an organization’s objectives and risk tolerance. They define the limits of acceptable actions by personnel, specifying what must happen, what must not happen and what may happen. When writing policies, entities, such as nations, organizations, and businesses should consider their intended audience – the people they want to understand and comply with the policy. Two types of policies are relevant for security leaders:
- Policy documents to be used by people in the intended audience
- Policy configurations used by technology, such the OCI Identity and Access Management (IAM) policies
Policy documents
These are broad collections of statements to guide a particular area of operations, such as these types of security policies. Policies often contain descriptions of what personnel must and must not do. Example statements which might be in an identity management policy include:
- Do not share your authentication credentials or hardware with anyone.
- Multi-factor authentication is required for all applications.
- Generic accounts are prohibited.
Policy configurations
Using the OCI IAM example, policy statements allow a group to work in certain ways with specific types of resources in a particular compartment using this syntax. A resource is a cloud object that you create and use when interacting with Oracle Cloud Infrastructure services. A compartment is a collection of related resources that can be accessed only by groups that have been given permission by an administrator.
Standards define rules
Standards are sets of RULES that align operations to policies. These rules can describe how to use technology as well as describe requirements for certain professions such as medicine, financial accounting, and law. Many organizations leverage standards defined by external sources, in addition to internally-defined standards. Sources of standards include organizations such as:
- US National Institute of Standards and Technology (NIST)
- Standards Australia
- European Standards within the European Union
- Financial Accounting Standards Board (FASB)
- International Standards Organization (ISO)
Similar to policies, there are two types of security standards:
- Standards documents used by people such as NIST 800-53 Security and Privacy Controls for Information Systems and Organizations
- Standards configurations used by technology such as OCI Security Rules or Zero Trust Packet Routing to control how OCI Networking handles connectivity
Example standards document statements for implementing an identity management policy might be:
- Authentication factors based on “something you know” must expire every 90 days.
- Passwords, passcodes, and other authentication factors based on “something you know” must be at least 20 characters long.
- Approved repositories must be used to store authentication credentials and tokens for service (machine to machine) accounts.
Processes define steps
Processes are WORKFLOWS which outline the activities required to operationally achieve a specific outcome, in compliance with policies and standards. Processes define who (by role) should take which steps and in what order. Many processes include conditional branches such as steps for handling variances for specific situations (if X, skip to step 9, else continue to next step). Pre-requisites may also be included for starting a process. Example processes steps supporting an identity management policy could be:
New employees
- New personnel must obtain initial authentication credentials from their Manager.
- Select which factors you will use for multi-factor authentication.
- Install necessary authentication applications or purchase authentication hardware.
- Configure your primary and alternate methods of multi-factor authentication in the identity management system.
Procedures define task instructions
Procedures detail step-by-step instructions for HOW TO complete a process and are typically more specific about who should complete each step and in what application. For example, a process step might assign to the IT team, but the procedures would specify that an Identify Management Analyst should execute the activity. Example procedural instructions for configuring authentication methods for process step 4 could be:
4a) Using your initial authentication credentials, log into the identity management system at <URL>.
4b) Click the checkbox next to all the methods of multi-factor authentication you’ll be using.
Note: You can only select a hardware token if you have purchased it already because the serial number must be registered.
4c) For each factor you’ll use, click the radio button for either ‘primary’ or ‘alternate’.
Use these tools to improve security posture
Security leaders can use the power tools of policies, standards, processes and procedures to drive the organization towards security goals and help prevent security incidents. Collectively, these tools provide a structured guidance framework that helps align organizational activities and decisions with executive expectations.
Power tools implementation checklist
- Define policy documents to answer “can I/must I” questions.
- Configure technology policies to enforce the policy document requirements.
- Define standards documents that align with policies.
- Configure standards in technology which implement policy and standards requirements.
- Define processes to answer operational questions about steps to achieve particular outcomes.
- Define detailed procedures of task instructions to answer “how do I” questions for each process step.

These sites provide examples and how-to help for writing and maintaining policies, standards, processes and procedures:
- Policy template and instructions, Brown University
- Policy management, Michigan State University
- Organization-wide policies in addition to department-specific policies, University of North Carolina
- Policies and standards, University of Texas
- User Guide to Writing Policies, University of Colorado
Learn more about using policies in Oracle Cloud Infrastructure (OCI):
- OCI Policy Reference explains how to configure and define technical policies
- OCI Glossary defines common terms
- Oracle Cloud Free Tier
- Free OCI training
